What is cl987it.exe?
cl987it.exe is part of IntelCpHDCPSvc and developed by HOSTNAME according to the cl987it.exe version information.
cl987it.exe's description is "BingASDS"
cl987it.exe is usually located in the 'c:\downloads\' folder.
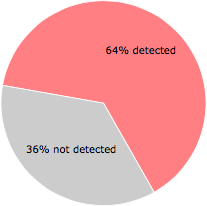
Some of the anti-virus scanners at VirusTotal detected cl987it.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Vendor and version information [?]
The following is the available information on cl987it.exe:
| Property | Value |
|---|---|
| Product name | IntelCpHDCPSvc |
| Company name | HOSTNAME |
| File description | BingASDS |
| Original filename | WmiPrvSE.exe |
| Legal copyright | sdclt |
| Product version | 471.294.862.825 |
| File version | 142.354.699.597 |
Here's a screenshot of the file properties when displayed by Windows Explorer:
| Product name | IntelCpHDCPSvc |
| Company name | HOSTNAME |
| File description | BingASDS |
| Original filename | WmiPrvSE.exe |
| Legal copyright | sdclt |
| Product version | 471.294.862.825 |
| File version | 142.354.699.597 |
Digital signatures [?]
cl987it.exe is not signed.
VirusTotal report
43 of the 67 anti-virus programs at VirusTotal detected the cl987it.exe file. That's a 64% detection rate.
| Scanner | Detection Name |
|---|---|
| Acronis | suspicious |
| AegisLab | Trojan.Win32.Autit.4!c |
| AhnLab-V3 | Trojan/Win32.Nymeria.R262941 |
| Alibaba | TrojanDropper:Win32/Autit.bfaa4d42 |
| Arcabit | AIT:Trojan.Nymeria.D778 |
| Avast | Win32:Trojan-gen |
| AVG | Win32:Trojan-gen |
| Avira | TR/Autoit.muyls |
| BitDefender | AIT:Trojan.Nymeria.1912 |
| ClamAV | Win.Malware.Generic-6937681-0 |
| CrowdStrike | win/malicious_confidence_90% (W) |
| Cybereason | malicious.a3b3b4 |
| Cyren | W32/Trojan.ACCN-2943 |
| DrWeb | Trojan.Inject3.13819 |
| Emsisoft | AIT:Trojan.Nymeria.1912 (B) |
| Endgame | malicious (high confidence) |
| ESET-NOD32 | a variant of Win32/Injector.Autoit.DWS |
| F-Secure | Trojan.TR/Autoit.muyls |
| FireEye | Generic.mg.f817368a3b3b40e1 |
| Fortinet | AutoIt/Injector.DWC!tr |
| GData | AIT:Trojan.Nymeria.1912 |
| Ikarus | Trojan.Autoit |
| Invincea | heuristic |
| K7AntiVirus | Trojan ( 700000111 ) |
| K7GW | Trojan ( 700000111 ) |
| Kaspersky | Trojan-Dropper.Win32.Autit.cql |
| Malwarebytes | Spyware.AzorUlt |
| MAX | malware (ai score=100) |
| MaxSecure | Trojan-Ransom.Win32.Gen.hwr |
| McAfee | Artemis!F817368A3B3B |
| McAfee-GW-Edition | AutoIt/Injector.af |
| Microsoft | Trojan:Win32/NjRat.SD!MTB |
| MicroWorld-eScan | AIT:Trojan.Nymeria.1912 |
| NANO-Antivirus | Trojan.Win32.Autit.fpbyzw |
| Paloalto | generic.ml |
| Panda | Trj/Genetic.gen |
| Qihoo-360 | Win32/Trojan.Dropper.78c |
| Sophos | Mal/Generic-S |
| Symantec | Trojan.Gen.MBT |
| Tencent | Win32.Trojan-dropper.Autit.Ebqd |
| Trapmine | suspicious.low.ml.score |
| TrendMicro-HouseCall | TROJ_GEN.R004C0DDH19 |
| ZoneAlarm | Trojan-Dropper.Win32.Autit.cql |
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"file_created": [
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Startup\\ie4uinit.url",
"C:\\Users\\cuck\\irftp\\MdRes.exe",
"C:\\Users\\cuck\\irftp\\ie4uinit.vbs"
],
"directory_created": [
"C:\\Users\\cuck\\irftp"
],
"dll_loaded": [
"Advapi32.dll",
"kernel32",
"SHELL32.dll",
"kernel32.dll",
"UxTheme.dll",
"dwmapi.dll",
"comctl32",
"ole32.dll",
"comctl32.dll",
"CRYPTSP.dll",
"IMM32.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\FolderDescriptions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\Compatibility\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}",
"HKEY_CURRENT_USER\\Control Panel\\Mouse",
"HKEY_CURRENT_USER\\Software\\AutoIt v3\\AutoIt"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Startup\\ie4uinit.url",
"C:\\Users\\cuck\\irftp\\ie4uinit.vbs",
"C:\\Users\\cuck\\irftp\\MdRes.exe"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin:Zone.Identifier",
"C:\\Users\\cuck\\irftp"
],
"mutex": [
"TSWbPrxy"
],
"command_line": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Icon",
"HKEY_CURRENT_USER\\Control Panel\\Mouse\\SwapMouseButtons",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\ProgramFilesDir",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\InitFolderHandler"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Users\\cuck",
"C:\\Users",
"C:\\Users\\cuck\\AppData\\Local",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin:Zone.Identifier"
]
}Dropped
[
{
"yara": [],
"sha1": "52e564c0c69eae77878f13f88bc0bfcf798f771c",
"name": "9065e6112b8dde9f_ie4uinit.url",
"filepath": "C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Startup\\ie4uinit.url",
