What is ouhqws.exe?
ouhqws.exe is usually located in the 'd:\' folder.
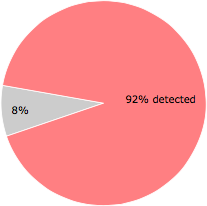
Some of the anti-virus scanners at VirusTotal detected ouhqws.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
VirusTotal report
65 of the 71 anti-virus programs at VirusTotal detected the ouhqws.exe file. That's a 92% detection rate.
| Scanner | Detection Name |
|---|---|
| Acronis | suspicious |
| Ad-Aware | Win32.Sality.3 |
| AhnLab-V3 | Win32/Kashu.E |
| ALYac | Worm.Sality.3.Gen |
| Antiy-AVL | Virus/Win32.Sality.gen |
| APEX | Malicious |
| Arcabit | Win32.Sality.3 |
| Avast | Win32:Sality |
| AVG | Win32:Sality |
| Avira | W32/Sality.AT |
| Baidu | Win32.Trojan.Sality.p |
| BitDefender | Win32.Sality.3 |
| Bkav | W32.Sality.PE |
| CAT-QuickHeal | W32.Sality.U |
| ClamAV | Win.Virus.Sality-1067 |
| Comodo | Virus.Win32.Sality.gen@1egj5j |
| CrowdStrike | win/malicious_confidence_100% (D) |
| Cybereason | malicious.697d9d |
| Cylance | Unsafe |
| Cyren | W32/Sality.gen2 |
| DrWeb | Win32.Sector.31 |
| eGambit | Trojan.Generic |
| Emsisoft | Win32.Sality.3 (B) |
| Endgame | malicious (high confidence) |
| ESET-NOD32 | Win32/Sality |
| F-Prot | W32/Sality.gen2 |
| F-Secure | Malware.W32/Sality.AT |
| FireEye | Generic.mg.b6bd427697d9df51 |
| Fortinet | W32/LPECrypt.A!tr |
| GData | Win32.Sality.3 |
| Ikarus | Virus.Win32.Sality |
| Invincea | heuristic |
| Jiangmin | Win32/HLLP.Kuku.poly2 |
| K7AntiVirus | Trojan ( 001e7bc71 ) |
| K7GW | Trojan ( 001e7bc71 ) |
| Kaspersky | Virus.Win32.Sality.gen |
| Malwarebytes | Trojan.MalPack.Gen |
| MAX | malware (ai score=86) |
| MaxSecure | Trojan.LordPE |
| McAfee | W32/Sality.gen.z |
| McAfee-GW-Edition | BehavesLike.Win32.Sality.cc |
| Microsoft | Virus:Win32/Sality.AT |
| MicroWorld-eScan | Win32.Sality.3 |
| NANO-Antivirus | Virus.Win32.Sality.beygb |
| Panda | W32/Sality.AK.drp |
| Qihoo-360 | Trojan.Win32.SalityStub.A |
| Rising | Virus.Sality!1.A5BD (CLASSIC) |
| SentinelOne | DFI - Malicious PE |
| Sophos | Troj/SalLoad-C |
| SUPERAntiSpyware | Trojan.Agent/Gen-Packed[LordPE] |
| Symantec | W32.Sality!dr |
| TACHYON | Virus/W32.Sality.D |
| Tencent | Trojan.Win32.SalityStub.a |
| TotalDefense | Win32/Sality.AA |
| Trapmine | malicious.high.ml.score |
| TrendMicro | PE_SALITY.RL-O |
| TrendMicro-HouseCall | PE_SALITY.RL-O |
| VBA32 | Virus.Win32.Sality.bakc |
| VIPRE | Virus.Win32.Sality.at (v) |
| ViRobot | Win32.Sality.N.Host |
| Webroot | W32.Sality |
| Yandex | Win32.Sality.BL |
| Zillya | Virus.Sality.Win32.25 |
| ZoneAlarm | Virus.Win32.Sality.gen |
| Zoner | Trojan.Win32.Sality.22009 |
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe"
],
"directory_created": [
"C:\\Users\\cuck",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Windows\\Themes\\",
"C:\\Users\\cuck\\AppData\\Roaming",
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\Caches"
],
"dll_loaded": [
"API-MS-Win-Security-LSALookup-L1-1-0.dll",
"apphelp.dll",
"kernel32.dll",
"MSVCRT.dll",
"POWRPROF.DLL",
"slc.dll",
"ntmarta.dll",
"API-MS-WIN-Service-Management-L1-1-0.dll",
"PROPSYS.dll",
"API-MS-Win-Core-LocalRegistry-L1-1-0.dll",
"KERNEL32.DLL",
"API-MS-WIN-Service-winsvc-L1-1-0.dll",
"ole32.dll",
"USER32.dll",
"fxsst.dll",
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"WININET.DLL",
"ADVAPI32.dll",
"OLEAUT32",
"OLEAUT32.dll",
"profapi.dll",
"SHELL32.dll",
"C:\\Windows\\system32\\FXSRESM.DLL",
"sfc",
"comctl32.dll",
"VERSION.dll",
"MPR",
"DEVRTL.dll",
"SHELL32.DLL",
"SETUPAPI.dll",
"WS2_32.dll"
],
"file_opened": [
"C:\\Windows\\System32\\ExplorerFrame.dll",
"C:\\Windows\\system.ini",
"C:\\Windows\\AppPatch\\sysmain.sdb",
"C:\\",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\FXSAPIDebugLogFile.txt",
"C:\\Windows\\System32\\",
"C:\\Users\\desktop.ini",
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\Caches\\{AFBF9F1A-8EE8-4C77-AF34-C647E37CA0D9}.1.ver0x0000000000000004.db",
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\Caches\\cversions.1.db",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Windows\\Themes\\slideshow.ini",
"C:\\Users\\cuck\\Desktop\\desktop.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe",
"C:\\Program Files (x86)\\desktop.ini",
"C:\\Windows\\winsxs\\FileMaps\\program_files_common_files_microsoft_shared_ink_3c86e3db0b3b254c.cdf-ms",
"C:\\Program Files\\desktop.ini",
"C:\\Windows\\System32\\explorerframe.dll"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Action Center\\Checks\\{01979c6a-42fa-414c-b8aa-eee2c8202018}.check.100",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\NonEnum",
"HKEY_CURRENT_USER\\Software\\Classes\\Local Settings\\Software\\Microsoft\\Windows\\Shell\\MuiCache ",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Security Center",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\KnownFolderSettings",
"HKEY_CURRENT_USER\\AppEvents\\EventLabels\\FaxSent",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Associations\\UrlAssociations\\Drive",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\FolderDescriptions",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_CLASSES_ROOT\\Drive",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Shell Extensions\\Blocked",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\(Default)",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Setup",
"HKEY_CLASSES_ROOT\\Drive\\shellex\\FolderExtensions\\{fbeb8a05-beee-4442-804e-409d6c4515e9}",
"HKEY_CURRENT_USER\\Software\\Arxv",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\shell\\open",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_CLASSES_ROOT\\Folder",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\crypt32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\shell\\open",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\NonEnum",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\policies\\system",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile",
"HKEY_CLASSES_ROOT\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Security Center\\Svc",
"HKEY_LOCAL_MACHINE\\System\\Setup",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_CLASSES_ROOT\\Drive\\shellex\\FolderExtensions",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\(Default)",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Control\\LSA\\AccessProviders",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fax\\Client\\ServiceStartup",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}",
"HKEY_CURRENT_USER\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\SessionInfo\\1\\KnownFolders",
"HKEY_LOCAL_MACHINE\\system\\CurrentControlSet\\control\\NetworkProvider\\HwOrder",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open\\command",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PropertyBag",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Shell Extensions\\Cached",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Run",
"HKEY_CLASSES_ROOT\\SystemFileAssociations\\Drive.Fixed",
"HKEY_LOCAL_MACHINE\\software\\microsoft\\windows\\currentversion\\setup\\PnpLockdownFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\PropertyBag",
"HKEY_CLASSES_ROOT\\CLSID\\{11DBB47C-A525-400B-9E80-A54615A090C0}\\SupportedProtocols",
"HKEY_CURRENT_USER\\Control Panel\\Personalization\\Desktop Slideshow",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\Shell\\RegisteredApplications\\UrlAssociations\\Drive\\OpenWithProgids",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\LDAP",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile\\AuthorizedApplications\\List",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\OLE\\Tracing",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\ShellCompatibility\\Applications\\de14f613fc54eb167248c47264de132c8dbecaef94b42cba4ee61623f5a424f7.bin",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\CurVer",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Shell Extensions\\Blocked",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\SessionInfo\\1",
"HKEY_CLASSES_ROOT\\CLSID\\{11DBB47C-A525-400B-9E80-A54615A090C0}\\InProcServer32",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\ShellNoRoam\\MUICache"
],
"command_line": [
"C:\\"
],
"file_written": [
"C:\\Windows\\system.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe"
],
"file_exists": [
"C:\\Users\\cuck",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe",
"C:\\",
"C:\\Users\\cuck\\AppData\\Roaming",
"C:\\Windows\\System32\\explorerframe.dll"
],
"mutex": [
"svchost.exeM_316_",
"cmd.exeM_1692_",
"svchost.exeM_1216_",
"svchost.exeM_660_",
"lsass.exeM_476_",
"svchost.exeM_276_",
"explorer.exeM_1788_",
"mobsync.exeM_1636_",
"wmpnetwk.exeM_1856_",
"svchost.exeM_712_",
"winlogon.exeM_424_",
"dwm.exeM_1768_",
"taskhost.exeM_1928_",
"wininit.exeM_376_",
"searchprotocolhost.exeM_304_",
"taskhost.exeM_1724_",
"conhost.exeM_1700_",
"svchost.exeM_1000_",
"lsm.exeM_484_",
"csrss.exeM_328_",
"svchost.exeM_480_",
"smss.exeM_252_",
"explorer.exeM_2672_",
"de14f613fc54eb167248c47264de132c8dbecaef94b42cba4ee61623f5a424fM_2124_",
"spoolsv.exeM_1084_",
"csrss.exeM_384_",
"audiodg.exeM_2560_",
"services.exeM_468_",
"svchost.exeM_880_",
"svchost.exeM_1548_",
"uxJLpe1m",
"searchfilterhost.exeM_2448_",
"svchost.exeM_592_",
"python.exeM_3032_",
"svchost.exeM_804_",
"Ap1mutx7",
"searchprotocolhost.exeM_3004_",
"python.exeM_2168_",
"svchost.exeM_3064_",
"svchost.exeM_1120_",
"searchindexer.exeM_1316_"
],
"file_failed": [
"\\??\\L:",
"\\??\\N:",
"\\??\\U:",
"\\??\\H:",
"\\??\\W:",
"\\??\\J:",
"\\??\\Q:",
"\\??\\D:",
"\\??\\S:",
"\\??\\F:",
"\\??\\M:",
"\\??\\X:",
"\\??\\Z:",
"C:\\desktop.ini",
"C:\\Windows\\winsxs\\FileMaps\\users_cuck_appdata_local_temp_c2004f3465698a5a.cdf-ms",
"\\??\\O:",
"\\??\\I:",
"\\??\\T:",
"\\??\\V:",
"\\??\\K:",
"\\??\\E:",
"\\??\\P:",
"\\??\\R:",
"\\??\\G:",
"\\??\\Y:"
],
"guid": [
"{b57046bc-32e5-428a-9887-19f712b907bf}",
"{9ba05972-f6a8-11cf-a442-00a0c90a8f39}",
"{ba126ae5-2166-11d1-b1d0-00805fc1270e}",
"{00000320-0000-0000-c000-000000000046}",
"{5762f2a7-4658-4c7a-a4ac-bdabfe154e0d}",
"{00000146-0000-0000-c000-000000000046}",
"{d0074ffd-570f-4a9b-8d69-199fdba5723b}",
"{75847177-f077-4171-bd2c-a6bb2164fbd0}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{11dbb47c-a525-400b-9e80-a54615a090c0}",
"{000214e6-0000-0000-c000-000000000046}",
"{1f486a52-3cb1-48fd-8f50-b8dc300d9f9d}",
"{00000323-0000-0000-c000-000000000046}",
"{ba126ad1-2166-11d1-b1d0-00805fc1270e}",
"{faedcf69-31fe-11d1-aad2-00805fc1270e}",
"{489e9453-869b-4bcc-a1c7-48b5285fd9d8}",
"{a47979d2-c419-11d9-a5b4-001185ad2b89}",
"{7007acc7-3202-11d1-aad2-00805fc1270e}",
"{682159d9-c321-47ca-b3f1-30e36b2ec8b9}",
"{85cb6900-4d95-11cf-960c-0080c7f4ee85}",
"{7f9185b0-cb92-43c5-80a9-92277a4f7b54}",
"{b196b284-bab4-101a-b69c-00aa00341d07}"
],
"file_read": [
"C:\\Users\\cuck\\Desktop\\desktop.ini",
"C:\\Users\\desktop.ini",
"C:\\Windows\\system.ini",
"C:\\Program Files (x86)\\desktop.ini",
"C:\\Windows\\winsxs\\FileMaps\\program_files_common_files_microsoft_shared_ink_3c86e3db0b3b254c.cdf-ms",
"C:\\Program Files\\desktop.ini",
"C:\\Windows\\System32\\ExplorerFrame.dll"
],
"regkey_read": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\ListviewAlphaSelect",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Icon",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseHostnameAsAlias",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoSetFolders",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\WantsFORDISPLAY",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\SourcePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open\\ExplorerHost",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\RelativePath",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@C:\\Windows\\system32\\prnfldr.dll,-8036",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\RestrictedAttributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Category",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseOldHostResolutionOrder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\DisableImprovedZoneCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\InProcServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoInternetIcon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\SortOrderIndex",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\WantsUniversalDelegate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\QueryForOverlay",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\MapNetDriveVerbs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\QueryForInfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\NoFileFolderJunction",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\NonEnum\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{21EC2020-3AEA-1069-A2DD-08002B30309D}\\SortOrderIndex",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Open\\.Current\\Default Flags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Attributes",
