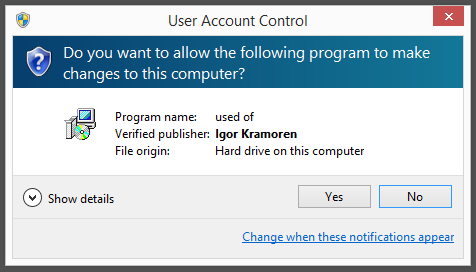
Found a file this morning, claiming to be a Flash Player setup file. However, the file was not digitally signed by Adobe, which is the publisher of the Flash Player. Instead it was signed by a company called Wilmaonline LTD. which made it look suspicious.
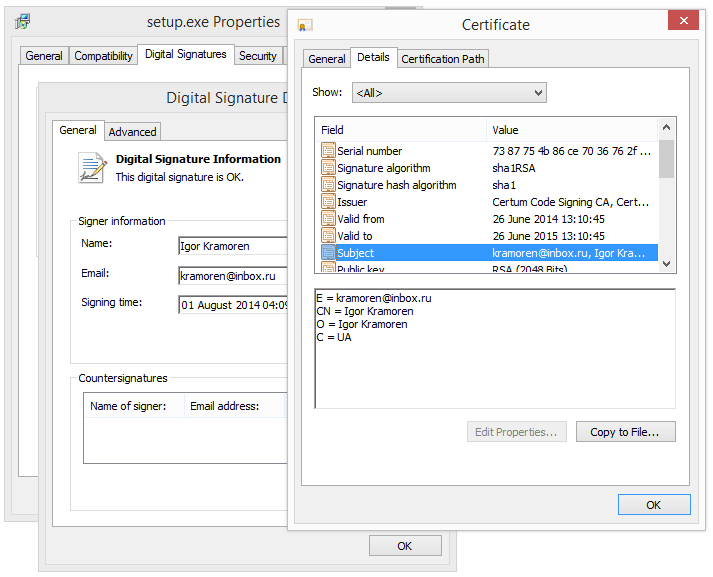
According to the certificate that is embedded in the file, Wilmaonline is a company located in Israel.
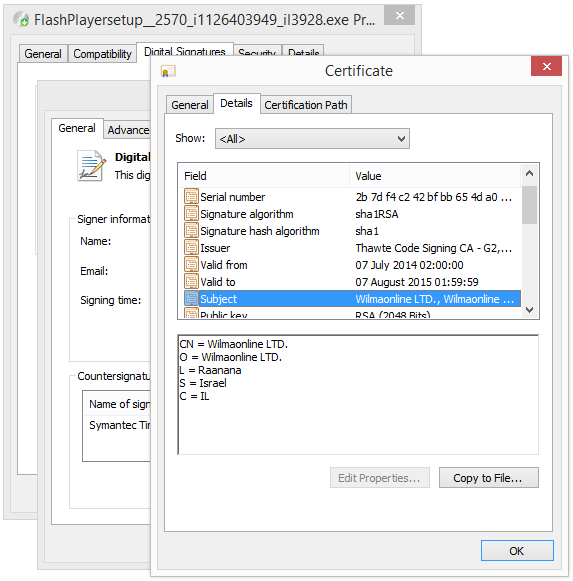
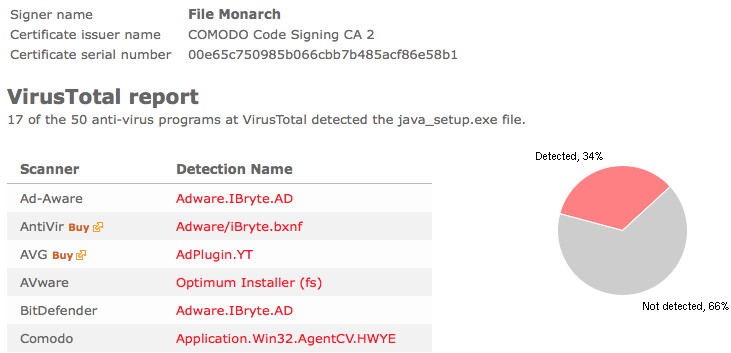
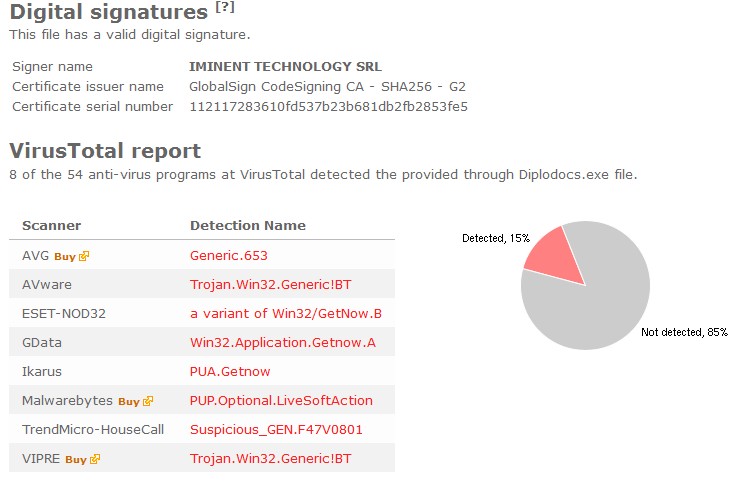
So, what does the anti-virus programs say about the Wilmaonline file? No problem, I just uploaded the file to VirusTotal and it turned out that many of the anti-virus programs detects the Wilmaonline file, with names such as Adware.Downware and PUP.Optional.Amonetize.
