What is sJg2e3U.exe?
sJg2e3U.exe is part of Microsoft(R) Windows Media Player and developed by Microsoft Corporation according to the sJg2e3U.exe version information.
sJg2e3U.exe's description is "Microsoft Windows Setup Utility"
sJg2e3U.exe is usually located in the 'c:\downloads\' folder.
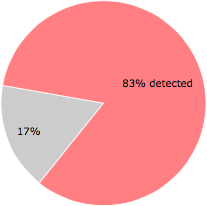
Some of the anti-virus scanners at VirusTotal detected sJg2e3U.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Vendor and version information [?]
The following is the available information on sJg2e3U.exe:
| Property | Value |
|---|---|
| Product name | Microsoft(R) Windows Media Player |
| Company name | Microsoft Corporation |
| File description | Microsoft Windows Setup Utility |
| Internal name | a6ize |
| Original filename | a6ize |
| Legal copyright | (C) Microsoft Corporation. All rights reserved. |
| Product version | 9.00.00.4503 |
| File version | 9.00.00.4503 |
Here's a screenshot of the file properties when displayed by Windows Explorer:
| Product name | Microsoft(R) Windows Media Player |
| Company name | Microsoft Corporation |
| File description | Microsoft Windows Setup Utility |
| Internal name | a6ize |
| Original filename | a6ize |
| Legal copyright | (C) Microsoft Corporation. All righ.. |
| Product version | 9.00.00.4503 |
| File version | 9.00.00.4503 |
Digital signatures [?]
sJg2e3U.exe is not signed.
VirusTotal report
57 of the 69 anti-virus programs at VirusTotal detected the sJg2e3U.exe file. That's a 83% detection rate.
| Scanner | Detection Name |
|---|---|
| Acronis | suspicious |
| Ad-Aware | Trojan.FakeAlert.DEO |
| AegisLab | Trojan.Win32.Generic.lIty |
| AhnLab-V3 | Spyware/Win32.Zbot.R52532 |
| ALYac | Trojan.FakeAlert.DEO |
| Antiy-AVL | Trojan[Spy]/Win32.Zbot |
| Arcabit | Trojan.FakeAlert.DEO |
| Avast | Win32:GenMalicious-IGS [Trj] |
| AVG | Win32:GenMalicious-IGS [Trj] |
| Avira | TR/PSW.ZBot.JH.12 |
| BitDefender | Trojan.FakeAlert.DEO |
| Bkav | HW32.Packed. |
| CAT-QuickHeal | TrojanPWS.Zbot.Gen |
| Comodo | TrojWare.Win32.Kryptik.BHBD@50lrjl |
| CrowdStrike | win/malicious_confidence_100% (W) |
| Cybereason | malicious.1de3f6 |
| Cylance | Unsafe |
| Cyren | W32/Zbot.HS.gen!Eldorado |
| DrWeb | Trojan.PWS.Panda.3629 |
| Emsisoft | Trojan.FakeAlert.DEO (B) |
| Endgame | malicious (high confidence) |
| ESET-NOD32 | Win32/Spy.Zbot.AAU |
| F-Prot | W32/Zbot.HS.gen!Eldorado |
| F-Secure | Trojan.TR/PSW.ZBot.JH.12 |
| Fortinet | W32/Zbot.AAU!tr |
| GData | Trojan.FakeAlert.DEO |
| Ikarus | Trojan-PWS.Win32.Zbot |
| Invincea | heuristic |
| Jiangmin | Trojan.Generic.cwyqz |
| K7AntiVirus | Trojan ( 0040f0ce1 ) |
| K7GW | Trojan-Downloader ( 0040f0ce1 ) |
| Kaspersky | HEUR:Trojan.Win32.Generic |
| Malwarebytes | Trojan.FakeMS.ED |
| MAX | malware (ai score=100) |
| McAfee | PWS-Zbot-FAKU!B2834931DE3F |
| McAfee-GW-Edition | PWS-Zbot-FAKU!B2834931DE3F |
| Microsoft | PWS:Win32/Zbot!GO |
| MicroWorld-eScan | Trojan.FakeAlert.DEO |
| NANO-Antivirus | Trojan.Win32.Zbot.bobpso |
| Paloalto | generic.ml |
| Panda | Trj/Hexas.HEU |
| Qihoo-360 | HEUR/Malware.QVM20.Gen |
| Rising | Spyware.Zbot!8.16B (RDM+:cmRtazoYPjgrHhGmTXEuLj/2Y943) |
| SentinelOne | DFI - Malicious PE |
| Sophos | Troj/Zbot-DTV |
| SUPERAntiSpyware | Trojan.Agent/Gen-Zbot |
| Symantec | Trojan.Zbot!gen39 |
| TACHYON | Trojan-Spy/W32.ZBot.347648.O |
| Tencent | Win32.Trojan.Psw.Pefj |
| TheHacker | Trojan/Spy.Zbot.aau |
| Trapmine | malicious.high.ml.score |
| TrendMicro-HouseCall | TSPY_ZBOT.SM20 |
| VBA32 | Malware-Cryptor.SB.01798 |
| Webroot | W32.Rogue.Gen |
| Yandex | Trojan.Agent!gYiAMuD/ZOU |
| Zillya | Trojan.Zbot.Win32.103666 |
| ZoneAlarm | HEUR:Trojan.Win32.Generic |
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"file_created": [
"C:\\Users\\cuck\\AppData\\LocalLow\\itduw.isa",
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\tmp8edbb27e.bat",
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
],
"file_recreated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\tmp8edbb27e.bat"
],
"regkey_written": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\GroupByKey:FMTID",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\BagMRU\\NodeSlots",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2ge3bij4",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\IconSize",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\FFlags",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\BagMRU\\MRUListEx",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\Sort",
"HKEY_CURRENT_USER\\Local Settings\\Software\\Microsoft\\Windows\\CurrentVersion\\TrayNotify\\IconStreams",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\ColInfo",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\GroupByDirection",
"HKEY_CURRENT_USER\\Local Settings\\Software\\Microsoft\\Windows\\CurrentVersion\\TrayNotify\\LastAdvertisement",
"HKEY_CURRENT_USER\\Local Settings\\Software\\Microsoft\\Windows\\CurrentVersion\\TrayNotify\\PastIconsStream",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\GroupView",
"HKEY_CURRENT_USER\\Local Settings\\Software\\Microsoft\\Windows\\CurrentVersion\\TrayNotify\\UserStartTime",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2d3fb83i",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\StuckRects2\\Settings",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\GroupByKey:PID",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\LogicalViewMode",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\Mode",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Streams\\Desktop\\TaskbarWinXP",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\1d3i9fei"
],
"dll_loaded": [
"NETAPI32.dll",
"CRYPT32.dll",
"kernel32.dll",
"msvcrt.dll",
"ntdll.dll",
"WININET.dll",
"Secur32.dll",
"ole32.dll",
"SHLWAPI.dll",
"CRYPTSP.dll",
"USER32.dll",
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"IPHLPAPI.DLL",
"C:\\Windows\\system32\\xmllite.dll",
"OLEAUT32.dll",
"profapi.dll",
"SHELL32.dll",
"VERSION.dll",
"KERNEL32.dll",
"GDI32.dll",
"ADVAPI32.dll",
"rpcrt4.dll",
"WS2_32.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe",
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo",
"C:\\Users\\cuck\\AppData\\LocalLow",
"C:\\Users\\cuck\\AppData\\Roaming",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\dd712e661dd0d4854be9a37fa4e2b7ba6f167c3c49e7b4ad63ce35067a578f26.bin"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_LOCAL_MACHINE\\ ",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\FolderDescriptions",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\StuckRects2",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\OLE\\Tracing",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\crypt32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Interface\\{00000140-0000-0000-c000-000000000046}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_CURRENT_USER\\Software\\Microsoft",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Currentversion\\Run",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\SessionInfo\\1\\KnownFolders",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLEAUT",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc\\SecurityService",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\SessionInfo\\1"
],
"command_line": [
"\"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe\"",
"\"C:\\Windows\\system32\\cmd.exe\" \/c \"C:\\Users\\cuck\\AppData\\Local\\Temp\\tmp8edbb27e.bat\""
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\tmp8edbb27e.bat",
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
],
"regkey_deleted": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\GroupCollapseState",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\ItemOrder",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\internat.exe",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\ItemPos800x600x96(1)"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\LocalLow",
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe",
"C:\\Users\\cuck\\Desktop",
"C:\\",
"C:\\Users\\cuck\\AppData\\Roaming"
],
"mutex": [
"Local\\{C8B94219-59B7-4B5C-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-3CEB-B06E2E0B9373}",
"Global\\{DA88BBAC-A002-596D-48EE-B06E5A0E9373}",
"Global\\{56060262-19CC-D5E3-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-28E0-B06E3A009373}",
"Global\\{DA88BBAC-A002-596D-80EB-B06E920B9373}",
"Global\\{DA88BBAC-A002-596D-8CEC-B06E9E0C9373}",
"Global\\{DA88BBAC-A002-596D-E0E0-B06EF2009373}",
"Global\\{DA88BBAC-A002-596D-74ED-B06E660D9373}",
"Global\\{DA88BBAC-A002-596D-FCEB-B06EEE0B9373}",
"Global\\{DA88BBAC-A002-596D-6CEE-B06E7E0E9373}",
"Global\\{A5B32338-3896-2656-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-CCEB-B06EDE0B9373}",
"Global\\{DA88BBAC-A002-596D-A8EB-B06EBA0B9373}",
"Global\\{DA88BBAC-A002-596D-F4EB-B06EE60B9373}",
"Global\\{DA88BBAC-A002-596D-68ED-B06E7A0D9373}",
"Global\\{DA88BBAC-A002-596D-E0E8-B06EF2089373}",
"Global\\{DA88BBAC-A002-596D-24EC-B06E360C9373}",
"Global\\{DA88BBAC-A002-596D-D0E1-B06EC2019373}",
"Global\\{DA88BBAC-A002-596D-0CE9-B06E1E099373}",
"Global\\{DA88BBAC-A002-596D-E8EE-B06EFA0E9373}",
"Global\\{DA88BBAC-A002-596D-B4EC-B06EA60C9373}",
"Global\\{73B5150B-0EA5-F050-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-84E1-B06E96019373}",
"Global\\{A95FF40D-EFA3-2ABA-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-58E9-B06E4A099373}",
"Global\\{DA88BBAC-A002-596D-2CEA-B06E3E0A9373}",
"Global\\{DA88BBAC-A002-596D-04E9-B06E16099373}",
"Global\\{C3671720-0C8E-4082-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-14EE-B06E060E9373}",
"Global\\{DA88BBAC-A002-596D-D4EA-B06EC60A9373}",
"Global\\{DA88BBAC-A002-596D-50EB-B06E420B9373}",
"Global\\{DA88BBAC-A002-596D-C0EF-B06ED20F9373}",
"Global\\{DA88BBAC-A002-596D-BCE8-B06EAE089373}",
"Global\\{DA88BBAC-A002-596D-C0E9-B06ED2099373}",
"Local\\Shell.CMruPidlList",
"Global\\{DA88BBAC-A002-596D-DCEE-B06ECE0E9373}",
"Global\\{DA88BBAC-A002-596D-60EB-B06E720B9373}",
"Global\\{A95FF40A-EFA4-2ABA-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-78E8-B06E6A089373}",
"Global\\{DA88BBAC-A002-596D-50E2-B06E42029373}",
"Local\\{E91F2729-3C87-6AFA-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-0CEF-B06E1E0F9373}",
"Global\\{DA88BBAC-A002-596D-94EC-B06E860C9373}",
"Global\\{DA88BBAC-A002-596D-D4EC-B06EC60C9373}",
"Local\\{C8B94218-59B6-4B5C-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-C8EB-B06EDA0B9373}",
"Global\\{DA88BBAC-A002-596D-C0EC-B06ED20C9373}",
"Global\\{DA88BBAC-A002-596D-4CEC-B06E5E0C9373}"
],
"file_failed": [
"C:\\Users\\cuck\\AppData\\LocalLow\\itduw.isa.dat"
],
"guid": [
"{9b63616c-36b2-46bc-959f-c1593952d19b}",
"{1a1f4206-0688-4e7f-be03-d82ec69df9a5}",
"{e0483ba0-47ff-4d9c-a6d6-7741d0b195f7}",
"{42aedc87-2188-41fd-b9a3-0c966feabec1}",
"{0ca545c6-37ad-4a6c-bf92-9f7610067ef5}",
"{f7898af5-cac4-4632-a2ec-da06e5111af2}",
"{304ce942-6e39-40d8-943a-b913c40c9cd4}",
