What is ctszxscq.exe?
ctszxscq.exe is part of ???????? according to the ctszxscq.exe version information.
ctszxscq.exe's description is "????????"
ctszxscq.exe is usually located in the 'c:\downloads\' folder.
Some of the anti-virus scanners at VirusTotal detected ctszxscq.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Vendor and version information [?]
The following is the available information on ctszxscq.exe:
| Property | Value |
|---|---|
| Product name | ???????? |
| File description | ???????? |
| Comments | ???????? |
| Legal copyright | ???????? |
| Product version | 3.5.0.0 |
| File version | 3.5.0.0 |
Here's a screenshot of the file properties when displayed by Windows Explorer:
| Product name | ???????? |
| File description | ???????? |
| Comments | ???????? |
| Legal copyright | ???????? |
| Product version | 3.5.0.0 |
| File version | 3.5.0.0 |
Digital signatures [?]
ctszxscq.exe is not signed.
VirusTotal report
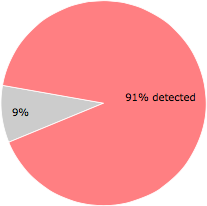
62 of the 68 anti-virus programs at VirusTotal detected the ctszxscq.exe file. That's a 91% detection rate.
| Scanner | Detection Name |
|---|---|
| Acronis | suspicious |
| Ad-Aware | Win32.Ramnit.Dam |
| AegisLab | Virus.Win32.Nimnul.n!c |
| AhnLab-V3 | Win32/Ramnit.B |
| Alibaba | Virus:Win32/Ramnit.c8460e55 |
| ALYac | Win32.Ramnit.Dam |
| Antiy-AVL | Virus/Win32.Nimnul.a |
| Arcabit | Win32.Ramnit.Dam |
| Avast | Win32:RmnDrp |
| AVG | Win32:RmnDrp |
| Avira | W32/Ramnit.CD |
| Baidu | Win32.Virus.Nimnul.a |
| BitDefender | Win32.Ramnit.Dam |
| Bkav | W32.RammitNNA.PE |
| CAT-QuickHeal | W32.Ramnit.A |
| ClamAV | Win.Trojan.Ramnit-1847 |
| Comodo | Virus.Win32.Ramnit.A@1xq65p |
| CrowdStrike | win/malicious_confidence_100% (W) |
| Cybereason | malicious.59dc85 |
| Cyren | W32/Ramnit.B!Generic |
| DrWeb | Win32.Rmnet |
| eGambit | Unsafe.AI_Score_98% |
| Emsisoft | Win32.Ramnit.Dam (B) |
| Endgame | malicious (high confidence) |
| ESET-NOD32 | Win32/Ramnit.A |
| F-Prot | W32/Ramnit.B!Generic |
| F-Secure | Malware.W32/Ramnit.CD |
| FireEye | Generic.mg.f298a6a59dc8528a |
| Fortinet | W32/Ramnit.A |
| GData | Win32.Virus.Ramnit.C |
| Ikarus | Virus.Ramnit |
| Invincea | heuristic |
| Jiangmin | Win32/PatchFile.et |
| K7AntiVirus | Virus ( 002fe95d1 ) |
| K7GW | Adware ( 004b942f1 ) |
| Kaspersky | Virus.Win32.Nimnul.a |
| Kingsoft | Win32.Ramnit.la.30720 |
| MAX | malware (ai score=100) |
| McAfee | W32/Ramnit.a |
| McAfee-GW-Edition | BehavesLike.Win32.Ramnit.tc |
| Microsoft | Virus:Win32/Ramnit.A |
| MicroWorld-eScan | Win32.Ramnit.Dam |
| NANO-Antivirus | Virus.Win32.Nimnul.bpchjo |
| Paloalto | generic.ml |
| Panda | W32/Cosmu.gen |
| Qihoo-360 | Virus.Win32.Ramnit.B |
| Rising | Virus.Ramnit!1.9AA5 (CLOUD) |
| SentinelOne | DFI - Malicious PE |
| Sophos | W32/Patched-I |
| Symantec | W32.Ramnit!inf |
| TACHYON | Virus/W32.Ramnit.B |
| Tencent | Virus.Win32.Nimnul.d |
| TotalDefense | Win32/Ramnit.A |
| Trapmine | malicious.high.ml.score |
| TrendMicro-HouseCall | PE_RAMNIT.H |
| VBA32 | Virus.Win32.Nimnul.a |
| VIPRE | Virus.Win32.Ramnit.a (v) |
| ViRobot | Win32.Ramnit.E |
| Yandex | Win32.Ramnit.Gen.3 |
| Zillya | Virus.Nimnul.Win32.1 |
| ZoneAlarm | Virus.Win32.Nimnul.a |
| Zoner | Trojan.Win32.Ramnit.23698 |
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"file_created": [
"C:\\Program Files (x86)\\Microsoft\\px58E2.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192Srv.exe"
],
"file_recreated": [
"C:\\Program Files (x86)\\Microsoft\\px58E2.tmp"
],
"directory_created": [
"C:\\Program Files (x86)\\Microsoft"
],
"dll_loaded": [
"C:\\Windows\\System32\\mswsock.dll",
"MSVFW32.dll",
"DNSAPI.dll",
"kernel32.dll",
"UxTheme.dll",
"C:\\Windows\\system32\\ole32.dll",
"dwmapi.dll",
"C:\\Windows\\system32\\napinsp.dll",
"USER32.DLL",
"API-MS-WIN-Service-Management-L1-1-0.dll",
"KERNEL32.DLL",
"API-MS-WIN-Service-winsvc-L1-1-0.dll",
"advapi32.dll",
"comctl32",
"ole32.dll",
"USER32.dll",
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"RASMAN.DLL",
"rtutils.dll",
"IPHLPAPI.DLL",
"wininet.dll",
"ADVAPI32.dll",
"OLEAUT32.dll",
"C:\\Windows\\system32\\pnrpnsp.dll",
"DHCPCSVC.DLL",
"C:\\Windows\\System32\\winrnr.dll",
"COMCTL32.dll",
"DCIMAN32.DLL",
"GDI32.dll",
"Kernel32.dll",
"MSVCRT.dll",
"C:\\Windows\\SysWOW64\\oleaut32.dll",
"SHELL32.DLL",
"WS2_32.dll",
"MSIMG32.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192.bin",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"file_copied": [
[
"C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192Srv.exe",
"C:\\Program Files (x86)\\Microsoft\\DesktopLayer.exe"
]
],
"connects_host": [
"www.shinannan.cn",
"t.163.com"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\TreatAs",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\DnsCache\\Parameters",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\DnsClient",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{8613E14C-D0C0-4161-AC0F-1DD2563286BC}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\LanguagePack\\SurrogateFallback\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{AE6BE008-07FB-400D-8BEB-337A64F7051F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Tracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Tracing\\RASMANCS",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\LanguageProfile\\0x00000000\\{0001bea3-ed56-483d-a2e2-aeae25577436}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{E429B25A-E5D3-4D1F-9BE3-0C608477E3A1}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{C1EE01F2-B3B6-4A6A-9DDD-E988C088EC82}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{07EB03D6-B001-41DF-9192-BF9B841EE71F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\Progid",
