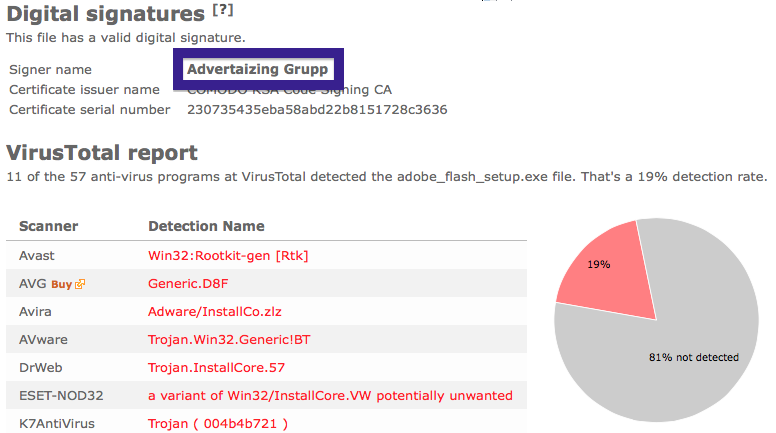
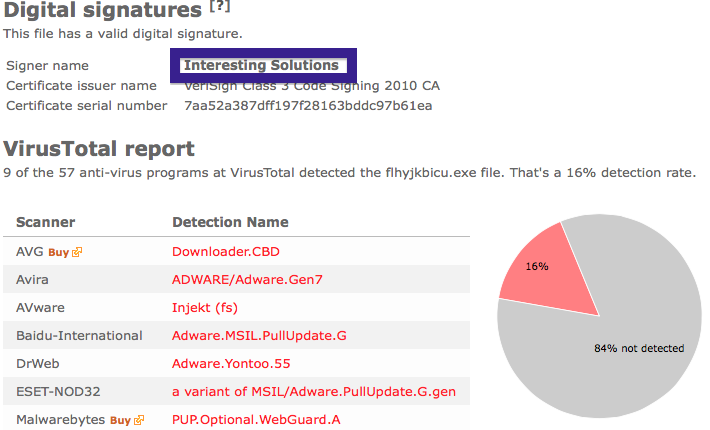
Welcome! Saturday night post this time 😉 Just wanted to let you know about a publisher called Jelbrus LLC. You may run into this download if you are visiting sites such as The Pirate Bay.
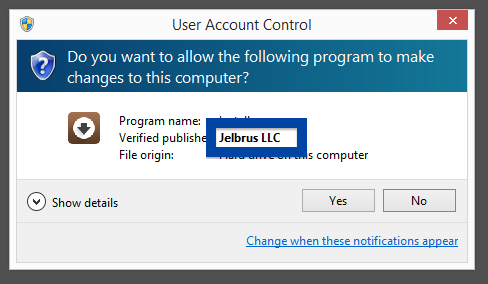
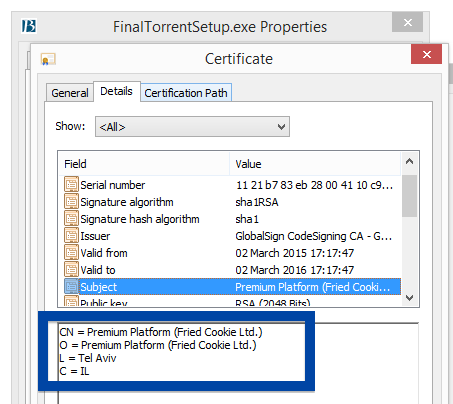
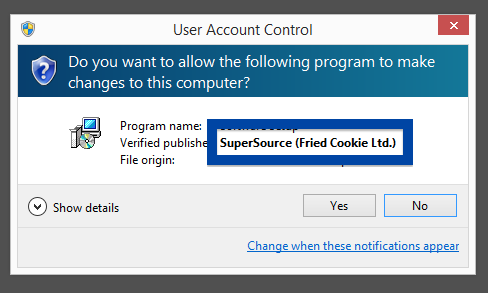
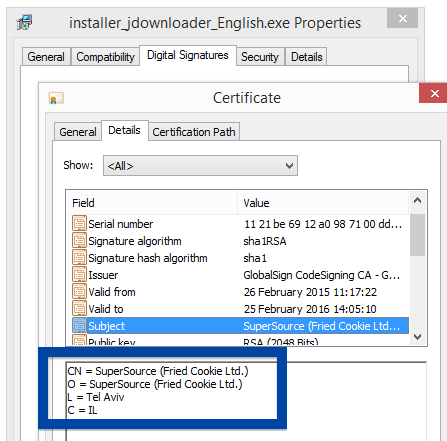
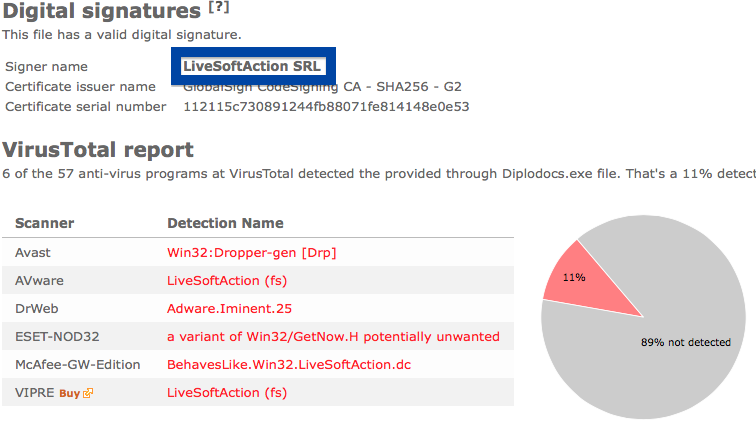
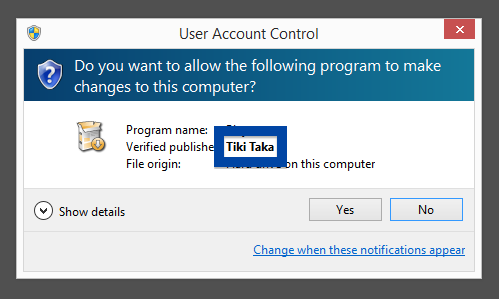
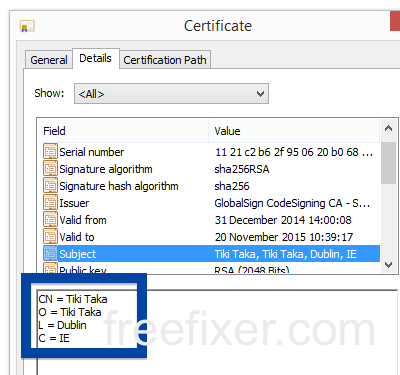
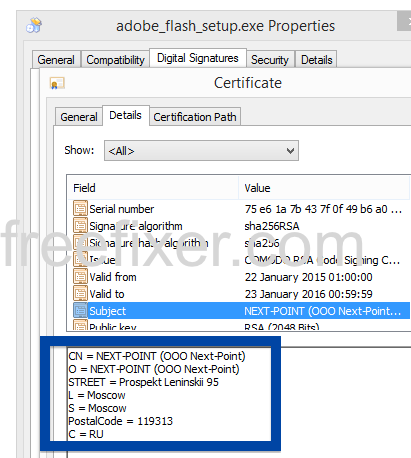