"{2fb499a3-cfce-480f-a5f3-2453db7a2b7a}"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\dd712e661dd0d4854be9a37fa4e2b7ba6f167c3c49e7b4ad63ce35067a578f26.bin"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Icon",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\BagMRU\\NodeSlot",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Stream",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\HideDrivesWithNoMedia",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\BagMRU Size",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\DigitalProductId",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\DisableImprovedZoneCheck",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Close\\.Current\\Default Flags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\LocalizedName",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\1bf0deg7",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Security",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\1d3i9fei",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\ParsingName",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Open\\.Current\\Default Flags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DebugHeapFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\PreCreate",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2225de0b",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\SecurityService\\DefaultAuthLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\ClearRecentDocsOnExit",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Category",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\26dc4g9h",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\FolderTypeID",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2bie43db",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PublishExpandedPath",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2d3fb83i",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Open\\.Current\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Roamable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\StreamResource",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\184992eh",
"HKEY_CURRENT_USER\\Local Settings\\Software\\Microsoft\\Windows\\CurrentVersion\\TrayNotify\\PromotedIconCache",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\LocalRedirectOnly",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Close\\.Current\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorSystemHeapIsPrivate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Security_HKLM_only",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorUseSystemHeap",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\InstallDate",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\319341cj",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2ge3bij4",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\BagMRU\\MRUListEx",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Description",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\NeverShowDrivesMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\shellex\\FolderExtensions\\{fbeb8a05-beee-4442-804e-409d6c4515e9}\\DriveMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\BagMRU\\NodeSlots",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\AppData",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PreCreate",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\_LabelFromReg",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\ParentFolder",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\InitFolderHandler"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData\\LocalLow\\*.277e56a4"
],
"directory_created": [
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo"
]
}Dropped
[
{
"yara": [],
"sha1": "78f2960a40d112c786e920e1e22e2802777534c4",
"name": "50f6811af53a89ac_uwpy.exe",
"filepath": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe",
"type": "PE32 executable (GUI) Intel 80386, for MS Windows",
"sha256": "50f6811af53a89ac3840c09d618a83c9e73257bc8734fb39903f62283ea74462",
"urls": [],
"crc32": "B28302C2",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/5867\/files\/50f6811af53a89ac_uwpy.exe",
"ssdeep": null,
"size": 347648,
"sha512": "06cb6190aeda65ff64e634c016bd628adba8a71dbc2719bacfdc830b16d18f3b06678ed709dd88a9dca6ecba3284e83462248c437b9f3906e834e34341e2cc65",
"pids": [
1268
],
"md5": "9e7f7770e3b367e64dd9df1eba0ece84"
},
{
"yara": [],
"sha1": "da39a3ee5e6b4b0d3255bfef95601890afd80709",
"name": "e3b0c44298fc1c14_uwpy.exe",
"type": "empty",
"sha256": "e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855",
"urls": [],
"crc32": "00000000",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/5867\/files\/e3b0c44298fc1c14_uwpy.exe",
"ssdeep": null,
"size": 0,
"sha512": "cf83e1357eefb8bdf1542850d66d8007d620e4050b5715dc83f4a921d36ce9ce47d0d13c5d85f2b0ff8318d2877eec2f63b931bd47417a81a538327af927da3e",
"md5": "d41d8cd98f00b204e9800998ecf8427e"
}
]Generic
[
{
"process_path": "C:\\Windows\\System32\\mobsync.exe",
"process_name": "mobsync.exe",
"pid": 1092,
"summary": {
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles"
]
},
"first_seen": 1583416395.01475,
"ppid": 592
},
{
"process_path": "C:\\Windows\\System32\\cmd.exe",
"process_name": "cmd.exe",
"pid": 1692,
"summary": {},
"first_seen": 1583416388.796,
"ppid": 1788
},
{
"process_path": "C:\\Windows\\System32\\taskhost.exe",
"process_name": "taskhost.exe",
"pid": 1724,
"summary": {
"regkey_read": [
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\(Default)",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Close\\.Current\\Default Flags",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Close\\.Current\\(Default)",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Open\\.Current\\(Default)",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Open\\.Current\\Default Flags"
],
"regkey_deleted": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\internat.exe"
]
},
"first_seen": 1583416387.76475,
"ppid": 468
},
{
"process_path": "C:\\Windows\\System32\\mobsync.exe",
"process_name": "mobsync.exe",
"pid": 1636,
"summary": {
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles"
]
},
"first_seen": 1583416389.186626,
"ppid": 592
},
{
"process_path": "C:\\Windows\\System32\\dwm.exe",
"process_name": "dwm.exe",
"pid": 1768,
"summary": {},
"first_seen": 1583416388.030375,
"ppid": 804
},
{
"process_path": "C:\\Windows\\explorer.exe",
"process_name": "explorer.exe",
"pid": 1788,
"summary": {
"regkey_written": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\FFlags",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\GroupByDirection",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\BagMRU\\MRUListEx",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\StuckRects2\\Settings",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\Sort",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\LogicalViewMode",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\Mode",
"HKEY_CURRENT_USER\\Local Settings\\Software\\Microsoft\\Windows\\CurrentVersion\\TrayNotify\\UserStartTime",
"HKEY_CURRENT_USER\\Local Settings\\Software\\Microsoft\\Windows\\CurrentVersion\\TrayNotify\\LastAdvertisement",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\GroupView",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\ColInfo",
"HKEY_CURRENT_USER\\Local Settings\\Software\\Microsoft\\Windows\\CurrentVersion\\TrayNotify\\IconStreams",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\GroupByKey:FMTID",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\BagMRU\\NodeSlots",
"HKEY_CURRENT_USER\\Local Settings\\Software\\Microsoft\\Windows\\CurrentVersion\\TrayNotify\\PastIconsStream",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Streams\\Desktop\\TaskbarWinXP",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\IconSize",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\GroupByKey:PID"
],
"dll_loaded": [
"C:\\Windows\\system32\\xmllite.dll"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\StuckRects2"
],
"regkey_deleted": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\GroupCollapseState",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\ItemOrder",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Bags\\1\\Desktop\\ItemPos800x600x96(1)"
],
"file_exists": [
"C:\\Users\\cuck\\Desktop",
"C:\\"
],
"mutex": [
"Local\\Shell.CMruPidlList"
],
"guid": [
"{9b63616c-36b2-46bc-959f-c1593952d19b}",
"{1a1f4206-0688-4e7f-be03-d82ec69df9a5}",
"{2fb499a3-cfce-480f-a5f3-2453db7a2b7a}",
"{42aedc87-2188-41fd-b9a3-0c966feabec1}"
],
"regkey_read": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\BagMRU\\NodeSlot",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\BagMRU\\MRUListEx",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\ClearRecentDocsOnExit",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\HideDrivesWithNoMedia",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\NeverShowDrivesMask",
"HKEY_CURRENT_USER\\Local Settings\\Software\\Microsoft\\Windows\\CurrentVersion\\TrayNotify\\PromotedIconCache",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\BagMRU\\NodeSlots",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\shellex\\FolderExtensions\\{fbeb8a05-beee-4442-804e-409d6c4515e9}\\DriveMask",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\BagMRU Size",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\_LabelFromReg"
]
},
"first_seen": 1583416388.249125,
"ppid": 1740
},
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\dd712e661dd0d4854be9a37fa4e2b7ba6f167c3c49e7b4ad63ce35067a578f26.bin",
"process_name": "dd712e661dd0d4854be9a37fa4e2b7ba6f167c3c49e7b4ad63ce35067a578f26.bin",
"pid": 1268,
"summary": {
"file_created": [
"C:\\Users\\cuck\\AppData\\LocalLow\\itduw.isa",
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\tmp8edbb27e.bat",
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
],
"file_recreated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\tmp8edbb27e.bat"
],
"directory_created": [
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo"
],
"dll_loaded": [
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"profapi.dll",
"rpcrt4.dll",
"IPHLPAPI.DLL",
"KERNEL32.dll",
"GDI32.dll",
"WININET.dll",
"SHELL32.dll",
"kernel32.dll",
"msvcrt.dll",
"Secur32.dll",
"CRYPT32.dll",
"NETAPI32.dll",
"VERSION.dll",
"ADVAPI32.dll",
"ntdll.dll",
"ole32.dll",
"SHLWAPI.dll",
"WS2_32.dll",
"USER32.dll",
"OLEAUT32.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe",
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo",
"C:\\Users\\cuck\\AppData\\LocalLow",
"C:\\Users\\cuck\\AppData\\Roaming",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\dd712e661dd0d4854be9a37fa4e2b7ba6f167c3c49e7b4ad63ce35067a578f26.bin"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_LOCAL_MACHINE\\ ",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\FolderDescriptions",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\OLE\\Tracing",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\crypt32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Interface\\{00000140-0000-0000-c000-000000000046}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_CURRENT_USER\\Software\\Microsoft",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\SessionInfo\\1\\KnownFolders",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLEAUT",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\SessionInfo\\1"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\tmp8edbb27e.bat",