"HKEY_CURRENT_USER\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\OleAut",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocHandler32",
"HKEY_CURRENT_USER\\Software\\Microsoft\\windows\\CurrentVersion\\Internet Settings\\Connections",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\Compatibility\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192.bin",
"HKEY_CURRENT_USER\\Software\\Microsoft\\CTF\\DirectSwitchHotkeys",
"HKEY_CURRENT_USER\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\LanguagePack\\SurrogateFallback",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\VFW",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{F89E9E58-BD2F-4008-9AC2-0F816C09F4EE}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\Progid",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{DCBD6FA8-032F-11D3-B5B1-00C04FC324A1}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Multimedia\\DrawDib",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{3697C5FA-60DD-4B56-92D4-74A569205C16}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocHandler",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\Tcpip\\Parameters",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{531FDEBF-9B4C-4A43-A2AA-960E8FCDC732}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{F25E9F57-2FC8-4EB3-A41A-CCE5F08541E6}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\windows\\CurrentVersion\\Internet Settings\\Wpad",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{A028AE76-01B1-46C2-99C4-ACD9858AE02F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CLASSES_ROOT\\http\\shell\\open\\command",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}",
"HKEY_CURRENT_USER\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{81D4E9C9-1D3B-41BC-9E6C-4B40BF79E35E}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{03B5835F-F03C-411B-9CE2-AA23E1171E36}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\KnownClasses",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\LanguagePack\\SurrogateFallback\\Arial",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\System\\DNSClient",
"HKEY_CURRENT_USER\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{78CB5B0E-26ED-4FCC-854C-77E8F3D1AA80}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\",
"HKEY_CURRENT_USER\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}"
],
"resolves_host": [
"wpad",
"cuckpc"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192Srv.exe"
],
"file_deleted": [
"C:\\Program Files (x86)\\Microsoft\\px58E2.tmp"
],
"file_exists": [
"C:\\Program Files (x86)\\Microsoft"
],
"mutex": [
"KyUffThOkYwRRtgPP",
"IESQMMUTEX_0_208"
],
"guid": [
"{a47979d2-c419-11d9-a5b4-001185ad2b89}",
"{dcb00c01-570f-4a9b-8d69-199fdba5723b}",
"{dcb00000-570f-4a9b-8d69-199fdba5723b}",
"{d0074ffd-570f-4a9b-8d69-199fdba5723b}"
],
"command_line": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192Srv.exe",
"C:\\Program Files (x86)\\Microsoft\\DesktopLayer.exe"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192.bin"
],
"regkey_read": [
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Language Hotkey",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Hotkey",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\http\\shell\\open\\command\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\ThreadingModel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\AppData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Layout Hotkey",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\FileDirectory",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\ProgramData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\FileTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\CTF\\EnableAnchorContext",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\AutoProxyDetectType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\LanguageProfile\\0x00000000\\{0001bea3-ed56-483d-a2e2-aeae25577436}\\Enable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileTracingMask",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileDirectory",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\MaxFileSize",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\(Default)"
],
"directory_enumerated": [
"C:\\ProgramData\\Microsoft\\Network\\Connections\\Pbk\\rasphone.pbk",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Network\\Connections\\Pbk\\*.pbk",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Network\\Connections\\Pbk\\rasphone.pbk",
"C:\\ProgramData\\Microsoft\\Network\\Connections\\Pbk\\*.pbk",
"C:\\Program Files (x86)\\Mozilla Firefox\\firefox.exe",
"C:\\Windows\\System32\\ras\\*.pbk"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableConsoleTracing",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionReason",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecision",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadNetworkName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableFileTracing",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileTracingMask",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionTime",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileDirectory",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Multimedia\\DrawDib\\ 800x600x32(BGR 0)"