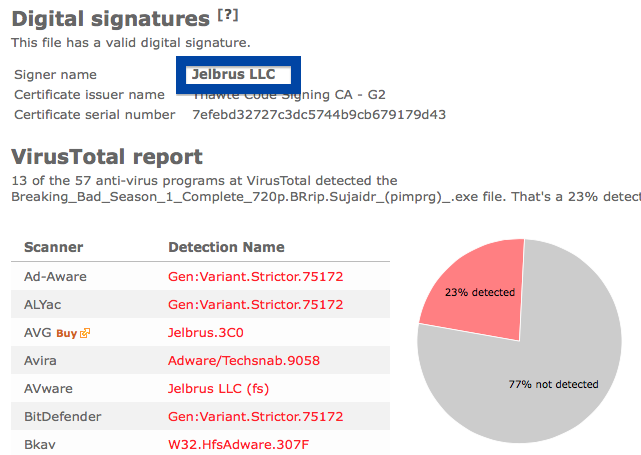
Information about a digital signature and the certificate can also be found under the Digital Signature tab. According to the embedded certificate we can see that Jelbrus LLC seems to be located in Moscow in Russia and that the certificate is issued by Thawte Code Signing CA – G2.
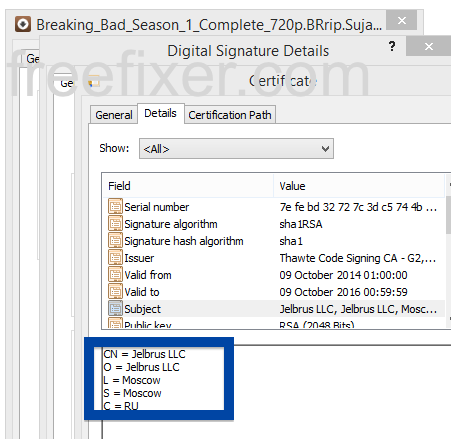
So what’s up with Jelbrus? The file I found is, named Breaking_Bad_Season_1_Complete_720p.BRrip.Sujaidr_(pimprg)_.exe, so you might get the impression that this is a download for the famous TV-Series called Breaking Bad. It’s not.