"type": "MS Windows 95 Internet shortcut text (URL=), ASCII text, with CRLF line terminators",
"sha256": "9065e6112b8dde9fe61881183f3258072b2cbdfc5585140e77d108050a7b6d39",
"urls": [],
"crc32": "5661CCD0",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4545\/files\/9065e6112b8dde9f_ie4uinit.url",
"ssdeep": null,
"size": 61,
"sha512": "01050fd983ac6d4d7f98b6beb5ebcc3ea9410738824888b0630d379b766dddc21948927a7f7108387048da2d47de68b21ea1f02c5a4dcce48924221bdf6dc641",
"pids": [
2436
],
"md5": "d2ec1f3b252d1379d661b46ebe5e73af"
},
{
"yara": [],
"sha1": "d703522a0ddd05c5bd1f679baa5e0426aff18823",
"name": "e8222836320fc150_mdres.exe",
"filepath": "C:\\Users\\cuck\\irftp\\MdRes.exe",
"type": "PE32 executable (GUI) Intel 80386, for MS Windows",
"sha256": "e8222836320fc150fb89e5dece2f6e0436d3344a7d8022156ac00dbb3344b9b8",
"urls": [],
"crc32": "59496CFF",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4545\/files\/e8222836320fc150_mdres.exe",
"ssdeep": null,
"size": 1305664,
"sha512": "e7d352ffbfaf026243b4189aa06d439fdfa430af0d63ad237dac80e25c38149f027e73485bcdd64d4b94bbd1802ab832f58c21c936a57ee68d6a324c273f49e3",
"pids": [
2436
],
"md5": "7ca4f58d05a9e6392adde108b0405867"
},
{
"yara": [],
"sha1": "9c0ef91c1b675eb700e4b0cd2b1a99f8d9c7003e",
"name": "3f648cc8b5cc2bf4_ie4uinit.vbs",
"filepath": "C:\\Users\\cuck\\irftp\\ie4uinit.vbs",
"type": "ASCII text, with CRLF line terminators",
"sha256": "3f648cc8b5cc2bf4385c38efa47e94a250efe8ab7486e4ebd90f50c068a79636",
"urls": [],
"crc32": "FC6888CD",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4545\/files\/3f648cc8b5cc2bf4_ie4uinit.vbs",
"ssdeep": null,
"size": 102,
"sha512": "8bb40d24949290f26fb3d11153546989628ee77c1b9dcac8d6bd37c5a2fbddf6ffead7353cd98eef47ac7c13651504bdef2d069340520c24c93a6b82f3fc3c0a",
"pids": [
2436
],
"md5": "1f60cadf3337a31d249a10a7176a118c"
}
] Generic
[
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1577335985.328125,
"ppid": 376
},
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin",
"process_name": "3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin",
"pid": 2436,
"summary": {
"file_created": [
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Startup\\ie4uinit.url",
"C:\\Users\\cuck\\irftp\\MdRes.exe",
"C:\\Users\\cuck\\irftp\\ie4uinit.vbs"
],
"directory_created": [
"C:\\Users\\cuck\\irftp"
],
"dll_loaded": [
"Advapi32.dll",
"kernel32",
"SHELL32.dll",
"kernel32.dll",
"UxTheme.dll",
"dwmapi.dll",
"comctl32",
"ole32.dll",
"comctl32.dll",
"CRYPTSP.dll",
"IMM32.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\FolderDescriptions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\Compatibility\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}",
"HKEY_CURRENT_USER\\Control Panel\\Mouse",
"HKEY_CURRENT_USER\\Software\\AutoIt v3\\AutoIt"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Startup\\ie4uinit.url",
"C:\\Users\\cuck\\irftp\\ie4uinit.vbs",
"C:\\Users\\cuck\\irftp\\MdRes.exe"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin:Zone.Identifier",
"C:\\Users\\cuck\\irftp"
],
"mutex": [
"TSWbPrxy"
],
"command_line": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Icon",
"HKEY_CURRENT_USER\\Control Panel\\Mouse\\SwapMouseButtons",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\ProgramFilesDir",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{D65231B0-B2F1-4857-A4CE-A8E7C6EA7D27}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{F38BF404-1D43-42F2-9305-67DE0B28FC23}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{7C5A40EF-A0FB-4BFC-874A-C0F2E0B9FA8E}\\InitFolderHandler"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Users\\cuck",
"C:\\Users",
"C:\\Users\\cuck\\AppData\\Local",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba.bin:Zone.Identifier"
]
},
"first_seen": 1577335985.546875,
"ppid": 2660
}
]Signatures
[
{
"markcount": 1,
"families": [],
"description": "Checks if process is being debugged by a debugger",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 0,
"stacktrace": [],
"last_error": 0,
"nt_status": -1073741772,
"api": "IsDebuggerPresent",
"return_value": 0,
"arguments": {},
"time": 1577335985.671875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 68
}
],
"references": [],
"name": "checks_debugger"
},
{
"markcount": 0,
"families": [],
"description": "One or more potentially interesting buffers were extracted, these generally contain injected code, configuration data, etc.",
"severity": 2,
"marks": [],
"references": [],
"name": "dumped_buffer"
},
{
"markcount": 7,
"families": [],