]
}Dropped
[
{
"yara": [],
"sha1": "b4fa74a6f4dab3a7ba702b6c8c129f889db32ca6",
"name": "fd6c69c345f1e329_489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192srv.exe",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192Srv.exe",
"type": "PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed",
"sha256": "fd6c69c345f1e32924f0a5bb7393e191b393a78d58e2c6413b03ced7482f2320",
"urls": [],
"crc32": "40C57347",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4542\/files\/fd6c69c345f1e329_489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192srv.exe",
"ssdeep": null,
"size": 56320,
"sha512": "c9d654ead35f40eea484a3dc5b5d0a44294b9e7b41a9bacdafdd463d3de9daa2a43237a5f113f6a9c8ea5e1366823fd3d83da18cd8197aa69a55e9f345512a7a",
"pids": [
1268
],
"md5": "ff5e1f27193ce51eec318714ef038bef"
},
{
"yara": [],
"sha1": "da39a3ee5e6b4b0d3255bfef95601890afd80709",
"name": "e3b0c44298fc1c14_px58E2.tmp",
"type": "empty",
"sha256": "e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855",
"urls": [],
"crc32": "00000000",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4542\/files\/e3b0c44298fc1c14_px58E2.tmp",
"ssdeep": null,
"size": 0,
"sha512": "cf83e1357eefb8bdf1542850d66d8007d620e4050b5715dc83f4a921d36ce9ce47d0d13c5d85f2b0ff8318d2877eec2f63b931bd47417a81a538327af927da3e",
"md5": "d41d8cd98f00b204e9800998ecf8427e"
}
]Generic
[
{
"process_path": "C:\\Program Files (x86)\\Microsoft\\DesktopLayer.exe",
"process_name": "DesktopLayer.exe",
"pid": 2584,
"summary": {
"dll_loaded": [
"SHELL32.DLL",
"advapi32.dll",
"KERNEL32.DLL",
"kernel32.dll",
"USER32.DLL"
],
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CLASSES_ROOT\\http\\shell\\open\\command"
],
"mutex": [
"KyUffThOkYwRRtgPP"
],
"regkey_read": [
"HKEY_CURRENT_USER\\http\\shell\\open\\command\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US"
],
"directory_enumerated": [
"C:\\Program Files (x86)\\Mozilla Firefox\\firefox.exe"
]
},
"first_seen": 1577325186.046875,
"ppid": 856
},
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192Srv.exe",
"process_name": "489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192Srv.exe",
"pid": 856,
"summary": {
"file_created": [
"C:\\Program Files (x86)\\Microsoft\\px58E2.tmp"
],
"file_recreated": [
"C:\\Program Files (x86)\\Microsoft\\px58E2.tmp"
],
"directory_created": [
"C:\\Program Files (x86)\\Microsoft"
],
"dll_loaded": [
"SHELL32.DLL",
"advapi32.dll",
"KERNEL32.DLL",
"kernel32.dll",
"USER32.DLL"
],
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"file_copied": [
[
"C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192Srv.exe",
"C:\\Program Files (x86)\\Microsoft\\DesktopLayer.exe"
]
],
"regkey_opened": [
"HKEY_CLASSES_ROOT\\http\\shell\\open\\command"
],
"file_deleted": [
"C:\\Program Files (x86)\\Microsoft\\px58E2.tmp"
],
"file_exists": [
"C:\\Program Files (x86)\\Microsoft"
],
"mutex": [
"KyUffThOkYwRRtgPP"
],
"command_line": [
"C:\\Program Files (x86)\\Microsoft\\DesktopLayer.exe"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_CURRENT_USER\\http\\shell\\open\\command\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US"
],
"directory_enumerated": [
"C:\\Program Files (x86)\\Mozilla Firefox\\firefox.exe"
]
},
"first_seen": 1577325185.84375,
"ppid": 1268
},
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1577325185.328125,
"ppid": 376
},
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192.bin",
"process_name": "489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192.bin",
"pid": 1268,
"summary": {
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192Srv.exe"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableConsoleTracing",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionReason",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecision",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadNetworkName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableFileTracing",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileTracingMask",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionTime",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileDirectory",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Multimedia\\DrawDib\\ 800x600x32(BGR 0)"
],
"dll_loaded": [
"C:\\Windows\\system32\\pnrpnsp.dll",
"MSVFW32.dll",
"DNSAPI.dll",
"kernel32.dll",
"UxTheme.dll",
"C:\\Windows\\system32\\ole32.dll",
"dwmapi.dll",
"C:\\Windows\\system32\\napinsp.dll",
"API-MS-WIN-Service-Management-L1-1-0.dll",
"KERNEL32.DLL",
"API-MS-WIN-Service-winsvc-L1-1-0.dll",
"comctl32",
"ole32.dll",
"USER32.dll",
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"RASMAN.DLL",
"rtutils.dll",
"IPHLPAPI.DLL",
"wininet.dll",
"OLEAUT32.dll",
"C:\\Windows\\System32\\mswsock.dll",
"DHCPCSVC.DLL",
"C:\\Windows\\System32\\winrnr.dll",
"COMCTL32.dll",
"DCIMAN32.DLL",
"GDI32.dll",
"Kernel32.dll",
"MSVCRT.dll",
"C:\\Windows\\SysWOW64\\oleaut32.dll",
"ADVAPI32.dll",
"WS2_32.dll",
