What is ie_to_edge_bho_64.dll?
ie_to_edge_bho_64.dll is part of IEToEdge BHO and developed by Microsoft Corporation according to the ie_to_edge_bho_64.dll version information.
ie_to_edge_bho_64.dll's description is "IEToEdge BHO"
ie_to_edge_bho_64.dll is digitally signed by Microsoft Corporation.
ie_to_edge_bho_64.dll is usually located in the 'C:\Program Files (x86)\Microsoft\Edge\Application\84.0.522.61\BHO\' folder.
None of the anti-virus scanners at VirusTotal reports anything malicious about ie_to_edge_bho_64.dll.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Vendor and version information [?]
The following is the available information on ie_to_edge_bho_64.dll:
| Property | Value |
|---|---|
| Product name | IEToEdge BHO |
| Company name | Microsoft Corporation |
| File description | IEToEdge BHO |
| Internal name | ie_to_edge_bho_64_dll |
| Original filename | ie_to_edge_bho_64.dll |
| Legal copyright | Copyright Microsoft Corporation. All rights reserved. |
| Product version | 84.0.522.61 |
| File version | 84.0.522.61 |
Here's a screenshot of the file properties when displayed by Windows Explorer:
| Product name | IEToEdge BHO |
| Company name | Microsoft Corporation |
| File description | IEToEdge BHO |
| Internal name | ie_to_edge_bho_64_dll |
| Original filename | ie_to_edge_bho_64.dll |
| Legal copyright | Copyright Microsoft Corporation. All.. |
| Product version | 84.0.522.61 |
| File version | 84.0.522.61 |
Digital signatures [?]
ie_to_edge_bho_64.dll has a valid digital signature.
| Property | Value |
|---|---|
| Signer name | Microsoft Corporation |
| Certificate issuer name | Microsoft Code Signing PCA 2011 |
| Certificate serial number | 330000018a073733cf2048893c00000000018a |
VirusTotal report
None of the 68 anti-virus programs at VirusTotal detected the ie_to_edge_bho_64.dll file.
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"dll_loaded": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\b01932b1814e4c96f4add3bdca654cabb4f356b21069dbe234320c3dc353d1b7.bin.dll"
],
"file_opened": [
"C:\\Windows\\System32\\en-US\\KERNELBASE.dll.mui",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\b01932b1814e4c96f4add3bdca654cabb4f356b21069dbe234320c3dc353d1b7.bin.dll"
],
"command_line": [
" C:\\Users\\cuck\\AppData\\Local\\Temp\\b01932b1814e4c96f4add3bdca654cabb4f356b21069dbe234320c3dc353d1b7.bin.dll"
],
"regkey_opened": [
"HKEY_CLASSES_ROOT\\.dll",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\dllfile\\AutoRegister",
"HKEY_CLASSES_ROOT\\dllfile"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\b01932b1814e4c96f4add3bdca654cabb4f356b21069dbe234320c3dc353d1b7.bin.dll"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\.dll\\(Default)"
]
}Generic
[
{
"process_path": "C:\\Windows\\System32\\regsvr32.exe",
"process_name": "regsvr32.exe",
"pid": 856,
"summary": {
"file_opened": [
"C:\\Windows\\System32\\en-US\\KERNELBASE.dll.mui"
],
"regkey_opened": [
"HKEY_CLASSES_ROOT\\.dll",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\dllfile\\AutoRegister",
"HKEY_CLASSES_ROOT\\dllfile"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\.dll\\(Default)"
],
"dll_loaded": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\b01932b1814e4c96f4add3bdca654cabb4f356b21069dbe234320c3dc353d1b7.bin.dll"
]
},
"first_seen": 1598133186.90625,
"ppid": 2800
},
{
"process_path": "C:\\Windows\\SysWOW64\\regsvr32.exe",
"process_name": "regsvr32.exe",
"pid": 2800,
"summary": {
"dll_loaded": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\b01932b1814e4c96f4add3bdca654cabb4f356b21069dbe234320c3dc353d1b7.bin.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\b01932b1814e4c96f4add3bdca654cabb4f356b21069dbe234320c3dc353d1b7.bin.dll"
],
"command_line": [
" C:\\Users\\cuck\\AppData\\Local\\Temp\\b01932b1814e4c96f4add3bdca654cabb4f356b21069dbe234320c3dc353d1b7.bin.dll"
