What is EFFMNWE.exe?
EFFMNWE.exe is usually located in the 'c:\downloads\' folder.
Some of the anti-virus scanners at VirusTotal detected EFFMNWE.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Digital signatures [?]
EFFMNWE.exe is not signed.
VirusTotal report
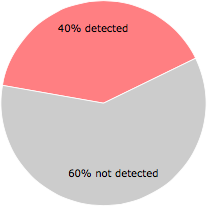
27 of the 67 anti-virus programs at VirusTotal detected the EFFMNWE.exe file. That's a 40% detection rate.
| Scanner | Detection Name |
|---|---|
| Ad-Aware | Trojan.GenericKD.31813666 |
| AegisLab | Trojan.Win32.Generic.4!c |
| AhnLab-V3 | Malware/Win32.Generic.C2867324 |
| ALYac | Trojan.GenericKD.31813666 |
| Antiy-AVL | Trojan/Win32.Occamy |
| Arcabit | Trojan.Generic.D1E57022 |
| Avast | Win32:Malware-gen |
| AVG | Win32:Malware-gen |
| BitDefender | Trojan.GenericKD.31813666 |
| Cybereason | malicious.1c69a1 |
| Cyren | W32/Trojan.AAKM-7906 |
| Emsisoft | Trojan.GenericKD.31813666 (B) |
| Endgame | malicious (high confidence) |
| FireEye | Trojan.GenericKD.31813666 |
| GData | Trojan.GenericKD.31813666 |
| Ikarus | Trojan.GenericKD.31813666 |
| K7AntiVirus | Riskware ( 0040eff71 ) |
| K7GW | Riskware ( 0040eff71 ) |
| MAX | malware (ai score=100) |
| McAfee-GW-Edition | BehavesLike.Win32.Dropper.ch |
| Microsoft | Trojan:Win32/Occamy.B |
| MicroWorld-eScan | Trojan.GenericKD.31813666 |
| Paloalto | generic.ml |
| Panda | Trj/GdSda.A |
| Rising | Trojan.Bitrep!8.F596 (CLOUD) |
| Sophos | Mal/Generic-S |
| TrendMicro-HouseCall | Ransom.Win32.GANDCRAB.SM1 |
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\decryption_log_utf16.txt"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\decryption_log_utf16.txt"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Command Processor"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\decryption_log_utf16.txt"
],
"file_deleted": [
"C:\\Python27\\Lib\\email\\test\\EFFMNWE-DECRYPT.html",
"C:\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\email\\test\\data\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\ctypes\\test\\EFFMNWE-DECRYPT.html",
"C:\\ProgramData\\EFFMNWE-DECRYPT.html",
"C:\\$Recycle.Bin\\S-1-5-21-699399860-4089948139-3198924279-1001\\$R3U3MZB\\EFFMNWE-DECRYPT.txt",
"C:\\PerfLogs\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\email\\mime\\EFFMNWE-DECRYPT.html",
"C:\\$Recycle.Bin\\S-1-5-21-699399860-4089948139-3198924279-1001\\EFFMNWE-DECRYPT.txt",
"C:\\Program Files\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\bsddb\\test\\EFFMNWE-DECRYPT.txt",
"C:\\ProgramData\\EFFMNWE-DECRYPT.txt",
"C:\\$Recycle.Bin\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\compiler\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\include\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\compiler\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\include\\EFFMNWE-DECRYPT.txt",
"C:\\cuckoo-agent\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\distutils\\tests\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\encodings\\EFFMNWE-DECRYPT.txt",
"C:\\PerfLogs\\Admin\\EFFMNWE-DECRYPT.txt",
"C:\\PerfLogs\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\email\\mime\\EFFMNWE-DECRYPT.txt",
"C:\\PerfLogs\\Admin\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\distutils\\tests\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\ctypes\\macholib\\EFFMNWE-DECRYPT.txt",
"C:\\Program Files (x86)\\EFFMNWE-DECRYPT.txt",
"C:\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\encodings\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\curses\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\bsddb\\EFFMNWE-DECRYPT.txt",
"C:\\$Recycle.Bin\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Doc\\EFFMNWE-DECRYPT.html",
"C:\\cuckoo-agent\\EFFMNWE-DECRYPT.html",
"C:\\Documents and Settings\\EFFMNWE-DECRYPT.html",
"C:\\$Recycle.Bin\\S-1-5-21-699399860-4089948139-3198924279-1001\\EFFMNWE-DECRYPT.html",