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\LocalLow",
"C:\\Users\\cuck\\AppData\\Roaming",
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
],
"mutex": [
"Global\\{56060262-19CC-D5E3-A920-6470BBC0476D}",
"Global\\{C3671720-0C8E-4082-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-84E1-B06E96019373}"
],
"file_failed": [
"C:\\Users\\cuck\\AppData\\LocalLow\\itduw.isa.dat"
],
"command_line": [
"\"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe\"",
"\"C:\\Windows\\system32\\cmd.exe\" \/c \"C:\\Users\\cuck\\AppData\\Local\\Temp\\tmp8edbb27e.bat\""
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\dd712e661dd0d4854be9a37fa4e2b7ba6f167c3c49e7b4ad63ce35067a578f26.bin"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorUseSystemHeap",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\ParsingName",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Description",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DebugHeapFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Description",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\InstallDate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\InfoTip",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2d3fb83i",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\DisableImprovedZoneCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\DigitalProductId",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PreCreate",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\AppData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorSystemHeapIsPrivate",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Security_HKLM_only"
],
"regkey_written": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2d3fb83i"
]
},
"first_seen": 1583416385.796,
"ppid": 2724
},
{
"process_path": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe",
"process_name": "uwpy.exe",
"pid": 2872,
"summary": {
"regkey_written": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2ge3bij4",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\1d3i9fei"
],
"dll_loaded": [
"NETAPI32.dll",
"CRYPT32.dll",
"KERNEL32.dll",
"msvcrt.dll",
"ntdll.dll",
"WININET.dll",
"Secur32.dll",
"ole32.dll",
"SHLWAPI.dll",
"CRYPTSP.dll",
"USER32.dll",
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"IPHLPAPI.DLL",
"OLEAUT32.dll",
"profapi.dll",
"SHELL32.dll",
"VERSION.dll",
"kernel32.dll",
"GDI32.dll",
"ADVAPI32.dll",
"rpcrt4.dll",
"WS2_32.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_LOCAL_MACHINE\\ ",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\FolderDescriptions",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\OLE\\Tracing",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\crypt32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Interface\\{00000140-0000-0000-c000-000000000046}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Currentversion\\Run",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\SessionInfo\\1\\KnownFolders",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLEAUT",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PropertyBag",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc\\SecurityService",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\SessionInfo\\1"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\LocalLow",
"C:\\Users\\cuck\\AppData\\Roaming"
],
"mutex": [
"Local\\{C8B94219-59B7-4B5C-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-3CEB-B06E2E0B9373}",
"Global\\{DA88BBAC-A002-596D-48EE-B06E5A0E9373}",
"Global\\{DA88BBAC-A002-596D-28E0-B06E3A009373}",
"Global\\{DA88BBAC-A002-596D-80EB-B06E920B9373}",
"Global\\{DA88BBAC-A002-596D-8CEC-B06E9E0C9373}",
"Global\\{DA88BBAC-A002-596D-E0E0-B06EF2009373}",
"Global\\{DA88BBAC-A002-596D-74ED-B06E660D9373}",
"Global\\{DA88BBAC-A002-596D-FCEB-B06EEE0B9373}",
"Global\\{DA88BBAC-A002-596D-6CEE-B06E7E0E9373}",
"Global\\{A5B32338-3896-2656-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-CCEB-B06EDE0B9373}",
"Global\\{DA88BBAC-A002-596D-A8EB-B06EBA0B9373}",
"Global\\{DA88BBAC-A002-596D-F4EB-B06EE60B9373}",
"Global\\{DA88BBAC-A002-596D-68ED-B06E7A0D9373}",
"Global\\{DA88BBAC-A002-596D-E0E8-B06EF2089373}",
"Global\\{DA88BBAC-A002-596D-24EC-B06E360C9373}",
"Global\\{DA88BBAC-A002-596D-D0E1-B06EC2019373}",
"Global\\{DA88BBAC-A002-596D-0CE9-B06E1E099373}",
"Global\\{DA88BBAC-A002-596D-E8EE-B06EFA0E9373}",
"Global\\{DA88BBAC-A002-596D-B4EC-B06EA60C9373}",
"Global\\{73B5150B-0EA5-F050-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-DCEE-B06ECE0E9373}",
"Global\\{A95FF40D-EFA3-2ABA-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-58E9-B06E4A099373}",
"Global\\{DA88BBAC-A002-596D-2CEA-B06E3E0A9373}",
"Global\\{DA88BBAC-A002-596D-04E9-B06E16099373}",
"Global\\{DA88BBAC-A002-596D-14EE-B06E060E9373}",
"Global\\{DA88BBAC-A002-596D-D4EA-B06EC60A9373}",
"Global\\{DA88BBAC-A002-596D-50EB-B06E420B9373}",
"Global\\{DA88BBAC-A002-596D-C0EF-B06ED20F9373}",
"Global\\{DA88BBAC-A002-596D-BCE8-B06EAE089373}",
"Global\\{DA88BBAC-A002-596D-C0E9-B06ED2099373}",
"Global\\{DA88BBAC-A002-596D-60EB-B06E720B9373}",
"Global\\{A95FF40A-EFA4-2ABA-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-78E8-B06E6A089373}",
"Global\\{DA88BBAC-A002-596D-50E2-B06E42029373}",
"Local\\{E91F2729-3C87-6AFA-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-0CEF-B06E1E0F9373}",
"Global\\{DA88BBAC-A002-596D-94EC-B06E860C9373}",
"Global\\{DA88BBAC-A002-596D-D4EC-B06EC60C9373}",
"Local\\{C8B94218-59B6-4B5C-A920-6470BBC0476D}",
"Global\\{DA88BBAC-A002-596D-C8EB-B06EDA0B9373}",
"Global\\{DA88BBAC-A002-596D-C0EC-B06ED20C9373}",
"Global\\{DA88BBAC-A002-596D-4CEC-B06E5E0C9373}"
],
"guid": [
"{0ca545c6-37ad-4a6c-bf92-9f7610067ef5}",
"{f7898af5-cac4-4632-a2ec-da06e5111af2}",
"{e0483ba0-47ff-4d9c-a6d6-7741d0b195f7}",
"{304ce942-6e39-40d8-943a-b913c40c9cd4}"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
],
"regkey_read": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\184992eh",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\SecurityService\\DefaultAuthLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorUseSystemHeap",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\ParsingName",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2ge3bij4",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\LocalRedirectOnly",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2bie43db",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\26dc4g9h",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Description",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DebugHeapFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Description",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\319341cj",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\FolderTypeID",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2225de0b",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\InfoTip",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\2d3fb83i",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\DisableImprovedZoneCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PreCreate",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\AppData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorSystemHeapIsPrivate",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\LocalizedName",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\1bf0deg7",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{A520A1A4-1780-4FF6-BD18-167343C5AF16}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Security_HKLM_only",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Ruec\\1d3i9fei"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData\\LocalLow\\*.277e56a4"
]
},
"first_seen": 1583416386.655375,
"ppid": 1268
},
{
"process_path": "C:\\Windows\\System32\\conhost.exe",
"process_name": "conhost.exe",
"pid": 1700,
"summary": {},
"first_seen": 1583416388.983501,
"ppid": 384
},
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1583416385.3125,
"ppid": 376
}
]Signatures
[
{
"markcount": 1,
"families": [],
"description": "Queries for the computername",
"severity": 1,
"marks": [
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1583416386.483,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5163
}
],
"references": [],
"name": "antivm_queries_computername"
},
{
"markcount": 2,
"families": [],
"description": "Collects information to fingerprint the system (MachineGuid, DigitalProductId, SystemBiosDate)",
"severity": 1,
"marks": [
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\DigitalProductId",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\InstallDate",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "recon_fingerprint"
},
{
"markcount": 1,
"families": [],
"description": "Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "GlobalMemoryStatusEx",
"return_value": 1,
"arguments": {},
"time": 1583416386.437,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5000
}
],
"references": [],
"name": "antivm_memory_available"
},
{
"markcount": 0,
"families": [],
"description": "One or more potentially interesting buffers were extracted, these generally contain injected code, configuration data, etc.",
"severity": 2,
"marks": [],
"references": [],
"name": "dumped_buffer"
},
{
"markcount": 37,
"families": [],
"description": "Allocates read-write-execute memory (usually to unpack itself)",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"region_size": 282624,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x00460000"
},
"time": 1583416385.874,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 1268,
"type": "call",
"cid": 2
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003d0000"
},
"time": 1583416385.874,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 1268,
"type": "call",
"cid": 4
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x004b0000"
},
"time": 1583416385.874,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 1268,
"type": "call",
"cid": 5
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x01d40000"
},
"time": 1583416386.265,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 1268,
"type": "call",
"cid": 4588
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x00418000"
},
"time": 1583416386.483,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5152
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x00418000"
},
"time": 1583416386.483,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5153
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"region_size": 65536,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x63db0000"
},
"time": 1583416389.452,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 1268,
