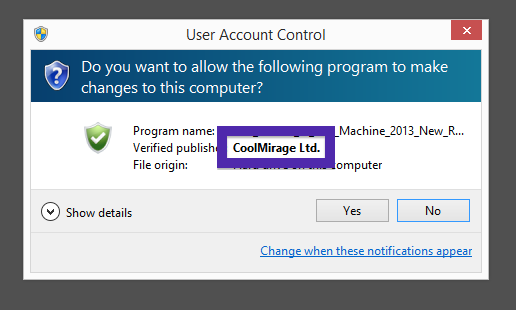
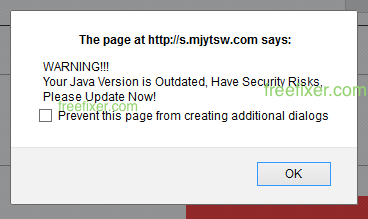
Hello! Here’s a short blog post from a foggy Stockholm. If you’ve been following me for the last year you know that I’ve been examining many software publishers that put a digital signature on their downloads. Today I found another publisher called CoolMirage Ltd. which appears to have been around for some time.
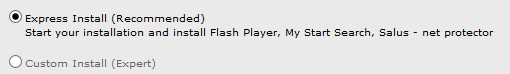
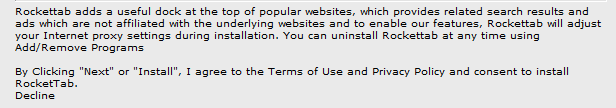