"HKEY_CURRENT_USER\\Software\\Arxv\\c1_1",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\WantsParseDisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open\\LocalServerOnly",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DebugHeapFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoDriveTypeAutoRun",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\WantsAliasedNotifications",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Close\\.Current\\Default Flags",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\UseDropHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoCommonGroups",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\PinToNameSpaceTree",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\FolderTypeID",
"HKEY_CURRENT_USER\\Software\\Arxv\\c3_0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\LdapClientIntegrity",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\InitFolderHandler",
"HKEY_CURRENT_USER\\Control Panel\\Personalization\\Desktop Slideshow\\AnimationDuration",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\WantsFORPARSING",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\InProcServer32\\LoadWithoutCOM",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\LocalizedString",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\{B725F130-47EF-101A-A5F1-02608C9EEBAC} 10",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open\\command\\DelegateExecute",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{2227A280-3AEA-1069-A2DE-08002B30309D}\\{B725F130-47EF-101A-A5F1-02608C9EEBAC} 10",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\PnpLockdownFiles\\%SystemDrive%\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\HideFolderVerbs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Description",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\Desktop",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Interface\\{2ABC0864-9677-42E5-882A-D415C556C284}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoDriveAutoRun",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Security",
"HKEY_CURRENT_USER\\Software\\Arxv\\c2_0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\HideInWebView",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorUseSystemHeap",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open\\LaunchExplorerFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\LocalRedirectOnly",
"HKEY_CURRENT_USER\\Control Panel\\Personalization\\Desktop Slideshow\\Flags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoPropertiesRecycleBin",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Close\\.Current\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\CallForAttributes",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\AccessProviders\\MartaExtension",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoPropertiesMyComputer",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorSystemHeapIsPrivate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\StreamResourceType",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{2227A280-3AEA-1069-A2DE-08002B30309D}\\LocalizedString",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Security",
"HKEY_CURRENT_USER\\Software\\Arxv\\c1_0",
"HKEY_CURRENT_USER\\Control Panel\\Personalization\\Desktop Slideshow\\Interval",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\ParsingName",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\EnableBalloonTips",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoDrives",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Security_HKLM_only",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\DevicePath",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Open\\.Current\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\System.ItemNameDisplay",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Stream",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\ParsingName",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@C:\\Windows\\system32\\netshell.dll,-1200",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\PreCreate",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Shell Extensions\\Cached\\{11DBB47C-A525-400B-9E80-A54615A090C0} {7F9185B0-CB92-43C5-80A9-92277A4F7B54} 0xFFFF",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\shellex\\FolderExtensions\\{fbeb8a05-beee-4442-804e-409d6c4515e9}\\DriveMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\HasNavigationEnum",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Category",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\InfoTip",
"HKEY_CURRENT_USER\\Software\\Arxv\\c4_0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\HideOnDesktopPerUser",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{2227A280-3AEA-1069-A2DE-08002B30309D}\\System.ItemNameDisplay",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{11DBB47C-A525-400B-9E80-A54615A090C0}\\InProcServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\LocalRedirectOnly",
"HKEY_CURRENT_USER\\Control Panel\\Personalization\\Desktop Slideshow\\Shuffle",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\AppData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoControlPanel",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\SmoothScroll",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\ListviewShadow",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PreCreate",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\_LabelFromReg",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Roamable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\MUI\\StringCacheSettings\\StringCacheGeneration",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Attributes",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Shell Folders\\Cache",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\ParentFolder"
],
"directory_enumerated": [
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\main\\*",
"F:\\*",
"Y:\\*",
"T:\\*",
"C:\\Windows\\System32\\*.*",
"R:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\hu-HU\\*",
"K:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\*",
"M:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\en-US\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\lv-LV\\*",
"I:\\*",
"D:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\he-IL\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\et-EE\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\keypad\\*",
"C:\\Windows\\System32",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\de-DE\\*",
"P:\\*",
"N:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\web\\*",
"V:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\auxpad\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\oskpred\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\HWRCUSTOMIZATION\\*",
"H:\\*",
"C:\\PerfLogs\\Admin\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\symbols\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\hr-HR\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\lt-LT\\*",
"W:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\fr-FR\\*",
"S:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\OSKNUMPAD\\*",
"U:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\it-IT\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\es-ES\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\ko-KR\\*",
"G:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\ar-SA\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\numbers\\*",
"C:\\*",
"Q:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\fi-FI\\*",
"O:\\*",
"C:\\CUCKOO-AGENT\\*",
"E:\\*",
"C:\\PROGRAM FILES\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\ja-JP\\*",
"Z:\\*",
"X:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\el-GR\\*",
"C:\\PerfLogs\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\cs-CZ\\*",
"C:\\DOCUMENTS AND SETTINGS\\*",
"C:\\Windows",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\bg-BG\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\da-DK\\*",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\*",
"L:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\oskmenu\\*",
"J:\\*"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\System\\EnableLUA",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\AntiVirusOverride",
"HKEY_CURRENT_USER\\Software\\Arxv\\c2_0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\UpdatesDisableNotify",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\UacDisableNotify",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\AntiVirusDisableNotify",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\UacDisableNotify",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile\\DoNotAllowExceptions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\FirewallOverride",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\418466543",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\Hidden",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\1801680227",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\-273140299",
"HKEY_CURRENT_USER\\Software\\Arxv\\c4_0",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\LanguageList",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\AntiVirusDisableNotify",
"HKEY_CURRENT_USER\\Software\\Arxv\\c3_0",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Action Center\\Checks\\{01979c6a-42fa-414c-b8aa-eee2c8202018}.check.100\\CheckSetting",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile\\DisableNotifications",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\UpdatesDisableNotify",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\1110073385",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\GlobalUserOffline",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\-2074820526",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\FirewallDisableNotify",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\-1383213684",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\AntiVirusOverride",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\FirewallOverride",
"HKEY_CURRENT_USER\\Software\\Arxv\\c1_0",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile\\EnableFirewall",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\FirewallDisableNotify",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\-691606842"
]
}Dropped
[
{
"yara": [],
"sha1": "a3bea5e2138d1558109fa26d46e2f79c3a20228f",
"name": "df83a0d6940600e4_avpto.exe",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe",
"type": "PE32 executable (GUI) Intel 80386, for MS Windows",
"sha256": "df83a0d6940600e4c4954f4874fcd4dd73e781e6690c3bf56f51c95285484a3c",
"urls": [],
"crc32": "88CB6BD9",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/2342\/files\/df83a0d6940600e4_avpto.exe",
"ssdeep": null,
"size": 741,
"sha512": "12e26fa999faf2ca017a49987be5c668930495c26c789e19863097e5b0555add90ecdbb397521436acb47d7f2dfd5029b9b4beed16877ac7df854b3321642e37",
"pids": [
2124
],
"md5": "25aa9bb549ecc7bb6100f8d179452508"
},
{
"yara": [],
"sha1": "6aa9f32e6aa345e9e25b7cf9e844467ad06b9931",
"name": "768e884b17555531_system.ini",
"filepath": "C:\\Windows\\system.ini",
"type": "Windows SYSTEM.INI, ASCII text, with CRLF line terminators",
"sha256": "768e884b17555531290250f6cea6a01c03062f7374ed8cb1f4cd4741f4f28506",
"urls": [],
"crc32": "005F0A8E",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/2342\/files\/768e884b17555531_system.ini",
"ssdeep": null,
"size": 256,
"sha512": "3e4c6cd5f9d0a644b3358c2e06c4775b7a61406b1596f0d400a7877261205f7f99edc2c563aeaeb864dff209896f5d0554f861757afb95c1b90ddd6a9d35dc0f",
"pids": [
2124
],
"md5": "7f68515c593dfa77ddbcaaf0a2eaa9bf"
}
]Generic
[
{
"process_path": "C:\\Windows\\System32\\SearchProtocolHost.exe",
"process_name": "SearchProtocolHost.exe",
"pid": 304,
"summary": {
"guid": [
"{00000323-0000-0000-c000-000000000046}",
"{00000146-0000-0000-c000-000000000046}"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles"
]
},
"first_seen": 1567839198.1402,
"ppid": 1316
},
{
"process_path": "C:\\Windows\\System32\\cmd.exe",
"process_name": "cmd.exe",
"pid": 1692,
"summary": {},
"first_seen": 1567839186.7031,
"ppid": 1788
},
