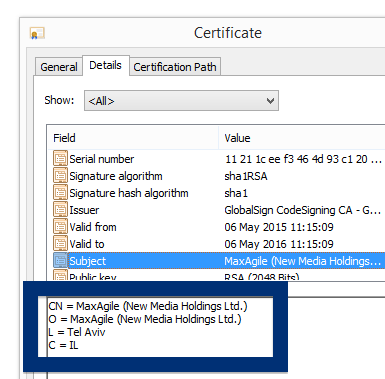
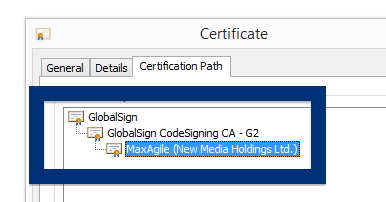
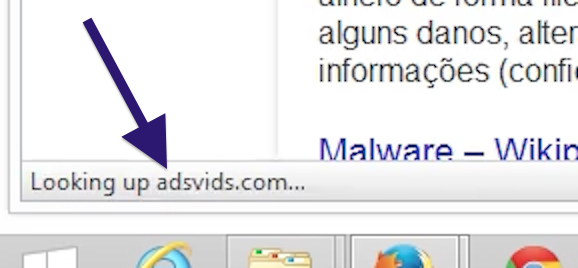
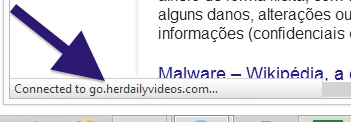
Sound familiar? You see pop-up ads from topf1le.com while browsing sites that typically don’t advertise in pop-up windows. The pop-ups manage to get round the built-in pop-up blockers in Google Chrome, Mozilla Firefox, Internet Explorer or Safari. Perhaps the topf1le.com pop-ups appear when clicking search results from Google? Or does the pop-ups appear even when you’re not browsing?
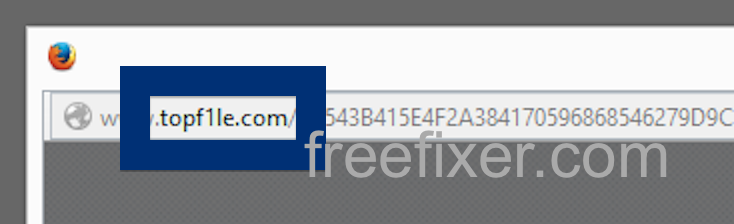
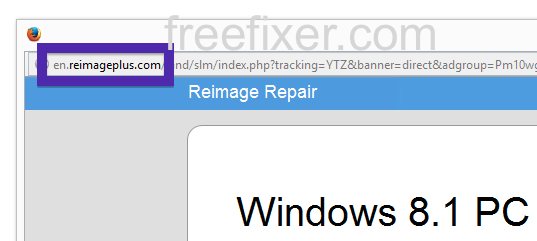
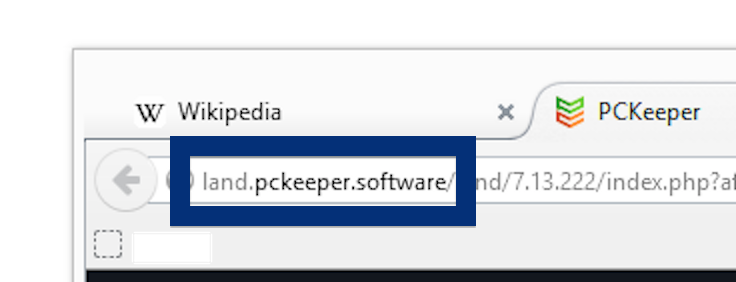
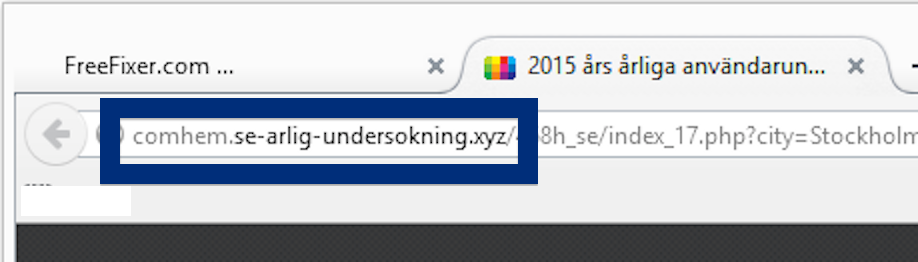