"C:\\Program Files\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\email\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\distutils\\command\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\distutils\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\email\\test\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\email\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Doc\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\DLLs\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\curses\\EFFMNWE-DECRYPT.txt",
"C:\\$Recycle.Bin\\S-1-5-21-699399860-4089948139-3198924279-1001\\$R3U3MZB\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\DLLs\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\bsddb\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\ctypes\\macholib\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\ctypes\\test\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\ctypes\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\bsddb\\test\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\EFFMNWE-DECRYPT.txt",
"C:\\Program Files (x86)\\EFFMNWE-DECRYPT.html",
"C:\\Documents and Settings\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\distutils\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\distutils\\command\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\email\\test\\data\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\ctypes\\EFFMNWE-DECRYPT.html"
],
"file_exists": [
"C:\\Windows\\System32\\cmd.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp"
],
"file_failed": [
"\\??\\B:",
"\\??\\A:"
],
"command_line": [
"C:\\Windows\\system32\\cmd.exe \/c cls"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\AutoRun",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\AutoRun",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\CompletionChar"
],
"directory_enumerated": [
"C:\\cuckoo-agent\\*",
"C:\\Users\\cuck\\AppData",
"C:\\Python27\\Lib\\email\\test\\data\\*",
"C:\\Python27\\DLLs\\*",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Python27\\Lib\\ctypes\\*",
"C:\\Python27\\Lib\\distutils\\command\\*",
"C:\\Python27\\Doc\\*",
"C:\\Python27\\Lib\\bsddb\\*",
"C:\\Python27\\Lib\\curses\\*",
"C:\\Python27\\Lib\\distutils\\tests\\*",
"C:\\Python27\\Lib\\bsddb\\test\\*",
"C:\\Python27\\Lib\\email\\mime\\*",
"C:\\Python27\\Lib\\email\\*",
"C:\\$Recycle.Bin\\*",
"C:\\$Recycle.Bin\\S-1-5-21-699399860-4089948139-3198924279-1001\\*",
"C:\\Users",
"C:\\Python27\\Lib\\*",
"C:\\Python27\\include\\*",
"C:\\PerfLogs\\Admin\\*",
"C:\\Python27\\Lib\\ctypes\\macholib\\*",
"C:\\Python27\\Lib\\ctypes\\test\\*",
"C:\\Python27\\Lib\\email\\test\\*",
"C:\\$Recycle.Bin\\S-1-5-21-699399860-4089948139-3198924279-1001\\$R3U3MZB\\*",
"C:\\Python27\\*",
"C:\\Users\\cuck",
"C:\\Python27\\Lib\\compiler\\*",
"C:\\Users\\cuck\\AppData\\Local",
"C:\\*",
"C:\\Python27\\Lib\\distutils\\*",
"C:\\Python27\\Lib\\encodings\\*",
"C:\\PerfLogs\\*",
"C:\\Documents and Settings\\*"
]
}Dropped
[
{
"yara": [],
"sha1": "3409ebef32162c01b115f78871ecd49ea58833a2",
"name": "0c9c88269da81295_decryption_log_utf16.txt",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\decryption_log_utf16.txt",
"type": "data",
"sha256": "0c9c88269da812958e7c9200b1c4c938e1e1e15fbe4588e54ab663f172fcf947",
"urls": [],
"crc32": "02EDC0D3",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/7460\/files\/0c9c88269da81295_decryption_log_utf16.txt",
"ssdeep": null,
"size": 242542,
"sha512": "b75565c10e2e77289a42b99e6528f63c817edd5511952c9cd48568441fab3720cf7f83b58f789d42674e0d6e34b3c0f6080718990c1375b9059beb75f9a463e1",
"pids": [
2740
],
"md5": "72ec0a58c6d289d18f0a64a8bb0de7a6"
}
]Generic
[
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1589147587.34375,
"ppid": 376
},
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\691ad9227ca29a3cee86043fbfeccfa7bc735cfabd14e108adb3be18420b0718.bin",
"process_name": "691ad9227ca29a3cee86043fbfeccfa7bc735cfabd14e108adb3be18420b0718.bin",
"pid": 2740,
"summary": {
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\decryption_log_utf16.txt"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\decryption_log_utf16.txt"
],
"command_line": [
"C:\\Windows\\system32\\cmd.exe \/c cls"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\decryption_log_utf16.txt"