{
"process_path": "C:\\Windows\\System32\\taskhost.exe",
"process_name": "taskhost.exe",
"pid": 1724,
"summary": {
"regkey_read": [
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\(Default)",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Close\\.Current\\Default Flags",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Close\\.Current\\(Default)",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Open\\.Current\\(Default)",
"HKEY_CURRENT_USER\\AppEvents\\Schemes\\Apps\\.Default\\Open\\.Current\\Default Flags"
]
},
"first_seen": 1567839186.0938,
"ppid": 468
},
{
"process_path": "C:\\Windows\\System32\\mobsync.exe",
"process_name": "mobsync.exe",
"pid": 1636,
"summary": {},
"first_seen": 1567839187.359,
"ppid": 592
},
{
"process_path": "C:\\Windows\\System32\\dwm.exe",
"process_name": "dwm.exe",
"pid": 1768,
"summary": {},
"first_seen": 1567839186.2812,
"ppid": 804
},
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1567839185.3438,
"ppid": 376
},
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\de14f613fc54eb167248c47264de132c8dbecaef94b42cba4ee61623f5a424f7.bin",
"process_name": "de14f613fc54eb167248c47264de132c8dbecaef94b42cba4ee61623f5a424f7.bin",
"pid": 2124,
"summary": {
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\System\\EnableLUA",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\AntiVirusOverride",
"HKEY_CURRENT_USER\\Software\\Arxv\\c2_0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\UpdatesDisableNotify",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\UacDisableNotify",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\AntiVirusDisableNotify",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\UacDisableNotify",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile\\DoNotAllowExceptions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\FirewallOverride",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\418466543",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\Hidden",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\1801680227",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\-273140299",
"HKEY_CURRENT_USER\\Software\\Arxv\\c4_0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\AntiVirusDisableNotify",
"HKEY_CURRENT_USER\\Software\\Arxv\\c3_0",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile\\DisableNotifications",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\UpdatesDisableNotify",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\1110073385",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\GlobalUserOffline",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\-2074820526",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\FirewallDisableNotify",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\-1383213684",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\AntiVirusOverride",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\FirewallOverride",
"HKEY_CURRENT_USER\\Software\\Arxv\\c1_0",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile\\EnableFirewall",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\FirewallDisableNotify",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959\\-691606842"
],
"dll_loaded": [
"API-MS-Win-Security-LSALookup-L1-1-0.dll",
"apphelp.dll",
"kernel32.dll",
"MSVCRT.dll",
"ntmarta.dll",
"PROPSYS.dll",
"KERNEL32.DLL",
"API-MS-Win-Core-LocalRegistry-L1-1-0.dll",
"ole32.dll",
"USER32.dll",
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"WININET.DLL",
"ADVAPI32.dll",
"OLEAUT32",
"OLEAUT32.dll",
"profapi.dll",
"SHELL32.dll",
"sfc",
"comctl32.dll",
"MPR",
"DEVRTL.dll",
"SHELL32.DLL",
"SETUPAPI.dll",
"WS2_32.dll"
],
"file_opened": [
"C:\\Windows\\system.ini",
"C:\\Windows\\AppPatch\\sysmain.sdb",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls",
"C:\\Windows\\System32\\",
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\Caches\\{AFBF9F1A-8EE8-4C77-AF34-C647E37CA0D9}.1.ver0x0000000000000004.db",
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\Caches\\cversions.1.db",
"C:\\Users\\cuck\\Desktop\\desktop.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe",
"C:\\Windows\\System32\\ExplorerFrame.dll",
"C:\\Windows\\winsxs\\FileMaps\\program_files_common_files_microsoft_shared_ink_3c86e3db0b3b254c.cdf-ms",
"C:\\Windows\\System32\\explorerframe.dll"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\NonEnum",
"HKEY_CURRENT_USER\\Software\\Classes\\Local Settings\\Software\\Microsoft\\Windows\\Shell\\MuiCache ",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Security Center",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\KnownFolderSettings",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\Shell\\Associations\\UrlAssociations\\Drive",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\FolderDescriptions",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_CLASSES_ROOT\\Drive",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Shell Extensions\\Blocked",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\(Default)",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Setup",
"HKEY_CLASSES_ROOT\\Drive\\shellex\\FolderExtensions\\{fbeb8a05-beee-4442-804e-409d6c4515e9}",
"HKEY_CURRENT_USER\\Software\\Arxv",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\shell\\open",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_CLASSES_ROOT\\Folder",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\crypt32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\shell\\open",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\NonEnum",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\policies\\system",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile",
"HKEY_CLASSES_ROOT\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Security Center\\Svc",
"HKEY_LOCAL_MACHINE\\System\\Setup",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_CLASSES_ROOT\\Drive\\shellex\\FolderExtensions",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\(Default)",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Control\\LSA\\AccessProviders",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}",
"HKEY_CURRENT_USER\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\SessionInfo\\1\\KnownFolders",
"HKEY_LOCAL_MACHINE\\system\\CurrentControlSet\\control\\NetworkProvider\\HwOrder",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open\\command",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PropertyBag",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Shell Extensions\\Cached",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PropertyBag",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Run",
"HKEY_CLASSES_ROOT\\SystemFileAssociations\\Drive.Fixed",
"HKEY_LOCAL_MACHINE\\software\\microsoft\\windows\\currentversion\\setup\\PnpLockdownFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\PropertyBag",
"HKEY_CLASSES_ROOT\\CLSID\\{11DBB47C-A525-400B-9E80-A54615A090C0}\\SupportedProtocols",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\Shell\\RegisteredApplications\\UrlAssociations\\Drive\\OpenWithProgids",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\LDAP",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile\\AuthorizedApplications\\List",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\OLE\\Tracing",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\ShellCompatibility\\Applications\\de14f613fc54eb167248c47264de132c8dbecaef94b42cba4ee61623f5a424f7.bin",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\CurVer",
"HKEY_CURRENT_USER\\Software\\Arxv\\-2022283959",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Shell Extensions\\Blocked",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\SessionInfo\\1",
"HKEY_CLASSES_ROOT\\CLSID\\{11DBB47C-A525-400B-9E80-A54615A090C0}\\InProcServer32",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\ShellNoRoam\\MUICache"
],
"command_line": [
"C:\\"
],
"file_written": [
"C:\\Windows\\system.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe",
"C:\\Windows\\System32\\explorerframe.dll"
],
"mutex": [
"svchost.exeM_316_",
"cmd.exeM_1692_",
"svchost.exeM_1216_",
"svchost.exeM_660_",
"lsass.exeM_476_",
"svchost.exeM_276_",
"explorer.exeM_1788_",
"mobsync.exeM_1636_",
"wmpnetwk.exeM_1856_",
"svchost.exeM_712_",
"winlogon.exeM_424_",
"dwm.exeM_1768_",
"taskhost.exeM_1928_",
"wininit.exeM_376_",
"searchprotocolhost.exeM_304_",
"taskhost.exeM_1724_",
"conhost.exeM_1700_",
"svchost.exeM_1000_",
"lsm.exeM_484_",
"csrss.exeM_328_",
"svchost.exeM_480_",
"smss.exeM_252_",
"explorer.exeM_2672_",
"de14f613fc54eb167248c47264de132c8dbecaef94b42cba4ee61623f5a424fM_2124_",
"spoolsv.exeM_1084_",
"csrss.exeM_384_",
"audiodg.exeM_2560_",
"services.exeM_468_",
"svchost.exeM_880_",
"svchost.exeM_1548_",
"uxJLpe1m",
"searchfilterhost.exeM_2448_",
"svchost.exeM_592_",
"python.exeM_3032_",
"svchost.exeM_804_",
"Ap1mutx7",
"searchprotocolhost.exeM_3004_",
"python.exeM_2168_",
"svchost.exeM_3064_",
"svchost.exeM_1120_",
"searchindexer.exeM_1316_"
],
"file_failed": [
"\\??\\L:",
"\\??\\N:",
"\\??\\U:",
"\\??\\H:",
"\\??\\W:",
"\\??\\J:",
"\\??\\Q:",
"\\??\\D:",
"\\??\\S:",
"\\??\\F:",
"\\??\\M:",
"\\??\\X:",
"\\??\\Z:",
"C:\\Windows\\winsxs\\FileMaps\\users_cuck_appdata_local_temp_c2004f3465698a5a.cdf-ms",
"\\??\\O:",
"\\??\\I:",
"\\??\\T:",
"\\??\\V:",
"\\??\\K:",
"\\??\\E:",
"\\??\\P:",
"\\??\\R:",
"\\??\\G:",
"\\??\\Y:"
],
"guid": [
"{5762f2a7-4658-4c7a-a4ac-bdabfe154e0d}",
"{489e9453-869b-4bcc-a1c7-48b5285fd9d8}",
"{682159d9-c321-47ca-b3f1-30e36b2ec8b9}",
"{9ba05972-f6a8-11cf-a442-00a0c90a8f39}",
"{85cb6900-4d95-11cf-960c-0080c7f4ee85}",
"{7f9185b0-cb92-43c5-80a9-92277a4f7b54}",
"{11dbb47c-a525-400b-9e80-a54615a090c0}",
"{1f486a52-3cb1-48fd-8f50-b8dc300d9f9d}"
],
"file_read": [
"C:\\Windows\\winsxs\\FileMaps\\program_files_common_files_microsoft_shared_ink_3c86e3db0b3b254c.cdf-ms",
"C:\\Windows\\system.ini",
"C:\\Users\\cuck\\Desktop\\desktop.ini",
"C:\\Windows\\System32\\ExplorerFrame.dll"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Icon",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseHostnameAsAlias",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoSetFolders",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\WantsFORDISPLAY",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\SourcePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open\\ExplorerHost",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\RelativePath",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\RestrictedAttributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseOldHostResolutionOrder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\DisableImprovedZoneCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoInternetIcon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\WantsUniversalDelegate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Security",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\QueryForOverlay",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\MapNetDriveVerbs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\QueryForInfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\NoFileFolderJunction",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\NonEnum\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\WantsParseDisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open\\LocalServerOnly",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DebugHeapFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoDriveTypeAutoRun",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\WantsAliasedNotifications",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\UseDropHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoCommonGroups",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\PinToNameSpaceTree",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\FolderTypeID",
"HKEY_CURRENT_USER\\Software\\Arxv\\c3_0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\LdapClientIntegrity",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\WantsFORPARSING",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\PublishExpandedPath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open\\command\\DelegateExecute",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\PnpLockdownFiles\\%SystemDrive%\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\HideFolderVerbs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Description",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\Desktop",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\StreamResource",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoDriveAutoRun",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Security",