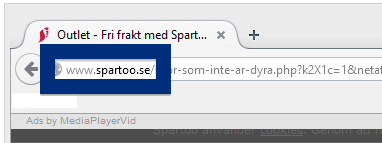
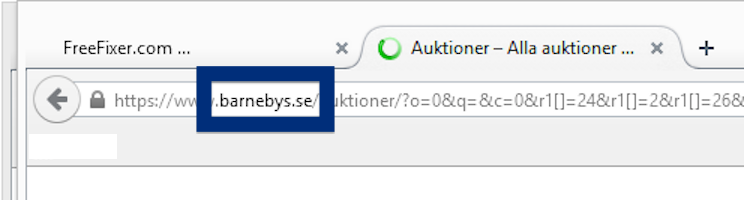
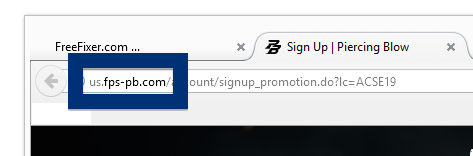
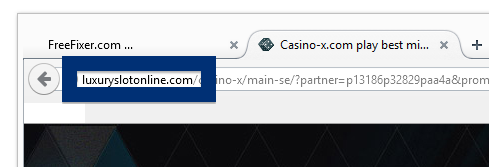
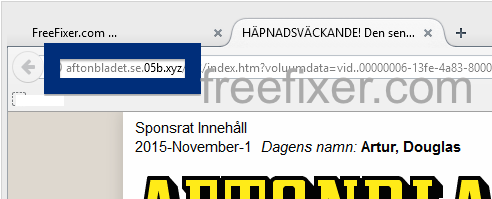
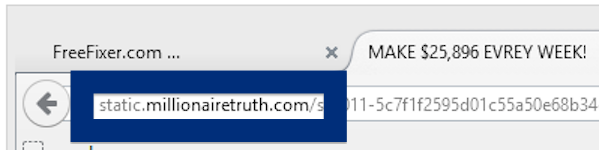
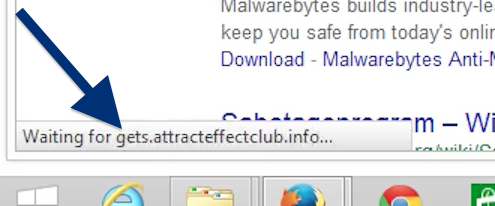
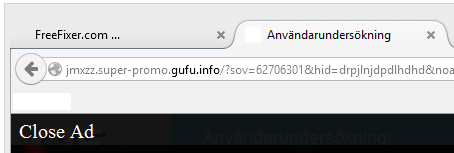
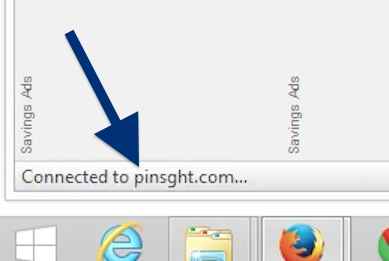
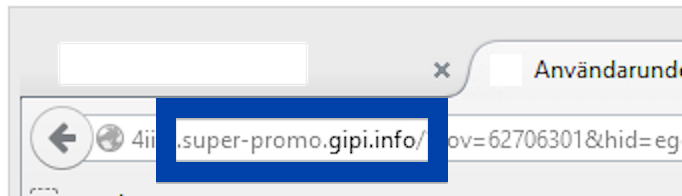
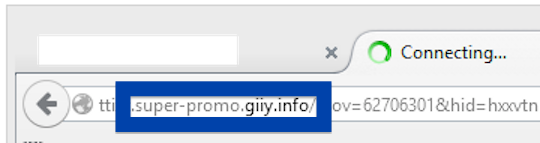
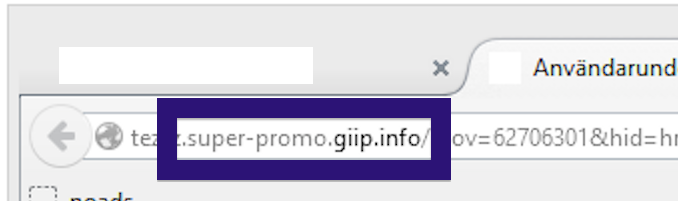
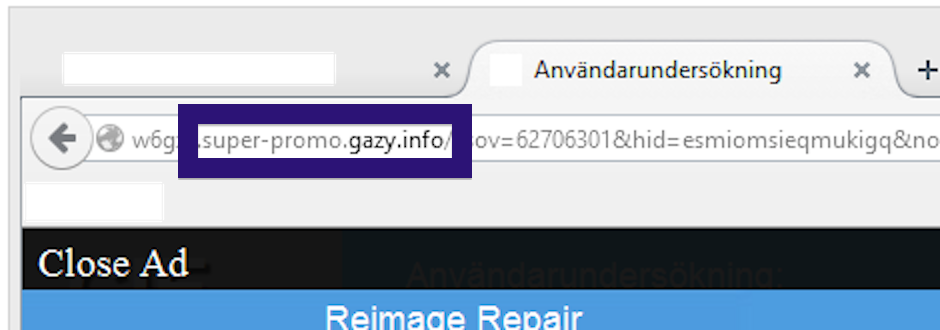
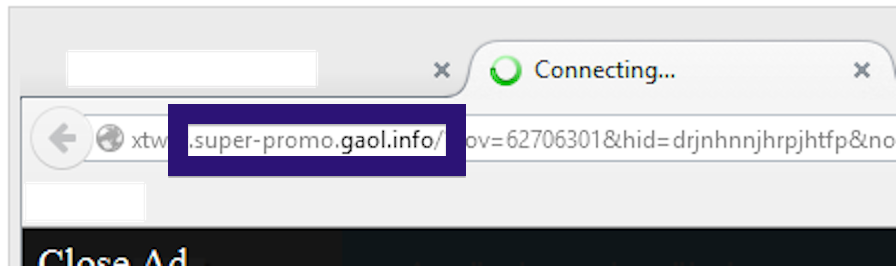
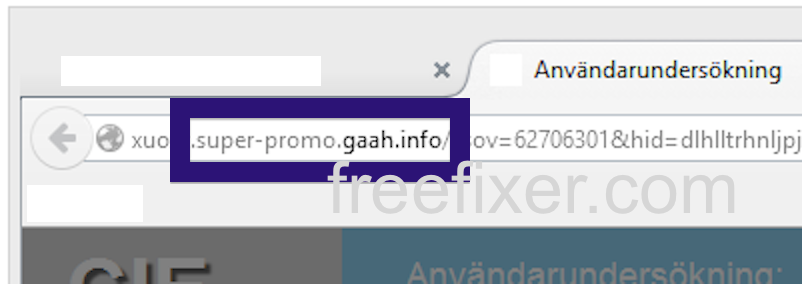
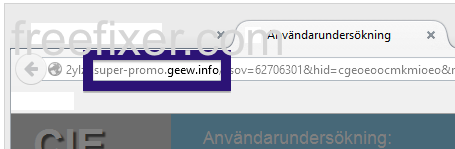
Here is how the topf1le.com ad looked like on my computer:
If this sounds like what you are seeing on your computer, you presumably have some adware installed on your system that pops up the topf1le.com ads. So there’s no use contacting the site owner. The ads are not coming from them. I’ll try help you with the topf1le.com removal in this blog post.
I found the topf1le.com pop-up on one of the lab machines where I have some adware running. I’ve talked about this in some of the previous blog posts. The adware was installed on purpose, and from time to time I check if something new has appeared, such as pop-up windows, new tabs in the browsers, injected ads on website that usually don’t show ads, or if some new files have been saved to the hard-drive.