],
"file_deleted": [
"C:\\Python27\\Lib\\email\\test\\EFFMNWE-DECRYPT.html",
"C:\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\email\\test\\data\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\ctypes\\test\\EFFMNWE-DECRYPT.html",
"C:\\ProgramData\\EFFMNWE-DECRYPT.html",
"C:\\$Recycle.Bin\\S-1-5-21-699399860-4089948139-3198924279-1001\\$R3U3MZB\\EFFMNWE-DECRYPT.txt",
"C:\\PerfLogs\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\email\\mime\\EFFMNWE-DECRYPT.html",
"C:\\$Recycle.Bin\\S-1-5-21-699399860-4089948139-3198924279-1001\\EFFMNWE-DECRYPT.txt",
"C:\\Program Files\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\bsddb\\test\\EFFMNWE-DECRYPT.txt",
"C:\\ProgramData\\EFFMNWE-DECRYPT.txt",
"C:\\$Recycle.Bin\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\compiler\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\include\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\compiler\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\include\\EFFMNWE-DECRYPT.txt",
"C:\\cuckoo-agent\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\distutils\\tests\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\encodings\\EFFMNWE-DECRYPT.txt",
"C:\\PerfLogs\\Admin\\EFFMNWE-DECRYPT.txt",
"C:\\PerfLogs\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\email\\mime\\EFFMNWE-DECRYPT.txt",
"C:\\PerfLogs\\Admin\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\distutils\\tests\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\ctypes\\macholib\\EFFMNWE-DECRYPT.txt",
"C:\\Program Files (x86)\\EFFMNWE-DECRYPT.txt",
"C:\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\encodings\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\curses\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\bsddb\\EFFMNWE-DECRYPT.txt",
"C:\\$Recycle.Bin\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Doc\\EFFMNWE-DECRYPT.html",
"C:\\cuckoo-agent\\EFFMNWE-DECRYPT.html",
"C:\\Documents and Settings\\EFFMNWE-DECRYPT.html",
"C:\\$Recycle.Bin\\S-1-5-21-699399860-4089948139-3198924279-1001\\EFFMNWE-DECRYPT.html",
"C:\\Program Files\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\email\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\distutils\\command\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\distutils\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\email\\test\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\email\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Doc\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\DLLs\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\curses\\EFFMNWE-DECRYPT.txt",
"C:\\$Recycle.Bin\\S-1-5-21-699399860-4089948139-3198924279-1001\\$R3U3MZB\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\DLLs\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\bsddb\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\ctypes\\macholib\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\ctypes\\test\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\ctypes\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\bsddb\\test\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\EFFMNWE-DECRYPT.txt",
"C:\\Program Files (x86)\\EFFMNWE-DECRYPT.html",
"C:\\Documents and Settings\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\distutils\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\distutils\\command\\EFFMNWE-DECRYPT.html",
"C:\\Python27\\Lib\\email\\test\\data\\EFFMNWE-DECRYPT.txt",
"C:\\Python27\\Lib\\ctypes\\EFFMNWE-DECRYPT.html"
],
"file_exists": [
"C:\\Windows\\System32\\cmd.exe"
],
"file_failed": [
"\\??\\B:",
"\\??\\A:"
],
"directory_enumerated": [
"C:\\cuckoo-agent\\*",
"C:\\Python27\\Lib\\email\\test\\data\\*",
"C:\\Python27\\*",
"C:\\Python27\\Lib\\ctypes\\*",
"C:\\Python27\\Lib\\distutils\\command\\*",
"C:\\Python27\\Doc\\*",
"C:\\Python27\\Lib\\bsddb\\*",
"C:\\Python27\\Lib\\curses\\*",
"C:\\Python27\\Lib\\distutils\\tests\\*",
"C:\\Python27\\Lib\\bsddb\\test\\*",
"C:\\Python27\\Lib\\email\\mime\\*",
"C:\\Python27\\Lib\\email\\*",