"HKEY_CURRENT_USER\\Software\\Arxv\\c2_0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\HideInWebView",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\InitFolderHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Folder\\shell\\open\\LaunchExplorerFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\LocalRedirectOnly",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoPropertiesRecycleBin",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\CallForAttributes",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\AccessProviders\\MartaExtension",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoPropertiesMyComputer",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorSystemHeapIsPrivate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Security",
"HKEY_CURRENT_USER\\Software\\Arxv\\c1_0",
"HKEY_CURRENT_USER\\Software\\Arxv\\c1_1",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\RelativePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoDrives",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\ParsingName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Security_HKLM_only",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\DevicePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\PageAllocatorUseSystemHeap",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Attributes",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Stream",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\LocalizedName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Icon",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\PreCreate",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Shell Extensions\\Cached\\{11DBB47C-A525-400B-9E80-A54615A090C0} {7F9185B0-CB92-43C5-80A9-92277A4F7B54} 0xFFFF",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\shellex\\FolderExtensions\\{fbeb8a05-beee-4442-804e-409d6c4515e9}\\DriveMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\HasNavigationEnum",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Description",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\FolderTypeID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\Category",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\InfoTip",
"HKEY_CURRENT_USER\\Software\\Arxv\\c4_0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\\ShellFolder\\HideOnDesktopPerUser",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\StreamResourceType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{11DBB47C-A525-400B-9E80-A54615A090C0}\\InProcServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\LocalRedirectOnly",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\AppData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\NoControlPanel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Stream",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\PreCreate",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\InfoTip",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{3EB685DB-65F9-4CF6-A03A-E3EF65729F3D}\\ParentFolder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Roamable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{1B3EA5DC-B587-4786-B4EF-BD1DC332AEAE}\\Category",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{5E6C858F-0E22-4760-9AFE-EA3317B67173}\\Attributes",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Shell Folders\\Cache",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\explorer\\FolderDescriptions\\{B4BFCC3A-DB2C-424C-B029-7FE99A87C641}\\ParentFolder"
],
"directory_enumerated": [
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\main\\*",
"F:\\*",
"Y:\\*",
"T:\\*",
"C:\\Windows\\System32\\*.*",
"R:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\hu-HU\\*",
"K:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\*",
"M:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\en-US\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\lv-LV\\*",
"I:\\*",
"D:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\he-IL\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\et-EE\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\keypad\\*",
"C:\\Windows\\System32",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\de-DE\\*",
"P:\\*",
"N:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\web\\*",
"V:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\auxpad\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\oskpred\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\HWRCUSTOMIZATION\\*",
"H:\\*",
"C:\\PerfLogs\\Admin\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\symbols\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\hr-HR\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\lt-LT\\*",
"W:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\fr-FR\\*",
"S:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\OSKNUMPAD\\*",
"U:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\it-IT\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\es-ES\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\ko-KR\\*",
"G:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\ar-SA\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\numbers\\*",
"C:\\*",
"Q:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\fi-FI\\*",
"O:\\*",
"C:\\CUCKOO-AGENT\\*",
"E:\\*",
"C:\\PROGRAM FILES\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\ja-JP\\*",
"Z:\\*",
"X:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\el-GR\\*",
"C:\\PerfLogs\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\cs-CZ\\*",
"C:\\DOCUMENTS AND SETTINGS\\*",
"C:\\Windows",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\bg-BG\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\da-DK\\*",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\*",
"L:\\*",
"C:\\PROGRAM FILES\\COMMON FILES\\MICROSOFT SHARED\\ink\\FSDEFINITIONS\\oskmenu\\*",
"J:\\*"
],
"directory_created": [
"C:\\Users\\cuck\\AppData\\Local\\Microsoft\\Windows\\Caches"
]
},
"first_seen": 1567839185.6875,
"ppid": 2504
},
{
"process_path": "C:\\Windows\\explorer.exe",
"process_name": "explorer.exe",
"pid": 2672,
"summary": {
"directory_created": [
"C:\\Users\\cuck",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Windows\\Themes\\",
"C:\\Users\\cuck\\AppData\\Roaming"
],
"dll_loaded": [
"API-MS-WIN-Service-Management-L1-1-0.dll",
"VERSION.dll",
"API-MS-WIN-Service-winsvc-L1-1-0.dll",
"POWRPROF.DLL",
"ADVAPI32.dll",
"ole32.dll",
"C:\\Windows\\system32\\FXSRESM.DLL",
"slc.dll",
"fxsst.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\FXSAPIDebugLogFile.txt",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Windows\\Themes\\slideshow.ini"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Control Panel\\Personalization\\Desktop Slideshow",
"HKEY_CURRENT_USER\\AppEvents\\EventLabels\\FaxSent",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fax\\Client\\ServiceStartup"
],
"file_exists": [
"C:\\Users\\cuck",
"C:\\Users\\cuck\\AppData\\Roaming"
],
"guid": [
"{ba126ad1-2166-11d1-b1d0-00805fc1270e}",
"{a47979d2-c419-11d9-a5b4-001185ad2b89}",
"{b196b284-bab4-101a-b69c-00aa00341d07}",
"{75847177-f077-4171-bd2c-a6bb2164fbd0}",
"{b57046bc-32e5-428a-9887-19f712b907bf}"
],
"regkey_read": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\ListviewShadow",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\SortOrderIndex",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\ListviewAlphaSelect",
"HKEY_CURRENT_USER\\Control Panel\\Personalization\\Desktop Slideshow\\AnimationDuration",
"HKEY_CURRENT_USER\\Control Panel\\Personalization\\Desktop Slideshow\\Interval",
"HKEY_CURRENT_USER\\Control Panel\\Personalization\\Desktop Slideshow\\Flags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{21EC2020-3AEA-1069-A2DD-08002B30309D}\\SortOrderIndex",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\EnableBalloonTips",
"HKEY_CURRENT_USER\\Control Panel\\Personalization\\Desktop Slideshow\\Shuffle",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Interface\\{2ABC0864-9677-42E5-882A-D415C556C284}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\SmoothScroll"
]
},
"first_seen": 1567839197.8746,
"ppid": 424
},
{
"process_path": "C:\\Windows\\System32\\conhost.exe",
"process_name": "conhost.exe",
"pid": 1700,
"summary": {},
"first_seen": 1567839186.8902,
"ppid": 384
},
{
"process_path": "C:\\Windows\\explorer.exe",
"process_name": "explorer.exe",
"pid": 1788,
"summary": {
"regkey_written": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Action Center\\Checks\\{01979c6a-42fa-414c-b8aa-eee2c8202018}.check.100\\CheckSetting",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\LanguageList"
],
"file_failed": [
"C:\\desktop.ini"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Action Center\\Checks\\{01979c6a-42fa-414c-b8aa-eee2c8202018}.check.100"
],
"file_exists": [
"C:\\"
],
"file_opened": [
"C:\\Users\\desktop.ini",
"C:\\Program Files (x86)\\desktop.ini",
"C:\\Program Files\\desktop.ini",
"C:\\"
],
"guid": [
"{00000320-0000-0000-c000-000000000046}",
"{00000323-0000-0000-c000-000000000046}",
"{a47979d2-c419-11d9-a5b4-001185ad2b89}",
"{00000146-0000-0000-c000-000000000046}",
"{7007acc7-3202-11d1-aad2-00805fc1270e}",
"{d0074ffd-570f-4a9b-8d69-199fdba5723b}",
"{faedcf69-31fe-11d1-aad2-00805fc1270e}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{ba126ae5-2166-11d1-b1d0-00805fc1270e}",
"{000214e6-0000-0000-c000-000000000046}"
],
"file_read": [
"C:\\Users\\desktop.ini",
"C:\\Program Files (x86)\\desktop.ini",
"C:\\Program Files\\desktop.ini"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{2227A280-3AEA-1069-A2DE-08002B30309D}\\LocalizedString",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{2227A280-3AEA-1069-A2DE-08002B30309D}\\System.ItemNameDisplay",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\SortOrderIndex",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@C:\\Windows\\system32\\prnfldr.dll,-8036",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\{B725F130-47EF-101A-A5F1-02608C9EEBAC} 10",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@C:\\Windows\\system32\\netshell.dll,-1200",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\System.ItemNameDisplay",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{2227A280-3AEA-1069-A2DE-08002B30309D}\\{B725F130-47EF-101A-A5F1-02608C9EEBAC} 10",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\InProcServer32\\LoadWithoutCOM",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{21EC2020-3AEA-1069-A2DD-08002B30309D}\\SortOrderIndex",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\InProcServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\MUI\\StringCacheSettings\\StringCacheGeneration",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Drive\\shellex\\FolderExtensions\\{fbeb8a05-beee-4442-804e-409d6c4515e9}\\DriveMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{7007ACC7-3202-11D1-AAD2-00805FC1270E}\\LocalizedString",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\_LabelFromReg"
]
},
"first_seen": 1567839186.4688,
"ppid": 1740
}
]Signatures
[
{
"markcount": 1,
"families": [],
"description": "Queries for the computername",
"severity": 1,
"marks": [
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameA",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1567839185.8755,
"tid": 2968,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 286
}
],
"references": [],
"name": "antivm_queries_computername"
},
{
"markcount": 3,
"families": [],
"description": "One or more processes crashed",
"severity": 1,
"marks": [
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "d\ne\n1\n4\nf\n6\n1\n3\nf\nc\n5\n4\ne\nb\n1\n6\n7\n2\n4\n8\nc\n4\n7\n2\n6\n4\nd\ne\n1\n3\n2\nc\n8\nd\nb\ne\nc\na\ne\nf\n9\n4\nb\n4\n2\nc\nb\na\n4\ne\ne\n6\n1\n6\n2\n3\nf\n5\na\n4\n2\n4\nf\n7\n+\n0\nx\n2\nd\nc\nd\n \n@\n \n0\nx\n4\n0\n2\nd\nc\nd",
"registers": {
"esp": 30998320,
"edi": 2178678801,
"eax": 2178678801,
"ebp": 30998360,
"edx": 2178678802,
"ebx": 31768972,
"esi": 4205006,
"ecx": 2008823930
},
"exception": {
"instruction_r": "8a 08 40 84 c9 75 f9 2b c2 c7 45 fc fe ff ff ff",
"symbol": "lstrlen+0x1a lstrcmpW-0x3f kernelbase+0xa34a",
"instruction": "mov cl, byte ptr [eax]",
"module": "KERNELBASE.dll",
"exception_code": "0xc0000005",
"offset": 41802,
"address": "0x75dba34a"
}
},
"time": 1567839185.8595,
"tid": 2968,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 72
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "0\nx\n5\n1\n9\n1\n9\n0\n4\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0\n\n\n0\nx\n3\n0",