"type": "call",
"cid": 5576
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63dec000"
},
"time": 1583416389.452,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5577
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63dec000"
},
"time": 1583416389.452,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5578
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63deb000"
},
"time": 1583416389.452,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5579
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63dec000"
},
"time": 1583416389.468,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5580
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63deb000"
},
"time": 1583416389.468,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5581
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x77317000"
},
"time": 1583416389.468,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5582
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x75710000"
},
"time": 1583416389.468,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5583
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63de5000"
},
"time": 1583416389.468,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5584
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63de5000"
},
"time": 1583416389.468,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5585
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 65536,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63db0000"
},
"time": 1583416389.468,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5598
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763a7000"
},
"time": 1583416389.468,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5599
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763e9000"
},
"time": 1583416389.468,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5600
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 65536,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63db0000"
},
"time": 1583416389.468,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5604
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x75fa0000"
},
"time": 1583416389.483,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5605
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 65536,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63db0000"
},
"time": 1583416389.483,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5608
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63deb000"
},
"time": 1583416389.483,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5609
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63dec000"
},
"time": 1583416389.483,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5610
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x77314000"
},
"time": 1583416389.483,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5611
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x77314000"
},
"time": 1583416389.483,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5612
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63dec000"
},
"time": 1583416389.483,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5613
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63dec000"
},
"time": 1583416389.483,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5614
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x77314000"
},
"time": 1583416389.483,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5615
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 65536,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63db0000"
},
"time": 1583416389.515,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5620
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63dde000"
},
"time": 1583416389.515,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5623
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 65536,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63db0000"
},
"time": 1583416389.515,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5626
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x63ddd000"
},
"time": 1583416389.515,
"tid": 552,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 5627
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2872,
"region_size": 282624,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x00460000"
},
"time": 1583416386.718375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 2
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2872,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003d0000"
},
"time": 1583416386.718375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 4
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2872,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x004b0000"
},
"time": 1583416386.718375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2872,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x00500000"
},
"time": 1583416386.999375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 4588
}
],
"references": [],
"name": "allocates_rwx"
},
{
"markcount": 0,
"families": [],
"description": "Checks whether any human activity is being performed by constantly checking whether the foreground window changed",
"severity": 2,
"marks": [],
"references": [
"https:\/\/www.virusbtn.com\/virusbulletin\/archive\/2015\/09\/vb201509-custom-packer.dkb"
],
"name": "antisandbox_foregroundwindows"
},
{
"markcount": 1,
"families": [],
"description": "Creates hidden or system file",
"severity": 2,
"marks": [
{
"call": {
"category": "file",
"status": 1,
"stacktrace": [],
"api": "NtCreateFile",
"return_value": 0,
"arguments": {
"create_disposition": 2,
"file_handle": "0x00000138",
"filepath": "C:\\Users\\cuck\\AppData\\LocalLow\\itduw.isa",
"desired_access": "0xc0110080",
"file_attributes": 2,
"filepath_r": "\\??\\C:\\Users\\cuck\\AppData\\LocalLow\\itduw.isa",
"create_options": 4192,
"status_info": 2,
"share_access": 0
},
"time": 1583416386.483,
"tid": 2740,
"flags": {
"create_disposition": "FILE_CREATE",
"desired_access": "FILE_READ_ATTRIBUTES|DELETE|SYNCHRONIZE|GENERIC_WRITE",
"create_options": "FILE_NON_DIRECTORY_FILE|FILE_SYNCHRONOUS_IO_NONALERT|FILE_DELETE_ON_CLOSE",
"file_attributes": "FILE_ATTRIBUTE_HIDDEN",
"status_info": "FILE_CREATED",
"share_access": ""
}
},
"pid": 1268,
"type": "call",
"cid": 5173
}
],
"references": [],
"name": "creates_hidden_file"
},
{
"markcount": 1,
"families": [],
"description": "Creates a suspicious process",
"severity": 2,
"marks": [
{
"category": "cmdline",
"ioc": "\"C:\\Windows\\system32\\cmd.exe\" \/c \"C:\\Users\\cuck\\AppData\\Local\\Temp\\tmp8edbb27e.bat\"",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "suspicious_process"
},
{
"markcount": 1,
"families": [],
"description": "Drops an executable to the user AppData folder",
"severity": 2,
"marks": [
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "exe_appdata"
},
{
"markcount": 2,
"families": [],
"description": "The binary likely contains encrypted or compressed data indicative of a packer",
"severity": 2,
"marks": [
{
"entropy": 6.952969544322912,
"section": {
"size_of_data": "0x00052200",
"virtual_address": "0x00003000",
"entropy": 6.952969544322912,
"name": ".data",
"virtual_size": "0x0005210c"
},
"type": "generic",
"description": "A section with a high entropy has been found"
},
{
"entropy": 0.9704579025110783,
"type": "generic",
"description": "Overall entropy of this PE file is high"
}
],
"references": [
"http:\/\/www.forensickb.com\/2013\/03\/file-entropy-explained.html",
"http:\/\/virii.es\/U\/Using%20Entropy%20Analysis%20to%20Find%20Encrypted%20and%20Packed%20Malware.pdf"
],
"name": "packer_entropy"
},
{
"markcount": 11,
"families": [],
"description": "One or more of the buffers contains an embedded PE file",
"severity": 3,
"marks": [
{
"category": "buffer",
"ioc": "Buffer with sha1: a8fd55cd622ca9e36cd28c15f24cfa5f64bfe645",
"type": "ioc",
"description": null
},
{
"category": "buffer",
"ioc": "Buffer with sha1: 094a6a8b3385847d62f9d5ac00675a208db9f229",
"type": "ioc",
"description": null
},
{
"category": "buffer",
"ioc": "Buffer with sha1: 89d285e8dd346a1a0bc6d6ecf089059020733d06",
"type": "ioc",
"description": null
},
{
"category": "buffer",
"ioc": "Buffer with sha1: 89a5b738ab6df9b7b222be51cff350dc086e5469",
"type": "ioc",
"description": null
},
{
"category": "buffer",
"ioc": "Buffer with sha1: 1bf63e9cf473d468d71ea82cd4577db0c9ddc818",
"type": "ioc",
"description": null
},
{
"category": "buffer",
"ioc": "Buffer with sha1: baffb93421b2380dbc772ce89cb6606229989662",
"type": "ioc",
"description": null
},
{
"category": "buffer",
"ioc": "Buffer with sha1: d5c50230952dbc877ec454a4533aab9ec9b77924",
"type": "ioc",
"description": null
},
{
"category": "buffer",
"ioc": "Buffer with sha1: 9f197252a216643938208db51c6370ae015d100b",
"type": "ioc",
"description": null
},
{
"category": "buffer",
"ioc": "Buffer with sha1: 5a6b28156799f192e5ae5452edb25284413cb638",
"type": "ioc",
"description": null
},
{
"category": "buffer",
"ioc": "Buffer with sha1: 313efd93395182fc8d74c5f0c9f848b1f561e75f",
"type": "ioc",
"description": null
},
{
"category": "buffer",
"ioc": "Buffer with sha1: af9759e2904dc9c12f325544e57b87dd56c188aa",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "dumped_buffer2"
},
{
"markcount": 11,
"families": [],
"description": "Allocates execute permission to another process indicative of possible code injection",
"severity": 3,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2988,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x0000013c",
"allocation_type": 12288,
"base_address": "0x000b0000"
},
"time": 1583416389.53,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 1268,
"type": "call",
"cid": 5653
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x02300000"
},
"time": 1583416387.062375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5271
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x00130000"
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5290
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1788,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x02a40000"
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5309
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x02680000"
},
"time": 1583416388.390375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5334
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x01c60000"
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5353
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x03300000"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5384
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1636,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x002d0000"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5413
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 812,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x03370000"
},
"time": 1583416389.343375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5432
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x02260000"
},