"description": "Allocates read-write-execute memory (usually to unpack itself)",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2436,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x00a80000"
},
"time": 1577335988.015875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 7888
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2436,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x00d00000"
},
"time": 1577335988.062875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 7983
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2436,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x00d40000"
},
"time": 1577335988.078875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 7993
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2436,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x00d80000"
},
"time": 1577335988.093875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 8003
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2436,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x00dc0000"
},
"time": 1577335988.109875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 8013
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2436,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x00e00000"
},
"time": 1577335988.125875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 8023
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2436,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x00fa0000"
},
"time": 1577335988.140875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 8033
}
],
"references": [],
"name": "allocates_rwx"
},
{
"markcount": 12,
"families": [],
"description": "Terminates another process",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 487,
"nt_status": -1073741800,
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000000",
"process_identifier": 300,
"process_handle": "0x00000138"
},
"time": 1577335988.062875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 7988
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000000",
"process_identifier": 300,
"process_handle": "0x00000138"
},
"time": 1577335988.062875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 7989
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 487,
"nt_status": -1073741800,
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000000",
"process_identifier": 2804,
"process_handle": "0x00000134"
},
"time": 1577335988.078875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 7998
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000000",
"process_identifier": 2804,
"process_handle": "0x00000134"
},
"time": 1577335988.078875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 7999
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 487,
"nt_status": -1073741800,
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000000",
"process_identifier": 2284,
"process_handle": "0x00000140"
},
"time": 1577335988.093875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 8008
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000000",
"process_identifier": 2284,
"process_handle": "0x00000140"
},
"time": 1577335988.093875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 8009
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 487,
"nt_status": -1073741800,
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000000",
"process_identifier": 2628,
"process_handle": "0x00000148"
},
"time": 1577335988.109875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 8018
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000000",
"process_identifier": 2628,
"process_handle": "0x00000148"
},
"time": 1577335988.109875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 8019
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 487,
"nt_status": -1073741800,
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000000",
"process_identifier": 2844,
"process_handle": "0x00000150"
},
"time": 1577335988.125875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 8028
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000000",
"process_identifier": 2844,
"process_handle": "0x00000150"
},
"time": 1577335988.125875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 8029
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 487,
"nt_status": -1073741800,
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000000",
"process_identifier": 2408,
"process_handle": "0x00000158"
},
"time": 1577335988.140875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 8038
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000000",
"process_identifier": 2408,
"process_handle": "0x00000158"
