What is detailsofAmazonOrderIDpdf.exe?
detailsofAmazonOrderIDpdf.exe is usually located in the 'c:\downloads\' folder.
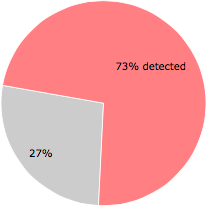
Some of the anti-virus scanners at VirusTotal detected detailsofAmazonOrderIDpdf.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Vendor and version information [?]
detailsofAmazonOrderIDpdf.exe does not have any version or vendor information.
Digital signatures [?]
detailsofAmazonOrderIDpdf.exe is not signed.
VirusTotal report
54 of the 74 anti-virus programs at VirusTotal detected the detailsofAmazonOrderIDpdf.exe file. That's a 73% detection rate.
| Scanner | Detection Name |
|---|---|
| Acronis | suspicious |
| Ad-Aware | Gen:Variant.Graftor.371552 |
| AegisLab | Trojan.Win32.Generic.4!c |
| AhnLab-V3 | Malware/Win32.Generic.C2158508 |
| Alibaba | VirTool:Win32/CeeInject.4b0eb5bb |
| ALYac | Gen:Variant.Graftor.371552 |
| Antiy-AVL | Trojan[PSW]/Win32.IMStealer |
| APEX | Malicious |
| Arcabit | Trojan.Graftor.D5AB60 |
| Avast | Win32:Malware-gen |
| AVG | Win32:Malware-gen |
| Avira | HEUR/AGEN.1021526 |
| BitDefender | Gen:Variant.Graftor.371552 |
| Comodo | Malware@#19ljfc529tiwm |
| CrowdStrike | win/malicious_confidence_90% (W) |
| Cybereason | malicious.7460ec |
| Cylance | Unsafe |
| Cyren | W32/Trojan.NAXF-1625 |
| DrWeb | Trojan.DownLoader14.35508 |
| Emsisoft | Gen:Variant.Graftor.371552 (B) |
| Endgame | malicious (high confidence) |
| ESET-NOD32 | a variant of Win32/PSW.Delf.OFA |
| F-Secure | Heuristic.HEUR/AGEN.1021526 |
| FireEye | Generic.mg.8798f177460ec7f9 |
| Fortinet | W32/Delf.OFA!tr |
| GData | Gen:Variant.Graftor.371552 |
| Ikarus | Trojan-Dropper.Win32.Delf |
| Invincea | heuristic |
| K7AntiVirus | Trojan ( 7000000f1 ) |
| K7GW | Trojan ( 7000000f1 ) |
| Kaspersky | HEUR:Trojan.Win32.Generic |
| MAX | malware (ai score=100) |
| MaxSecure | Trojan.Malware.7164915.susgen |
| McAfee | GenericRXER-KH!8798F177460E |
| McAfee-GW-Edition | BehavesLike.Win32.Backdoor.fc |
| Microsoft | VirTool:Win32/CeeInject.RS!bit |
| MicroWorld-eScan | Gen:Variant.Graftor.371552 |
| NANO-Antivirus | Trojan.Win32.Delphi.epfiyp |
| Paloalto | generic.ml |
| Panda | Trj/CI.A |
| Qihoo-360 | HEUR/QVM41.2.A221.Malware.Gen |
| Rising | Stealer.Delf!8.415 (C64:YzY0OjkJ9q6naEKF) |
| SentinelOne | DFI - Malicious PE |
| Sophos | Mal/Generic-S |
| Symantec | ML.Attribute.HighConfidence |
| TheHacker | Trojan/Delf.ofa |
| Trapmine | malicious.high.ml.score |
| TrendMicro | TROJ_GEN.R002C0DC219 |
| TrendMicro-HouseCall | TROJ_GEN.R002C0DC219 |
| VBA32 | Trojan.Inject |
| VIPRE | Trojan.Win32.Generic!BT |
| Yandex | Trojan.Agent!PW52dpRJa+c |
| Zillya | Trojan.Delf.Win32.81138 |
| ZoneAlarm | HEUR:Trojan.Win32.Generic |
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.dll"
],
"regkey_written": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Internet Explorer\\Tabs\\sq"
],
"dll_loaded": [
"shell32.dll",
"advapi32.dll",
"kernel32.dll",
"user32.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba.bin",
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.dll",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"file_copied": [
[
"C:\\Users\\cuck\\AppData\\Local\\Temp\\78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba.bin",
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.exe"
]
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Shell Folders",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Internet Explorer\\Tabs",
"HKEY_CURRENT_USER\\Software\\Borland\\Delphi\\Locales",
"HKEY_LOCAL_MACHINE\\Software\\Borland\\Locales",
"HKEY_CURRENT_USER\\Software\\Borland\\Locales"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.dll"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.dll"
],
"command_line": [
"svchost.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba.bin h7"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba.bin",
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.dll"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Shell Folders\\Startup",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Shell Folders\\Local AppData",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
]
}Dropped
[
{
"yara": [],
"sha1": "16149b2270b1319a9fc3ebb9d9051c0e3a19cd1f",
"name": "83b029829f8f9249_msfrbth.dll",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.dll",
"type": "PE32 executable (DLL) (GUI) Intel 80386, for MS Windows, UPX compressed",
"sha256": "83b029829f8f9249b6057409b63bbba6da06b19276ee55fdf2707f4f8adeccf6",
"urls": [],
"crc32": "28C3986C",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/1502\/files\/83b029829f8f9249_msfrbth.dll",
"ssdeep": null,
"size": 304306,
"sha512": "ae53d347c32ea1e48986cc320e3b3d9ace28301d10a479cf03cc666aa50ce9c64d4a6c2e0a8581d95a9309eba8af3e98afb1bb2f117fbe4e2a567b4bfe4178a7",
"pids": [
2500
],
"md5": "19dd93bf8f296699d4801c47f7470c31"
}
]Generic
[
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba.bin",
"process_name": "78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba.bin",
"pid": 1664,
"summary": {
"command_line": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba.bin h7"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Borland\\Delphi\\Locales",
"HKEY_LOCAL_MACHINE\\Software\\Borland\\Locales",
"HKEY_CURRENT_USER\\Software\\Borland\\Locales"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
],
"dll_loaded": [
"kernel32.dll"
]
},
"first_seen": 1564815185.5469,
"ppid": 2448
},
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1564815185.3125,
"ppid": 376
},
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba.bin",
"process_name": "78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba.bin",
"pid": 2500,
"summary": {
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.dll"
],
"regkey_written": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Internet Explorer\\Tabs\\sq"
],
"dll_loaded": [
"shell32.dll",
"advapi32.dll",
"kernel32.dll",
"user32.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba.bin",
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.dll",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"file_copied": [
[
"C:\\Users\\cuck\\AppData\\Local\\Temp\\78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba.bin",
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.exe"
]
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Shell Folders",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Internet Explorer\\Tabs",
"HKEY_CURRENT_USER\\Software\\Borland\\Delphi\\Locales",
"HKEY_LOCAL_MACHINE\\Software\\Borland\\Locales",
"HKEY_CURRENT_USER\\Software\\Borland\\Locales"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.dll"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.dll"
],
"command_line": [
"svchost.exe"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba.bin",
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.dll"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Shell Folders\\Startup",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Shell Folders\\Local AppData",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US"
]
},
"first_seen": 1564815185.8594,
"ppid": 1664
}
]Signatures
[
{
"markcount": 3,
"families": [],
"description": "The executable contains unknown PE section names indicative of a packer (could be a false positive)",
"severity": 1,
"marks": [
{
"category": "section",
"ioc": "CODE",
"type": "ioc",
"description": null
},
{
"category": "section",
"ioc": "DATA",
"type": "ioc",
"description": null
},
{
"category": "section",
"ioc": "BSS",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "pe_features"
},
{
"markcount": 0,
"families": [],
"description": "One or more potentially interesting buffers were extracted, these generally contain injected code, configuration data, etc.",
"severity": 2,
"marks": [],
"references": [],
"name": "dumped_buffer"
},
{
"markcount": 3,
"families": [],
"description": "Allocates read-write-execute memory (usually to unpack itself)",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2500,
"region_size": 503808,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x10410000"
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 192