"time": 1583416389.405375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5469
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1092,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000174",
"allocation_type": 12288,
"base_address": "0x01f30000"
},
"time": 1583416394.577375,
"tid": 1096,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5961
}
],
"references": [],
"name": "allocates_execute_remote_process"
},
{
"markcount": 566,
"families": [],
"description": "Installs itself for autorun at Windows startup",
"severity": 3,
"marks": [
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\{2EAD3E3A-2594-AD48-A920-6470BBC0476D}",
"reg_value": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe"
}
],
"references": [],
"name": "persistence_autorun"
},
{
"markcount": 2,
"families": [],
"description": "Creates or sets a registry key to a long series of bytes, possibly to store a binary or malware config",
"severity": 3,
"marks": [
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "NtSetValueKey",
"return_value": 0,
"arguments": {
"index": 0,
"key_handle": "0x0000000000000f84",
"value": "\u0014\u0000\u0000\u0000\u0005\u0000\u0000\u0000\u0001\u0000\u0001\u0000\u0010\u0000\u0000\u0000\u0014\u0000\u0000\u0000IL \u0006\u0010\u0000$\u0000\u0018\u0000\u0010\u0000\u0010\u0000\u00ff\u00ff\u00ff\u00ff!\u0010\u00ff\u00ff\u00ff\u00ff\u00ff\u00ff\u00ff\u00ffBM6\u0000\u0000\u0000\u0000\u0000\u0000\u00006\u0000\u0000\u0000(\u0000\u0000\u0000\u0010\u0000\u0000\u0000@\u0002\u0000\u0000\u0001\u0000 \u0000\u0000\u0000\u0000\u0000\u0000\u0090\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000",
"reg_type": 3,
"regkey": "HKEY_CURRENT_USER\\Local Settings\\Software\\Microsoft\\Windows\\CurrentVersion\\TrayNotify\\PastIconsStream"
},
"time": 1583416396.983125,
"tid": 1828,
"flags": {
"reg_type": "REG_BINARY"
}
},
"pid": 1788,
"type": "call",
"cid": 676
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "NtSetValueKey",
"return_value": 0,
"arguments": {
"index": 0,
"key_handle": "0x00000000000001e0",
"value": "\u0014\u0000\u0000\u0000\u0007\u0000\u0000\u0000\u0001\u0000\u0001\u0000\u0004\u0000\u0000\u0000\u0014\u0000\u0000\u0000{\u0000S\u00003\u00008\u0000O\u0000S\u00004\u00000\u00004\u0000-\u00001\u0000Q\u00004\u00003\u0000-\u00004\u00002\u0000S\u00002\u0000-\u00009\u00003\u00000\u00005\u0000-\u00006\u00007\u0000Q\u0000R\u00000\u0000O\u00002\u00008\u0000S\u0000P\u00002\u00003\u0000}\u0000\\\u0000r\u0000k\u0000c\u0000y\u0000b\u0000e\u0000r\u0000e\u0000.\u0000r\u0000k\u0000r\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000{\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0002\u0000\u0000\u0000\u00e4\u0007\u0003\u0000F\u0000b\u0000y\u0000i\u0000r\u0000 \u0000C\u0000P\u0000 \u0000v\u0000f\u0000f\u0000h\u0000r\u0000f\u0000:\u0000 \u00001\u0000 \u0000z\u0000r\u0000f\u0000f\u0000n\u0000t\u0000r\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u000e\u0000\u0000\u0000v\u00ae x\u00e3#)B\u0082\u00c1\u00e4\u001c\u00b6}[\u009c\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00b3\u0086;4\u00e6\u00ee\u00d4\u0001\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\r !\u008f\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000{\u0000S\u00003\u00008\u0000O\u0000S\u00004\u00000\u00004\u0000-\u00001\u0000Q\u00004\u00003\u0000-\u00004\u00002\u0000S\u00002\u0000-\u00009\u00003\u00000\u00005\u0000-\u00006\u00007\u0000Q\u0000R\u00000\u0000O\u00002\u00008\u0000S\u0000P\u00002\u00003\u0000}\u0000\\\u0000r\u0000k\u0000c\u0000y\u0000b\u0000e\u0000r\u0000e\u0000.\u0000r\u0000k\u0000r\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000d\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0002\u0000\u0000\u0000\u00e4\u0007\u0003\u0000F\u0000c\u0000r\u0000n\u0000x\u0000r\u0000e\u0000f\u0000:\u0000 \u00006\u00007\u0000%\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u000f\u0000\u0000\u0000s\u00ae x\u00e3#)B\u0082\u00c1\u00e4\u001c\u00b6}[\u009c\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0086\u00e2\u009e\u00956\u0005\u00d4\u0001\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\r !\u008f\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0002\u0000\u0000\u0000{\u0000S\u00003\u00008\u0000O\u0000S\u00004\u00000\u00004\u0000-\u00001\u0000Q\u00004\u00003\u0000-\u00004\u00002\u0000S\u00002\u0000-\u00009\u00003\u00000\u00005\u0000-\u00006\u00007\u0000Q\u0000R\u00000\u0000O\u00002\u00008\u0000S\u0000P\u00002\u00003\u0000}\u0000\\\u0000r\u0000k\u0000c\u0000y\u0000b\u0000e\u0000r\u0000e\u0000.\u0000r\u0000k\u0000r\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000}\u00c0\u0000\u0000\u0000\u0000\u0000\u0000\u0001\u0000\u0000\u0000\u00e4\u0007\u0003\u0000H\u0000a\u0000v\u0000q\u0000r\u0000a\u0000g\u0000v\u0000s\u0000v\u0000r\u0000q\u0000 \u0000a\u0000r\u0000g\u0000j\u0000b\u0000e\u0000x\u0000 \u0000A\u0000b\u0000 \u0000V\u0000a\u0000g\u0000r\u0000e\u0000a\u0000r\u0000g\u0000 \u0000n\u0000p\u0000p\u0000r\u0000f\u0000f\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000",
"reg_type": 3,
"regkey": "HKEY_CURRENT_USER\\Local Settings\\Software\\Microsoft\\Windows\\CurrentVersion\\TrayNotify\\IconStreams"
},
"time": 1583416396.983125,
"tid": 1828,
"flags": {
"reg_type": "REG_BINARY"
}
},
"pid": 1788,
"type": "call",
"cid": 678
}
],
"references": [],
"name": "creates_largekey"
},
{
"markcount": 1,
"families": [],
"description": "Deletes executed files from disk",
"severity": 3,
"marks": [
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "deletes_executed_files"
},
{
"markcount": 20,
"families": [],
"description": "Creates a thread using CreateRemoteThread in a non-child process indicative of process injection",
"severity": 3,
"marks": [
{
"category": "Process injection",
"ioc": "Process 2872 created a remote thread in non-child process 1724",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1724,
"function_address": "0x0230adea",
"flags": 0,
"process_handle": "0x00000140",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5280
},
{
"category": "Process injection",
"ioc": "Process 2872 created a remote thread in non-child process 1768",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1768,
"function_address": "0x0013adea",
"flags": 0,
"process_handle": "0x00000140",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5299
},
{
"category": "Process injection",
"ioc": "Process 2872 created a remote thread in non-child process 1788",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1788,
"function_address": "0x02a4adea",
"flags": 0,
"process_handle": "0x00000140",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1583416388.390375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5318
},
{
"category": "Process injection",
"ioc": "Process 2872 created a remote thread in non-child process 1692",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1692,
"function_address": "0x0268adea",
"flags": 0,
"process_handle": "0x00000140",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5343
},
{
"category": "Process injection",
"ioc": "Process 2872 created a remote thread in non-child process 1700",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1700,
"function_address": "0x01c6adea",
"flags": 0,
"process_handle": "0x00000140",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5362
},
{
"category": "Process injection",
"ioc": "Process 2872 created a remote thread in non-child process 2168",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 2168,
"function_address": "0x0330adea",
"flags": 0,
"process_handle": "0x00000140",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5393
},
{
"category": "Process injection",
"ioc": "Process 2872 created a remote thread in non-child process 1636",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1636,
"function_address": "0x002dadea",
"flags": 0,
"process_handle": "0x00000140",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1583416389.343375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5422
},
{
"category": "Process injection",
"ioc": "Process 2872 created a remote thread in non-child process 812",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 812,
"function_address": "0x0337adea",
"flags": 0,
"process_handle": "0x00000140",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1583416389.405375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5441
},
{
"category": "Process injection",
"ioc": "Process 2872 created a remote thread in non-child process 1268",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 324,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1268,
"function_address": "0x0226adea",
"flags": 0,
"process_handle": "0x00000140",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1583416389.421375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5478
},
{
"category": "Process injection",
"ioc": "Process 2872 created a remote thread in non-child process 1092",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1092,
"function_address": "0x01f3adea",
"flags": 0,
"process_handle": "0x00000174",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1583416395.155375,
"tid": 1096,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5976
}
],
"references": [
"www.endgame.com\/blog\/technical-blog\/ten-process-injection-techniques-technical-survey-common-and-trending-process"
],
"name": "injection_createremotethread"
},
{
"markcount": 22,
"families": [],
"description": "Manipulates memory of a non-child process indicative of process injection",
"severity": 3,
"marks": [
{
"category": "Process injection",
"ioc": "Process 1268 manipulating memory of non-child process 2988",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2988,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x0000013c",
"allocation_type": 12288,
"base_address": "0x000b0000"
},
"time": 1583416389.53,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 1268,
"type": "call",
"cid": 5653
},
{
"category": "Process injection",
"ioc": "Process 2872 manipulating memory of non-child process 1724",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x02300000"
},
"time": 1583416387.062375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5271
},
{
"category": "Process injection",
"ioc": "Process 2872 manipulating memory of non-child process 1768",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x00130000"
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5290
},
{
"category": "Process injection",
"ioc": "Process 2872 manipulating memory of non-child process 1788",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1788,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x02a40000"
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5309
},
{
"category": "Process injection",
"ioc": "Process 2872 manipulating memory of non-child process 1692",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x02680000"
},
"time": 1583416388.390375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5334
},
{
"category": "Process injection",
"ioc": "Process 2872 manipulating memory of non-child process 1700",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x01c60000"
