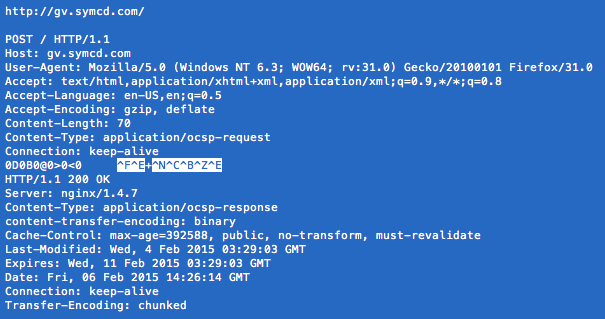
Morning! Hope you are having a great weekend. I’ve been experimenting with some network monitoring of HTTP requests and responses in Mozilla Firefox. While playing around with one of the tools I’m evaluating I noticed a request to gv.symcd.com:
I had not heard of the symcd.com domain before so I got curious. The request is a “application/ocsp-request“. OCSP is a abbreviation for Online Certificate Status Protocol and it is an Internet protocol used for retrieve the revocation status of a digital certificate.
That’s what the symcd.com connection is about: Checking the revocation state for some certificate. The tool I used to track the network traffic does not have any advanced features to decode the OSCP communication so I don’t know exactly what information Firefox requests from symcd.com.
So, who owns symcd.com? The WHOIS database answer is Symantec Corporation:
Registrant Organization: Symantec Corporation Registrant Street: 350 Ellis Street Registrant City: Mountain View Registrant State/Province: CA Registrant Postal Code: 94043 Registrant Country: US
Symcd.com was created on 2013-12-12.
I did not find much information about gv.symdc.com, and the reason for that is probably because there’s a large number of subdomains used. I found this list over at VirusTotal:
- sm.symcd.com
- gz.symcd.com
- gp.symcd.com
- tl.symcd.com
- sn.symcd.com
- tm.symcd.com
- gq.symcd.com
- sk.symcd.com
- gw.symcd.com
- si.symcd.com
- gx.symcd.com
- gk.symcd.com
- s.symcd.com
- sw.symcd.com
- gu.symcd.com
- sh.symcd.com
- tf.symcd.com
- t.symcd.com
- tn.symcd.com
- gv.symcd.com
- ta.symcd.com
- gd.symcd.com
- st.symcd.com
- tg.symcd.com
- sr.symcd.com
- sd.symcd.com
- sf.symcd.com
- sg.symcd.com
- th.symcd.com
- ga.symcd.com
- gn.symcd.com
- se.symcd.com
- sv.symcd.com
- tj.symcd.com
- su.symcd.com
- tb.symcd.com
- ti.symcd.com
- tc.symcd.com
- sc.symcd.com
- gm.symcd.com
- sb.symcd.com
- gb.symcd.com
- ss.symcd.com
- sj.symcd.com
- gj.symcd.com
- td.symcd.com
- sa.symcd.com
- tk.symcd.com
I checked a few of the domains, and they all resolved to the 23.43.139.27 IP address.
Thanks for reading!
So what exactly triggers this? I see this show up while surfing non https sites like tumblr pages. If OCSP is meant for https sites(as far I am aware), then what purpose does it serve when surfing tumblr or other pages having nothing to do with https?
Rather strange. Makes me a little paranoid. Is it the browser calling out because a page triggers it or is it a bug or malware etc making a callout?
Or just something on a webpage that may be benign?
It is my belief that the Symantec Corporation is $ucking the fun out of being a home PC users that does not want BIG companies programs like FW, AV, AM, etc. & have 2 pay Too much money 4 such program!?! So we use all smaller companies that develops free programs that are more superior & better built 4 home users!?! Then Symantec comes along & buy up these little companies, promising 2 keep them going!?! Then suddenly you wake up 1 morning 2 find out that ur FW or AV no longer works because Symantec has shut them down, oh but if you only pay this 1 time steal of a deal 2 use theirs & blah blah blah….. & THE SHIT GOES ON!?!