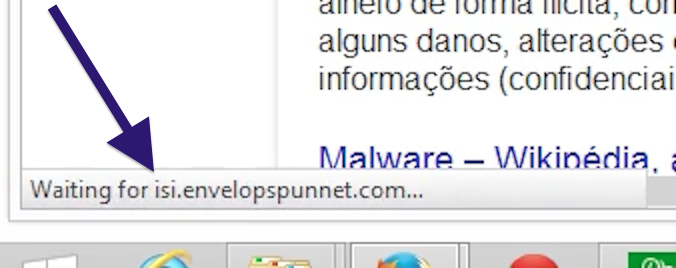
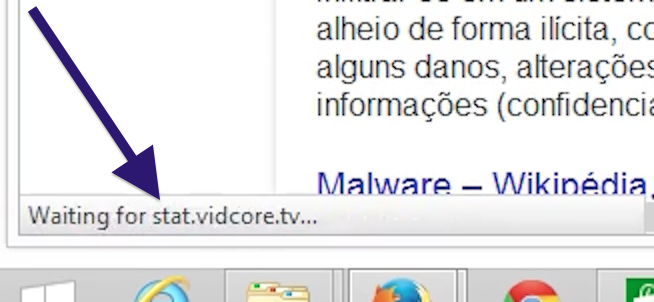
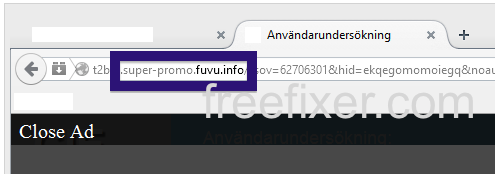
topf1le.com was registered on 2015-07-24. In the pop up URL I’ve spotted the following domain:
- www.ultifiletur.com
- www.defile4.com
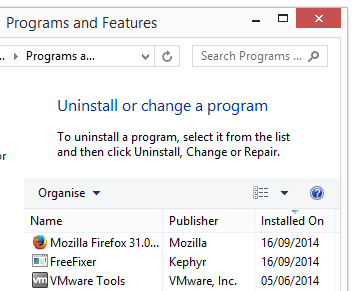
So, how do you remove the topf1le.com pop-up ads? On the machine where I got the topf1le.com ads I had gosearch.me, SmartComp Safe Network, Live Malware Protection and Windows Menager installed. I removed them with FreeFixer and that stopped the topf1le.com pop-ups and all the other ads I was getting in Mozilla Firefox.
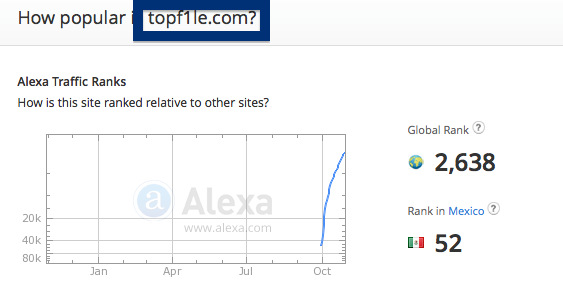
If you are wonder if there are many others out there also getting the topf1le.com ads, the answer is probably yes. Check out the traffic rank from Alexa:
The issue with pop-ups like the one described in this blog post is that it can be popped up by many variants of adware. This makes it impossible to say exactly what you need to remove to stop the pop-ups.
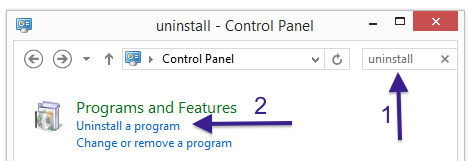
So, what can be done? To remove the topf1le.com pop-up ads you need to check your machine for adware or other types of unwanted software and uninstall it. Here’s my suggested removal procedure:
- Review what programs you have installed in the Add/Remove programs dialog in the Windows Control Panel. Do you see something that you don’t remember installing or that was recently installed?
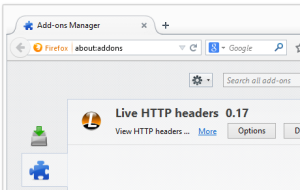
- You can also check the add-ons you have in your browsers. Same thing here, do you see something that you don’t remember installing?