"registers": {
"r14": 103280040,
"r9": 0,
"rcx": 48,
"rsi": 103280040,
"r10": 0,
"rbx": 98187056,
"rdi": 69354496,
"r11": 156302544,
"r8": 2007859596,
"rdx": 8796092387920,
"rbp": 156299888,
"r15": 262145,
"r12": 262144,
"rsp": 156299768,
"rax": 85530880,
"r13": 156301057
},
"exception": {
"instruction_r": "83 3d 8d d1 02 00 00 68 53 12 69 fb c7 44 24 04",
"instruction": "cmp dword ptr [rip + 0x2d18d], 0",
"exception_code": "0xc0000005",
"symbol": "",
"address": "0x5191904"
}
},
"time": 1567839187.3907,
"tid": 2104,
"flags": {}
},
"pid": 1788,
"type": "call",
"cid": 1007
},
{
"call": {
"category": "__notification__",
"status": 1,
"stacktrace": [],
"raw": [
"stacktrace"
],
"api": "__exception__",
"return_value": 0,
"arguments": {
"stacktrace": "R\na\ni\ns\ne\nE\nx\nc\ne\np\nt\ni\no\nn\n+\n0\nx\n3\nd\n \nF\nr\ne\ne\nE\nn\nv\ni\nr\no\nn\nm\ne\nn\nt\nS\nt\nr\ni\nn\ng\ns\nW\n-\n0\nx\n3\n7\n3\n \nk\ne\nr\nn\ne\nl\nb\na\ns\ne\n+\n0\nx\na\n4\n9\nd\n \n@\n \n0\nx\n7\nf\ne\nf\nd\na\n1\na\n4\n9\nd\n\n\nR\np\nc\nR\na\ni\ns\ne\nE\nx\nc\ne\np\nt\ni\no\nn\n+\n0\nx\n5\n3\n \nR\np\nc\nE\nx\nc\ne\np\nt\ni\no\nn\nF\ni\nl\nt\ne\nr\n-\n0\nx\n2\nb\nd\n \nr\np\nc\nr\nt\n4\n+\n0\nx\n1\n7\n3\nc\n3\n \n@\n \n0\nx\n7\nf\ne\nf\ne\ne\nf\n7\n3\nc\n3\n\n\nC\no\nG\ne\nt\nI\nn\ns\nt\na\nn\nc\ne\nF\nr\no\nm\nF\ni\nl\ne\n+\n0\nx\na\n7\n0\na\n \nH\nA\nC\nC\nE\nL\n_\nU\ns\ne\nr\nF\nr\ne\ne\n-\n0\nx\n1\n6\nc\n6\n \no\nl\ne\n3\n2\n+\n0\nx\n1\n7\n6\n2\nb\na\n \n@\n \n0\nx\n7\nf\ne\nf\nf\nb\n6\n6\n2\nb\na\n\n\nN\nd\nr\n6\n4\nA\ns\ny\nn\nc\nS\ne\nr\nv\ne\nr\nC\na\nl\nl\nA\nl\nl\n+\n0\nx\n1\n4\nc\n9\n \nN\nd\nr\n6\n4\nA\ns\ny\nn\nc\nC\nl\ni\ne\nn\nt\nC\na\nl\nl\n-\n0\nx\n5\n1\n7\n \nr\np\nc\nr\nt\n4\n+\n0\nx\nd\nb\n9\n4\n9\n \n@\n \n0\nx\n7\nf\ne\nf\ne\nf\nb\nb\n9\n4\n9\n\n\nC\no\nG\ne\nt\nI\nn\ns\nt\na\nn\nc\ne\nF\nr\no\nm\nF\ni\nl\ne\n+\n0\nx\n6\n6\n2\n0\n \nH\nA\nC\nC\nE\nL\n_\nU\ns\ne\nr\nF\nr\ne\ne\n-\n0\nx\n5\n7\nb\n0\n \no\nl\ne\n3\n2\n+\n0\nx\n1\n7\n2\n1\nd\n0\n \n@\n \n0\nx\n7\nf\ne\nf\nf\nb\n6\n2\n1\nd\n0\n\n\nD\nc\no\nm\nC\nh\na\nn\nn\ne\nl\nS\ne\nt\nH\nR\ne\ns\nu\nl\nt\n+\n0\nx\n3\n0\n6\n6\n \nO\nb\nj\ne\nc\nt\nS\nt\nu\nb\nl\ne\ns\ns\nC\nl\ni\ne\nn\nt\n3\n-\n0\nx\n7\ne\ne\n \no\nl\ne\n3\n2\n+\n0\nx\n2\nd\n8\na\n2\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n1\nd\n8\na\n2\n\n\nO\nb\nj\ne\nc\nt\nS\nt\nu\nb\nl\ne\ns\ns\nC\nl\ni\ne\nn\nt\n5\n+\n0\nx\n1\n8\n3\n \nI\ns\nV\na\nl\ni\nd\nI\nn\nt\ne\nr\nf\na\nc\ne\n-\n0\nx\n1\n0\n5\nd\n \no\nl\ne\n3\n2\n+\n0\nx\n3\n1\nb\nb\n3\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n2\n1\nb\nb\n3\n\n\nO\nb\nj\ne\nc\nt\nS\nt\nu\nb\nl\ne\ns\ns\nC\nl\ni\ne\nn\nt\n5\n+\n0\nx\nf\n2\n \nI\ns\nV\na\nl\ni\nd\nI\nn\nt\ne\nr\nf\na\nc\ne\n-\n0\nx\n1\n0\ne\ne\n \no\nl\ne\n3\n2\n+\n0\nx\n3\n1\nb\n2\n2\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n2\n1\nb\n2\n2\n\n\nC\no\nM\na\nr\ns\nh\na\nl\nI\nn\nt\ne\nr\nf\na\nc\ne\n+\n0\nx\n2\n6\n3\nf\n \nO\nb\nj\ne\nc\nt\nS\nt\nu\nb\nl\ne\ns\ns\nC\nl\ni\ne\nn\nt\n5\n-\n0\nx\n2\n4\n5\n \no\nl\ne\n3\n2\n+\n0\nx\n3\n1\n7\ne\nb\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n2\n1\n7\ne\nb\n\n\nC\no\nM\na\nr\ns\nh\na\nl\nI\nn\nt\ne\nr\nf\na\nc\ne\n+\n0\nx\n2\n2\n6\nb\n \nO\nb\nj\ne\nc\nt\nS\nt\nu\nb\nl\ne\ns\ns\nC\nl\ni\ne\nn\nt\n5\n-\n0\nx\n6\n1\n9\n \no\nl\ne\n3\n2\n+\n0\nx\n3\n1\n4\n1\n7\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n2\n1\n4\n1\n7\n\n\nC\no\nS\ne\nt\nS\nt\na\nt\ne\n+\n0\nx\n4\n5\na\n \nD\nc\no\nm\nC\nh\na\nn\nn\ne\nl\nS\ne\nt\nH\nR\ne\ns\nu\nl\nt\n-\n0\nx\n1\n3\n4\n2\n \no\nl\ne\n3\n2\n+\n0\nx\n2\n9\n4\nf\na\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n1\n9\n4\nf\na\n\n\nC\no\nS\ne\nt\nS\nt\na\nt\ne\n+\n0\nx\n3\n8\n8\n \nD\nc\no\nm\nC\nh\na\nn\nn\ne\nl\nS\ne\nt\nH\nR\ne\ns\nu\nl\nt\n-\n0\nx\n1\n4\n1\n4\n \no\nl\ne\n3\n2\n+\n0\nx\n2\n9\n4\n2\n8\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n1\n9\n4\n2\n8\n\n\nC\no\nS\ne\nt\nS\nt\na\nt\ne\n+\n0\nx\na\na\n9\n \nD\nc\no\nm\nC\nh\na\nn\nn\ne\nl\nS\ne\nt\nH\nR\ne\ns\nu\nl\nt\n-\n0\nx\nc\nf\n3\n \no\nl\ne\n3\n2\n+\n0\nx\n2\n9\nb\n4\n9\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n1\n9\nb\n4\n9\n\n\nC\no\nR\ne\ng\ni\ns\nt\ne\nr\nM\ne\ns\ns\na\ng\ne\nF\ni\nl\nt\ne\nr\n+\n0\nx\n1\n5\n3\nb\n \nC\no\nU\nn\ni\nn\ni\nt\ni\na\nl\ni\nz\ne\n-\n0\nx\n3\n3\n4\n1\n \no\nl\ne\n3\n2\n+\n0\nx\n1\nd\nf\nd\n3\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n0\nd\nf\nd\n3\n\n\nC\no\nR\ne\ng\ni\ns\nt\ne\nr\nM\ne\ns\ns\na\ng\ne\nF\ni\nl\nt\ne\nr\n+\n0\nx\n1\n1\nc\n0\n \nC\no\nU\nn\ni\nn\ni\nt\ni\na\nl\ni\nz\ne\n-\n0\nx\n3\n6\nb\nc\n \no\nl\ne\n3\n2\n+\n0\nx\n1\nd\nc\n5\n8\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n0\nd\nc\n5\n8\n\n\nC\no\nR\ne\ng\ni\ns\nt\ne\nr\nM\ne\ns\ns\na\ng\ne\nF\ni\nl\nt\ne\nr\n+\n0\nx\nb\n9\n7\n \nC\no\nU\nn\ni\nn\ni\nt\ni\na\nl\ni\nz\ne\n-\n0\nx\n3\nc\ne\n5\n \no\nl\ne\n3\n2\n+\n0\nx\n1\nd\n6\n2\nf\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n0\nd\n6\n2\nf\n\n\nC\no\nR\ne\ng\ni\ns\nt\ne\nr\nM\ne\ns\ns\na\ng\ne\nF\ni\nl\nt\ne\nr\n+\n0\nx\n1\n3\nf\ne\n \nC\no\nU\nn\ni\nn\ni\nt\ni\na\nl\ni\nz\ne\n-\n0\nx\n3\n4\n7\ne\n \no\nl\ne\n3\n2\n+\n0\nx\n1\nd\ne\n9\n6\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n0\nd\ne\n9\n6\n\n\nO\nb\nj\ne\nc\nt\nS\nt\nu\nb\nl\ne\ns\ns\nC\nl\ni\ne\nn\nt\n3\n2\n+\n0\nx\n7\n3\nc\n2\n \nC\no\nD\ni\ns\nc\no\nn\nn\ne\nc\nt\nC\no\nn\nt\ne\nx\nt\n-\n0\nx\n9\nc\nb\n6\n \no\nl\ne\n3\n2\n+\n0\nx\n4\na\ne\nc\n2\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n3\na\ne\nc\n2\n\n\nC\no\nU\nn\ni\nn\ni\nt\ni\na\nl\ni\nz\ne\n+\n0\nx\n1\n0\n1\n0\n \nC\no\nI\nn\ni\nt\ni\na\nl\ni\nz\ne\nE\nx\n-\n0\nx\n7\n0\nc\n \no\nl\ne\n3\n2\n+\n0\nx\n2\n2\n3\n2\n4\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n1\n2\n3\n2\n4\n\n\nC\no\nR\ne\ng\ni\ns\nt\ne\nr\nM\ne\ns\ns\na\ng\ne\nF\ni\nl\nt\ne\nr\n+\n0\nx\n3\nc\n3\n0\n \nC\no\nU\nn\ni\nn\ni\nt\ni\na\nl\ni\nz\ne\n-\n0\nx\nc\n4\nc\n \no\nl\ne\n3\n2\n+\n0\nx\n2\n0\n6\nc\n8\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n1\n0\n6\nc\n8\n\n\nC\no\nR\ne\ng\ni\ns\nt\ne\nr\nM\ne\ns\ns\na\ng\ne\nF\ni\nl\nt\ne\nr\n+\n0\nx\n3\nc\n0\n1\n \nC\no\nU\nn\ni\nn\ni\nt\ni\na\nl\ni\nz\ne\n-\n0\nx\nc\n7\nb\n \no\nl\ne\n3\n2\n+\n0\nx\n2\n0\n6\n9\n9\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n1\n0\n6\n9\n9\n\n\nC\no\nD\ni\ns\na\nb\nl\ne\nC\na\nl\nl\nC\na\nn\nc\ne\nl\nl\na\nt\ni\no\nn\n+\n0\nx\n3\nf\nc\n \nO\nb\nj\ne\nc\nt\nS\nt\nu\nb\nl\ne\ns\ns\nC\nl\ni\ne\nn\nt\n2\n4\n-\n0\nx\ne\n4\n \no\nl\ne\n3\n2\n+\n0\nx\ne\n7\na\nc\n \n@\n \n0\nx\n7\nf\ne\nf\nf\n9\nf\ne\n7\na\nc\n\n\nC\no\nU\nn\ni\nn\ni\nt\ni\na\nl\ni\nz\ne\n+\n0\nx\na\n6\n \nC\no\nI\nn\ni\nt\ni\na\nl\ni\nz\ne\nE\nx\n-\n0\nx\n1\n6\n7\n6\n \no\nl\ne\n3\n2\n+\n0\nx\n2\n1\n3\nb\na\n \n@\n \n0\nx\n7\nf\ne\nf\nf\na\n1\n1\n3\nb\na\n\n\nN\ne\nw\n_\no\nl\ne\n3\n2\n_\nC\no\nU\nn\ni\nn\ni\nt\ni\na\nl\ni\nz\ne\n+\n0\nx\n5\n7\n \nN\ne\nw\n_\no\nl\ne\n3\n2\n_\nO\nl\ne\nC\no\nn\nv\ne\nr\nt\nO\nL\nE\nS\nT\nR\nE\nA\nM\nT\no\nI\nS\nt\no\nr\na\ng\ne\n-\n0\nx\n5\n3\n \n@\n \n0\nx\n6\n5\na\na\n7\n6\n1\ne\n\n\nm\no\nb\ns\ny\nn\nc\n+\n0\nx\n6\n8\n4\n0\n \n@\n \n0\nx\nf\nf\nc\na\n6\n8\n4\n0\n\n\nm\no\nb\ns\ny\nn\nc\n+\n0\nx\n7\n0\na\ne\n \n@\n \n0\nx\nf\nf\nc\na\n7\n0\na\ne\n\n\nB\na\ns\ne\nT\nh\nr\ne\na\nd\nI\nn\ni\nt\nT\nh\nu\nn\nk\n+\n0\nx\nd\n \nC\nr\ne\na\nt\ne\nT\nh\nr\ne\na\nd\n-\n0\nx\n5\n3\n \nk\ne\nr\nn\ne\nl\n3\n2\n+\n0\nx\n1\n6\n5\n2\nd\n \n@\n \n0\nx\n7\n7\n7\na\n6\n5\n2\nd\n\n\nR\nt\nl\nU\ns\ne\nr\nT\nh\nr\ne\na\nd\nS\nt\na\nr\nt\n+\n0\nx\n2\n1\n \ns\nt\nr\nc\nh\nr\n-\n0\nx\n3\nd\nf\n \nn\nt\nd\nl\nl\n+\n0\nx\n2\nc\n5\n2\n1\n \n@\n \n0\nx\n7\n7\n9\nd\nc\n5\n2\n1",
"registers": {
"r14": 0,
"r9": 0,
"rcx": 2547520,
"rsi": 0,
"r10": 0,
"rbx": 0,
"rdi": 0,
"r11": 2549280,
"r8": 0,
"rdx": 1,
"rbp": 0,
"r15": 0,
"r12": 0,
"rsp": 2554336,
"rax": 2011641923,
"r13": 0
},
"exception": {
"instruction_r": "48 81 c4 c8 00 00 00 c3 48 85 f6 74 08 83 3b 00",
"symbol": "RaiseException+0x3d FreeEnvironmentStringsW-0x373 kernelbase+0xa49d",
"instruction": "add rsp, 0xc8",
"module": "KERNELBASE.dll",
"exception_code": "0x80010012",
"offset": 42141,
"address": "0x7fefda1a49d"
}
},
"time": 1567839187.969,
"tid": 916,
"flags": {}
},
"pid": 1636,
"type": "call",
"cid": 19
}
],
"references": [],
"name": "raises_exception"
},
{
"markcount": 0,
"families": [],
"description": "One or more potentially interesting buffers were extracted, these generally contain injected code, configuration data, etc.",
"severity": 2,
"marks": [],
"references": [],
"name": "dumped_buffer"
},
{
"markcount": 2,
"families": [],
"description": "Allocates read-write-execute memory (usually to unpack itself)",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2124,
"region_size": 17358848,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffff",
"allocation_type": 12288,
"base_address": "0x01dc0000"
},
"time": 1567839185.8445,
"tid": 2968,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 36
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2124,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffff",
"base_address": "0x01dc0000"
},
"time": 1567839185.8595,
"tid": 2968,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2124,
"type": "call",
"cid": 192
}
],
"references": [],
"name": "allocates_rwx"
},
{
"markcount": 0,
"families": [],
"description": "Checks whether any human activity is being performed by constantly checking whether the foreground window changed",
"severity": 2,
"marks": [],
"references": [
"https:\/\/www.virusbtn.com\/virusbulletin\/archive\/2015\/09\/vb201509-custom-packer.dkb"
],
"name": "antisandbox_foregroundwindows"
},
{
"markcount": 1,
"families": [],
"description": "A process attempted to delay the analysis task.",
"severity": 2,
"marks": [
{
"type": "generic",
"description": "de14f613fc54eb167248c47264de132c8dbecaef94b42cba4ee61623f5a424f7.bin tried to sleep 840 seconds, actually delayed analysis time by 840 seconds"
}
],
"references": [],
"name": "antisandbox_sleep"
},
{
"markcount": 1,
"families": [],
"description": "Drops an executable to the user AppData folder",
"severity": 2,
"marks": [
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Temp\\avpto.exe",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "exe_appdata"
},
{
"markcount": 3,
"families": [],
"description": "Searches running processes potentially to identify processes for sandbox evasion, code injection or memory dumping",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "Process32NextW",
"return_value": 1,
"arguments": {
"process_name": "SearchFilterHost.exe",
"snapshot_handle": "0x000001f4",
"process_identifier": 2448
},
"time": 1567839187.4845,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1289
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "Process32NextW",
"return_value": 1,
"arguments": {
"process_name": "svchost.exe",
"snapshot_handle": "0x000002e8",
"process_identifier": 316
},
"time": 1567839197.7815,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1595
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "Process32NextW",
"return_value": 1,
"arguments": {
"process_name": "SearchProtocolHost.exe",
"snapshot_handle": "0x000002e8",
"process_identifier": 304
},
"time": 1567839198.0005,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1612
}
],
"references": [],
"name": "injection_process_search"
},
{
"markcount": 2,
"families": [],
"description": "The binary likely contains encrypted or compressed data indicative of a packer",
"severity": 2,
"marks": [
{
"entropy": 7.9872830822919,
"section": {
"size_of_data": "0x00013200",
"virtual_address": "0x00001000",
"entropy": 7.9872830822919,
"name": ".text",
"virtual_size": "0x00014000"
},
"type": "generic",
"description": "A section with a high entropy has been found"
},
{
"entropy": 1,
"type": "generic",
"description": "Overall entropy of this PE file is high"
}
],
"references": [
"http:\/\/www.forensickb.com\/2013\/03\/file-entropy-explained.html",
"http:\/\/virii.es\/U\/Using%20Entropy%20Analysis%20to%20Find%20Encrypted%20and%20Packed%20Malware.pdf"
],
"name": "packer_entropy"
},
{
"markcount": 12,
"families": [],
"description": "Checks for the Locally Unique Identifier on the system for a suspicious privilege",
"severity": 2,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1567839187.2505,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1252
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1567839197.7815,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1571
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1567839208.6415,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1907