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2500,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 192512,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10411000"
},
"time": 1564815188.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2500,
"type": "call",
"cid": 623
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2500,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 303104,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x10440000"
},
"time": 1564815188.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2500,
"type": "call",
"cid": 624
}
],
"references": [],
"name": "allocates_rwx"
},
{
"markcount": 1,
"families": [],
"description": "Creates a suspicious process",
"severity": 2,
"marks": [
{
"category": "cmdline",
"ioc": "svchost.exe",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "suspicious_process"
},
{
"markcount": 1,
"families": [],
"description": "Drops an executable to the user AppData folder",
"severity": 2,
"marks": [
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\msfrbth.dll",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "exe_appdata"
},
{
"markcount": 1,
"families": [],
"description": "One or more of the buffers contains an embedded PE file",
"severity": 3,
"marks": [
{
"category": "buffer",
"ioc": "Buffer with sha1: 8afdf568b5d21d2805d4685f1c027e06d4fccc4c",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "dumped_buffer2"
},
{
"markcount": 109,
"families": [],
"description": "Allocates execute permission to another process indicative of possible code injection",
"severity": 3,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 503808,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x10410000"
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 194
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x000b0000"
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 205
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x000c0000"
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 207
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x000d0000"
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 209
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00020000"
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 220
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00030000"
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 222
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x000e0000"
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 224
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x000f0000"
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 226
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00100000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 235
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x001d0000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 237
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x001e0000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 239
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x001f0000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 241
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00200000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 250
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00210000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 252
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00220000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 254
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00270000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 256
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00280000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 265
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00290000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 267
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x002a0000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 269
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00330000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 271
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00340000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 280
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00350000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 282
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00360000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 284
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x004e0000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 286
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x004f0000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 293
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00500000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 295
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00510000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 297
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00520000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 308
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00530000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 310
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00540000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 312
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00550000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 314
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00560000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 321
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00570000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 323
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00580000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 325
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x005a0000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 336
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x005b0000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 338
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x005c0000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 340
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x005d0000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 342
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00620000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 349
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00630000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 351
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00640000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 353
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x006d0000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 364
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x006e0000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 366
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x006f0000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 368
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00700000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 370
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00710000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 377
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00720000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 379
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00730000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 381
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00780000"
},
"time": 1564815187.3284,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 392
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00790000"
},
"time": 1564815187.3284,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 394
}
],
"references": [],
"name": "allocates_execute_remote_process"
},
{
"markcount": 32,
"families": [],
"description": "Creates a thread using CreateRemoteThread in a non-child process indicative of process injection",
"severity": 3,
"marks": [
{
"category": "Process injection",
"ioc": "Process 2500 created a remote thread in non-child process 2952",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 236,
"arguments": {
"thread_identifier": 2272,
"process_identifier": 2952,