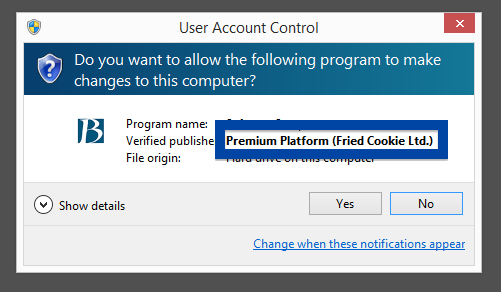
Here’s how the Jelbrus installer looks like if you run the file:
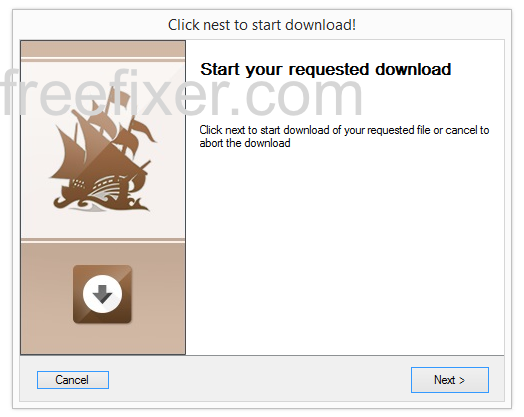
When clicking the Next button a bunch settings are changed and some files are added on your computer. Here’s the interesting stuff from a FreeFixer log:
FreeFixer v1.13 log
http://www.freefixer.com/
Scheduled tasks (39 whitelisted)
================================
Great Performance Ultimate, C:\Program Files (x86)\PrivateVPN\gpup.exe , signer: [unsigned]
Jelbrus Secure Web Task, C:\Program Files (x86)\Jelbrus Secure Web\jswtask.exe , signer: [unsigned]
Malware Cleaner, C:\Users\honeypotter\AppData\Roaming\1265.tmp.exe (file is missing)
Processes (42 whitelisted)
==========================
C:\Windows\mlwps.exe, signer: [unsigned]
C:\Users\HONEYP~1\AppData\Local\Temp\92.tmp.exe, signer: [unsigned]
C:\Program Files (x86)\Jelbrus Secure Web\privoxy.exe, signer: [unsigned]
Services (47 whitelisted)
=========================
Live Malware Protection, Live Malware Protection, c:\windows\mlwps.exe, signer: [unsigned]
PrivoxyService, Privoxy (PrivoxyService), c:\program files (x86)\jelbrus secure web\privoxy.exe, signer: [unsigned]
Recently created/modified files
===============================
20 minutes, c:\Program Files (x86)\Jelbrus Secure Web\mgwz.dll, signer: [unsigned]
20 minutes, c:\Program Files (x86)\Jelbrus Secure Web\privoxy.exe, signer: [unsigned]
20 minutes, c:\Program Files (x86)\Jelbrus Secure Web\jsie.dll, signer: [unsigned]
20 minutes, c:\Program Files (x86)\Jelbrus Secure Web\jswff.exe, signer: Jelbrus LLC [valid]
20 minutes, c:\Program Files (x86)\Jelbrus Secure Web\jsweb64.dll, signer: [unsigned]