"C:\\$Recycle.Bin\\*",
"C:\\$Recycle.Bin\\S-1-5-21-699399860-4089948139-3198924279-1001\\*",
"C:\\Python27\\Lib\\email\\test\\*",
"C:\\Python27\\Lib\\*",
"C:\\Python27\\Lib\\distutils\\*",
"C:\\PerfLogs\\Admin\\*",
"C:\\Python27\\Lib\\ctypes\\macholib\\*",
"C:\\Python27\\Lib\\ctypes\\test\\*",
"C:\\$Recycle.Bin\\S-1-5-21-699399860-4089948139-3198924279-1001\\$R3U3MZB\\*",
"C:\\Python27\\DLLs\\*",
"C:\\Python27\\Lib\\compiler\\*",
"C:\\*",
"C:\\Python27\\include\\*",
"C:\\Python27\\Lib\\encodings\\*",
"C:\\PerfLogs\\*",
"C:\\Documents and Settings\\*"
]
},
"first_seen": 1589147587.625,
"ppid": 1664
},
{
"process_path": "C:\\Windows\\SysWOW64\\cmd.exe",
"process_name": "cmd.exe",
"pid": 2500,
"summary": {
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Command Processor"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\AutoRun",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\AutoRun",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\CompletionChar"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Users\\cuck",
"C:\\Users\\cuck\\AppData",
"C:\\Users\\cuck\\AppData\\Local",
"C:\\Users"
]
},
"first_seen": 1589147587.953125,
"ppid": 2740
}
]Signatures
[
{
"markcount": 2,
"families": [],
"description": "Command line console output was observed",
"severity": 1,
"marks": [
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleA",
"return_value": 1,
"arguments": {
"buffer": "~GandCrab ransomware decryptor~\r\n\r\n",
"console_handle": "0x00000007"
},
"time": 1589147587.688,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 39
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleA",
"return_value": 1,
"arguments": {
"buffer": "Decryption log path: C:\\Users\\cuck\\AppData\\Local\\Temp\\decryption_log_utf16.txt\r\n\r\nDo not remove it, it is needed for debugging some decryption problems.",
"console_handle": "0x00000007"
},
"time": 1589147587.688,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 43
}
],
"references": [],
"name": "console_output"
},
{
"markcount": 31,
"families": [],
"description": "Allocates read-write-execute memory (usually to unpack itself)",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147588.094,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 118
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147588.156,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 149
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147588.203,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 181
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147588.735,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 261
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147589.219,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 317
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147589.281,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 366
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147590.328,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 426
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147590.328,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 458
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147590.531,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 495
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147590.594,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 526
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147590.656,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 558
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147590.719,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 589
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147590.766,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 622
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147596.344,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 1027
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147596.86,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 1078
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147616.735,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 2586