"function_address": "0x000d0000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x000c0000",
"stack_size": 0
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 211
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 236,
"arguments": {
"thread_identifier": 1616,
"process_identifier": 2952,
"function_address": "0x000f0000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x000e0000",
"stack_size": 0
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 228
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 232,
"arguments": {
"thread_identifier": 2256,
"process_identifier": 2952,
"function_address": "0x001f0000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x001e0000",
"stack_size": 0
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 243
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 240,
"arguments": {
"thread_identifier": 2056,
"process_identifier": 2952,
"function_address": "0x00270000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x00220000",
"stack_size": 0
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 258
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 244,
"arguments": {
"thread_identifier": 2804,
"process_identifier": 2952,
"function_address": "0x00330000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x002a0000",
"stack_size": 0
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 273
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 248,
"arguments": {
"thread_identifier": 1224,
"process_identifier": 2952,
"function_address": "0x004e0000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x00360000",
"stack_size": 0
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 288
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 252,
"arguments": {
"thread_identifier": 1424,
"process_identifier": 2952,
"function_address": "0x00510000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x00500000",
"stack_size": 0
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 299
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 252,
"arguments": {
"thread_identifier": 2572,
"process_identifier": 2952,
"function_address": "0x00550000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x00540000",
"stack_size": 0
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 316
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 256,
"arguments": {
"thread_identifier": 2236,
"process_identifier": 2952,
"function_address": "0x00580000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x00570000",
"stack_size": 0
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 327
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 256,
"arguments": {
"thread_identifier": 368,
"process_identifier": 2952,
"function_address": "0x005d0000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x005c0000",
"stack_size": 0
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 344
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 260,
"arguments": {
"thread_identifier": 2824,
"process_identifier": 2952,
"function_address": "0x00640000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x00630000",
"stack_size": 0
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 355
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 260,
"arguments": {
"thread_identifier": 2284,
"process_identifier": 2952,
"function_address": "0x00700000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x006f0000",
"stack_size": 0
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 372
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 264,
"arguments": {
"thread_identifier": 3052,
"process_identifier": 2952,
"function_address": "0x00730000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x00720000",
"stack_size": 0
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 383
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 264,
"arguments": {
"thread_identifier": 2792,
"process_identifier": 2952,
"function_address": "0x007b0000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x007a0000",
"stack_size": 0
},
"time": 1564815187.3284,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 400
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 268,
"arguments": {
"thread_identifier": 1496,
"process_identifier": 2952,
"function_address": "0x00860000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x00850000",
"stack_size": 0
},
"time": 1564815187.3284,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 411
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 268,
"arguments": {
"thread_identifier": 1468,
"process_identifier": 2952,
"function_address": "0x008f0000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x008e0000",
"stack_size": 0
},
"time": 1564815187.4534,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 428
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 272,
"arguments": {
"thread_identifier": 2252,
"process_identifier": 2952,
"function_address": "0x00920000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x00910000",
"stack_size": 0
},
"time": 1564815187.4534,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 439
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 272,
"arguments": {
"thread_identifier": 2184,
"process_identifier": 2952,
"function_address": "0x009e0000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x009d0000",
"stack_size": 0
},
"time": 1564815187.5624,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 456
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 276,
"arguments": {
"thread_identifier": 2648,
"process_identifier": 2952,
"function_address": "0x00d70000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x00d60000",
"stack_size": 0
},
"time": 1564815187.5624,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 467
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 276,
"arguments": {
"thread_identifier": 2508,
"process_identifier": 2952,
"function_address": "0x00df0000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x00da0000",
"stack_size": 0
},
"time": 1564815187.6724,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 484
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 280,
"arguments": {
"thread_identifier": 2628,
"process_identifier": 2952,
"function_address": "0x00e20000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x00e10000",
"stack_size": 0
},
"time": 1564815187.6724,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 495
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 280,
"arguments": {
"thread_identifier": 1556,
"process_identifier": 2952,
"function_address": "0x02670000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x02660000",
"stack_size": 0
},
"time": 1564815187.7814,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 512
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 284,
"arguments": {
"thread_identifier": 1132,
"process_identifier": 2952,
"function_address": "0x026e0000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x026d0000",
"stack_size": 0
},
"time": 1564815187.7814,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 523
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 284,
"arguments": {
"thread_identifier": 2964,
"process_identifier": 2952,
"function_address": "0x02760000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x02750000",
"stack_size": 0
},
"time": 1564815187.8914,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 540
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 288,
"arguments": {
"thread_identifier": 264,
"process_identifier": 2952,
"function_address": "0x02790000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x02780000",
"stack_size": 0
},
"time": 1564815187.8914,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 551
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 288,
"arguments": {
"thread_identifier": 2268,
"process_identifier": 2952,
"function_address": "0x02810000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x02800000",
"stack_size": 0
},
"time": 1564815188.0004,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 568
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 292,
"arguments": {
"thread_identifier": 1996,
"process_identifier": 2952,