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5353
},
{
"category": "Process injection",
"ioc": "Process 2872 manipulating memory of non-child process 2168",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x03300000"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5384
},
{
"category": "Process injection",
"ioc": "Process 2872 manipulating memory of non-child process 1636",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1636,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x002d0000"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5413
},
{
"category": "Process injection",
"ioc": "Process 2872 manipulating memory of non-child process 812",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 812,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x03370000"
},
"time": 1583416389.343375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5432
},
{
"category": "Process injection",
"ioc": "Process 2872 manipulating memory of non-child process 1268",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x02260000"
},
"time": 1583416389.405375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5469
},
{
"category": "Process injection",
"ioc": "Process 2872 manipulating memory of non-child process 1092",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1092,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000174",
"allocation_type": 12288,
"base_address": "0x01f30000"
},
"time": 1583416394.577375,
"tid": 1096,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5961
}
],
"references": [
"www.endgame.com\/blog\/technical-blog\/ten-process-injection-techniques-technical-survey-common-and-trending-process"
],
"name": "injection_modifies_memory"
},
{
"markcount": 55,
"families": [],
"description": "Potential code injection by writing to the memory of another process",
"severity": 3,
"marks": [
{
"category": "Process injection",
"ioc": "Process 1268 injected into non-child 2988",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2988,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x0000013c",
"base_address": "0x000f0730"
},
"time": 1583416389.858,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5656
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2988,
"buffer": "\u0000\u0000\u000b\u0000",
"process_handle": "0x0000013c",
"base_address": "0x000f0744"
},
"time": 1583416389.858,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5657
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2988,
"buffer": "\b\u0000\u0000\u0000",
"process_handle": "0x0000013c",
"base_address": "0x000f0df0"
},
"time": 1583416389.858,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5659
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2988,
"buffer": "\f\u0000\u0000\u0000",
"process_handle": "0x0000013c",
"base_address": "0x000f0df4"
},
"time": 1583416389.858,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5661
},
{
"category": "Process injection",
"ioc": "Process 2872 injected into non-child 1724",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1724,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x02340730"
},
"time": 1583416387.687375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5274
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1724,
"buffer": "\u0000\u00000\u0002",
"process_handle": "0x00000140",
"base_address": "0x02340744"
},
"time": 1583416387.687375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5275
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1724,
"buffer": "X\u0003\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x02340df0"
},
"time": 1583416387.687375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5277
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1724,
"buffer": "(\u0003\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x02340df4"
},
"time": 1583416387.687375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5279
},
{
"category": "Process injection",
"ioc": "Process 2872 injected into non-child 1768",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1768,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x00170730"
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5293
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1768,
"buffer": "\u0000\u0000\u0013\u0000",
"process_handle": "0x00000140",
"base_address": "0x00170744"
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5294
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1768,
"buffer": "4\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x00170df0"
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5296
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1768,
"buffer": "\u00d8\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x00170df4"
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5298
},
{
"category": "Process injection",
"ioc": "Process 2872 injected into non-child 1788",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1788,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x02a80730"
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5312
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1788,
"buffer": "\u0000\u0000\u00a4\u0002",
"process_handle": "0x00000140",
"base_address": "0x02a80744"
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5313
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1788,
"buffer": "\u00a0\r\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x02a80df0"
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5315
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1788,
"buffer": "L\u0014\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x02a80df4"
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5317
},
{
"category": "Process injection",
"ioc": "Process 2872 injected into non-child 1692",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1692,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x026c0730"
},
"time": 1583416388.702375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5337
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1692,
"buffer": "\u0000\u0000h\u0002",
"process_handle": "0x00000140",
"base_address": "0x026c0744"
},
"time": 1583416388.702375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5338
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1692,
"buffer": "x\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x026c0df0"
},
"time": 1583416388.702375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5340
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1692,
"buffer": "D\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x026c0df4"
},
"time": 1583416388.702375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5342
},
{
"category": "Process injection",
"ioc": "Process 2872 injected into non-child 1700",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1700,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x01ca0730"
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5356
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1700,
"buffer": "\u0000\u0000\u00c6\u0001",
"process_handle": "0x00000140",
"base_address": "0x01ca0744"
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5357
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1700,
"buffer": "\u0000\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x01ca0df0"
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5359
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1700,
"buffer": "\u0004\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x01ca0df4"
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5361
},
{
"category": "Process injection",
"ioc": "Process 2872 injected into non-child 2168",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2168,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x03340730"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5387
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2168,
"buffer": "\u0000\u00000\u0003",
"process_handle": "0x00000140",
"base_address": "0x03340744"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5388
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2168,
"buffer": "t\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x03340df0"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5390
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2168,
"buffer": "x\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x03340df4"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5392
},
{
"category": "Process injection",
"ioc": "Process 2872 injected into non-child 1636",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1636,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x00310730"
},
"time": 1583416389.093375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5416
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1636,
"buffer": "\u0000\u0000-\u0000",
"process_handle": "0x00000140",
"base_address": "0x00310744"
},
"time": 1583416389.093375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5417
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1636,
"buffer": "X\u0002\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x00310df0"
},
"time": 1583416389.093375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5419
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1636,
"buffer": "\\\u0002\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x00310df4"
},
"time": 1583416389.093375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5421
},
{
"category": "Process injection",
"ioc": "Process 2872 injected into non-child 812",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 812,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x033b0730"
},
"time": 1583416389.405375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5435
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 812,
"buffer": "\u0000\u00007\u0003",
"process_handle": "0x00000140",
"base_address": "0x033b0744"
},
"time": 1583416389.405375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5436
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 812,
"buffer": "\u00b4\u0003\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x033b0df0"
},
"time": 1583416389.405375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5438
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 812,
"buffer": " \u0004\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x033b0df4"
},
"time": 1583416389.405375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5440
},
{
"category": "Process injection",
"ioc": "Process 2872 injected into non-child 1268",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1268,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x022a0730"
},
"time": 1583416389.421375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5472
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1268,
"buffer": "\u0000\u0000&\u0002",
"process_handle": "0x00000140",
"base_address": "0x022a0744"
},
"time": 1583416389.421375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5473
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1268,