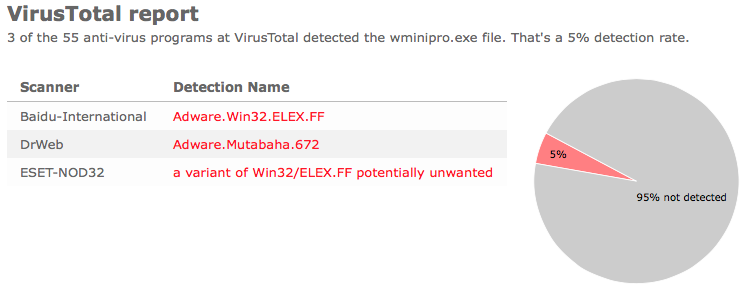
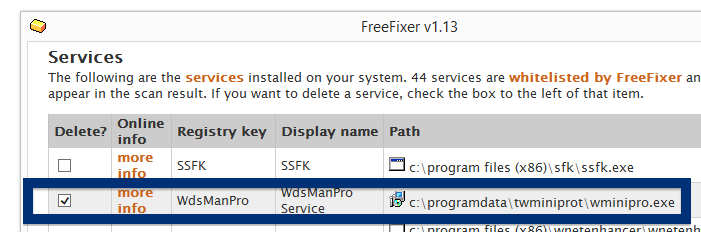
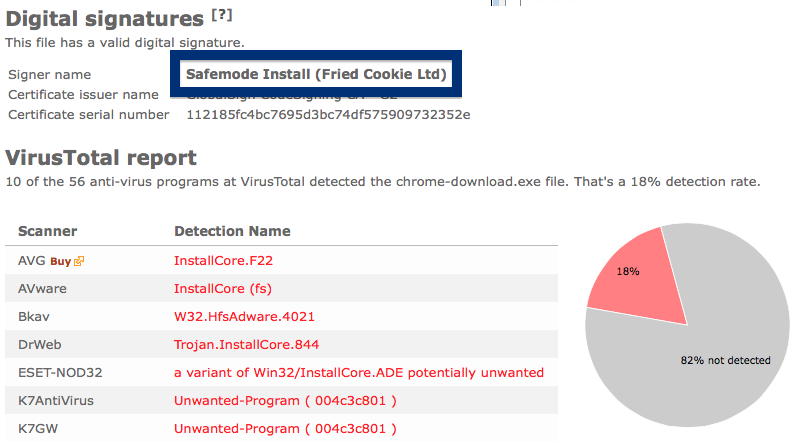
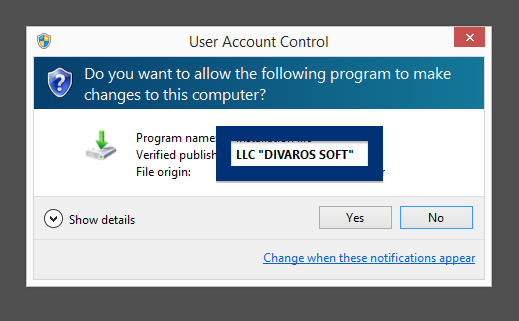
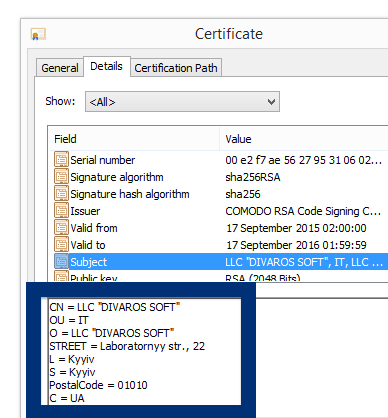
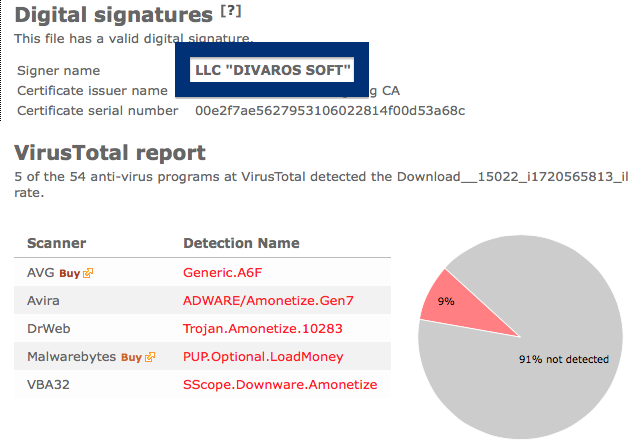
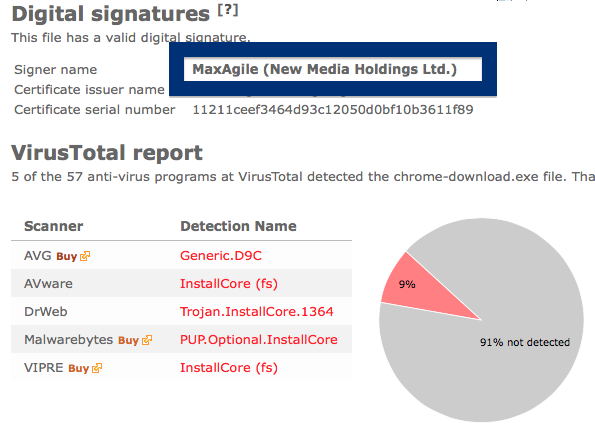
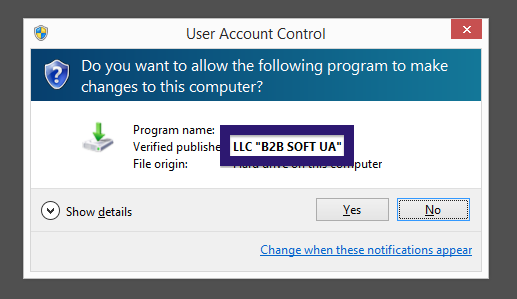
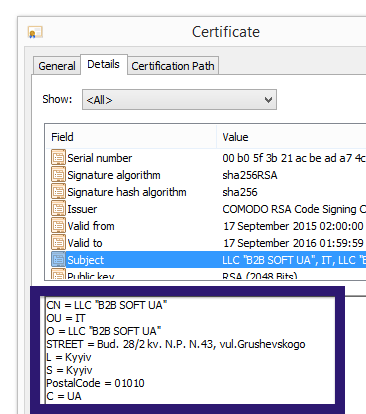
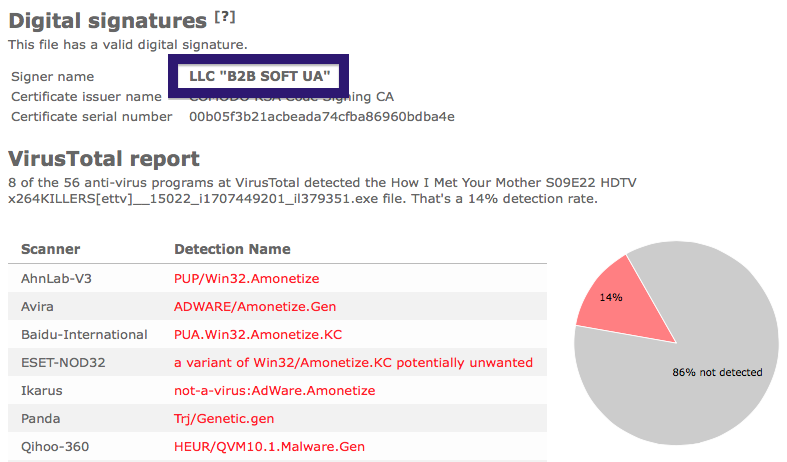
- If that did not help, you can give FreeFixer a try. FreeFixer is built to assist users when manually tracking down adware and other types of unwanted software. It is a freeware utility that I’ve been working since 2006 and it scans your computer at lots of