"function_address": "0x02840000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x02830000",
"stack_size": 0
},
"time": 1564815188.0004,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 579
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 292,
"arguments": {
"thread_identifier": 2844,
"process_identifier": 2952,
"function_address": "0x02880000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x02870000",
"stack_size": 0
},
"time": 1564815188.1094,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 596
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 296,
"arguments": {
"thread_identifier": 2440,
"process_identifier": 2952,
"function_address": "0x02970000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x028e0000",
"stack_size": 0
},
"time": 1564815188.1094,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 607
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 296,
"arguments": {
"thread_identifier": 2484,
"process_identifier": 2952,
"function_address": "0x029a0000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x02990000",
"stack_size": 0
},
"time": 1564815188.2194,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 622
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "CreateRemoteThread",
"return_value": 300,
"arguments": {
"thread_identifier": 1500,
"process_identifier": 2952,
"function_address": "0x02a00000",
"flags": 0,
"process_handle": "0x000000e0",
"parameter": "0x029f0000",
"stack_size": 0
},
"time": 1564815188.8444,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 631
}
],
"references": [
"www.endgame.com\/blog\/technical-blog\/ten-process-injection-techniques-technical-survey-common-and-trending-process"
],
"name": "injection_createremotethread"
},
{
"markcount": 110,
"families": [],
"description": "Manipulates memory of a non-child process indicative of process injection",
"severity": 3,
"marks": [
{
"category": "Process injection",
"ioc": "Process 2500 manipulating memory of non-child process 2952",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 503808,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x10410000"
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 194
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x000b0000"
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 205
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x000c0000"
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 207
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x000d0000"
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 209
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00020000"
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 220
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00030000"
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 222
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x000e0000"
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 224
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x000f0000"
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 226
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00100000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 235
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x001d0000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 237
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x001e0000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 239
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x001f0000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 241
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00200000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 250
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00210000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 252
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00220000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 254
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00270000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 256
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00280000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 265
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00290000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 267
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x002a0000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 269
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00330000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 271
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00340000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 280
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00350000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 282
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00360000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 284
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x004e0000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 286
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x004f0000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 293
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00500000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 295
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00510000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 297
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00520000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 308
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00530000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 310
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00540000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 312
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00550000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 314
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00560000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 321
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00570000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 323
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00580000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 325
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x005a0000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 336
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x005b0000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 338
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x005c0000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 340
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x005d0000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 342
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00620000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 349
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00630000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 351
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00640000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 353
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x006d0000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 364
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x006e0000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 366
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x006f0000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 368
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00700000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 370
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00710000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 377
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00720000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 379
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00730000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 381
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2952,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000000e0",
"allocation_type": 12288,
"base_address": "0x00780000"
},
"time": 1564815187.3284,
"tid": 1676,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2500,
"type": "call",
"cid": 392
}
],
"references": [
"www.endgame.com\/blog\/technical-blog\/ten-process-injection-techniques-technical-survey-common-and-trending-process"