"MSIMG32.dll"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\TreatAs",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\DnsCache\\Parameters",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\DnsClient",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{8613E14C-D0C0-4161-AC0F-1DD2563286BC}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\LanguagePack\\SurrogateFallback\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{AE6BE008-07FB-400D-8BEB-337A64F7051F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Tracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Tracing\\RASMANCS",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\LanguageProfile\\0x00000000\\{0001bea3-ed56-483d-a2e2-aeae25577436}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{E429B25A-E5D3-4D1F-9BE3-0C608477E3A1}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{C1EE01F2-B3B6-4A6A-9DDD-E988C088EC82}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{07EB03D6-B001-41DF-9192-BF9B841EE71F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\Progid",
"HKEY_CURRENT_USER\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\OleAut",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocHandler32",
"HKEY_CURRENT_USER\\Software\\Microsoft\\windows\\CurrentVersion\\Internet Settings\\Connections",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\Compatibility\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192.bin",
"HKEY_CURRENT_USER\\Software\\Microsoft\\CTF\\DirectSwitchHotkeys",
"HKEY_CURRENT_USER\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\LanguagePack\\SurrogateFallback",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\VFW",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{F89E9E58-BD2F-4008-9AC2-0F816C09F4EE}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\Progid",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{DCBD6FA8-032F-11D3-B5B1-00C04FC324A1}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Multimedia\\DrawDib",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{3697C5FA-60DD-4B56-92D4-74A569205C16}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocHandler",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\Tcpip\\Parameters",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{531FDEBF-9B4C-4A43-A2AA-960E8FCDC732}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{F25E9F57-2FC8-4EB3-A41A-CCE5F08541E6}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\windows\\CurrentVersion\\Internet Settings\\Wpad",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{A028AE76-01B1-46C2-99C4-ACD9858AE02F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}",
"HKEY_CURRENT_USER\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{81D4E9C9-1D3B-41BC-9E6C-4B40BF79E35E}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{03B5835F-F03C-411B-9CE2-AA23E1171E36}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\KnownClasses",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\LanguagePack\\SurrogateFallback\\Arial",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\System\\DNSClient",
"HKEY_CURRENT_USER\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{78CB5B0E-26ED-4FCC-854C-77E8F3D1AA80}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}"
],
"connects_host": [
"www.shinannan.cn",
"t.163.com"
],
"command_line": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192Srv.exe"
],
"resolves_host": [
"wpad",
"cuckpc"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192Srv.exe"
],
"mutex": [
"KyUffThOkYwRRtgPP",
"IESQMMUTEX_0_208"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192.bin"
],
"guid": [
"{a47979d2-c419-11d9-a5b4-001185ad2b89}",
"{dcb00c01-570f-4a9b-8d69-199fdba5723b}",
"{dcb00000-570f-4a9b-8d69-199fdba5723b}",
"{d0074ffd-570f-4a9b-8d69-199fdba5723b}"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192.bin"
],
"regkey_read": [
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Language Hotkey",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Hotkey",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\LanguageProfile\\0x00000000\\{0001bea3-ed56-483d-a2e2-aeae25577436}\\Enable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\ThreadingModel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\AppData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Layout Hotkey",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\FileDirectory",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\FileTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\CTF\\EnableAnchorContext",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\AutoProxyDetectType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\ProgramData",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileDirectory",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\MaxFileSize",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\(Default)"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Network\\Connections\\Pbk\\rasphone.pbk",
"C:\\ProgramData\\Microsoft\\Network\\Connections\\Pbk\\rasphone.pbk",
"C:\\Windows\\System32\\ras\\*.pbk",
"C:\\ProgramData\\Microsoft\\Network\\Connections\\Pbk\\*.pbk",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Network\\Connections\\Pbk\\*.pbk"
]
},
"first_seen": 1577325185.640625,
"ppid": 3040
}
]Signatures
[
{
"markcount": 1,
"families": [],
"description": "The executable contains unknown PE section names indicative of a packer (could be a false positive)",
"severity": 1,
"marks": [
{