20 minutes, c:\Program Files (x86)\Jelbrus Secure Web\jswchromium64.exe, signer: [unsigned]
20 minutes, c:\Program Files (x86)\Jelbrus Secure Web\jsweb.dll, signer: [unsigned]
20 minutes, c:\Program Files (x86)\Jelbrus Secure Web\jswchromium.exe, signer: [unsigned]
20 minutes, c:\Program Files (x86)\Jelbrus Secure Web\jswtask.exe, signer: [unsigned]
20 minutes, c:\Users\honeypotter\AppData\Local\Temp\92.tmp.exe, signer: [unsigned]
21 minutes, c:\Program Files (x86)\PrivateVPN\tasks.dll, signer: [unsigned]
21 minutes, c:\Users\honeypotter\AppData\Local\Temp\tasks.dll, signer: [unsigned]
21 minutes, c:\Program Files (x86)\PrivateVPN\gpup.exe, signer: [unsigned]
21 minutes, c:\Users\honeypotter\AppData\Local\Temp\580C.tmp.exe, signer: [unsigned]
23 minutes, c:\Users\honeypotter\AppData\Local\Temp\1716.tmp.exe, signer: [unsigned]
24 minutes, c:\Users\honeypotter\AppData\Local\Temp\6E23.tmp.exe, signer: [unsigned]
LAN Proxy Settings
==================
*=127.0.0.1:8118
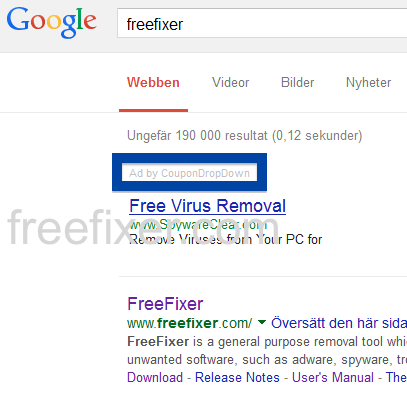
You will also see advertisements while browsing the web labelled “Ad by CouponDropDown“. Here’s the “Ad by CouponDropDown” ads on Google:
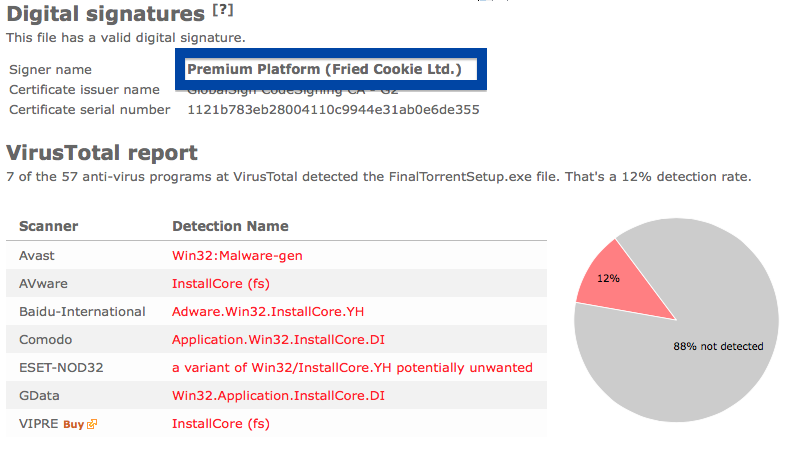
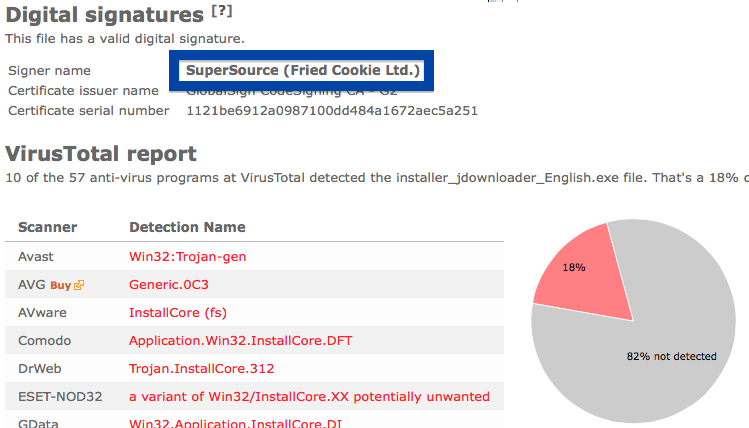
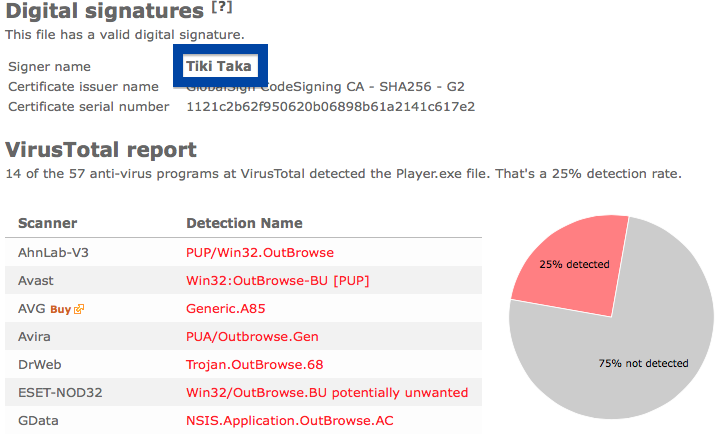
So what does the anti-virus scanners at VirusTotal say about Jelbrus’ “Breaking Bad” file? The detection rate is 13/57. Gen:Variant.Strictor.75172, Jelbrus.3C0, Adware/Techsnab.9058, Jelbrus LLC (fs), W32.HfsAdware.307F and Gen:Variant.Strictor.75172 were some of the detection names.
Did you also find an Jelbrus LLC? Did you also find it at The Pirate Bay?
Thank you for reading.