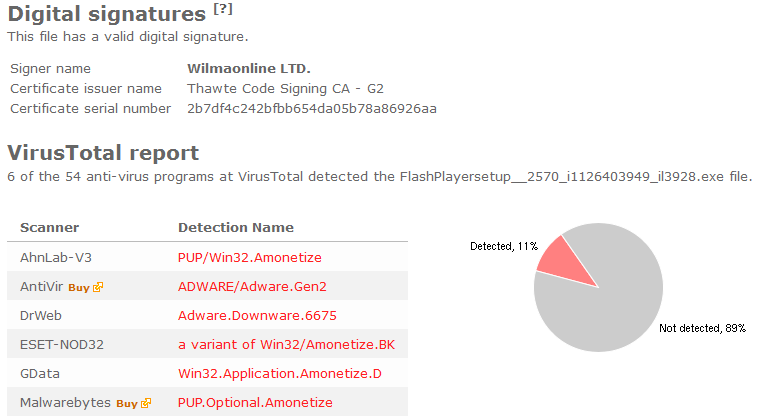
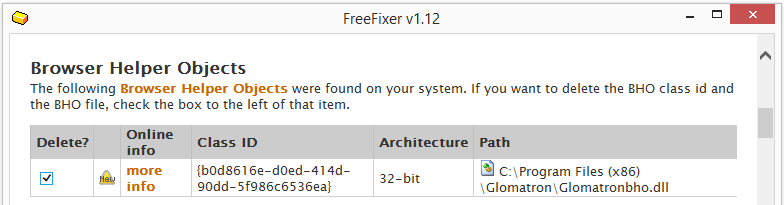
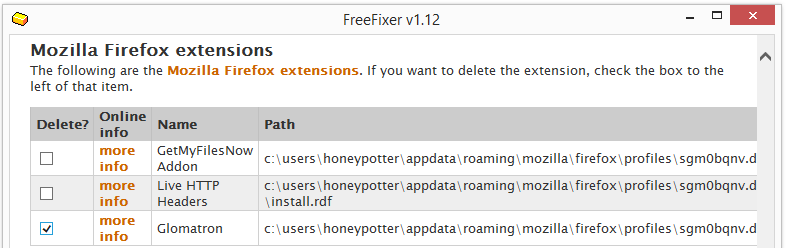
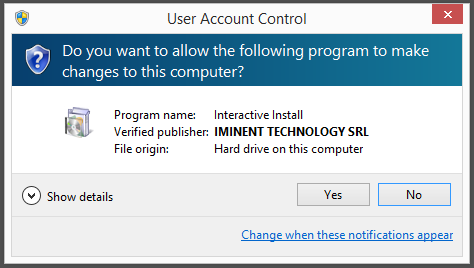
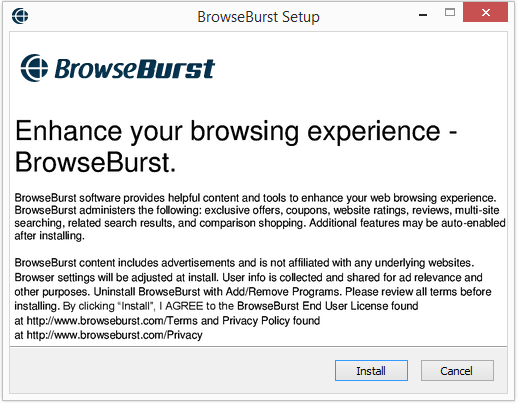
To see more in details what changes the Wilmaonline file would do on a user’s computer I decided to run the file on my lab machine. The following InstallPath installer appeared, where “Flash Player”, Dolphin Deals, Flow Surf, Webssearches and OffersWizard selected for installation by default. This is probably the reason why the anti-virus programs detects the Wilmaonline file, in addition to using Adobe’s Flash trademark.
Did you also find a file digitally signed by Wilma Online? What kind of download was it and where did you find it?
Update 13 Sep 2014: Thought I should follow up on this one. The Wilmaonline signed files are still being distributed. They are promoted as Flash Players, chess games, Ask.FM trackers, keygens, cracks, etc. The installer file includes lots of bundled programs, but for unknown reasons, nothing is installed when I click through the installer. Did you also see this behaviour, or did it install the bundled programs on your machine? The anti-virus programs have improved their detection rates somewhat for the WilmaOnline files:
- 18/54 – FlashPlayersetup__2570_i1300328638_il1783.exe
- 15/52 – Chess Titans setup__6670_il4710.exe
- 15/55 – Ask Fm Tracker 2014 Downloader__3687_i1301881522_il2700510.exe
- 14/55 – Keygen Installer__9167_il260.exe