"category": "section",
"ioc": ".rmnet",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "pe_features"
},
{
"markcount": 1,
"families": [],
"description": "The file contains an unknown PE resource name possibly indicative of a packer",
"severity": 1,
"marks": [
{
"category": "resource name",
"ioc": "TEXTINCLUDE",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "pe_unknown_resource_name"
},
{
"markcount": 1,
"families": [],
"description": "One or more processes crashed",
"severity": 1,
"marks": [
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "C\nh\ne\nc\nk\nE\nl\ne\nv\na\nt\ni\no\nn\nE\nn\na\nb\nl\ne\nd\n+\n0\nx\n4\na\n7\n \nB\na\ns\ne\nG\ne\nn\ne\nr\na\nt\ne\nA\np\np\nC\no\nm\np\na\nt\nD\na\nt\na\n-\n0\nx\n1\n5\n2\n \nk\ne\nr\nn\ne\nl\n3\n2\n+\n0\nx\n2\n3\n6\n0\n5\n \n@\n \n0\nx\n7\n5\nb\nd\n3\n6\n0\n5\n\n\nC\nh\ne\nc\nk\nE\nl\ne\nv\na\nt\ni\no\nn\nE\nn\na\nb\nl\ne\nd\n+\n0\nx\n2\na\n3\n \nB\na\ns\ne\nG\ne\nn\ne\nr\na\nt\ne\nA\np\np\nC\no\nm\np\na\nt\nD\na\nt\na\n-\n0\nx\n3\n5\n6\n \nk\ne\nr\nn\ne\nl\n3\n2\n+\n0\nx\n2\n3\n4\n0\n1\n \n@\n \n0\nx\n7\n5\nb\nd\n3\n4\n0\n1\n\n\nC\nh\ne\nc\nk\nE\nl\ne\nv\na\nt\ni\no\nn\nE\nn\na\nb\nl\ne\nd\n+\n0\nx\n1\n9\n0\n \nB\na\ns\ne\nG\ne\nn\ne\nr\na\nt\ne\nA\np\np\nC\no\nm\np\na\nt\nD\na\nt\na\n-\n0\nx\n4\n6\n9\n \nk\ne\nr\nn\ne\nl\n3\n2\n+\n0\nx\n2\n3\n2\ne\ne\n \n@\n \n0\nx\n7\n5\nb\nd\n3\n2\ne\ne\n\n\nC\nr\ne\na\nt\ne\nP\nr\no\nc\ne\ns\ns\nI\nn\nt\ne\nr\nn\na\nl\nW\n+\n0\nx\nc\n6\n5\n \nB\na\ns\ne\np\nF\nr\ne\ne\nA\np\np\nC\no\nm\np\na\nt\nD\na\nt\na\n-\n0\nx\n4\nd\n9\n \nk\ne\nr\nn\ne\nl\n3\n2\n+\n0\nx\n2\n4\n8\n5\n8\n \n@\n \n0\nx\n7\n5\nb\nd\n4\n8\n5\n8\n\n\nN\ne\nw\n_\nk\ne\nr\nn\ne\nl\n3\n2\n_\nC\nr\ne\na\nt\ne\nP\nr\no\nc\ne\ns\ns\nI\nn\nt\ne\nr\nn\na\nl\nW\n@\n4\n8\n+\n0\nx\n1\n8\n7\n \nN\ne\nw\n_\nk\ne\nr\nn\ne\nl\n3\n2\n_\nC\nr\ne\na\nt\ne\nR\ne\nm\no\nt\ne\nT\nh\nr\ne\na\nd\n@\n2\n8\n-\n0\nx\n1\n6\nb\n \n@\n \n0\nx\n6\n3\nd\nd\n7\n8\n2\n4\n\n\nC\nr\ne\na\nt\ne\nP\nr\no\nc\ne\ns\ns\nI\nn\nt\ne\nr\nn\na\nl\nA\n+\n0\nx\n1\n2\n3\n \nS\ne\nt\nC\no\nn\ns\no\nl\ne\nM\no\nd\ne\n-\n0\nx\n1\na\n3\n \nk\ne\nr\nn\ne\nl\n3\n2\n+\n0\nx\n2\na\n5\nd\na\n \n@\n \n0\nx\n7\n5\nb\nd\na\n5\nd\na\n\n\nC\nr\ne\na\nt\ne\nP\nr\no\nc\ne\ns\ns\nA\n+\n0\nx\n2\nc\n \nS\nl\ne\ne\np\n-\n0\nx\n6\n1\n \nk\ne\nr\nn\ne\nl\n3\n2\n+\n0\nx\n1\n1\n0\n9\ne\n \n@\n \n0\nx\n7\n5\nb\nc\n1\n0\n9\ne\n\n\nd\ne\ns\nk\nt\no\np\nl\na\ny\ne\nr\n+\n0\nx\n1\n3\nc\n0\n \n@\n \n0\nx\n4\n0\n1\n3\nc\n0\n\n\nd\ne\ns\nk\nt\no\np\nl\na\ny\ne\nr\n+\n0\nx\n2\nc\nd\na\n \n@\n \n0\nx\n4\n0\n2\nc\nd\na\n\n\nR\nt\nl\nI\nn\ni\nt\ni\na\nl\ni\nz\ne\nE\nx\nc\ne\np\nt\ni\no\nn\nC\nh\na\ni\nn\n+\n0\nx\n6\n3\n \nR\nt\nl\nA\nl\nl\no\nc\na\nt\ne\nA\nc\nt\ni\nv\na\nt\ni\no\nn\nC\no\nn\nt\ne\nx\nt\nS\nt\na\nc\nk\n-\n0\nx\na\n1\n \nn\nt\nd\nl\nl\n+\n0\nx\n3\n9\ne\nd\n2\n \n@\n \n0\nx\n7\n7\nb\nc\n9\ne\nd\n2\n\n\nR\nt\nl\nI\nn\ni\nt\ni\na\nl\ni\nz\ne\nE\nx\nc\ne\np\nt\ni\no\nn\nC\nh\na\ni\nn\n+\n0\nx\n3\n6\n \nR\nt\nl\nA\nl\nl\no\nc\na\nt\ne\nA\nc\nt\ni\nv\na\nt\ni\no\nn\nC\no\nn\nt\ne\nx\nt\nS\nt\na\nc\nk\n-\n0\nx\nc\ne\n \nn\nt\nd\nl\nl\n+\n0\nx\n3\n9\ne\na\n5\n \n@\n \n0\nx\n7\n7\nb\nc\n9\ne\na\n5",
"registers": {
"esp": 1634936,
"edi": 1635572,
"eax": 1635008,
"ebp": 1634968,
"edx": 83,
"ebx": 1636324,
"esi": 2008743428,
"ecx": 731540836
},
"exception": {
"symbol": "",
"exception_code": "0xc0000005",
"address": "0xec663f6c"
}
},
"time": 1577325186.187875,
"tid": 2576,
"flags": {}
},
"pid": 2584,
"type": "call",
"cid": 1447
}
],
"references": [],
"name": "raises_exception"
},
{
"markcount": 79,
"families": [],
"description": "Allocates read-write-execute memory (usually to unpack itself)",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"region_size": 253952,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x10000000"
},
"time": 1577325185.781625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 1268,
"type": "call",
"cid": 67
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10000000"
},
"time": 1577325185.796625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 303
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 334
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x7631d000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 335
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 337
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 338
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x76318000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 339
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 341
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 342
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763ad000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 343
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 345
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 346
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763b6000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 347
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 349
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 350
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763a8000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 351
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 353
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 354