locations where unwanted software is known to hook into your computer. If you would like to get additional details about a file in FreeFixer’s scan result, you can just click the More Info link for that file and a web page with a VirusTotal report will open up, which can be very useful to determine if the file is safe or malware:

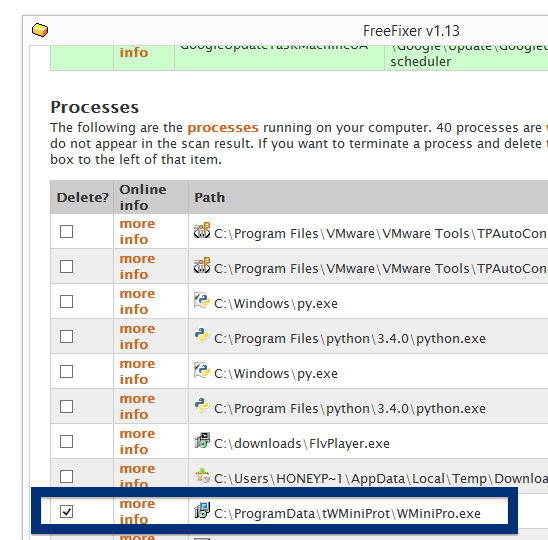
An example of FreeFixer’s “More Info” links. Click for full size.
Here’s a video tutorial which shows FreeFixer in action removing adware that caused pop-up ads:
Did this blog post help you to remove the topf1le.com pop-up ads? Please let me know or how I can improve this blog post.
Thank you!