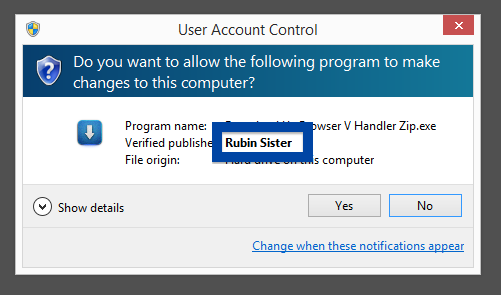
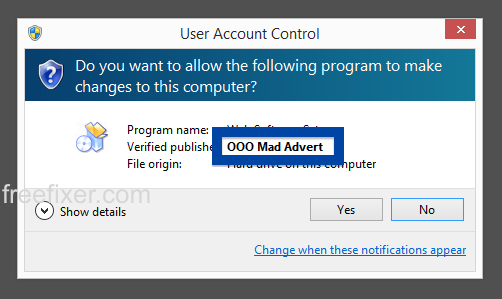
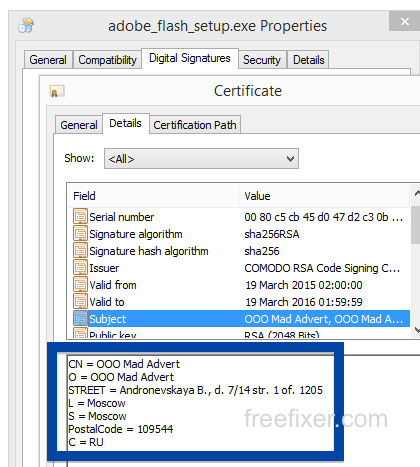
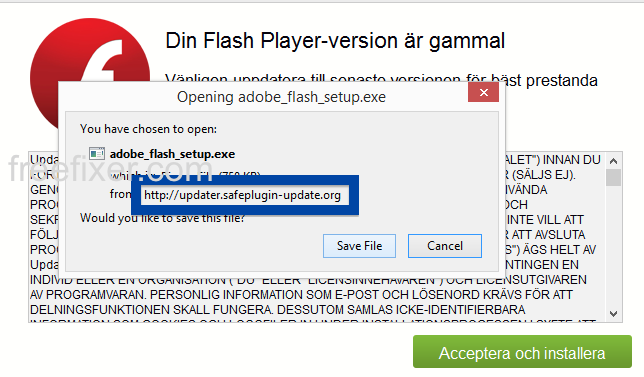
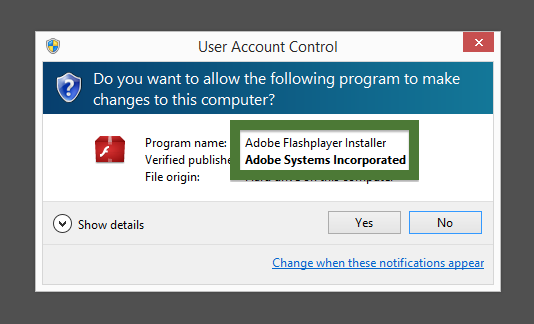
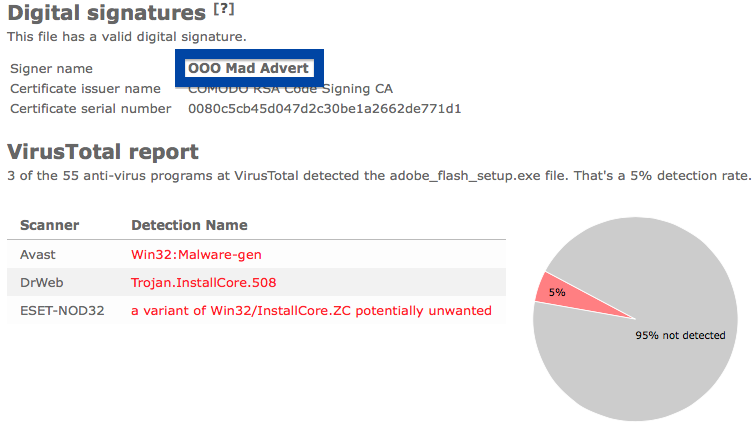
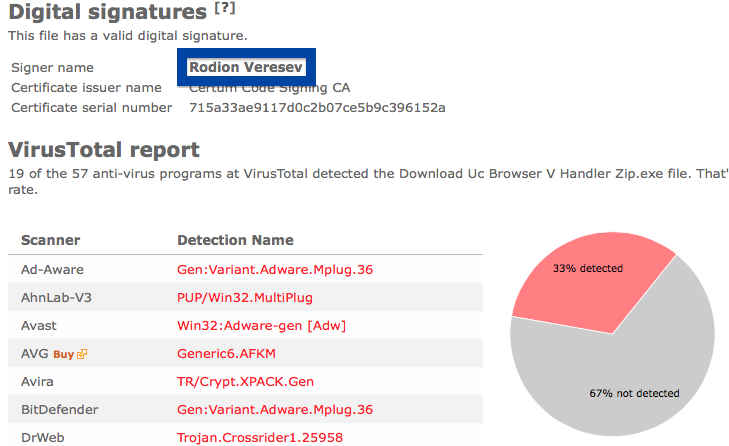
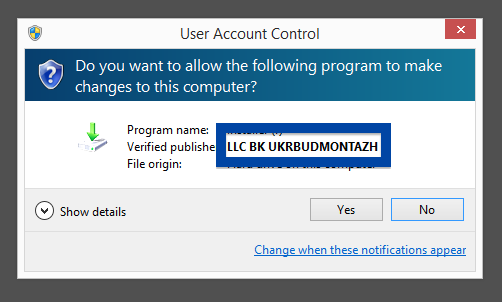
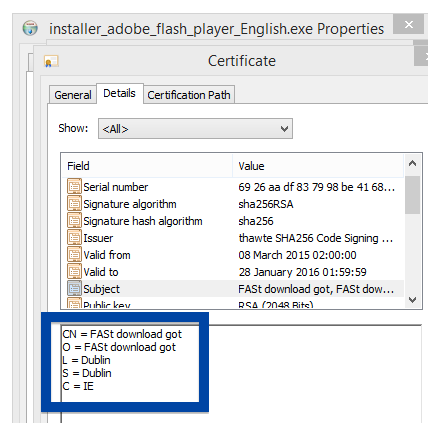