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 8192,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763a6000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 355
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 357
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 358
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763b1000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 359
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 361
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 362
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763b1000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 363
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 365
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 366
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763a7000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 367
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 369
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 370
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763a8000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 371
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 373
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 374
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763a7000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 375
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 377
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 378
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763b1000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 379
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 381
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 382
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763b4000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 383
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 385
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 386
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763b4000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 387
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 389
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 390
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763b9000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 391
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 393
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 394
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x763b3000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 395
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1268,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10009000"
},
"time": 1577325185.812625,
"tid": 2740,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1268,
"type": "call",
"cid": 397
}
],
"references": [],
"name": "allocates_rwx"
},
{
"markcount": 51,
"families": [],
"description": "Foreign language identified in PE resource",
"severity": 2,
"marks": [
{
"name": "TEXTINCLUDE",
"language": "LANG_CHINESE",
"offset": "0x001c0b78",
"filetype": "C source, ASCII text, with CRLF line terminators",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000151"
},
{
"name": "TEXTINCLUDE",
"language": "LANG_CHINESE",
"offset": "0x001c0b78",
"filetype": "C source, ASCII text, with CRLF line terminators",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000151"
},
{
"name": "TEXTINCLUDE",
"language": "LANG_CHINESE",
"offset": "0x001c0b78",
"filetype": "C source, ASCII text, with CRLF line terminators",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000151"
},
{
"name": "RT_CURSOR",
"language": "LANG_CHINESE",
"offset": "0x001c1068",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x000000b4"
},
{
"name": "RT_CURSOR",
"language": "LANG_CHINESE",
"offset": "0x001c1068",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x000000b4"
},
{
"name": "RT_CURSOR",
"language": "LANG_CHINESE",
"offset": "0x001c1068",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x000000b4"
},
{
"name": "RT_CURSOR",
"language": "LANG_CHINESE",
"offset": "0x001c1068",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x000000b4"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x001c2770",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000144"
},
{
"name": "RT_MENU",
"language": "LANG_CHINESE",
"offset": "0x001c5278",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000284"
},
{
"name": "RT_MENU",
"language": "LANG_CHINESE",
"offset": "0x001c5278",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000284"
},
{
"name": "RT_DIALOG",
"language": "LANG_CHINESE",
"offset": "0x001c64c0",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x0000018c"
},
{
"name": "RT_DIALOG",
"language": "LANG_CHINESE",
"offset": "0x001c64c0",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x0000018c"
},
{
"name": "RT_DIALOG",
"language": "LANG_CHINESE",
"offset": "0x001c64c0",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x0000018c"
},
{
"name": "RT_DIALOG",
"language": "LANG_CHINESE",
"offset": "0x001c64c0",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x0000018c"
},
{
"name": "RT_DIALOG",
"language": "LANG_CHINESE",
"offset": "0x001c64c0",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x0000018c"
},
{
"name": "RT_DIALOG",
"language": "LANG_CHINESE",
"offset": "0x001c64c0",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x0000018c"
},
{
"name": "RT_DIALOG",