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2172
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2399
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1567839239.4845,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2626
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1567839249.7505,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2867
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1567839260.0165,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 3089
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1567839270.2975,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 3301
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1567839280.5475,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 3512
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1567839290.8285,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 3739
},
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1567839301.0945,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 3936
}
],
"references": [],
"name": "privilege_luid_check"
},
{
"markcount": 93,
"families": [],
"description": "Allocates execute permission to another process indicative of possible code injection",
"severity": 3,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001fc",
"allocation_type": 12288,
"base_address": "0x002e0000"
},
"time": 1567839185.9845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1079
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001f8",
"allocation_type": 12288,
"base_address": "0x00130000"
},
"time": 1567839186.1875,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1167
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1788,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001fc",
"allocation_type": 12288,
"base_address": "0x03ed0000"
},
"time": 1567839186.3755,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1177
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001fc",
"allocation_type": 12288,
"base_address": "0x00140000"
},
"time": 1567839186.5945,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1195
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001f8",
"allocation_type": 12288,
"base_address": "0x01b20000"
},
"time": 1567839186.7975,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1205
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001fc",
"allocation_type": 12288,
"base_address": "0x01d20000"
},
"time": 1567839187.2505,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1236
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1636,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001fc",
"allocation_type": 12288,
"base_address": "0x002d0000"
},
"time": 1567839187.2505,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1259
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 3032,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000184",
"allocation_type": 12288,
"base_address": "0x00440000"
},
"time": 1567839187.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1270
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2124,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000184",
"allocation_type": 12288,
"base_address": "0x03210000"
},
"time": 1567839187.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1300
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2124,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000184",
"allocation_type": 12288,
"base_address": "0x03260000"
},
"time": 1567839187.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1303
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f0",
"allocation_type": 12288,
"base_address": "0x024d0000"
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1514
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x020d0000"
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1523
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f0",
"allocation_type": 12288,
"base_address": "0x026c0000"
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1535
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x01c90000"
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1544
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f0",
"allocation_type": 12288,
"base_address": "0x01d50000"
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1559
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 3032,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x00460000"
},
"time": 1567839197.7815,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1578
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2672,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x04570000"
},
"time": 1567839197.7815,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1606
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 304,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f0",
"allocation_type": 12288,
"base_address": "0x00120000"
},
"time": 1567839198.0165,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1616
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000314",
"allocation_type": 12288,
"base_address": "0x02500000"
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1850
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x020e0000"
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1859
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000314",
"allocation_type": 12288,
"base_address": "0x026d0000"
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1871
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x01cb0000"
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1880
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000314",
"allocation_type": 12288,
"base_address": "0x03300000"
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1895
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 3032,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x00470000"
},
"time": 1567839208.6415,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1914
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2672,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000314",
"allocation_type": 12288,
"base_address": "0x04b70000"
},
"time": 1567839208.6415,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1938
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 304,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x01c70000"
},
"time": 1567839208.6415,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1947
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x02510000"
},
"time": 1567839218.8915,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2115
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x020f0000"
},
"time": 1567839218.8915,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2124
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x026e0000"
},
"time": 1567839218.8915,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2136
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x01cc0000"
},
"time": 1567839218.8915,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2145
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x03310000"
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2160
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 3032,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x00480000"
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2179
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2672,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x04b80000"
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2203
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 304,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x01c80000"
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2212
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x02520000"
},
"time": 1567839229.1725,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2342
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x02200000"
},
"time": 1567839229.1725,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2351
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x026f0000"
},
"time": 1567839229.1725,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2363
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x01dc0000"
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2372
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x03320000"
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2387
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 3032,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x00490000"
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2406
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2672,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x03a40000"
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2430
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 304,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x01c90000"
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2439
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000324",
"allocation_type": 12288,
"base_address": "0x02530000"
},
"time": 1567839239.4695,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2569
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000320",
"allocation_type": 12288,
"base_address": "0x02660000"
},
"time": 1567839239.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2578
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000324",
"allocation_type": 12288,
"base_address": "0x02700000"
},
"time": 1567839239.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2590
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000320",
"allocation_type": 12288,
"base_address": "0x01dd0000"
},
"time": 1567839239.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2599
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000324",
"allocation_type": 12288,
"base_address": "0x03330000"
},
"time": 1567839239.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2614
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 3032,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000320",
"allocation_type": 12288,
"base_address": "0x004a0000"
},
"time": 1567839239.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2633
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2672,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000324",
"allocation_type": 12288,
"base_address": "0x03a50000"
},
"time": 1567839239.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2657
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 304,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000320",
"allocation_type": 12288,
"base_address": "0x01cb0000"
},
"time": 1567839239.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2666
}
],
"references": [],
"name": "allocates_execute_remote_process"
},
{
"markcount": 1,
"families": [],
"description": "Installs itself for autorun at Windows startup",
"severity": 3,
"marks": [
{
"category": "file",
"ioc": "C:\\Windows\\system.ini",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "persistence_autorun"
},
{
"markcount": 1,
"families": [],
"description": "Operates on local firewall's policies and settings",
"severity": 3,
"marks": [
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "bypass_firewall"
},
{
"markcount": 101,
"families": [],
"description": "Creates a thread using CreateRemoteThread in a non-child process indicative of process injection",
"severity": 3,
"marks": [
{
"category": "Process injection",
"ioc": "Process 2124 created a remote thread in non-child process 1724",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1724,
"function_address": "0x002e0000",
"flags": 0,
"process_handle": "0x000001fc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839186.1875,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1160
},
{
"category": "Process injection",
"ioc": "Process 2124 created a remote thread in non-child process 1768",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1768,
"function_address": "0x00130000",
"flags": 0,
"process_handle": "0x000001f8",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839186.3755,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1170
},
{
"category": "Process injection",
"ioc": "Process 2124 created a remote thread in non-child process 1788",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1788,
"function_address": "0x03ed0000",
"flags": 0,
"process_handle": "0x000001fc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839186.5945,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1181
},
{
"category": "Process injection",