],
"name": "injection_modifies_memory"
},
{
"markcount": 109,
"families": [],
"description": "Potential code injection by writing to the memory of another process",
"severity": 3,
"marks": [
{
"category": "Process injection",
"ioc": "Process 2500 injected into non-child 2952",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "KERNEL32.DLL\u0000",
"process_handle": "0x000000e0",
"base_address": "0x000b0000"
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 206
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u00d7I\u00bcu\u0000\u0000\u000b\u0000\u00ff\u0010\u00bcu",
"process_handle": "0x000000e0",
"base_address": "0x000c0000"
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 208
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00f4\u008bE\b\u008b\u0010\u0089U\u00f4\u008bP\u0004\u0089U\u00f8\u008bP\b\u0089U\u00fc\u00ffu\u00f8\u00ffU\u00f4\u00b8\u00ff\u00ff\u00ff\u00ffP\u00ffU\u00fc\u00eb\u00f5\u008b\u00e5]\u00c2\u0004\u0000\u008d@\u0000U\u008b\u00ec\u0083\u00c4\u00f0SV\u0089U\u00fc\u008b\u00f0\u008bE\u00fc\u00e8\u00cb\u00af\u00ff\u00ff3\u00c0Uh\u008d\u0095@\u0000d\u00ff0d\u0089 3\u00dbh\u009c\u0095@\u0000h\u00a4\u0095@\u0000\u00e8h\u00c5\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00f8h\u00b0\u0095@\u0000h\u00a4\u0095@\u0000\u00e8L\u00c5\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00f0\u008bE\u00fc\u00e8\u008b\u00af\u00ff\u00ff\u008b\u00d0\u008b\u00c6\u00e8\"\u00fe\u00ff\u00ff\u0089E\u00f4j\fj\u0000\u008dM\u00f0\u00ba\u00a8\u0094@\u0000\u008b\u00c6\u00e8\u00d0\u00fe\u00ff\u00ff\u0085\u00c0t\u0013P\u00a1\u00bc;A\u0000\u008b\u0000\u00ff\u00d0\u00b3\u0001jd\u00e8Q\u00c5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u0094\u0095@\u0000\u008dE\u00fc\u00e8\u00a4\u00aa\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x000d0000"
},
"time": 1564815186.7344,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 210
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "LoadLibraryA",
"process_handle": "0x000000e0",
"base_address": "0x00020000"
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 221
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "KERNEL32.DLL\u0000",
"process_handle": "0x000000e0",
"base_address": "0x00030000"
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 223
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u0098\u00d5\u00bew\"\u0012\u00bcuE\u0012\u00bcu\u0000\u0000\u0003\u0000\u0000\u0000\u0002\u0000",
"process_handle": "0x000000e0",
"base_address": "0x000e0000"
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 225
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00ecVW\u008bE\b\u008b\u00f0\u008d}\u00ec\u00a5\u00a5\u00a5\u00a5\u00a5\u00ffu\u00f8\u00ffU\u00f4\u00ffu\u00fcP\u00ffU\u00f0P\u00ffU\u00ec_^\u008b\u00e5]\u00c2\u0004\u0000\u008b\u00c0U\u008b\u00ec\u0083\u00c4\u00e0SVW\u0089M\u00f8\u0089U\u00fc\u008b\u00d8\u008bu\b3\u00ffh\u0010\u009a@\u0000h$\u009a@\u0000\u00e8\u000f\u00c1\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e8h0\u009a@\u0000h$\u009a@\u0000\u00e8\u00f3\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e4h@\u009a@\u0000h$\u009a@\u0000\u00e8\u00d7\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e0\u0083\u00fe\u0004u\b\u008bE\u00f8\u0089E\u00f0\u00eb\u000f\u008b\u00ce\u008bU\u00f8\u008b\u00c3\u00e85\u00fa\u00ff\u00ff\u0089E\u00f0\u008bU\u00fc\u008b\u00c3\u00e8\u0098\u00f9\u00ff\u00ff\u0089E\u00ecj\u0014j\u0000\u008dM\u00e0\u00ba\u0014\u0099@\u0000\u008b\u00c3\u00e8F\u00fa\u00ff\u00ff\u008b\u00d8\u0085\u00dbt\u0015j\u00ffS\u00e8\u0000\u00c1\u00ff\u00ff\u008dE\u00f4PS\u00e8N\u00c0\u00ff\u00ff\u008b}\u00f4\u008b\u00c7_^[\u008b\u00e5]\u00c2\u0004\u0000GetModuleHandleA\u0000\u0000\u0000\u0000kernel32\u0000\u0000\u0000\u0000GetProcAddress\u0000\u0000ExitThread\u0000\u0000U\u008b\u00ec\u0083\u00c4\u00f8\u0089U\u00f8\u0089E\u00fc\u008bE\u00fc\u00e8\u00d0\u00b5\u00ff\u00ff\u008bE\u00f8\u00e8T\u00aa\u00ff\u00ff3\u00c0Uh\u00d1\u009a@\u0000d\u00ff0d\u0089 \u008bE\u00fc\u00e8\u0086\u00b3\u00ff\u00ff@P\u008dE\u00fc\u00b9\u0001\u0000\u0000\u0000\u008b\u00158\u0090@\u0000\u00e8-\u00b5\u00ff\u00ff\u0083\u00c4\u0004\u008bE\u00fc\u00e8f\u00b3\u00ff\u00ff\u008bU\u00fc\u008dD\u0082\u00fc\u008bU\u00f8\u00e8\u00d7\u00a5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u00d8\u009a@\u0000\u008dE\u00f8\u00e8n\u00a5\u00ff\u00ff\u008dE\u00fc\u008b\u00158\u0090@\u0000\u00e8\u00fc\u00b4\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x000f0000"
},
"time": 1564815186.8444,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 227
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "GetProcAddress",
"process_handle": "0x000000e0",
"base_address": "0x00100000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 236
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "KERNEL32.DLL\u0000",
"process_handle": "0x000000e0",
"base_address": "0x001d0000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 238
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u0098\u00d5\u00bew\"\u0012\u00bcuE\u0012\u00bcu\u0000\u0000\u001d\u0000\u0000\u0000\u0010\u0000",
"process_handle": "0x000000e0",
"base_address": "0x001e0000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 240
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00ecVW\u008bE\b\u008b\u00f0\u008d}\u00ec\u00a5\u00a5\u00a5\u00a5\u00a5\u00ffu\u00f8\u00ffU\u00f4\u00ffu\u00fcP\u00ffU\u00f0P\u00ffU\u00ec_^\u008b\u00e5]\u00c2\u0004\u0000\u008b\u00c0U\u008b\u00ec\u0083\u00c4\u00e0SVW\u0089M\u00f8\u0089U\u00fc\u008b\u00d8\u008bu\b3\u00ffh\u0010\u009a@\u0000h$\u009a@\u0000\u00e8\u000f\u00c1\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e8h0\u009a@\u0000h$\u009a@\u0000\u00e8\u00f3\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e4h@\u009a@\u0000h$\u009a@\u0000\u00e8\u00d7\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e0\u0083\u00fe\u0004u\b\u008bE\u00f8\u0089E\u00f0\u00eb\u000f\u008b\u00ce\u008bU\u00f8\u008b\u00c3\u00e85\u00fa\u00ff\u00ff\u0089E\u00f0\u008bU\u00fc\u008b\u00c3\u00e8\u0098\u00f9\u00ff\u00ff\u0089E\u00ecj\u0014j\u0000\u008dM\u00e0\u00ba\u0014\u0099@\u0000\u008b\u00c3\u00e8F\u00fa\u00ff\u00ff\u008b\u00d8\u0085\u00dbt\u0015j\u00ffS\u00e8\u0000\u00c1\u00ff\u00ff\u008dE\u00f4PS\u00e8N\u00c0\u00ff\u00ff\u008b}\u00f4\u008b\u00c7_^[\u008b\u00e5]\u00c2\u0004\u0000GetModuleHandleA\u0000\u0000\u0000\u0000kernel32\u0000\u0000\u0000\u0000GetProcAddress\u0000\u0000ExitThread\u0000\u0000U\u008b\u00ec\u0083\u00c4\u00f8\u0089U\u00f8\u0089E\u00fc\u008bE\u00fc\u00e8\u00d0\u00b5\u00ff\u00ff\u008bE\u00f8\u00e8T\u00aa\u00ff\u00ff3\u00c0Uh\u00d1\u009a@\u0000d\u00ff0d\u0089 \u008bE\u00fc\u00e8\u0086\u00b3\u00ff\u00ff@P\u008dE\u00fc\u00b9\u0001\u0000\u0000\u0000\u008b\u00158\u0090@\u0000\u00e8-\u00b5\u00ff\u00ff\u0083\u00c4\u0004\u008bE\u00fc\u00e8f\u00b3\u00ff\u00ff\u008bU\u00fc\u008dD\u0082\u00fc\u008bU\u00f8\u00e8\u00d7\u00a5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u00d8\u009a@\u0000\u008dE\u00f8\u00e8n\u00a5\u00ff\u00ff\u008dE\u00fc\u008b\u00158\u0090@\u0000\u00e8\u00fc\u00b4\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x001f0000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 242
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "VirtualProtect",
"process_handle": "0x000000e0",
"base_address": "0x00200000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 251
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "KERNEL32.DLL\u0000",
"process_handle": "0x000000e0",
"base_address": "0x00210000"
},
"time": 1564815186.8594,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 253
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u0098\u00d5\u00bew\"\u0012\u00bcuE\u0012\u00bcu\u0000\u0000!\u0000\u0000\u0000 \u0000",
"process_handle": "0x000000e0",
"base_address": "0x00220000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 255