"language": "LANG_CHINESE",
"offset": "0x001c64c0",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x0000018c"
},
{
"name": "RT_DIALOG",
"language": "LANG_CHINESE",
"offset": "0x001c64c0",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x0000018c"
},
{
"name": "RT_DIALOG",
"language": "LANG_CHINESE",
"offset": "0x001c64c0",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x0000018c"
},
{
"name": "RT_DIALOG",
"language": "LANG_CHINESE",
"offset": "0x001c64c0",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x0000018c"
},
{
"name": "RT_STRING",
"language": "LANG_CHINESE",
"offset": "0x001c6f08",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000024"
},
{
"name": "RT_STRING",
"language": "LANG_CHINESE",
"offset": "0x001c6f08",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000024"
},
{
"name": "RT_STRING",
"language": "LANG_CHINESE",
"offset": "0x001c6f08",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000024"
},
{
"name": "RT_STRING",
"language": "LANG_CHINESE",
"offset": "0x001c6f08",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000024"
},
{
"name": "RT_STRING",
"language": "LANG_CHINESE",
"offset": "0x001c6f08",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000024"
},
{
"name": "RT_STRING",
"language": "LANG_CHINESE",
"offset": "0x001c6f08",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000024"
},
{
"name": "RT_STRING",
"language": "LANG_CHINESE",
"offset": "0x001c6f08",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000024"
},
{
"name": "RT_STRING",
"language": "LANG_CHINESE",
"offset": "0x001c6f08",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000024"
},
{
"name": "RT_STRING",
"language": "LANG_CHINESE",
"offset": "0x001c6f08",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000024"
},
{
"name": "RT_STRING",
"language": "LANG_CHINESE",
"offset": "0x001c6f08",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000024"
},
{
"name": "RT_STRING",
"language": "LANG_CHINESE",
"offset": "0x001c6f08",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000024"
},
{
"name": "RT_GROUP_CURSOR",
"language": "LANG_CHINESE",
"offset": "0x001c6f54",
"filetype": "MS Windows cursor resource - 2 icons, 32x256, hotspot @1x1",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000022"
},
{
"name": "RT_GROUP_CURSOR",
"language": "LANG_CHINESE",
"offset": "0x001c6f54",
"filetype": "MS Windows cursor resource - 2 icons, 32x256, hotspot @1x1",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000022"
},
{
"name": "RT_GROUP_CURSOR",
"language": "LANG_CHINESE",
"offset": "0x001c6f54",
"filetype": "MS Windows cursor resource - 2 icons, 32x256, hotspot @1x1",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000022"
},
{
"name": "RT_GROUP_ICON",
"language": "LANG_CHINESE",
"offset": "0x001c6fa0",
"filetype": "MS Windows icon resource - 1 icon, 16x16, 16 colors",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000014"
},
{
"name": "RT_GROUP_ICON",
"language": "LANG_CHINESE",
"offset": "0x001c6fa0",
"filetype": "MS Windows icon resource - 1 icon, 16x16, 16 colors",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000014"
},
{
"name": "RT_GROUP_ICON",
"language": "LANG_CHINESE",
"offset": "0x001c6fa0",
"filetype": "MS Windows icon resource - 1 icon, 16x16, 16 colors",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000014"
}
],
"references": [],
"name": "origin_langid"
},
{
"markcount": 1,
"families": [],
"description": "Drops an executable to the user AppData folder",
"severity": 2,
"marks": [
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Temp\\489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192Srv.exe",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "exe_appdata"
},
{
"markcount": 1,
"families": [],
"description": "Checks adapter addresses which can be used to detect virtual network interfaces",
"severity": 2,
"marks": [
{
"call": {
"category": "network",
"status": 0,
"stacktrace": [],
"last_error": 0,
"nt_status": -1073741772,
"api": "GetAdaptersAddresses",
"return_value": 111,
"arguments": {
"flags": 0,
"family": 0
},
"time": 1577325186.109625,
"tid": 2952,
"flags": {}
},
"pid": 1268,
"type": "call",
"cid": 921
}
],
"references": [],
"name": "antivm_network_adapters"
},
{
"markcount": 3,
"families": [],
"description": "The binary likely contains encrypted or compressed data indicative of a packer",
"severity": 2,
"marks": [
{
"entropy": 7.37077036113406,
"section": {
"size_of_data": "0x00103000",
"virtual_address": "0x00085000",
"entropy": 7.37077036113406,
"name": ".rdata",
"virtual_size": "0x00102202"
},
"type": "generic",
"description": "A section with a high entropy has been found"
},
{
"entropy": 7.776227754280914,
"section": {
"size_of_data": "0x0000f000",
"virtual_address": "0x001c8000",
"entropy": 7.776227754280914,
"name": ".rmnet",
"virtual_size": "0x0000f000"
},
"type": "generic",
"description": "A section with a high entropy has been found"
},
{
"entropy": 0.6386946386946387,
"type": "generic",
"description": "Overall entropy of this PE file is high"
}
],
"references": [
"http:\/\/www.forensickb.com\/2013\/03\/file-entropy-explained.html",
"http:\/\/virii.es\/U\/Using%20Entropy%20Analysis%20to%20Find%20Encrypted%20and%20Packed%20Malware.pdf"
],
"name": "packer_entropy"
},
{
"markcount": 5,
"families": [],