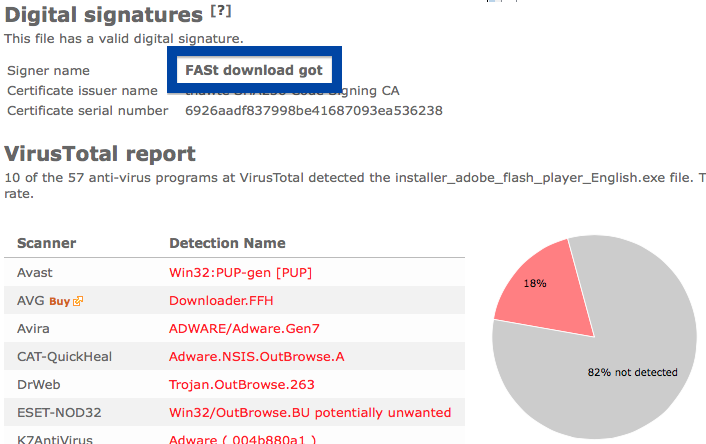
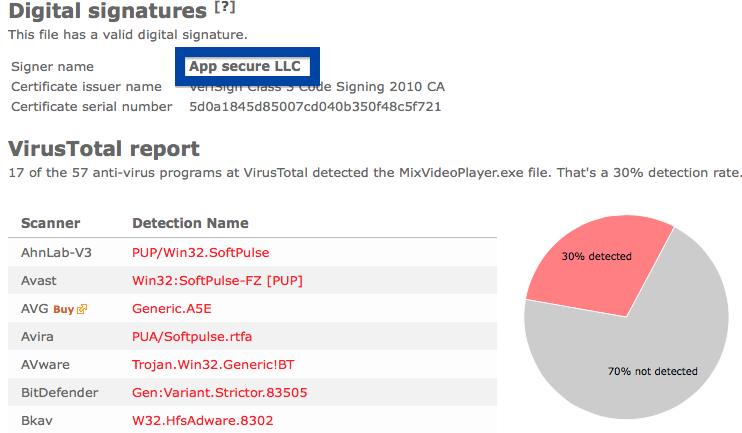
Hello! If you are a regular here on the FreeFixer blog you know that I’ve been looking on the certificates used to sign files that bundled various types of unwanted software. Today I found another certificate, used by a publisher called App secure LLC.