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00ecVW\u008bE\b\u008b\u00f0\u008d}\u00ec\u00a5\u00a5\u00a5\u00a5\u00a5\u00ffu\u00f8\u00ffU\u00f4\u00ffu\u00fcP\u00ffU\u00f0P\u00ffU\u00ec_^\u008b\u00e5]\u00c2\u0004\u0000\u008b\u00c0U\u008b\u00ec\u0083\u00c4\u00e0SVW\u0089M\u00f8\u0089U\u00fc\u008b\u00d8\u008bu\b3\u00ffh\u0010\u009a@\u0000h$\u009a@\u0000\u00e8\u000f\u00c1\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e8h0\u009a@\u0000h$\u009a@\u0000\u00e8\u00f3\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e4h@\u009a@\u0000h$\u009a@\u0000\u00e8\u00d7\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e0\u0083\u00fe\u0004u\b\u008bE\u00f8\u0089E\u00f0\u00eb\u000f\u008b\u00ce\u008bU\u00f8\u008b\u00c3\u00e85\u00fa\u00ff\u00ff\u0089E\u00f0\u008bU\u00fc\u008b\u00c3\u00e8\u0098\u00f9\u00ff\u00ff\u0089E\u00ecj\u0014j\u0000\u008dM\u00e0\u00ba\u0014\u0099@\u0000\u008b\u00c3\u00e8F\u00fa\u00ff\u00ff\u008b\u00d8\u0085\u00dbt\u0015j\u00ffS\u00e8\u0000\u00c1\u00ff\u00ff\u008dE\u00f4PS\u00e8N\u00c0\u00ff\u00ff\u008b}\u00f4\u008b\u00c7_^[\u008b\u00e5]\u00c2\u0004\u0000GetModuleHandleA\u0000\u0000\u0000\u0000kernel32\u0000\u0000\u0000\u0000GetProcAddress\u0000\u0000ExitThread\u0000\u0000U\u008b\u00ec\u0083\u00c4\u00f8\u0089U\u00f8\u0089E\u00fc\u008bE\u00fc\u00e8\u00d0\u00b5\u00ff\u00ff\u008bE\u00f8\u00e8T\u00aa\u00ff\u00ff3\u00c0Uh\u00d1\u009a@\u0000d\u00ff0d\u0089 \u008bE\u00fc\u00e8\u0086\u00b3\u00ff\u00ff@P\u008dE\u00fc\u00b9\u0001\u0000\u0000\u0000\u008b\u00158\u0090@\u0000\u00e8-\u00b5\u00ff\u00ff\u0083\u00c4\u0004\u008bE\u00fc\u00e8f\u00b3\u00ff\u00ff\u008bU\u00fc\u008dD\u0082\u00fc\u008bU\u00f8\u00e8\u00d7\u00a5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u00d8\u009a@\u0000\u008dE\u00f8\u00e8n\u00a5\u00ff\u00ff\u008dE\u00fc\u008b\u00158\u0090@\u0000\u00e8\u00fc\u00b4\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x00270000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 257
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "VirtualAlloc",
"process_handle": "0x000000e0",
"base_address": "0x00280000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 266
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "KERNEL32.DLL\u0000",
"process_handle": "0x000000e0",
"base_address": "0x00290000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 268
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u0098\u00d5\u00bew\"\u0012\u00bcuE\u0012\u00bcu\u0000\u0000)\u0000\u0000\u0000(\u0000",
"process_handle": "0x000000e0",
"base_address": "0x002a0000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 270
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00ecVW\u008bE\b\u008b\u00f0\u008d}\u00ec\u00a5\u00a5\u00a5\u00a5\u00a5\u00ffu\u00f8\u00ffU\u00f4\u00ffu\u00fcP\u00ffU\u00f0P\u00ffU\u00ec_^\u008b\u00e5]\u00c2\u0004\u0000\u008b\u00c0U\u008b\u00ec\u0083\u00c4\u00e0SVW\u0089M\u00f8\u0089U\u00fc\u008b\u00d8\u008bu\b3\u00ffh\u0010\u009a@\u0000h$\u009a@\u0000\u00e8\u000f\u00c1\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e8h0\u009a@\u0000h$\u009a@\u0000\u00e8\u00f3\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e4h@\u009a@\u0000h$\u009a@\u0000\u00e8\u00d7\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e0\u0083\u00fe\u0004u\b\u008bE\u00f8\u0089E\u00f0\u00eb\u000f\u008b\u00ce\u008bU\u00f8\u008b\u00c3\u00e85\u00fa\u00ff\u00ff\u0089E\u00f0\u008bU\u00fc\u008b\u00c3\u00e8\u0098\u00f9\u00ff\u00ff\u0089E\u00ecj\u0014j\u0000\u008dM\u00e0\u00ba\u0014\u0099@\u0000\u008b\u00c3\u00e8F\u00fa\u00ff\u00ff\u008b\u00d8\u0085\u00dbt\u0015j\u00ffS\u00e8\u0000\u00c1\u00ff\u00ff\u008dE\u00f4PS\u00e8N\u00c0\u00ff\u00ff\u008b}\u00f4\u008b\u00c7_^[\u008b\u00e5]\u00c2\u0004\u0000GetModuleHandleA\u0000\u0000\u0000\u0000kernel32\u0000\u0000\u0000\u0000GetProcAddress\u0000\u0000ExitThread\u0000\u0000U\u008b\u00ec\u0083\u00c4\u00f8\u0089U\u00f8\u0089E\u00fc\u008bE\u00fc\u00e8\u00d0\u00b5\u00ff\u00ff\u008bE\u00f8\u00e8T\u00aa\u00ff\u00ff3\u00c0Uh\u00d1\u009a@\u0000d\u00ff0d\u0089 \u008bE\u00fc\u00e8\u0086\u00b3\u00ff\u00ff@P\u008dE\u00fc\u00b9\u0001\u0000\u0000\u0000\u008b\u00158\u0090@\u0000\u00e8-\u00b5\u00ff\u00ff\u0083\u00c4\u0004\u008bE\u00fc\u00e8f\u00b3\u00ff\u00ff\u008bU\u00fc\u008dD\u0082\u00fc\u008bU\u00f8\u00e8\u00d7\u00a5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u00d8\u009a@\u0000\u008dE\u00f8\u00e8n\u00a5\u00ff\u00ff\u008dE\u00fc\u008b\u00158\u0090@\u0000\u00e8\u00fc\u00b4\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x00330000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 272
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "VirtualFree",
"process_handle": "0x000000e0",
"base_address": "0x00340000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 281
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "KERNEL32.DLL\u0000",
"process_handle": "0x000000e0",
"base_address": "0x00350000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 283
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u0098\u00d5\u00bew\"\u0012\u00bcuE\u0012\u00bcu\u0000\u00005\u0000\u0000\u00004\u0000",
"process_handle": "0x000000e0",
"base_address": "0x00360000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 285
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00ecVW\u008bE\b\u008b\u00f0\u008d}\u00ec\u00a5\u00a5\u00a5\u00a5\u00a5\u00ffu\u00f8\u00ffU\u00f4\u00ffu\u00fcP\u00ffU\u00f0P\u00ffU\u00ec_^\u008b\u00e5]\u00c2\u0004\u0000\u008b\u00c0U\u008b\u00ec\u0083\u00c4\u00e0SVW\u0089M\u00f8\u0089U\u00fc\u008b\u00d8\u008bu\b3\u00ffh\u0010\u009a@\u0000h$\u009a@\u0000\u00e8\u000f\u00c1\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e8h0\u009a@\u0000h$\u009a@\u0000\u00e8\u00f3\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e4h@\u009a@\u0000h$\u009a@\u0000\u00e8\u00d7\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e0\u0083\u00fe\u0004u\b\u008bE\u00f8\u0089E\u00f0\u00eb\u000f\u008b\u00ce\u008bU\u00f8\u008b\u00c3\u00e85\u00fa\u00ff\u00ff\u0089E\u00f0\u008bU\u00fc\u008b\u00c3\u00e8\u0098\u00f9\u00ff\u00ff\u0089E\u00ecj\u0014j\u0000\u008dM\u00e0\u00ba\u0014\u0099@\u0000\u008b\u00c3\u00e8F\u00fa\u00ff\u00ff\u008b\u00d8\u0085\u00dbt\u0015j\u00ffS\u00e8\u0000\u00c1\u00ff\u00ff\u008dE\u00f4PS\u00e8N\u00c0\u00ff\u00ff\u008b}\u00f4\u008b\u00c7_^[\u008b\u00e5]\u00c2\u0004\u0000GetModuleHandleA\u0000\u0000\u0000\u0000kernel32\u0000\u0000\u0000\u0000GetProcAddress\u0000\u0000ExitThread\u0000\u0000U\u008b\u00ec\u0083\u00c4\u00f8\u0089U\u00f8\u0089E\u00fc\u008bE\u00fc\u00e8\u00d0\u00b5\u00ff\u00ff\u008bE\u00f8\u00e8T\u00aa\u00ff\u00ff3\u00c0Uh\u00d1\u009a@\u0000d\u00ff0d\u0089 \u008bE\u00fc\u00e8\u0086\u00b3\u00ff\u00ff@P\u008dE\u00fc\u00b9\u0001\u0000\u0000\u0000\u008b\u00158\u0090@\u0000\u00e8-\u00b5\u00ff\u00ff\u0083\u00c4\u0004\u008bE\u00fc\u00e8f\u00b3\u00ff\u00ff\u008bU\u00fc\u008dD\u0082\u00fc\u008bU\u00f8\u00e8\u00d7\u00a5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u00d8\u009a@\u0000\u008dE\u00f8\u00e8n\u00a5\u00ff\u00ff\u008dE\u00fc\u008b\u00158\u0090@\u0000\u00e8\u00fc\u00b4\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x004e0000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 287
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "advapi32.dll\u0000",
"process_handle": "0x000000e0",
"base_address": "0x004f0000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 294
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u00d7I\u00bcu\u0000\u0000O\u0000\u00ff\u0010\u00bcu",
"process_handle": "0x000000e0",
"base_address": "0x00500000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 296
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00f4\u008bE\b\u008b\u0010\u0089U\u00f4\u008bP\u0004\u0089U\u00f8\u008bP\b\u0089U\u00fc\u00ffu\u00f8\u00ffU\u00f4\u00b8\u00ff\u00ff\u00ff\u00ffP\u00ffU\u00fc\u00eb\u00f5\u008b\u00e5]\u00c2\u0004\u0000\u008d@\u0000U\u008b\u00ec\u0083\u00c4\u00f0SV\u0089U\u00fc\u008b\u00f0\u008bE\u00fc\u00e8\u00cb\u00af\u00ff\u00ff3\u00c0Uh\u008d\u0095@\u0000d\u00ff0d\u0089 3\u00dbh\u009c\u0095@\u0000h\u00a4\u0095@\u0000\u00e8h\u00c5\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00f8h\u00b0\u0095@\u0000h\u00a4\u0095@\u0000\u00e8L\u00c5\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00f0\u008bE\u00fc\u00e8\u008b\u00af\u00ff\u00ff\u008b\u00d0\u008b\u00c6\u00e8\"\u00fe\u00ff\u00ff\u0089E\u00f4j\fj\u0000\u008dM\u00f0\u00ba\u00a8\u0094@\u0000\u008b\u00c6\u00e8\u00d0\u00fe\u00ff\u00ff\u0085\u00c0t\u0013P\u00a1\u00bc;A\u0000\u008b\u0000\u00ff\u00d0\u00b3\u0001jd\u00e8Q\u00c5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u0094\u0095@\u0000\u008dE\u00fc\u00e8\u00a4\u00aa\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x00510000"