HI.. I FOUND :
h t t p : / / g v . s y m c d . c o m \ AND BIG HUGE NUMBER STRING..(deleted it was too big, LOOKED LIKE A DEVICE KEY..OR IDENTIFIER)
AS A SYSTEM FILE, ( ACTUALY DOZENS OF THEM ) IN MY SURFACE 2 WINDOWS RT 8.1
YOU SAY ITS MOZILLA AND OR SEMANTIC…. WHAT THE HELL IS IT DOING AS SYSTEM FILES ON WINDOWS RT ? COULD THAT BE PART OF OR WHAT WINDOWS DEFENDER IS..?
C:\Users\jxxx_000\AppData\LocalLow\Microsoft\CryptnetUrlCache\Metadata\ h t t p : / / g v . s y m c d . c o m \(big long number here..deleted it)
My husband has it on his Pc too. His one note notebook has a license attached to it for wondershare in Japan and I’m affraid he’s doing something he shouldn’t be
Someone was playing around with that traffic and was doing a man in the middle attack, basically changing certificates on the fly.
I had a program attempt to connect to th.symcd.com today. When I went to google it, it went to the site, and automatically downloaded a file simply called ‘download’ onto my machine with no prompts or permission from me. I deleted it immediately but I wonder if this site is as benign as people believe it is.
Strange things, this ‘??.symcd.com’ set of sites. I tried several things to block them at the router (like ‘block *.symcd.com’) and the ‘block all’ did not work on that domain. Split domain, eh? ok, doing it the hard way, I keyed in the list of all known symcd.com variants. Interestingly enough, SS.symcd.com and gn.symcd.com can STILL be accessed!
It is a Windoze thing, as nothing on my Linux systems are calling this intrusive domain. So, if you are paranoid about symcd.com, maybe you have a reason to justifiably be. If this were a ‘certificate revocation’ site only, it would be unilateral across all systems. If it were legitimate, going to Symantec’s site should give you information about it. If you hide it in secrecy, have a hundred variant sites all pointing to about 7 actual IANA locations, and only call it through one operating system, it sure looks maliciously like MALWARE to me. Blocked at the router, get over it Symantec…explain yourself or forget you.
It’s nothing to worry about. To operate an ocsp server is quite expensive. Symantec is providing this server as an “free” service to the “customers”… as far as I know, the server responses to everyone whos asking him about validity of certificates. Since they need ocsp to run their business (need to check certificates all day long) having this infrastructure comes in handy… i don’t know if thei get paid from (for example) microsoft, cause this watson/telemetry shit from microsoft seems to trigger ocsp requests so symcd.com.
And yes, this protocol is not perfect but internet standard.
You are free to block ocsp.
And for your paranoia… nobody of you is worth the work of distribute a “man in the middle” – ocsp related hack, with compromised certificates or something… this is way too much work for nothing 🙂
greez
Reguardless of what or why it is.. It is intusive.
Looking at this feeds date .. Today 1222016 IE would not open from prompt. So I do the run admin … As IE loads to google front page. All these symcd.cm’$ mention were bocked by the maleware identity program. And the page had not loaded….interesting
I tested some Urls on
http://urlquery.net/report.php?id=1484662181106
and some come up with symcd.com connections
e.g mozilla.org , or hetzner.de
but others not.
So its not my firefox , or is it ? I stopped all certificate checking in FF and others things..
perhaps its a new bug ….?
Nearby , does anyone know why Firefox makes connections double with localhost ?
and this is not explained at mozilla.
http://kb.mozillazine.org/Connections_established_on_startup_-_Firefox
This is the best side : Set all to false.
https://support.mozilla.org/en-US/kb/how-stop-firefox-making-automatic-connections?redirectlocale=en-US&redirectslug=how-stop-firefox-automatically-making-connections