"ioc": "Process 2124 created a remote thread in non-child process 1692",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1692,
"function_address": "0x00140000",
"flags": 0,
"process_handle": "0x000001fc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839186.7975,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1198
},
{
"category": "Process injection",
"ioc": "Process 2124 created a remote thread in non-child process 1700",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1700,
"function_address": "0x01b20000",
"flags": 0,
"process_handle": "0x000001f8",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839187.2505,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1215
},
{
"category": "Process injection",
"ioc": "Process 2124 created a remote thread in non-child process 2168",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 2168,
"function_address": "0x01d20000",
"flags": 0,
"process_handle": "0x000001fc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839187.2505,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1238
},
{
"category": "Process injection",
"ioc": "Process 2124 created a remote thread in non-child process 1636",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1636,
"function_address": "0x002d0000",
"flags": 0,
"process_handle": "0x000001fc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839187.4845,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1263
},
{
"category": "Process injection",
"ioc": "Process 2124 created a remote thread in non-child process 3032",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 3032,
"function_address": "0x00440000",
"flags": 0,
"process_handle": "0x00000184",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839187.4845,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1272
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1724,
"function_address": "0x024d0000",
"flags": 0,
"process_handle": "0x000002f0",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1516
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1768,
"function_address": "0x020d0000",
"flags": 0,
"process_handle": "0x000002f4",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1525
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1692,
"function_address": "0x026c0000",
"flags": 0,
"process_handle": "0x000002f0",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1537
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1700,
"function_address": "0x01c90000",
"flags": 0,
"process_handle": "0x000002f4",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1546
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 2168,
"function_address": "0x01d50000",
"flags": 0,
"process_handle": "0x000002f0",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839197.7815,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1561
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 3032,
"function_address": "0x00460000",
"flags": 0,
"process_handle": "0x000002f4",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839197.7815,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1580
},
{
"category": "Process injection",
"ioc": "Process 2124 created a remote thread in non-child process 2672",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 2672,
"function_address": "0x04570000",
"flags": 0,
"process_handle": "0x000002f4",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839198.0005,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1609
},
{
"category": "Process injection",
"ioc": "Process 2124 created a remote thread in non-child process 304",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 304,
"function_address": "0x00120000",
"flags": 0,
"process_handle": "0x000002f0",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839198.3755,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1619
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1724,
"function_address": "0x02500000",
"flags": 0,
"process_handle": "0x00000314",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1852
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1768,
"function_address": "0x020e0000",
"flags": 0,
"process_handle": "0x000002f4",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1861
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1692,
"function_address": "0x026d0000",
"flags": 0,
"process_handle": "0x00000314",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1873
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1700,
"function_address": "0x01cb0000",
"flags": 0,
"process_handle": "0x000002f4",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1882
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 2168,
"function_address": "0x03300000",
"flags": 0,
"process_handle": "0x00000314",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839208.6415,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1897
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 3032,
"function_address": "0x00470000",
"flags": 0,
"process_handle": "0x000002f4",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839208.6415,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1916
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 2672,
"function_address": "0x04b70000",
"flags": 0,
"process_handle": "0x00000314",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839208.6415,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1940
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 304,
"function_address": "0x01c70000",
"flags": 0,
"process_handle": "0x000002f4",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839208.6415,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 1949
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1724,
"function_address": "0x02510000",
"flags": 0,
"process_handle": "0x000002ec",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839218.8915,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2117
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1768,
"function_address": "0x020f0000",
"flags": 0,
"process_handle": "0x000001dc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839218.8915,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2126
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1692,
"function_address": "0x026e0000",
"flags": 0,
"process_handle": "0x000002ec",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839218.8915,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2138
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1700,
"function_address": "0x01cc0000",
"flags": 0,
"process_handle": "0x000001dc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2147
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 2168,
"function_address": "0x03310000",
"flags": 0,
"process_handle": "0x000002ec",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2162
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 3032,
"function_address": "0x00480000",
"flags": 0,
"process_handle": "0x000001dc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2181
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 2672,
"function_address": "0x04b80000",
"flags": 0,
"process_handle": "0x000002ec",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2205
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 304,
"function_address": "0x01c80000",
"flags": 0,
"process_handle": "0x000001dc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2214
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1724,
"function_address": "0x02520000",
"flags": 0,
"process_handle": "0x000002ec",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839229.1725,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2344
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1768,
"function_address": "0x02200000",
"flags": 0,
"process_handle": "0x000001dc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839229.1725,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2353
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1692,
"function_address": "0x026f0000",
"flags": 0,
"process_handle": "0x000002ec",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839229.1725,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2365
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 1700,
"function_address": "0x01dc0000",
"flags": 0,
"process_handle": "0x000001dc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2374
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 2168,
"function_address": "0x03320000",
"flags": 0,
"process_handle": "0x000002ec",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2389
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 3032,
"function_address": "0x00490000",
"flags": 0,
"process_handle": "0x000001dc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2408
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 2672,
"function_address": "0x03a40000",
"flags": 0,
"process_handle": "0x000002ec",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2432
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 5,
"nt_status": -1073741790,
"api": "CreateRemoteThread",
"return_value": 0,
"arguments": {
"thread_identifier": 0,
"process_identifier": 304,
"function_address": "0x01c90000",
"flags": 0,
"process_handle": "0x000001dc",
"parameter": "0x00000000",
"stack_size": 0
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {}
},
"pid": 2124,
"type": "call",
"cid": 2441
}
],
"references": [
"www.endgame.com\/blog\/technical-blog\/ten-process-injection-techniques-technical-survey-common-and-trending-process"
],
"name": "injection_createremotethread"
},
{
"markcount": 104,
"families": [],
"description": "Manipulates memory of a non-child process indicative of process injection",
"severity": 3,
"marks": [
{
"category": "Process injection",
"ioc": "Process 2124 manipulating memory of non-child process 1724",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001fc",
"allocation_type": 12288,
"base_address": "0x002e0000"
},
"time": 1567839185.9845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1079
},
{
"category": "Process injection",
"ioc": "Process 2124 manipulating memory of non-child process 1768",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001f8",
"allocation_type": 12288,
"base_address": "0x00130000"
},
"time": 1567839186.1875,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1167
},
{
"category": "Process injection",
"ioc": "Process 2124 manipulating memory of non-child process 1788",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1788,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001fc",
"allocation_type": 12288,
"base_address": "0x03ed0000"
},
"time": 1567839186.3755,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1177
},
{
"category": "Process injection",
"ioc": "Process 2124 manipulating memory of non-child process 1692",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001fc",
"allocation_type": 12288,
"base_address": "0x00140000"
},
"time": 1567839186.5945,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1195
},
{
"category": "Process injection",
"ioc": "Process 2124 manipulating memory of non-child process 1700",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001f8",
"allocation_type": 12288,
"base_address": "0x01b20000"
},
"time": 1567839186.7975,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1205
},
{
"category": "Process injection",
"ioc": "Process 2124 manipulating memory of non-child process 2168",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001fc",
"allocation_type": 12288,
"base_address": "0x01d20000"
},
"time": 1567839187.2505,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1236
},
{
"category": "Process injection",
"ioc": "Process 2124 manipulating memory of non-child process 1636",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1636,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001fc",
"allocation_type": 12288,
"base_address": "0x002d0000"
},
"time": 1567839187.2505,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1259
},
{
"category": "Process injection",
"ioc": "Process 2124 manipulating memory of non-child process 3032",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 3032,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000184",
"allocation_type": 12288,
"base_address": "0x00440000"
},
"time": 1567839187.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1270
},
{
"category": "Process injection",
"ioc": "Process 2124 manipulating memory of non-child process 2124",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2124,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000184",