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147621.36,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 2970
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147622.625,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 3098
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147632.281,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 3840
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147637.969,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 4291
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147638.031,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 4323
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147639.031,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 4422
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147652.047,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 5421
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147654.953,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 5664
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147656.219,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 5792
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147669.547,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 6820
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147681.922,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 7770
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147685.328,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 8058
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147688.219,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 8316
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147688.281,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 8348
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x003b0000"
},
"time": 1589147701.906,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2740,
"type": "call",
"cid": 9366
}
],
"references": [],
"name": "allocates_rwx"
},
{
"markcount": 1,
"families": [],
"description": "A process attempted to delay the analysis task.",
"severity": 2,
"marks": [
{
"type": "generic",
"description": "691ad9227ca29a3cee86043fbfeccfa7bc735cfabd14e108adb3be18420b0718.bin tried to sleep 125 seconds, actually delayed analysis time by 113 seconds"
}
],
"references": [],
"name": "antisandbox_sleep"
},
{
"markcount": 1,
"families": [],
"description": "Creates a suspicious process",
"severity": 2,
"marks": [
{
"category": "cmdline",
"ioc": "C:\\Windows\\system32\\cmd.exe \/c cls",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "suspicious_process"
},
{
"markcount": 1,
"families": [],
"description": "Writes a potential ransom message to disk",
"severity": 3,
"marks": [
{
"call": {
"category": "file",
"status": 0,
"stacktrace": [],
"last_error": 0,
"nt_status": -1073741592,
"api": "NtWriteFile",
"return_value": 3221225704,
"arguments": {
"file_handle": "0x00000094",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\decryption_log_utf16.txt",
"buffer": "\u0000\u0000\u0000\u0000\u0000\u0000]\u00df\u0097*\u00cb\u00ce\u0000\bh\u00e5<\u00008Z=\u0000\u000b\u0000\u0000\u0000\u00c0\u00d0\u00e0\u00f0\u00c1\u0015\u00d3\u0010\u0000\u0000\u0000\u008eH\u0000O\u0000M\u0000E\u0000D\u0000R\u0000I\u0000V\u0000E\u0000=\u0000C\u0000:\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00fc\u0015\u00d3\u0010\u0000\u0000\u0000\u008cO\u0000S\u0000=\u0000W\u0000i\u0000n\u0000d\u0000o\u0000w\u0000s\u0000_\u0000N\u0000T\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00fb\u0015\u00d3\u0010\u0000\u0000\u0000\u008aS\u0000y\u0000s\u0000t\u0000e\u0000m\u0000D\u0000r\u0000i\u0000v\u0000e\u0000=\u0000C\u0000:\u0000\u0000\u0000\u0000\u0000\u00f6\u0015\u00d3\u0010\u0000\u0000\u0000\u008cU\u0000S\u0000E\u0000R\u0000N\u0000A\u0000M\u0000E\u0000=\u0000c\u0000u\u0000c\u0000k\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00ed\u0015\u00d3\u0010\u0000\u0000\u0000\u0088\u0000\u0000\u0000\u0000\u00f0\u00e2\u00e1\u0000\u00b8m=\u0000xE=\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00e8\u0015\u00d3\u0010\u0000\u0000\u0000\u0088\u0000\u0000\u0000\u0000\u00d8\u00e2\u00e1\u0000\u00e0m=\u0000\u0090m=\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00e7\u0015\u00d3\u0010\u0000\u0000\u0000\u0088\u0000\u0000\u0000\u0000\u009c\u00e3\u00e1\u0000h\u0001\u00c9w\u00b8m=\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00e2\u0015\u00d3\u0010\u0000\u0000\u0000\u0088\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0099\u0015\u00d3\u0010\u0000\u0000\u0000\u0080\/\u0000?