},
"time": 1564815186.8754,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 298
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "LsaClose",
"process_handle": "0x000000e0",
"base_address": "0x00520000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 309
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "advapi32.dll\u0000",
"process_handle": "0x000000e0",
"base_address": "0x00530000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 311
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u0098\u00d5\u00bew\"\u0012\u00bcuE\u0012\u00bcu\u0000\u0000S\u0000\u0000\u0000R\u0000",
"process_handle": "0x000000e0",
"base_address": "0x00540000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 313
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00ecVW\u008bE\b\u008b\u00f0\u008d}\u00ec\u00a5\u00a5\u00a5\u00a5\u00a5\u00ffu\u00f8\u00ffU\u00f4\u00ffu\u00fcP\u00ffU\u00f0P\u00ffU\u00ec_^\u008b\u00e5]\u00c2\u0004\u0000\u008b\u00c0U\u008b\u00ec\u0083\u00c4\u00e0SVW\u0089M\u00f8\u0089U\u00fc\u008b\u00d8\u008bu\b3\u00ffh\u0010\u009a@\u0000h$\u009a@\u0000\u00e8\u000f\u00c1\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e8h0\u009a@\u0000h$\u009a@\u0000\u00e8\u00f3\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e4h@\u009a@\u0000h$\u009a@\u0000\u00e8\u00d7\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e0\u0083\u00fe\u0004u\b\u008bE\u00f8\u0089E\u00f0\u00eb\u000f\u008b\u00ce\u008bU\u00f8\u008b\u00c3\u00e85\u00fa\u00ff\u00ff\u0089E\u00f0\u008bU\u00fc\u008b\u00c3\u00e8\u0098\u00f9\u00ff\u00ff\u0089E\u00ecj\u0014j\u0000\u008dM\u00e0\u00ba\u0014\u0099@\u0000\u008b\u00c3\u00e8F\u00fa\u00ff\u00ff\u008b\u00d8\u0085\u00dbt\u0015j\u00ffS\u00e8\u0000\u00c1\u00ff\u00ff\u008dE\u00f4PS\u00e8N\u00c0\u00ff\u00ff\u008b}\u00f4\u008b\u00c7_^[\u008b\u00e5]\u00c2\u0004\u0000GetModuleHandleA\u0000\u0000\u0000\u0000kernel32\u0000\u0000\u0000\u0000GetProcAddress\u0000\u0000ExitThread\u0000\u0000U\u008b\u00ec\u0083\u00c4\u00f8\u0089U\u00f8\u0089E\u00fc\u008bE\u00fc\u00e8\u00d0\u00b5\u00ff\u00ff\u008bE\u00f8\u00e8T\u00aa\u00ff\u00ff3\u00c0Uh\u00d1\u009a@\u0000d\u00ff0d\u0089 \u008bE\u00fc\u00e8\u0086\u00b3\u00ff\u00ff@P\u008dE\u00fc\u00b9\u0001\u0000\u0000\u0000\u008b\u00158\u0090@\u0000\u00e8-\u00b5\u00ff\u00ff\u0083\u00c4\u0004\u008bE\u00fc\u00e8f\u00b3\u00ff\u00ff\u008bU\u00fc\u008dD\u0082\u00fc\u008bU\u00f8\u00e8\u00d7\u00a5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u00d8\u009a@\u0000\u008dE\u00f8\u00e8n\u00a5\u00ff\u00ff\u008dE\u00fc\u008b\u00158\u0090@\u0000\u00e8\u00fc\u00b4\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x00550000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 315
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "crypt32.dll\u0000",
"process_handle": "0x000000e0",
"base_address": "0x00560000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 322
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u00d7I\u00bcu\u0000\u0000V\u0000\u00ff\u0010\u00bcu",
"process_handle": "0x000000e0",
"base_address": "0x00570000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 324
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00f4\u008bE\b\u008b\u0010\u0089U\u00f4\u008bP\u0004\u0089U\u00f8\u008bP\b\u0089U\u00fc\u00ffu\u00f8\u00ffU\u00f4\u00b8\u00ff\u00ff\u00ff\u00ffP\u00ffU\u00fc\u00eb\u00f5\u008b\u00e5]\u00c2\u0004\u0000\u008d@\u0000U\u008b\u00ec\u0083\u00c4\u00f0SV\u0089U\u00fc\u008b\u00f0\u008bE\u00fc\u00e8\u00cb\u00af\u00ff\u00ff3\u00c0Uh\u008d\u0095@\u0000d\u00ff0d\u0089 3\u00dbh\u009c\u0095@\u0000h\u00a4\u0095@\u0000\u00e8h\u00c5\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00f8h\u00b0\u0095@\u0000h\u00a4\u0095@\u0000\u00e8L\u00c5\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00f0\u008bE\u00fc\u00e8\u008b\u00af\u00ff\u00ff\u008b\u00d0\u008b\u00c6\u00e8\"\u00fe\u00ff\u00ff\u0089E\u00f4j\fj\u0000\u008dM\u00f0\u00ba\u00a8\u0094@\u0000\u008b\u00c6\u00e8\u00d0\u00fe\u00ff\u00ff\u0085\u00c0t\u0013P\u00a1\u00bc;A\u0000\u008b\u0000\u00ff\u00d0\u00b3\u0001jd\u00e8Q\u00c5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u0094\u0095@\u0000\u008dE\u00fc\u00e8\u00a4\u00aa\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x00580000"
},
"time": 1564815186.9844,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 326
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "CryptUnprotectData",
"process_handle": "0x000000e0",
"base_address": "0x005a0000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 337
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "crypt32.dll\u0000",
"process_handle": "0x000000e0",
"base_address": "0x005b0000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 339
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u0098\u00d5\u00bew\"\u0012\u00bcuE\u0012\u00bcu\u0000\u0000[\u0000\u0000\u0000Z\u0000",
"process_handle": "0x000000e0",
"base_address": "0x005c0000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 341
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00ecVW\u008bE\b\u008b\u00f0\u008d}\u00ec\u00a5\u00a5\u00a5\u00a5\u00a5\u00ffu\u00f8\u00ffU\u00f4\u00ffu\u00fcP\u00ffU\u00f0P\u00ffU\u00ec_^\u008b\u00e5]\u00c2\u0004\u0000\u008b\u00c0U\u008b\u00ec\u0083\u00c4\u00e0SVW\u0089M\u00f8\u0089U\u00fc\u008b\u00d8\u008bu\b3\u00ffh\u0010\u009a@\u0000h$\u009a@\u0000\u00e8\u000f\u00c1\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e8h0\u009a@\u0000h$\u009a@\u0000\u00e8\u00f3\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e4h@\u009a@\u0000h$\u009a@\u0000\u00e8\u00d7\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e0\u0083\u00fe\u0004u\b\u008bE\u00f8\u0089E\u00f0\u00eb\u000f\u008b\u00ce\u008bU\u00f8\u008b\u00c3\u00e85\u00fa\u00ff\u00ff\u0089E\u00f0\u008bU\u00fc\u008b\u00c3\u00e8\u0098\u00f9\u00ff\u00ff\u0089E\u00ecj\u0014j\u0000\u008dM\u00e0\u00ba\u0014\u0099@\u0000\u008b\u00c3\u00e8F\u00fa\u00ff\u00ff\u008b\u00d8\u0085\u00dbt\u0015j\u00ffS\u00e8\u0000\u00c1\u00ff\u00ff\u008dE\u00f4PS\u00e8N\u00c0\u00ff\u00ff\u008b}\u00f4\u008b\u00c7_^[\u008b\u00e5]\u00c2\u0004\u0000GetModuleHandleA\u0000\u0000\u0000\u0000kernel32\u0000\u0000\u0000\u0000GetProcAddress\u0000\u0000ExitThread\u0000\u0000U\u008b\u00ec\u0083\u00c4\u00f8\u0089U\u00f8\u0089E\u00fc\u008bE\u00fc\u00e8\u00d0\u00b5\u00ff\u00ff\u008bE\u00f8\u00e8T\u00aa\u00ff\u00ff3\u00c0Uh\u00d1\u009a@\u0000d\u00ff0d\u0089 \u008bE\u00fc\u00e8\u0086\u00b3\u00ff\u00ff@P\u008dE\u00fc\u00b9\u0001\u0000\u0000\u0000\u008b\u00158\u0090@\u0000\u00e8-\u00b5\u00ff\u00ff\u0083\u00c4\u0004\u008bE\u00fc\u00e8f\u00b3\u00ff\u00ff\u008bU\u00fc\u008dD\u0082\u00fc\u008bU\u00f8\u00e8\u00d7\u00a5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u00d8\u009a@\u0000\u008dE\u00f8\u00e8n\u00a5\u00ff\u00ff\u008dE\u00fc\u008b\u00158\u0090@\u0000\u00e8\u00fc\u00b4\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x005d0000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 343
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "gdi32.dll\u0000",
"process_handle": "0x000000e0",
"base_address": "0x00620000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 350
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u00d7I\u00bcu\u0000\u0000b\u0000\u00ff\u0010\u00bcu",
"process_handle": "0x000000e0",
"base_address": "0x00630000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 352
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00f4\u008bE\b\u008b\u0010\u0089U\u00f4\u008bP\u0004\u0089U\u00f8\u008bP\b\u0089U\u00fc\u00ffu\u00f8\u00ffU\u00f4\u00b8\u00ff\u00ff\u00ff\u00ffP\u00ffU\u00fc\u00eb\u00f5\u008b\u00e5]\u00c2\u0004\u0000\u008d@\u0000U\u008b\u00ec\u0083\u00c4\u00f0SV\u0089U\u00fc\u008b\u00f0\u008bE\u00fc\u00e8\u00cb\u00af\u00ff\u00ff3\u00c0Uh\u008d\u0095@\u0000d\u00ff0d\u0089 3\u00dbh\u009c\u0095@\u0000h\u00a4\u0095@\u0000\u00e8h\u00c5\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00f8h\u00b0\u0095@\u0000h\u00a4\u0095@\u0000\u00e8L\u00c5\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00f0\u008bE\u00fc\u00e8\u008b\u00af\u00ff\u00ff\u008b\u00d0\u008b\u00c6\u00e8\"\u00fe\u00ff\u00ff\u0089E\u00f4j\fj\u0000\u008dM\u00f0\u00ba\u00a8\u0094@\u0000\u008b\u00c6\u00e8\u00d0\u00fe\u00ff\u00ff\u0085\u00c0t\u0013P\u00a1\u00bc;A\u0000\u008b\u0000\u00ff\u00d0\u00b3\u0001jd\u00e8Q\u00c5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u0094\u0095@\u0000\u008dE\u00fc\u00e8\u00a4\u00aa\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x00640000"