"buffer": "H\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x022a0df0"
},
"time": 1583416389.421375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5475
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1268,
"buffer": "L\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x022a0df4"
},
"time": 1583416389.421375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5477
}
],
"references": [],
"name": "injection_write_memory"
},
{
"markcount": 1,
"families": [],
"description": "Creates a windows hook that monitors keyboard input (keylogger)",
"severity": 3,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "SetWindowsHookExW",
"return_value": 61145687,
"arguments": {
"thread_identifier": 0,
"callback_function": "0x00000000ffe9ae10",
"module_address": "0x00000000ffdf0000",
"hook_identifier": 13
},
"time": 1583416450.030125,
"tid": 1828,
"flags": {
"hook_identifier": "WH_KEYBOARD_LL"
}
},
"pid": 1788,
"type": "call",
"cid": 3724
}
],
"references": [],
"name": "infostealer_keylogger"
},
{
"markcount": 2,
"families": [],
"description": "Used NtSetContextThread to modify a thread in a remote process indicative of process injection",
"severity": 3,
"marks": [
{
"category": "Process injection",
"ioc": "Process 1268 called NtSetContextThread to modify thread in remote process 2988",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtSetContextThread",
"return_value": 0,
"arguments": {
"thread_handle": "0x00000134",
"registers": {
"eip": 2008678852,
"esp": 2423440,
"edi": 0,
"eax": 765366,
"ebp": 0,
"edx": 0,
"ebx": 2130567168,
"esi": 0,
"ecx": 0
},
"process_identifier": 2988
},
"time": 1583416389.858,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5663
}
],
"references": [
"www.endgame.com\/blog\/technical-blog\/ten-process-injection-techniques-technical-survey-common-and-trending-process"
],
"name": "injection_ntsetcontextthread"
},
{
"markcount": 56,
"families": [
"zeus"
],
"description": "Zeus P2P (Banking Trojan)",
"severity": 3,
"marks": [
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-3CEB-B06E2E0B9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-48EE-B06E5A0E9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{56060262-19CC-D5E3-A920-6470BBC0476D}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-28E0-B06E3A009373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-80EB-B06E920B9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Local\\{C8B94219-59B7-4B5C-A920-6470BBC0476D}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-E0E0-B06EF2009373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-74ED-B06E660D9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-FCEB-B06EEE0B9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-6CEE-B06E7E0E9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{A5B32338-3896-2656-A920-6470BBC0476D}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-CCEB-B06EDE0B9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-A8EB-B06EBA0B9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-F4EB-B06EE60B9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-68ED-B06E7A0D9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-E0E8-B06EF2089373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-24EC-B06E360C9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-D0E1-B06EC2019373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-0CE9-B06E1E099373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-E8EE-B06EFA0E9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-B4EC-B06EA60C9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{73B5150B-0EA5-F050-A920-6470BBC0476D}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-84E1-B06E96019373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-D4EC-B06EC60C9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-58E9-B06E4A099373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-2CEA-B06E3E0A9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-50EB-B06E420B9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{C3671720-0C8E-4082-A920-6470BBC0476D}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-14EE-B06E060E9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-C0EF-B06ED20F9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-D4EA-B06EC60A9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-04E9-B06E16099373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-8CEC-B06E9E0C9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-BCE8-B06EAE089373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-C0E9-B06ED2099373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-DCEE-B06ECE0E9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-60EB-B06E720B9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{A95FF40A-EFA4-2ABA-A920-6470BBC0476D}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-78E8-B06E6A089373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-50E2-B06E42029373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Local\\{E91F2729-3C87-6AFA-A920-6470BBC0476D}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-0CEF-B06E1E0F9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-94EC-B06E860C9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{A95FF40D-EFA3-2ABA-A920-6470BBC0476D}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Local\\{C8B94218-59B6-4B5C-A920-6470BBC0476D}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-C8EB-B06EDA0B9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-C0EC-B06ED20C9373}",
"type": "ioc",
"description": null
},
{
"category": "mutex",
"ioc": "Global\\{DA88BBAC-A002-596D-4CEC-B06E5E0C9373}",
"type": "ioc",
"description": null
},
{
"category": "udp",
"ioc": {
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7070,
"time": 3.083219051361084,
"dport": 5355,
"sport": 51001
},
"type": "ioc",
"description": null
},
{
"category": "udp",
"ioc": {
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7398,
"time": 1.0839118957519531,
"dport": 5355,
"sport": 53595
},
"type": "ioc",
"description": null
}
],
"references": [
"https:\/\/malwr.com\/analysis\/NmNhODg5ZWRkYjc0NDY0M2I3YTJhNDRlM2FlOTZiMjA\/",
"https:\/\/malwr.com\/analysis\/MmMwNDJlMTI0MTNkNGFjNmE0OGY3Y2I5MjhiMGI1NzI\/",
"https:\/\/malwr.com\/analysis\/MzY5ZTM2NzZhMzI3NDY2YjgzMjJiODFkODZkYzIwYmQ\/",
"https:\/\/www.virustotal.com\/de\/file\/301fcadf53e6a6167e559c84d6426960af8626d12b2e25aa41de6dce511d0568\/analysis\/#behavioural-info",
"https:\/\/www.virustotal.com\/de\/file\/d3cf49a7ac726ee27eae9d29dee648e34cb3e8fd9d494e1b347209677d62cdf9\/analysis\/#behavioural-info",
"https:\/\/www.virustotal.com\/de\/file\/d3cf49a7ac726ee27eae9d29dee648e34cb3e8fd9d494e1b347209677d62cdf9\/analysis\/#behavioural-info",
"https:\/\/www.virustotal.com\/de\/file\/301fcadf53e6a6167e559c84d6426960af8626d12b2e25aa41de6dce511d0568\/analysis\/#behavioural-info"
],
"name": "banker_zeus_p2p"
},
{
"markcount": 79,
"families": [],
"description": "Executed a process and injected code into it, probably while unpacking",
"severity": 5,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtResumeThread",
"return_value": 0,
"arguments": {
"thread_handle": "0x00000108",
"suspend_count": 1,
"process_identifier": 1268
},
"time": 1583416386.452,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5011
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateProcessInternalW",
"return_value": 1,
"arguments": {
"thread_identifier": 1480,
"thread_handle": "0x00000138",
"process_identifier": 2872,
"current_directory": "C:\\Users\\cuck\\AppData\\Roaming",
"filepath": "",
"track": 1,
"command_line": "\"C:\\Users\\cuck\\AppData\\Roaming\\Dopo\\uwpy.exe\"",
"filepath_r": "",
"stack_pivoted": 0,
"creation_flags": 67108864,
"process_handle": "0x0000013c",
"inherit_handles": 0
},
"time": 1583416386.577,
"tid": 2740,
"flags": {
"creation_flags": "CREATE_DEFAULT_ERROR_MODE"
}
},
"pid": 1268,
"type": "call",
"cid": 5209
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2988,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x0000013c",
"allocation_type": 12288,
"base_address": "0x000b0000"
},
"time": 1583416389.53,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 1268,
"type": "call",
"cid": 5653
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"buffer": "313efd93395182fc8d74c5f0c9f848b1f561e75f",
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2988,
"buffer": "",
"process_handle": "0x0000013c",
"base_address": "0x000b0000"
},
"time": 1583416389.53,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5654
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2988,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x0000013c",
"base_address": "0x000f0730"
},
"time": 1583416389.858,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5656
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2988,
"buffer": "\u0000\u0000\u000b\u0000",
"process_handle": "0x0000013c",
"base_address": "0x000f0744"
},
"time": 1583416389.858,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5657
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2988,
"buffer": "\b\u0000\u0000\u0000",
"process_handle": "0x0000013c",
"base_address": "0x000f0df0"
},
"time": 1583416389.858,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5659
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2988,
"buffer": "\f\u0000\u0000\u0000",
"process_handle": "0x0000013c",
"base_address": "0x000f0df4"
},
"time": 1583416389.858,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5661
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtGetContextThread",
"return_value": 0,
"arguments": {
"thread_handle": "0x00000134"
},
"time": 1583416389.858,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5662
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtSetContextThread",
"return_value": 0,
"arguments": {
"thread_handle": "0x00000134",
"registers": {
"eip": 2008678852,
"esp": 2423440,
"edi": 0,
"eax": 765366,
"ebp": 0,
"edx": 0,
"ebx": 2130567168,
"esi": 0,
"ecx": 0
},
"process_identifier": 2988
},
"time": 1583416389.858,
"tid": 2740,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 5663
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateProcessInternalW",
"return_value": 1,
"arguments": {
"thread_identifier": 2148,
"thread_handle": "0x00000134",
"process_identifier": 2988,
"current_directory": "",
"filepath": "",
"track": 1,
"command_line": "\"C:\\Windows\\system32\\cmd.exe\" \/c \"C:\\Users\\cuck\\AppData\\Local\\Temp\\tmp8edbb27e.bat\"",
"filepath_r": "",
"stack_pivoted": 0,
"creation_flags": 67108864,
"process_handle": "0x0000013c",
"inherit_handles": 0
},
"time": 1583416389.937,
"tid": 2740,
"flags": {
"creation_flags": "CREATE_DEFAULT_ERROR_MODE"
}
},
"pid": 1268,
"type": "call",
"cid": 5665
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtResumeThread",
"return_value": 0,
"arguments": {
"thread_handle": "0x00000108",
"suspend_count": 1,
"process_identifier": 2872
},
"time": 1583416387.030375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5004
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x02300000"
},
"time": 1583416387.062375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5271