\u0000?\u0000\\\u0000C\u0000:\u0000\\\u0000U\u0000s\u0000e\u0000r\u0000s\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0094\u0015\u00d3\u0010\u0000\u0000\u0000\u00804\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0093\u0015\u00d3\u0010\u0000\u0000\u0000\u00809\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u008e\u0015\u00d3\u0010\u0000\u0000\u0000\u0080>\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0085\u0015\u00d3\u0010\u0000\u0000\u0000\u0080C\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0080\u0015\u00d3\u0010\u0000\u0000\u0000\u0080H\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00bf\u0015\u00d3\u0010\u0000\u0000\u0000\u0080M\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00ba\u0015\u00d3\u0010\u0000\u0000\u0000\u0080R\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00b1\u0015\u00d3\u0010\u0000\u0000\u0000\u0080W\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00ac\u0015\u00d3\u0010\u0000\u0000\u0000\u0080\\\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00ab\u0015\u00d3\u0010\u0000\u0000\u0000\u0080a\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00a6\u0015\u00d3\u0010\u0000\u0000\u0000\u0080f\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000]\u0016\u00d3\u0010\u0000\u0000\u0000\u0080k\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000X\u0016\u00d3\u0010\u0000\u0000\u0000\u0080p\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000W\u0016\u00d3\u0010\u0000\u0000\u0000\u0080u\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000R\u0016\u00d3\u0010\u0000\u0000\u0000\u0080z\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000I\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000D\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u0084\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000C\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u0089\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000~\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u008e\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000u\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u0093\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000p\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u0098\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000o\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u009d\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000j\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00a2\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000a\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00a7\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u001c\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00ac\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u001b\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00b1\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0016\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00b6\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\r\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00bb\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\b\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00c0\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0007\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00c5\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0002\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00ca\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00009\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00cf\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00004\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00d4\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00003\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00d9\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000.