},
"time": 1577335988.140875,
"tid": 2124,
"flags": {}
},
"pid": 2436,
"type": "call",
"cid": 8039
}
],
"references": [],
"name": "terminates_remote_process"
},
{
"markcount": 1,
"families": [],
"description": "One or more of the buffers contains an embedded PE file",
"severity": 3,
"marks": [
{
"category": "buffer",
"ioc": "Buffer with sha1: cb33e5df7243abd32fd7d6d0ef7b89a34e8241c7",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "dumped_buffer2"
},
{
"markcount": 6,
"families": [],
"description": "Allocates execute permission to another process indicative of possible code injection",
"severity": 3,
"marks": [
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -2147483642,
"api": "NtAllocateVirtualMemory",
"return_value": 3221225496,
"arguments": {
"process_identifier": 300,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000138",
"allocation_type": 12288,
"base_address": "0x00400000"
},
"time": 1577335988.062875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 7984
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -2147483642,
"api": "NtAllocateVirtualMemory",
"return_value": 3221225496,
"arguments": {
"process_identifier": 2804,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000134",
"allocation_type": 12288,
"base_address": "0x00400000"
},
"time": 1577335988.078875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 7994
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -2147483642,
"api": "NtAllocateVirtualMemory",
"return_value": 3221225496,
"arguments": {
"process_identifier": 2284,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x00400000"
},
"time": 1577335988.093875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 8004
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -2147483642,
"api": "NtAllocateVirtualMemory",
"return_value": 3221225496,
"arguments": {
"process_identifier": 2628,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000148",
"allocation_type": 12288,
"base_address": "0x00400000"
},
"time": 1577335988.109875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 8014
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -2147483642,
"api": "NtAllocateVirtualMemory",
"return_value": 3221225496,
"arguments": {
"process_identifier": 2844,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000150",
"allocation_type": 12288,
"base_address": "0x00400000"
},
"time": 1577335988.125875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 8024
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -2147483642,
"api": "NtAllocateVirtualMemory",
"return_value": 3221225496,
"arguments": {
"process_identifier": 2408,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000158",
"allocation_type": 12288,
"base_address": "0x00400000"
},
"time": 1577335988.140875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 8034
}
],
"references": [],
"name": "allocates_execute_remote_process"
},
{
"markcount": 1,
"families": [],
"description": "Installs itself for autorun at Windows startup",
"severity": 3,
"marks": [
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Startup\\ie4uinit.url",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "persistence_autorun"
},
{
"markcount": 12,
"families": [],
"description": "Manipulates memory of a non-child process indicative of process injection",
"severity": 3,
"marks": [
{
"category": "Process injection",
"ioc": "Process 2436 manipulating memory of non-child process 300",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -2147483642,
"api": "NtAllocateVirtualMemory",
"return_value": 3221225496,
"arguments": {
"process_identifier": 300,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000138",
"allocation_type": 12288,
"base_address": "0x00400000"
},
"time": 1577335988.062875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 7984
},
{
"category": "Process injection",
"ioc": "Process 2436 manipulating memory of non-child process 2804",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -2147483642,
"api": "NtAllocateVirtualMemory",
"return_value": 3221225496,
"arguments": {
"process_identifier": 2804,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000134",
"allocation_type": 12288,
"base_address": "0x00400000"
},
"time": 1577335988.078875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 7994
},
{
"category": "Process injection",
"ioc": "Process 2436 manipulating memory of non-child process 2284",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -2147483642,
"api": "NtAllocateVirtualMemory",
"return_value": 3221225496,
"arguments": {