"description": "Sets or modifies WPAD proxy autoconfiguration file for traffic interception",
"severity": 3,
"marks": [
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExA",
"return_value": 0,
"arguments": {
"key_handle": "0x00000368",
"value": 1,
"regkey_r": "WpadDecisionReason",
"reg_type": 4,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionReason"
},
"time": 1577325186.453625,
"tid": 2952,
"flags": {
"reg_type": "REG_DWORD"
}
},
"pid": 1268,
"type": "call",
"cid": 934
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExA",
"return_value": 0,
"arguments": {
"key_handle": "0x00000368",
"value": "P<;\u00dc\u00d7\u00bb\u00d5\u0001",
"regkey_r": "WpadDecisionTime",
"reg_type": 3,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionTime"
},
"time": 1577325186.453625,
"tid": 2952,
"flags": {
"reg_type": "REG_BINARY"
}
},
"pid": 1268,
"type": "call",
"cid": 935
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExA",
"return_value": 0,
"arguments": {
"key_handle": "0x00000368",
"value": 3,
"regkey_r": "WpadDecision",
"reg_type": 4,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecision"
},
"time": 1577325186.453625,
"tid": 2952,
"flags": {
"reg_type": "REG_DWORD"
}
},
"pid": 1268,
"type": "call",
"cid": 936
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExW",
"return_value": 0,
"arguments": {
"key_handle": "0x00000368",
"value": "Unidentified network",
"regkey_r": "WpadNetworkName",
"reg_type": 1,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadNetworkName"
},
"time": 1577325186.453625,
"tid": 2952,
"flags": {
"reg_type": "REG_SZ"
}
},
"pid": 1268,
"type": "call",
"cid": 937
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExW",
"return_value": 0,
"arguments": {
"key_handle": "0x00000364",
"value": "{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}",
"regkey_r": "WpadLastNetwork",
"reg_type": 1,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork"
},
"time": 1577325186.453625,
"tid": 2952,
"flags": {
"reg_type": "REG_SZ"
}
},
"pid": 1268,
"type": "call",
"cid": 1005
}
],
"references": [],
"name": "modifies_proxy_wpad"
},
{
"markcount": 1,
"families": [
"ramnit"
],
"description": "Ramnit malware indicators found",
"severity": 3,
"marks": [
{
"category": "mutex",
"ioc": "KyUffThOkYwRRtgPP",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "ramnit"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 546,
"time": 3.0786240100860596,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 5226,
"time": 9.07856011390686,
"dport": 138,
"sport": 138
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7070,
"time": 2.5923211574554443,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7390,
"time": 1.0647900104522705,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7718,
"time": 3.012761116027832,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8046,
"time": 1.6959450244903564,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8374,
"time": -0.09126806259155273,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8702,
"time": 3.0207390785217285,
"dport": 5355,
"sport": 55880
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 9030,
"time": 1.625196933746338,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 28440,
"time": 1.0981900691986084,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 36824,
"time": 3.1252920627593994,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "614827c4c9b690ef10faf7bb75fa784b8288a920ee08f65cfb9a5fd5e9795428",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "0d927312be4de1bbeca4380719b1f023d3bd09e2b3b9b786432475a1df2b034f",
"irc": [],
"https_ex": []
}Screenshots
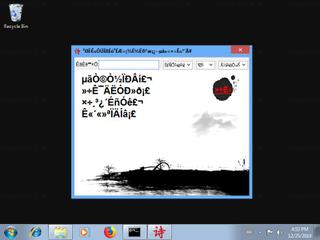
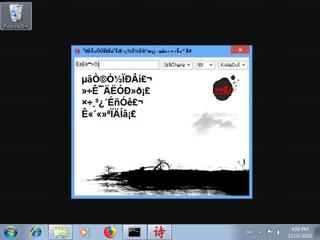
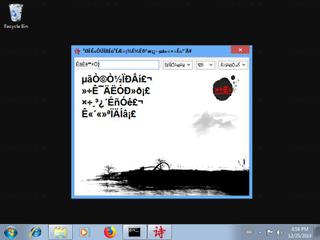
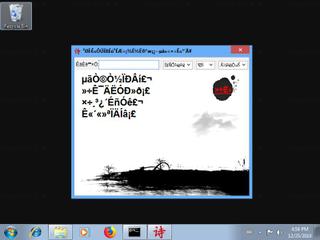
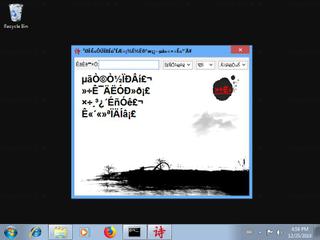
ctszxscq.exe removal instructions
The instructions below shows how to remove ctszxscq.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the ctszxscq.exe file for removal, restart your computer and scan it again to verify that ctszxscq.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate ctszxscq.exe in the scan result and tick the checkbox next to the ctszxscq.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate ctszxscq.exe in the scan result.

 c:\downloads\ctszxscq.exe
c:\downloads\ctszxscq.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If ctszxscq.exe still remains in the scan result, proceed with the next step. If ctszxscq.exe is gone from the scan result you're done.
- If ctszxscq.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that ctszxscq.exe no longer appear in the scan result.
Hashes [?]
| Property | Value |
|---|---|
| MD5 | f298a6a59dc8528a65ad0eb2055c6807 |
| SHA256 | 489f76b315823e1eba21ed11c633b34ca56022ad4b4dbb52bd417a7bbd2e1192 |
Error Messages
These are some of the error messages that can appear related to ctszxscq.exe:
ctszxscq.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
ctszxscq.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
???????? has stopped working.
End Program - ctszxscq.exe. This program is not responding.
ctszxscq.exe is not a valid Win32 application.
ctszxscq.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with ctszxscq.exe?
To help other users, please let us know what you will do with ctszxscq.exe:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.