\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00de\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000%\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00e3\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000 \u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00e8\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00df\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00ed\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00da\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00f2\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00d1\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00f7\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00cc\u0016\u00d3\u0010\u0000\u0000\u0000\u0080\u00ff\u00ff\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000U\u00de\u009f+\u00cc\u00cf\u0000\fU\u0000S\u0000E\u0000R\u0000P\u0000R\u0000O\u0000F\u0000I\u0000L\u0000E\u0000=\u0000C\u0000:\u0000\\\u0000U\u0000s\u0000e\u0000r\u0000s\u0000\\\u0000c\u0000u\u0000c\u0000k\u0000\u0000\u0000\u0000\u0000\u0000\u0000[\u00de\u009f%\u00c4\u00ce\u0000\fw\u0000i\u0000n\u0000d\u0000i\u0000r\u0000=\u0000C\u0000:\u0000\\\u0000W\u0000i\u0000n\u0000d\u0000o\u0000w\u0000s\u0000\u0000\u0000\u0000\u0000\u0000\u0000Z\u00de\u009f$\u00ca\u00ce\u0000\bw\u0000i\u0000n\u0000d\u0000o\u0000w\u0000s\u0000_\u0000t\u0000r\u0000a\u0000c\u0000i\u0000n\u0000g\u0000_\u0000f\u0000l\u0000a\u0000g\u0000s\u0000=\u00003\u0000\u0000\u0000N\u00de\u009f0\u00cb\u00ce\u0000\fw\u0000i\u0000n\u0000d\u0000o\u0000w\u0000s\u0000_\u0000t\u0000r\u0000a\u0000c\u0000i\u0000n\u0000g\u0000_\u0000l\u0000o\u0000g\u0000f\u0000i\u0000l\u0000e\u0000=\u0000C\u0000:\u0000\\\u0000B\u0000V\u0000T\u0000B\u0000i\u0000n\u0000\\\u0000T\u0000e\u0000s\u0000t\u0000s\u0000\\\u0000i\u0000n\u0000s\u0000t\u0000a\u0000l\u0000l\u0000p\u0000a\u0000c\u0000k\u0000a\u0000g\u0000e\u0000\\\u0000c\u0000s\u0000i\u0000l\u0000o\u0000g\u0000f\u0000i\u0000l\u0000e\u0000.\u0000l\u0000o\u0000g\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00d4\u00de\u009f\u00aa\u00df\u00ce\u0000\b\u0000\u0000\u00e0\u0000\u00000\u0002\u0000\u0000\u0000\u0000\u0001\u00f4\u0000\u00f6\u0000$v=\u0000\\\u0000D\u0000e\u0000v\u0000i\u0000c\u0000e\u0000\\\u0000H\u0000a\u0000r\u0000d\u0000d\u0000i\u0000s\u0000k\u0000V\u0000o\u0000l\u0000u\u0000m\u0000e\u00002\u0000\\\u0000U\u0000s\u0000e\u0000r\u0000s\u0000\\\u0000c\u0000u\u0000c\u0000k\u0000\\\u0000A\u0000p\u0000p\u0000D\u0000a\u0000t\u0000a\u0000\\\u0000L\u0000o\u0000c\u0000a\u0000l\u0000\\\u0000T\u0000e\u0000m\u0000p\u0000\\\u00006\u00009\u00001\u0000a\u0000d\u00009\u00002\u00002\u00007\u0000c\u0000a\u00002\u00009\u0000a\u00003\u0000c\u0000e\u0000e\u00008\u00006\u00000\u00004\u00003\u0000f\u0000b\u0000f\u0000e\u0000c\u0000c\u0000f\u0000a\u00007\u0000b\u0000c\u00007\u00003\u00005\u0000c\u0000f\u0000a\u0000b\u0000d\u00001\u00004\u0000e\u00001\u00000\u00008\u0000a\u0000d\u0000b\u00003\u0000b\u0000e\u00001\u00008\u00004\u00002\u00000\u0000b\u00000\u00007\u00001\u00008\u0000.\u0000b\u0000i\u0000n\u0000\u0000\u0000\u00dcc.\u00ba\u00ddc-g\u00e0\u0000\u0082\u0097\u00e0\u0000P\u009a\u00e0\u0000+S\u00e0\u0000\u00ca3\u00bcu\u00d2\u009e\u00bcw\u00a5\u009e\u00bcw\u0000\u0000\u0000\u0000\u0018\u0000\u0000\u00004567\u0011\u0000\u0000\u0000<=>?