},
"time": 1564815187.1094,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 354
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "SetROP2",
"process_handle": "0x000000e0",
"base_address": "0x006d0000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 365
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "gdi32.dll\u0000",
"process_handle": "0x000000e0",
"base_address": "0x006e0000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 367
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u0098\u00d5\u00bew\"\u0012\u00bcuE\u0012\u00bcu\u0000\u0000n\u0000\u0000\u0000m\u0000",
"process_handle": "0x000000e0",
"base_address": "0x006f0000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 369
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00ecVW\u008bE\b\u008b\u00f0\u008d}\u00ec\u00a5\u00a5\u00a5\u00a5\u00a5\u00ffu\u00f8\u00ffU\u00f4\u00ffu\u00fcP\u00ffU\u00f0P\u00ffU\u00ec_^\u008b\u00e5]\u00c2\u0004\u0000\u008b\u00c0U\u008b\u00ec\u0083\u00c4\u00e0SVW\u0089M\u00f8\u0089U\u00fc\u008b\u00d8\u008bu\b3\u00ffh\u0010\u009a@\u0000h$\u009a@\u0000\u00e8\u000f\u00c1\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e8h0\u009a@\u0000h$\u009a@\u0000\u00e8\u00f3\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e4h@\u009a@\u0000h$\u009a@\u0000\u00e8\u00d7\u00c0\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00e0\u0083\u00fe\u0004u\b\u008bE\u00f8\u0089E\u00f0\u00eb\u000f\u008b\u00ce\u008bU\u00f8\u008b\u00c3\u00e85\u00fa\u00ff\u00ff\u0089E\u00f0\u008bU\u00fc\u008b\u00c3\u00e8\u0098\u00f9\u00ff\u00ff\u0089E\u00ecj\u0014j\u0000\u008dM\u00e0\u00ba\u0014\u0099@\u0000\u008b\u00c3\u00e8F\u00fa\u00ff\u00ff\u008b\u00d8\u0085\u00dbt\u0015j\u00ffS\u00e8\u0000\u00c1\u00ff\u00ff\u008dE\u00f4PS\u00e8N\u00c0\u00ff\u00ff\u008b}\u00f4\u008b\u00c7_^[\u008b\u00e5]\u00c2\u0004\u0000GetModuleHandleA\u0000\u0000\u0000\u0000kernel32\u0000\u0000\u0000\u0000GetProcAddress\u0000\u0000ExitThread\u0000\u0000U\u008b\u00ec\u0083\u00c4\u00f8\u0089U\u00f8\u0089E\u00fc\u008bE\u00fc\u00e8\u00d0\u00b5\u00ff\u00ff\u008bE\u00f8\u00e8T\u00aa\u00ff\u00ff3\u00c0Uh\u00d1\u009a@\u0000d\u00ff0d\u0089 \u008bE\u00fc\u00e8\u0086\u00b3\u00ff\u00ff@P\u008dE\u00fc\u00b9\u0001\u0000\u0000\u0000\u008b\u00158\u0090@\u0000\u00e8-\u00b5\u00ff\u00ff\u0083\u00c4\u0004\u008bE\u00fc\u00e8f\u00b3\u00ff\u00ff\u008bU\u00fc\u008dD\u0082\u00fc\u008bU\u00f8\u00e8\u00d7\u00a5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u00d8\u009a@\u0000\u008dE\u00f8\u00e8n\u00a5\u00ff\u00ff\u008dE\u00fc\u008b\u00158\u0090@\u0000\u00e8\u00fc\u00b4\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x00700000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 371
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "ole32.dll\u0000",
"process_handle": "0x000000e0",
"base_address": "0x00710000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 378
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "\u00d7I\u00bcu\u0000\u0000q\u0000\u00ff\u0010\u00bcu",
"process_handle": "0x000000e0",
"base_address": "0x00720000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 380
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "U\u008b\u00ec\u0083\u00c4\u00f4\u008bE\b\u008b\u0010\u0089U\u00f4\u008bP\u0004\u0089U\u00f8\u008bP\b\u0089U\u00fc\u00ffu\u00f8\u00ffU\u00f4\u00b8\u00ff\u00ff\u00ff\u00ffP\u00ffU\u00fc\u00eb\u00f5\u008b\u00e5]\u00c2\u0004\u0000\u008d@\u0000U\u008b\u00ec\u0083\u00c4\u00f0SV\u0089U\u00fc\u008b\u00f0\u008bE\u00fc\u00e8\u00cb\u00af\u00ff\u00ff3\u00c0Uh\u008d\u0095@\u0000d\u00ff0d\u0089 3\u00dbh\u009c\u0095@\u0000h\u00a4\u0095@\u0000\u00e8h\u00c5\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00f8h\u00b0\u0095@\u0000h\u00a4\u0095@\u0000\u00e8L\u00c5\u00ff\u00ffP\u00a1P:A\u0000\u008b\u0000\u00ff\u00d0\u0089E\u00f0\u008bE\u00fc\u00e8\u008b\u00af\u00ff\u00ff\u008b\u00d0\u008b\u00c6\u00e8\"\u00fe\u00ff\u00ff\u0089E\u00f4j\fj\u0000\u008dM\u00f0\u00ba\u00a8\u0094@\u0000\u008b\u00c6\u00e8\u00d0\u00fe\u00ff\u00ff\u0085\u00c0t\u0013P\u00a1\u00bc;A\u0000\u008b\u0000\u00ff\u00d0\u00b3\u0001jd\u00e8Q\u00c5\u00ff\u00ff3\u00c0ZYYd\u0089\u0010h\u0094\u0095@\u0000\u008dE\u00fc\u00e8\u00a4\u00aa\u00ff\u00ff\u00c3",
"process_handle": "0x000000e0",
"base_address": "0x00730000"
},
"time": 1564815187.2194,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 382
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "CoInitialize",
"process_handle": "0x000000e0",
"base_address": "0x00780000"
},
"time": 1564815187.3284,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 393
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "WriteProcessMemory",
"return_value": 1,
"arguments": {
"process_identifier": 2952,
"buffer": "ole32.dll\u0000",
"process_handle": "0x000000e0",
"base_address": "0x00790000"
},
"time": 1564815187.3284,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 395
}
],
"references": [],
"name": "injection_write_memory"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 662,
"time": 6.222461938858,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 5342,
"time": 12.207713127136,
"dport": 138,
"sport": 138
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7186,
"time": 6.1586129665375,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7514,
"time": 4.1586050987244,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7842,
"time": 6.1702480316162,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8170,
"time": 4.6618700027466,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8498,
"time": 3.055459022522,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 8826,
"time": 4.6780450344086,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 28236,
"time": 4.1798660755157,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 36620,
"time": 6.2534461021423,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "fe77b256c07f535b63a9ba8f81fc882279019d24ea7d1d15c6485cd91139e5d8",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "84eeb589b62b28de283316442981f5e6822943ccead5f2d0a728c06066896c3c",
"irc": [],
"https_ex": []
}Screenshots
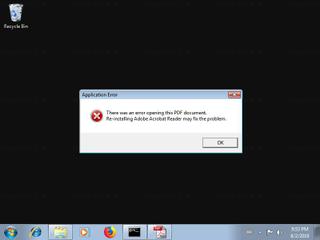
detailsofAmazonOrderIDpdf.exe removal instructions
The instructions below shows how to remove detailsofAmazonOrderIDpdf.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the detailsofAmazonOrderIDpdf.exe file for removal, restart your computer and scan it again to verify that detailsofAmazonOrderIDpdf.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate detailsofAmazonOrderIDpdf.exe in the scan result and tick the checkbox next to the detailsofAmazonOrderIDpdf.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate detailsofAmazonOrderIDpdf.exe in the scan result.

 c:\downloads\detailsofAmazonOrderIDpdf.exe
c:\downloads\detailsofAmazonOrderIDpdf.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If detailsofAmazonOrderIDpdf.exe still remains in the scan result, proceed with the next step. If detailsofAmazonOrderIDpdf.exe is gone from the scan result you're done.
- If detailsofAmazonOrderIDpdf.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that detailsofAmazonOrderIDpdf.exe no longer appear in the scan result.
Hashes [?]
| Property | Value |
|---|---|
| MD5 | 8798f177460ec7f94a33df27954bd546 |
| SHA256 | 78e13ea6cfb01bf2d56c3ff46546e98c942a3d448baa8f902649740b3369e6ba |
Error Messages
These are some of the error messages that can appear related to detailsofamazonorderidpdf.exe:
detailsofamazonorderidpdf.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
detailsofamazonorderidpdf.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
detailsofamazonorderidpdf.exe has stopped working.
End Program - detailsofamazonorderidpdf.exe. This program is not responding.
detailsofamazonorderidpdf.exe is not a valid Win32 application.
detailsofamazonorderidpdf.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with the file?
To help other users, please let us know what you will do with the file:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.