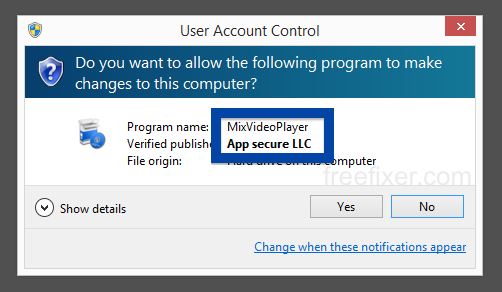
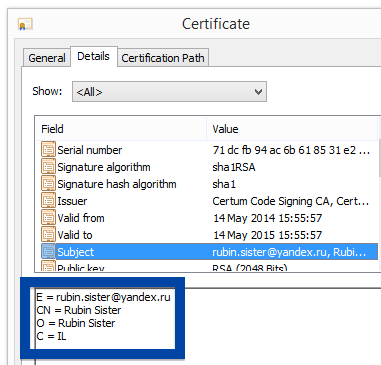
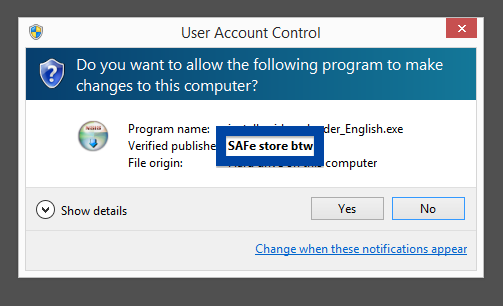
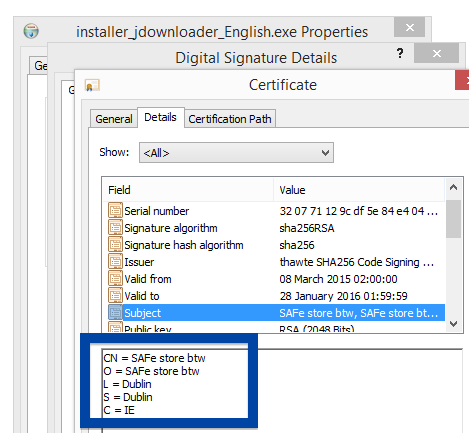
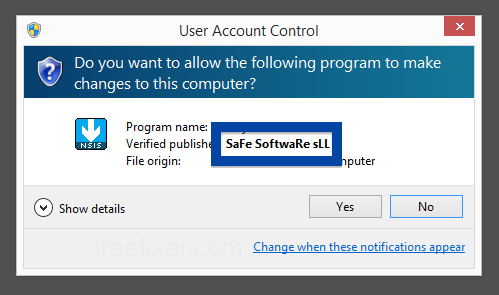
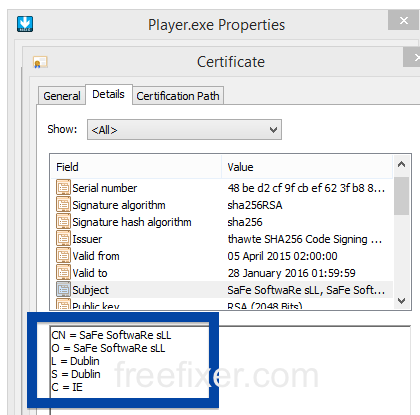
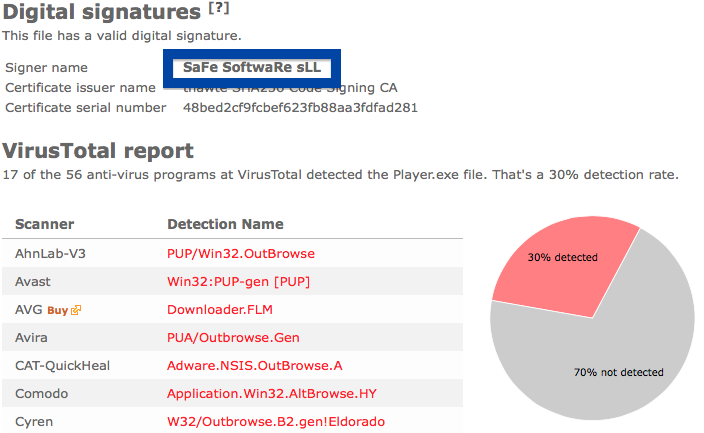
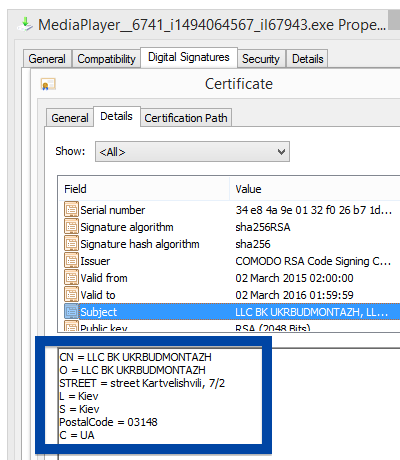
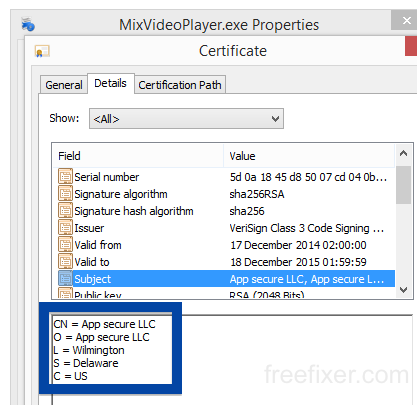
Windows will display App secure LLC as the publisher when running the file. Information about a digital signature and the certificate can also be found under the Digital Signature tab. The screenshot below shows the App secure LLC certificate. From the certificate info we can see that App secure LLC appears to be located in Wilmington, Delaware in the US.