],
"regkey_opened": [
"HKEY_CLASSES_ROOT\\.dll",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\dllfile\\AutoRegister",
"HKEY_CLASSES_ROOT\\dllfile"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\b01932b1814e4c96f4add3bdca654cabb4f356b21069dbe234320c3dc353d1b7.bin.dll"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\.dll\\(Default)"
]
},
"first_seen": 1598133186.671875,
"ppid": 2924
},
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1598133186.328125,
"ppid": 376
}
]Signatures
[
{
"markcount": 1,
"families": [],
"description": "This executable has a PDB path",
"severity": 1,
"marks": [
{
"category": "pdb_path",
"ioc": "ie_to_edge_bho_64.dll.pdb",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "has_pdb"
},
{
"markcount": 3,
"families": [],
"description": "The executable contains unknown PE section names indicative of a packer (could be a false positive)",
"severity": 1,
"marks": [
{
"category": "section",
"ioc": ".00cfg",
"type": "ioc",
"description": null
},
{
"category": "section",
"ioc": ".retplne",
"type": "ioc",
"description": null
},
{
"category": "section",
"ioc": "_RDATA",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "pe_features"
},
{
"markcount": 1,
"families": [],
"description": "The file contains an unknown PE resource name possibly indicative of a packer",
"severity": 1,
"marks": [
{
"category": "resource name",
"ioc": "TYPELIB",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "pe_unknown_resource_name"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 546,
"time": 3.0758798122406006,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 5326,
"time": 3.0400450229644775,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 5654,
"time": 1.0088648796081543,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 5982,
"time": 3.0520269870758057,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 6310,
"time": 1.518009901046753,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 6638,
"time": -0.09951305389404297,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 6966,
"time": 1.5306580066680908,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 16764,
"time": 1.043125867843628,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 25148,
"time": 3.105548858642578,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "cd2d1472588c145be3c21bab73f6d99f74d9ea27a3684eb69886cbc549c10a82",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "6c85a7cc3d15ac1a330f6f893c256ac7327b1d4a836c334e84e6f126083b38b5",
"irc": [],
"https_ex": []
}Screenshots
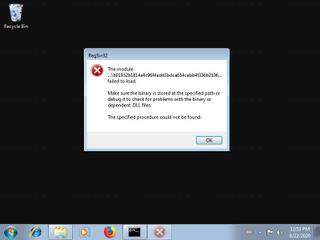
Hashes [?]
| Property | Value |
|---|---|
| MD5 | 56a8a7cdecd2beafb490d3f35ba1d5e9 |
| SHA256 | b01932b1814e4c96f4add3bdca654cabb4f356b21069dbe234320c3dc353d1b7 |
What will you do with the file?
To help other users, please let us know what you will do with the file:
What did other users do?
The poll result listed below shows what users chose to do with the file. 73% have voted for removal. Based on votes from 526 users.
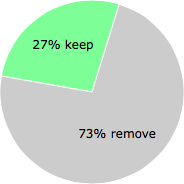
NOTE: Please do not use this poll as the only source of input to determine what you will do with the file.
Malware or legitimate?
If you feel that you need more information to determine if your should keep this file or remove it, please read this guide.
And now some shameless self promotion ;)
 Hi, my name is Roger Karlsson. I've been running this website since 2006. I want to let you know about the FreeFixer program. FreeFixer is a freeware tool that analyzes your system and let you manually identify unwanted programs. Once you've identified some malware files, FreeFixer is pretty good at removing them. You can download FreeFixer here. It runs on Windows 2000/XP/2003/2008/2016/2019/Vista/7/8/8.1/10. Supports both 32- and 64-bit Windows.