The file is named in a way which can make some users think they are downloading a movie, rather than an executable file.
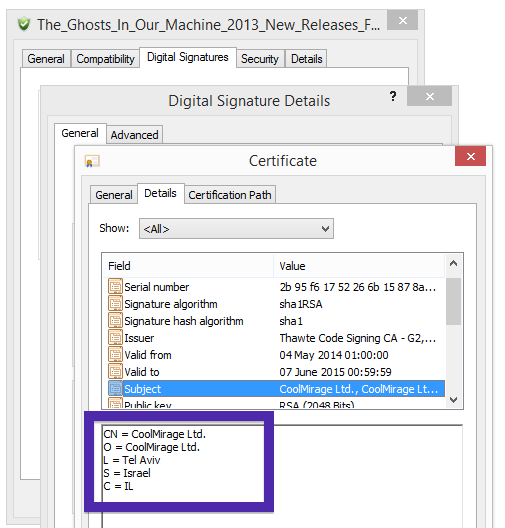
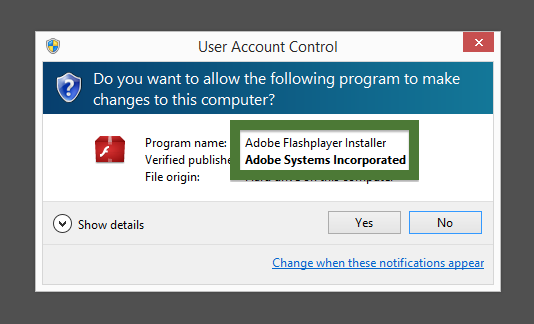
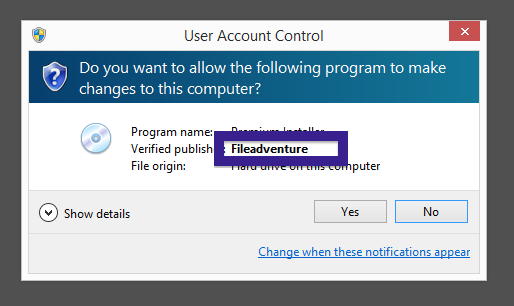
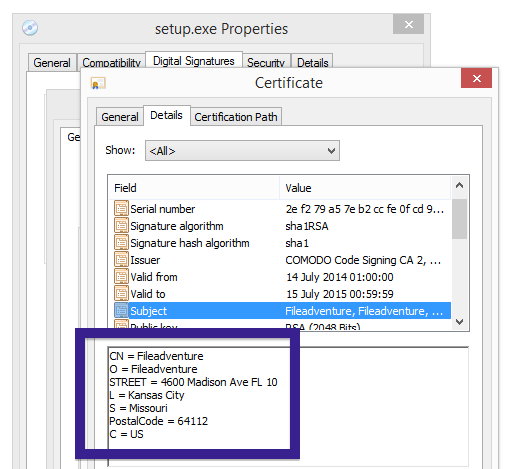
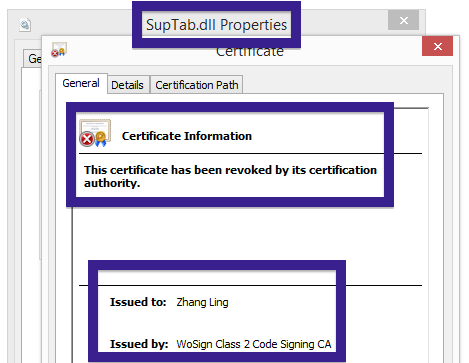
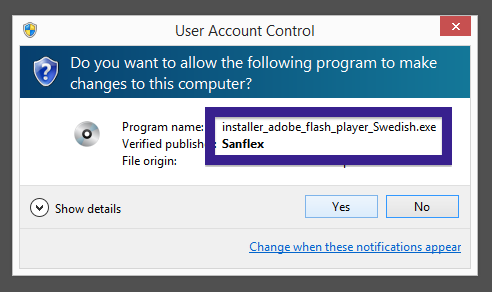
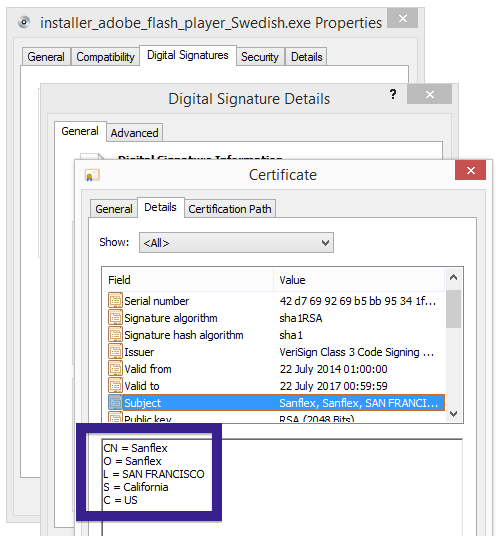
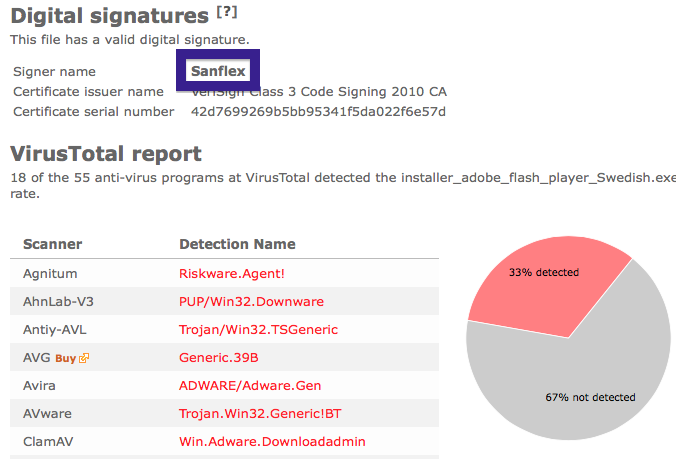
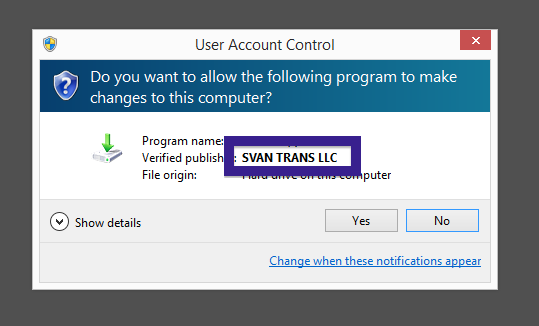
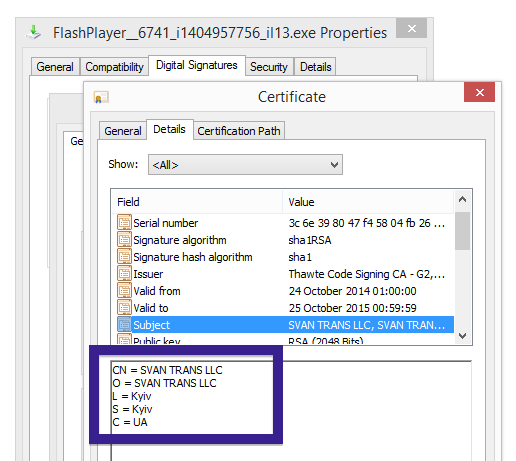
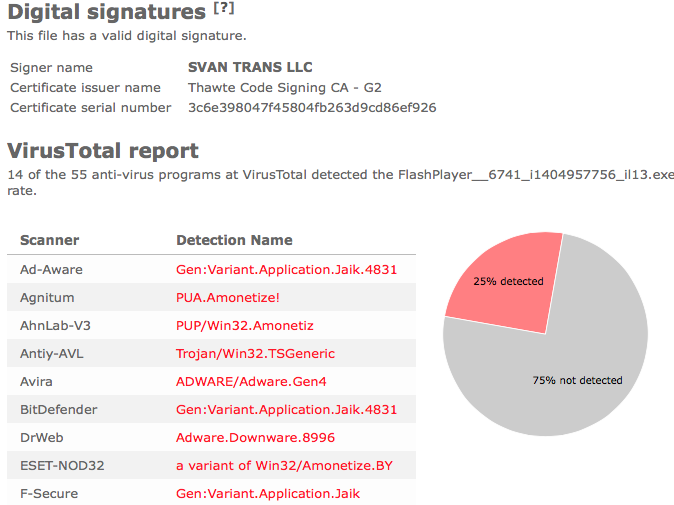