"allocation_type": 12288,
"base_address": "0x03210000"
},
"time": 1567839187.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1300
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2124,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000184",
"allocation_type": 12288,
"base_address": "0x03260000"
},
"time": 1567839187.4845,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1303
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f0",
"allocation_type": 12288,
"base_address": "0x024d0000"
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1514
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x020d0000"
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1523
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f0",
"allocation_type": 12288,
"base_address": "0x026c0000"
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1535
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x01c90000"
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1544
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f0",
"allocation_type": 12288,
"base_address": "0x01d50000"
},
"time": 1567839197.7665,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1559
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 3032,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x00460000"
},
"time": 1567839197.7815,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1578
},
{
"category": "Process injection",
"ioc": "Process 2124 manipulating memory of non-child process 2672",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2672,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x04570000"
},
"time": 1567839197.7815,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1606
},
{
"category": "Process injection",
"ioc": "Process 2124 manipulating memory of non-child process 304",
"type": "ioc",
"description": null
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 304,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f0",
"allocation_type": 12288,
"base_address": "0x00120000"
},
"time": 1567839198.0165,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1616
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000314",
"allocation_type": 12288,
"base_address": "0x02500000"
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1850
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x020e0000"
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1859
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000314",
"allocation_type": 12288,
"base_address": "0x026d0000"
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1871
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x01cb0000"
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1880
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000314",
"allocation_type": 12288,
"base_address": "0x03300000"
},
"time": 1567839208.6255,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1895
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 3032,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x00470000"
},
"time": 1567839208.6415,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1914
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2672,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x00000314",
"allocation_type": 12288,
"base_address": "0x04b70000"
},
"time": 1567839208.6415,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1938
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 304,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002f4",
"allocation_type": 12288,
"base_address": "0x01c70000"
},
"time": 1567839208.6415,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 1947
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x02510000"
},
"time": 1567839218.8915,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2115
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x020f0000"
},
"time": 1567839218.8915,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2124
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x026e0000"
},
"time": 1567839218.8915,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2136
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x01cc0000"
},
"time": 1567839218.8915,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2145
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x03310000"
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2160
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 3032,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x00480000"
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2179
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2672,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x04b80000"
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2203
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 304,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x01c80000"
},
"time": 1567839218.9065,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2212
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1724,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x02520000"
},
"time": 1567839229.1725,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2342
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1768,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x02200000"
},
"time": 1567839229.1725,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2351
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1692,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x026f0000"
},
"time": 1567839229.1725,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2363
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 1700,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000001dc",
"allocation_type": 12288,
"base_address": "0x01dc0000"
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2372
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2168,
"region_size": 8192,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0x000002ec",
"allocation_type": 12288,
"base_address": "0x03320000"
},
"time": 1567839229.1875,
"tid": 2500,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2124,
"type": "call",
"cid": 2387
}
],
"references": [
"www.endgame.com\/blog\/technical-blog\/ten-process-injection-techniques-technical-survey-common-and-trending-process"
],
"name": "injection_modifies_memory"
},
{
"markcount": 12,
"families": [],
"description": "Modifies security center warnings",
"severity": 3,
"marks": [
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\UpdatesDisableNotify",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\UacDisableNotify",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\AntiVirusOverride",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\UpdatesDisableNotify",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\AntiVirusOverride",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\FirewallOverride",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\UacDisableNotify",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\FirewallDisableNotify",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\AntiVirusDisableNotify",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\AntiVirusDisableNotify",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\FirewallOverride",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\Svc\\FirewallDisableNotify",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "modifies_security_center_warnings"
},
{
"markcount": 1,
"families": [],
"description": "Attempts to modify Explorer settings to prevent hidden files from being displayed",
"severity": 3,
"marks": [
{
"category": "registry",
"ioc": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\Hidden",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "stealth_hiddenfile"
},
{
"markcount": 10,
"families": [],
"description": "Disables Windows Security features",
"severity": 5,
"marks": [
{
"type": "generic",
"description": "attempts to disable user access control",
"registry": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\System\\EnableLUA"
},
{
"type": "generic",
"description": "attempts to disable antivirus notifications",
"registry": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\AntiVirusOverride"
},
{
"type": "generic",
"description": "attempts to disable antivirus notifications",
"registry": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\AntiVirusDisableNotify"
},
{
"type": "generic",
"description": "attempts to disable firewall notifications",
"registry": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\FirewallDisableNotify"
},
{
"type": "generic",
"description": "attempts to disable firewall notifications",
"registry": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\FirewallOverride"
},
{
"type": "generic",
"description": "attempts to disable windows update notifications",
"registry": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\UpdatesDisableNotify"
},
{
"type": "generic",
"description": "disables user access control notifications",
"registry": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Security Center\\UacDisableNotify"
},
{
"type": "generic",
"description": "attempts to disable windows firewall",
"registry": "HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile\\EnableFirewall"
},
{
"type": "generic",
"description": "attempts to disable firewall exceptions",
"registry": "HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile\\DoNotAllowExceptions"
},
{
"type": "generic",
"description": "attempts to disable firewall notifications",
"registry": "HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\SharedAccess\\Parameters\\FirewallPolicy\\StandardProfile\\DisableNotifications"
}
],
"references": [],
"name": "disables_security"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 662,
"time": 6.2276821136475,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 5990,
"time": 12.214584112167,
"dport": 138,
"sport": 138
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7834,
"time": 6.1501441001892,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8162,
"time": 4.1523599624634,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8490,
"time": 6.1649761199951,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8818,
"time": 4.6543991565704,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 9146,
"time": 3.0460710525513,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 9474,
"time": 4.6670999526978,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 28884,
"time": 4.1711449623108,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 37268,
"time": 6.2727701663971,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "432b6cd963e38537133d97d3d7438c0c5b6be8abc0f9ef626d92d053134c4ff9",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "aa88cad9798bdda6b4c5e2352fb4dd8b28d89e8f59e685305ebb65de4ed9aeb4",
"irc": [],
"https_ex": []
}Screenshots
ouhqws.exe removal instructions
The instructions below shows how to remove ouhqws.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the ouhqws.exe file for removal, restart your computer and scan it again to verify that ouhqws.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate ouhqws.exe in the scan result and tick the checkbox next to the ouhqws.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate ouhqws.exe in the scan result.

 d:\ouhqws.exe
d:\ouhqws.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If ouhqws.exe still remains in the scan result, proceed with the next step. If ouhqws.exe is gone from the scan result you're done.
- If ouhqws.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that ouhqws.exe no longer appear in the scan result.
Filename variants
ouhqws.exe may also use other filenames. The most common variants are listed below:
- twav.exe
Folder name variants
ouhqws.exe may also be located in other folders than d:\. The most common variants are listed below:
- j:\
Hashes [?]
| Property | Value |
|---|---|
| MD5 | b6bd427697d9df51a4380ecb7cdc6d82 |
| SHA256 | de14f613fc54eb167248c47264de132c8dbecaef94b42cba4ee61623f5a424f7 |
Error Messages
These are some of the error messages that can appear related to ouhqws.exe:
ouhqws.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
ouhqws.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
ouhqws.exe has stopped working.
End Program - ouhqws.exe. This program is not responding.
ouhqws.exe is not a valid Win32 application.
ouhqws.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with ouhqws.exe?
To help other users, please let us know what you will do with ouhqws.exe:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.