"process_identifier": 2284,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000140",
"allocation_type": 12288,
"base_address": "0x00400000"
},
"time": 1577335988.093875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 8004
},
{
"category": "Process injection",
"ioc": "Process 2436 manipulating memory of non-child process 2628",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -2147483642,
"api": "NtAllocateVirtualMemory",
"return_value": 3221225496,
"arguments": {
"process_identifier": 2628,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000148",
"allocation_type": 12288,
"base_address": "0x00400000"
},
"time": 1577335988.109875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 8014
},
{
"category": "Process injection",
"ioc": "Process 2436 manipulating memory of non-child process 2844",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -2147483642,
"api": "NtAllocateVirtualMemory",
"return_value": 3221225496,
"arguments": {
"process_identifier": 2844,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000150",
"allocation_type": 12288,
"base_address": "0x00400000"
},
"time": 1577335988.125875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 8024
},
{
"category": "Process injection",
"ioc": "Process 2436 manipulating memory of non-child process 2408",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -2147483642,
"api": "NtAllocateVirtualMemory",
"return_value": 3221225496,
"arguments": {
"process_identifier": 2408,
"region_size": 221184,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000158",
"allocation_type": 12288,
"base_address": "0x00400000"
},
"time": 1577335988.140875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2436,
"type": "call",
"cid": 8034
}
],
"references": [
"www.endgame.com\/blog\/technical-blog\/ten-process-injection-techniques-technical-survey-common-and-trending-process"
],
"name": "injection_modifies_memory"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 546,
"time": 3.0781819820404053,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 5226,
"time": 9.078963994979858,
"dport": 138,
"sport": 138
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7070,
"time": 3.0108401775360107,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7398,
"time": 1.036879062652588,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7726,
"time": 3.018721103668213,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8054,
"time": 1.6424281597137451,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8382,
"time": -0.0886988639831543,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 8710,
"time": 1.1260759830474854,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 28120,
"time": 1.0703799724578857,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 36504,
"time": 3.144282102584839,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "5808fb0895fb030b1868bf5f6cf8c3a805c01fd43a95167d30ab573e78cab5e1",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "3652118aa9c9133867b0ae4132364d61816ce9f54213f76d4f13c99d57a5dce4",
"irc": [],
"https_ex": []
}Screenshots
cl987it.exe removal instructions
The instructions below shows how to remove cl987it.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the cl987it.exe file for removal, restart your computer and scan it again to verify that cl987it.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate cl987it.exe in the scan result and tick the checkbox next to the cl987it.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate cl987it.exe in the scan result.

 c:\downloads\cl987it.exe
c:\downloads\cl987it.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If cl987it.exe still remains in the scan result, proceed with the next step. If cl987it.exe is gone from the scan result you're done.
- If cl987it.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that cl987it.exe no longer appear in the scan result.
Hashes [?]
| Property | Value |
|---|---|
| MD5 | f817368a3b3b40e1e87ee58a696989f6 |
| SHA256 | 3d54b369591fef010c619416ebad0fe9595ad2fb0afd4eda04132adbf07cf9ba |
Error Messages
These are some of the error messages that can appear related to cl987it.exe:
cl987it.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
cl987it.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
BingASDS has stopped working.
End Program - cl987it.exe. This program is not responding.
cl987it.exe is not a valid Win32 application.
cl987it.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with cl987it.exe?
To help other users, please let us know what you will do with cl987it.exe:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.