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"buffer": "9f197252a216643938208db51c6370ae015d100b",
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1724,
"buffer": "",
"process_handle": "0x00000140",
"base_address": "0x02300000"
},
"time": 1583416387.062375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5272
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1724,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x02340730"
},
"time": 1583416387.687375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5274
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1724,
"buffer": "\u0000\u00000\u0002",
"process_handle": "0x00000140",
"base_address": "0x02340744"
},
"time": 1583416387.687375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5275
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1724,
"buffer": "X\u0003\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x02340df0"
},
"time": 1583416387.687375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5277
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1724,
"buffer": "(\u0003\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x02340df4"
},
"time": 1583416387.687375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5279
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x00130000"
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5290
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"buffer": "baffb93421b2380dbc772ce89cb6606229989662",
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1768,
"buffer": "",
"process_handle": "0x00000140",
"base_address": "0x00130000"
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5291
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1768,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x00170730"
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5293
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1768,
"buffer": "\u0000\u0000\u0013\u0000",
"process_handle": "0x00000140",
"base_address": "0x00170744"
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5294
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1768,
"buffer": "4\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x00170df0"
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5296
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1768,
"buffer": "\u00d8\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x00170df4"
},
"time": 1583416387.921375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5298
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1788,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x02a40000"
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5309
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"buffer": "1bf63e9cf473d468d71ea82cd4577db0c9ddc818",
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1788,
"buffer": "",
"process_handle": "0x00000140",
"base_address": "0x02a40000"
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5310
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1788,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x02a80730"
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5312
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1788,
"buffer": "\u0000\u0000\u00a4\u0002",
"process_handle": "0x00000140",
"base_address": "0x02a80744"
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5313
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1788,
"buffer": "\u00a0\r\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x02a80df0"
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5315
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1788,
"buffer": "L\u0014\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x02a80df4"
},
"time": 1583416388.140375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5317
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x02680000"
},
"time": 1583416388.390375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5334
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"buffer": "094a6a8b3385847d62f9d5ac00675a208db9f229",
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1692,
"buffer": "",
"process_handle": "0x00000140",
"base_address": "0x02680000"
},
"time": 1583416388.390375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5335
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1692,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x026c0730"
},
"time": 1583416388.702375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5337
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1692,
"buffer": "\u0000\u0000h\u0002",
"process_handle": "0x00000140",
"base_address": "0x026c0744"
},
"time": 1583416388.702375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5338
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1692,
"buffer": "x\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x026c0df0"
},
"time": 1583416388.702375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5340
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1692,
"buffer": "D\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x026c0df4"
},
"time": 1583416388.702375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5342
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x01c60000"
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5353
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"buffer": "d5c50230952dbc877ec454a4533aab9ec9b77924",
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1700,
"buffer": "",
"process_handle": "0x00000140",
"base_address": "0x01c60000"
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5354
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1700,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x01ca0730"
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5356
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1700,
"buffer": "\u0000\u0000\u00c6\u0001",
"process_handle": "0x00000140",
"base_address": "0x01ca0744"
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5357
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1700,
"buffer": "\u0000\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x01ca0df0"
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5359
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1700,
"buffer": "\u0004\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x01ca0df4"
},
"time": 1583416388.890375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5361
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x03300000"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5384
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"buffer": "5a6b28156799f192e5ae5452edb25284413cb638",
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2168,
"buffer": "",
"process_handle": "0x00000140",
"base_address": "0x03300000"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5385
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2168,
"buffer": "\u0000\u0000\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x03340730"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5387
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2168,
"buffer": "\u0000\u00000\u0003",
"process_handle": "0x00000140",
"base_address": "0x03340744"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5388
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2168,
"buffer": "t\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x03340df0"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5390
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2168,
"buffer": "x\u0001\u0000\u0000",
"process_handle": "0x00000140",
"base_address": "0x03340df4"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5392
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1636,
"region_size": 290816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x002d0000"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2872,
"type": "call",
"cid": 5413
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"buffer": "89a5b738ab6df9b7b222be51cff350dc086e5469",
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 1636,
"buffer": "",
"process_handle": "0x00000140",
"base_address": "0x002d0000"
},
"time": 1583416389.077375,
"tid": 1480,
"flags": {}
},
"pid": 2872,
"type": "call",
"cid": 5414
}
],
"references": [],
"name": "injection_runpe"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 546,
"time": 3.1531879901885986,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 5226,
"time": 9.149450063705444,
"dport": 138,
"sport": 138
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7070,
"time": 3.083219051361084,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7398,
"time": 1.0839118957519531,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7726,
"time": 3.0985829830169678,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8054,
"time": 1.5888419151306152,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8382,
"time": -0.037574052810668945,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 8710,
"time": 1.6013660430908203,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 28120,
"time": 1.1080939769744873,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 36504,
"time": 3.178213119506836,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "b7885aaa30d61b3ede218f1d38782a57739e93877afaa8aaab47f4d764ea5a87",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "2a699a9ad6599f0993b6c87aecb7967047fb13499479852decc2102319d807f4",
"irc": [],
"https_ex": []
}Screenshots
sJg2e3U.exe removal instructions
The instructions below shows how to remove sJg2e3U.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the sJg2e3U.exe file for removal, restart your computer and scan it again to verify that sJg2e3U.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate sJg2e3U.exe in the scan result and tick the checkbox next to the sJg2e3U.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate sJg2e3U.exe in the scan result.

 c:\downloads\sJg2e3U.exe
c:\downloads\sJg2e3U.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If sJg2e3U.exe still remains in the scan result, proceed with the next step. If sJg2e3U.exe is gone from the scan result you're done.
- If sJg2e3U.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that sJg2e3U.exe no longer appear in the scan result.
Hashes [?]
| Property | Value |
|---|---|
| MD5 | b2834931de3f6fb0c6fe5f4f5a63ce16 |
| SHA256 | dd712e661dd0d4854be9a37fa4e2b7ba6f167c3c49e7b4ad63ce35067a578f26 |
Error Messages
These are some of the error messages that can appear related to sjg2e3u.exe:
sjg2e3u.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
sjg2e3u.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
Microsoft Windows Setup Utility has stopped working.
End Program - sjg2e3u.exe. This program is not responding.
sjg2e3u.exe is not a valid Win32 application.
sjg2e3u.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with sJg2e3U.exe?
To help other users, please let us know what you will do with sJg2e3U.exe:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.