@ABCDEFGHIJK\u0000\u0000\u0000\u0000\u0018\u0000\u0000\u0018\u00c4\u0000<\u0000;\u001d\u0000&\\]^_`abc\u0000\u0000\u0000\u0000\u0080\u0000\u0000\u0000lmno;\u001d\u0000&\u0010v=\u0000\u0001\u0000\u0000\u0000|}~\n\u0000\u0000\u0000\b\u0000\u0000\u0000\u0010l=\u0000\u0010l=\u0000\u000bl=\u0000\u0000\u0000\u0000\u0000\u0098\u0099\u009a\u0000\u0000\u0000<\u0000\u00a0\u00a1\u00a2\u0001\u00b4\u00fb5\u0000\u00a8\u00a9\u00aa\u00ab\u0098\u00fd5\u0000\u00cd\u001e\u00c0w\u00ca\u00be\u001d\u0000\u00fe\u00ff\u00ff\u00ff\u00a3<\u00bcw\u00ce<\u00bcw\u0080\u0000\u0000\u0000\u0088\u0000\u0000\u0000\nl=\u0000\u00e8\u00fc5\u0000\u00ba\u00ee\u00dccd\u00d2\u00e8c\u0000\u0000\u0000\u0000\u00e0\u00e1\u00e2\u00e3\u00e4\u00e5\u00e6\u00e7\u00e8\u00e9\u00ea\u00eb\u00ec\u00ed\u00ee\u00ef\u00f0\u00f1\u00f2\u00f3\u00f4\u00f5\u00f6\u00f7\u00f8\u00f9\u00fa\u00fb\u0000\u00d0\u00fd~\u00e8\u00fc5\u0000\u00ef~\u00dcc\u0018\u0000\u0000\u0000\u0001\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u00ce\u0087\u00bcu\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000E\u00de\u009f;E\u00ce\u0000\fM\u0000o\u0000d\u0000e\u0000:\u0000 \u0000F\u0000u\u0000l\u0000l\u0000 \u0000d\u0000e\u0000c\u0000r\u0000y\u0000p\u0000t\u0000i\u0000o\u0000n\u0000.\u0000 \u0000B\u0000a\u0000c\u0000k\u0000u\u0000p\u0000 \u0000f\u0000i\u0000l\u0000e\u0000s\u0000.\u0000 \u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\\\u00dc\u009f \u00d4\u00ce\u0000\bDecryption log path: C:\\Users\\cuck\\AppData\\Local\\Temp\\decryption_log_utf16.txt\n\nDo not remove it, it is needed for debugging some decryption problems.\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000\u0000",
"offset": 0
},
"time": 1589147587.688,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 62
}
],
"references": [],
"name": "ransomware_message"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 662,
"time": 6.188086986541748,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 5342,
"time": 12.188724040985107,
"dport": 138,
"sport": 138
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7186,
"time": 6.1231849193573,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7514,
"time": 4.125166893005371,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7842,
"time": 6.131793022155762,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8170,
"time": 4.627958059310913,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8498,
"time": 3.008759021759033,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 8826,
"time": 4.14624285697937,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 28236,
"time": 4.14650297164917,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 36620,
"time": 6.235976934432983,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "11748533f034db1e6be594aef10f0497804566113b29b142df6a73c286d57485",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "2df713c0196f94e6c2850130e4b56bb464c2fde06747883e638e8d97a599a53a",
"irc": [],
"https_ex": []
}Screenshots
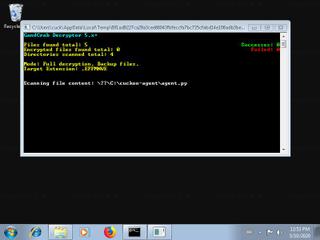
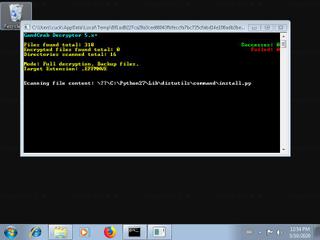
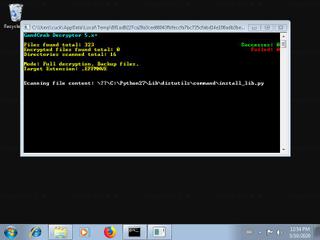
EFFMNWE.exe removal instructions
The instructions below shows how to remove EFFMNWE.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the EFFMNWE.exe file for removal, restart your computer and scan it again to verify that EFFMNWE.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate EFFMNWE.exe in the scan result and tick the checkbox next to the EFFMNWE.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate EFFMNWE.exe in the scan result.

 c:\downloads\EFFMNWE.exe
c:\downloads\EFFMNWE.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If EFFMNWE.exe still remains in the scan result, proceed with the next step. If EFFMNWE.exe is gone from the scan result you're done.
- If EFFMNWE.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that EFFMNWE.exe no longer appear in the scan result.
Hashes [?]
| Property | Value |
|---|---|
| MD5 | de60f021c69a1a44190f5d0282b8e2e2 |
| SHA256 | 691ad9227ca29a3cee86043fbfeccfa7bc735cfabd14e108adb3be18420b0718 |
Error Messages
These are some of the error messages that can appear related to effmnwe.exe:
effmnwe.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
effmnwe.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
effmnwe.exe has stopped working.
End Program - effmnwe.exe. This program is not responding.
effmnwe.exe is not a valid Win32 application.
effmnwe.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with EFFMNWE.exe?
To help other users, please let us know what you will do with EFFMNWE.exe:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.