Hi, my name is Roger Karlsson. I've been running this website since 2006. I want to let you know about the FreeFixer program. FreeFixer is a freeware tool that analyzes your system and let you manually identify unwanted programs. Once you've identified some malware files, FreeFixer is pretty good at removing them. You can download FreeFixer here. It runs on Windows 2000/XP/2003/2008/2016/2019/Vista/7/8/8.1/10. Supports both 32- and 64-bit Windows.
If you have questions, feedback on FreeFixer or the freefixer.com website, need help analyzing FreeFixer's scan result or just want to say hello, please contact me. You can find my email address at the contact page.
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
Tony Montana writes
i think the file function is for the reveal something about users
}remember the new reality of digital world is like a new hegemonic power that wants see everything
for pleasure or punishment
i think the diversity of subjetivities is amazing but the control maybe is a something moral or neoliberalist development around the power of minds pretends control the traffic or consume or whatever in pro capitalistic production, the last think maybe is a potenciality of us, but each human have diferent sense of life and i think we need more freedom more lonelyness because the privacity is a myth or they want something data, i dont have anything and im only o poor man with desire and life ,, much sense of humor or whatever do you wants, but , the malware is a devil viruses are like badguys in the virtual life.but no meaning anything, the systems have a lot of duplicates ,,.. the problem is own freedom we are in the center of the eyes of the programmers the Coding mens or women like a new nazis around here, and i a pagan guy hunted for the christians hackers
# 9 Jun 2021, 12:32
free man writes
fuck this pop up it forcing to accept this program https://support.microsoft.com/en-us/topic/this-website-works-better-in-microsoft-edge-160fa918-d581-4932-9e4e-1075c4713595?ui=en-us&rs=en-us&ad=us
# 31 Aug 2021, 18:00
Chuckwagon CHili writes
Hello My Love, may our egos be ever deflated as we look at the control that wishes =/ has been taken over the lives of others.... shame on us all... Tisk Tisk...
P.S. Happy Saturday
# 20 Nov 2021, 3:45
HollowSoul writes
From what I heard this .dll is to redirect those of you who still use IE to use edge.That's it nothing more nothing less
# 23 Jan 2022, 2:21
PrinceThaDon writes
Dr. Dean Preacher Kantrel Ghones-Prince
BexarCountyPetition2018
# 22 Mar 2022, 9:15
CAP.GUILE writes
Estimados: IE (ojalá) dejará de existir en julio del 22. Mi pregunta es: ¿Realmente es necesario habilitar este complemento? El mismo IE me solicitó "frenarlo" por tardar demasiado en ejecutarse. Hay sitios, aún no sé por qué tienen que abrir en IE. Ej. "Ayuda de WinRAR, informes de AMD, y varios otros". Los que critican el uso de EDGE Chromium, deben saber que Chrome hace exactamente lo mismo. No puedo decir que Firefox, Opera, etc lo hagan. Pueden desinstalarlo con Iobit Unistaller o lo que les guste, pero prepárense a reinstalar de 0 Win 10 en mi caso. Ningún Script funcionará. Chau PC o Notebook o Netbook o Talent MSX. SALUD! -os. Cap. Guile, La Plata, Argentina. -
# 3 May 2022, 0:33
Glen writes
How Do You Remove This ie_to_edge_bho_64.dll? It's An ad on or extension, but it doesn't give me an option to remove it. I don't like it. I did not ask for it, and I don't even know how I got it. It just showed up one day, and I have had tons of trouble with my computer ever since. I don't know what it is, but I can tell you it's no good.
# 6 Jun 2022, 11:46
Greg Fanara writes
For some reason my corporate laptop has a shell windows installed and the path led me here. Looks like it was created for some pathetic "cuck". Not sure how or why it's on my laptop. Could the loser who wrote this uncuck himself, pull the dildo out of his ass, be a man, and directly contact me?
gregoryfanara@outlook.com
# 7 Jul 2022, 17:15
Shawn Standish CEO of SDRS Excel writes
This unauthorized evasive program from Microsoft is a lawsuit waiting to happen !!!!!
# 26 Nov 2022, 19:01
Rox writes
This unauthorized, evasive, and misleading program presents as a legitimate Microsoft program deserves to be looked into for copyright infringement
# 14 Apr 2023, 19:46

wwwww writes