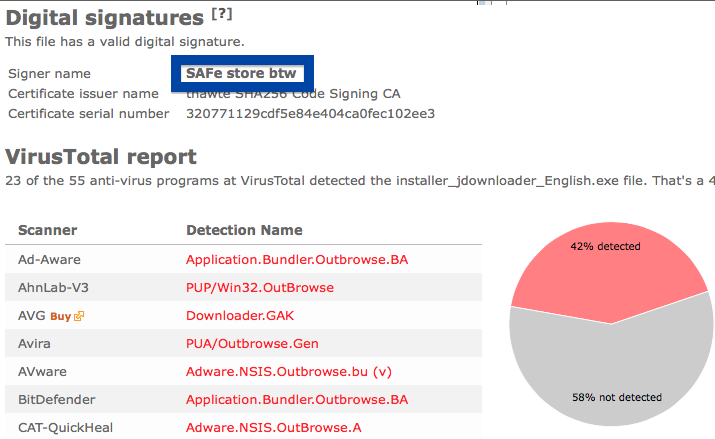
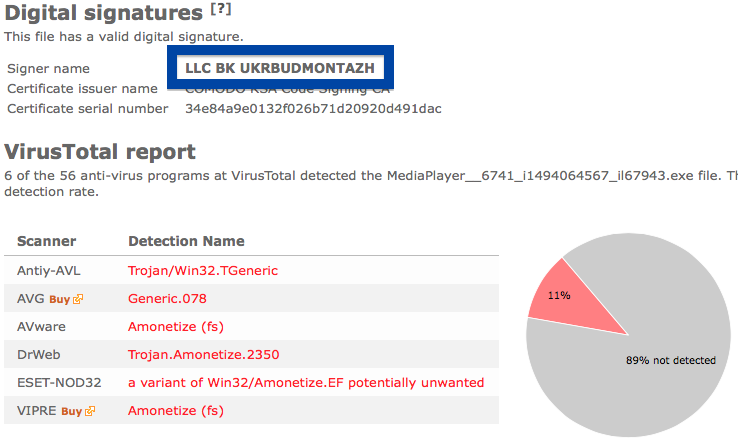
When I uploaded the App secure LLC file to VirusTotal, it came up with a 30% detection rate. The file is detected as Win32:SoftPulse-FZ [PUP] by Avast, W32.HfsAdware.8302 by Bkav, Gen:Variant.Strictor.83505 (B) by Emsisoft, a variant of Win32/SoftPulse.AB potentially unwanted by ESET-NOD32, not-a-virus:Downloader.Win32.DriverUpd.wui by Kaspersky and SoftPulse by Sophos.
The company web site appears to be APPSECURELLC.COM. Here’s some of the info from the WHOIS database:
Registrant Name: Roberto Blangino
Registrant Organization: App Software LLC
Registrant Street: 501 Silverside Road, Suite 105
Registrant City: Wilmington
Registrant State/Province: Delaware
Registrant Postal Code: 19809
Registrant Country: US
I checked some of services that provides domain info based on an IP address, and the following sites appears to be or have been located on the same IP:
- 123maxmusic.com
- 88dls.com
- acpsoftwarellc.com
- www.magnoplayer.com
- www.newvideoplayer.com
Did you also find a file that was signed by App secure LLC? What kind of download was it and was it detected by the anti-virus scanners at VirusTotal? Please share in posting comments below.
Thanks for reading.