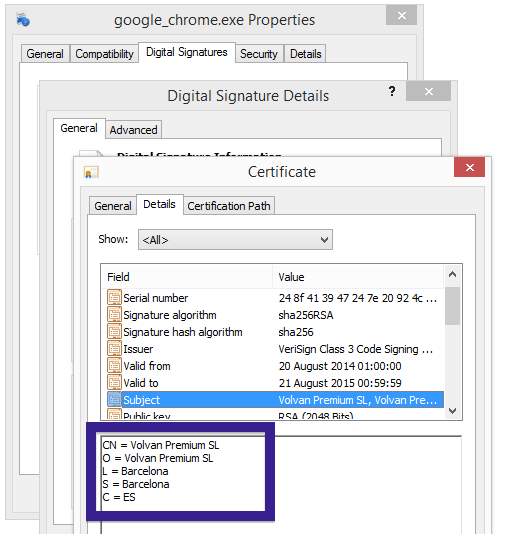
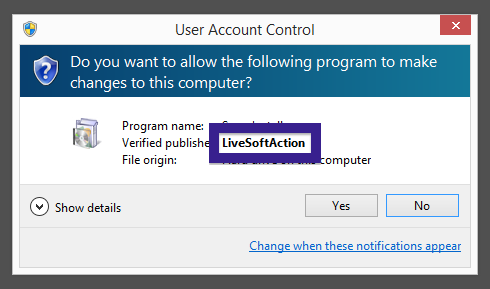
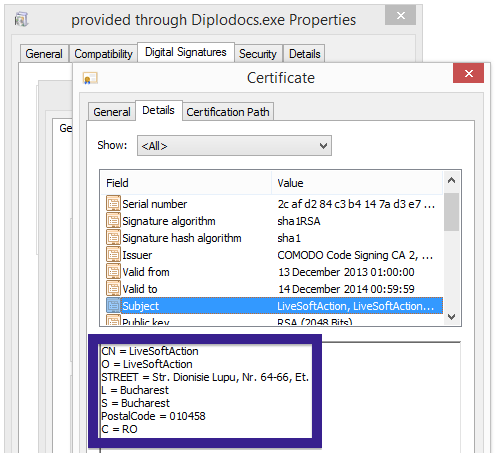
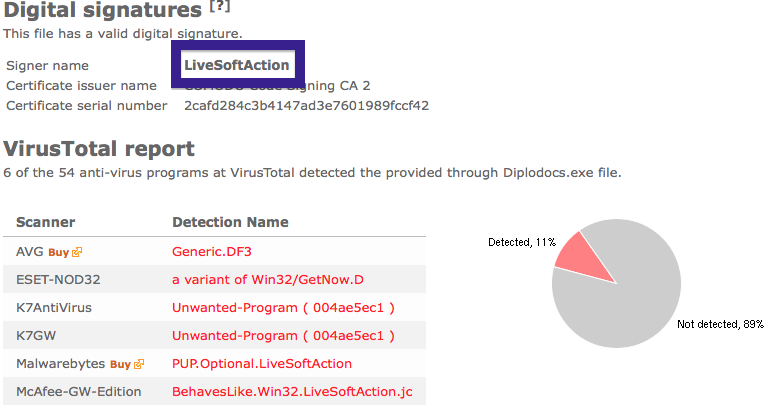
Typically you’d see the CoolMirage Ltd. publisher name appear when double-clicking on the downloaded file: Viewing the certificate information is also possible by looking under the digital signature tab for the file. Here the certificate says that CoolMirage Ltd. is located in Tel Aviv, Israel.
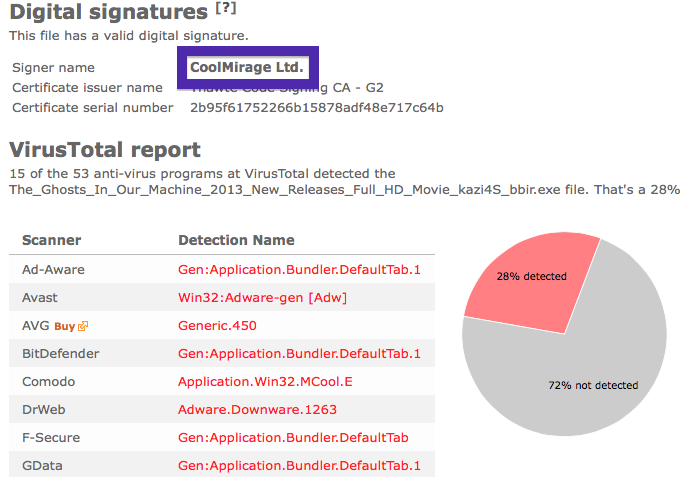
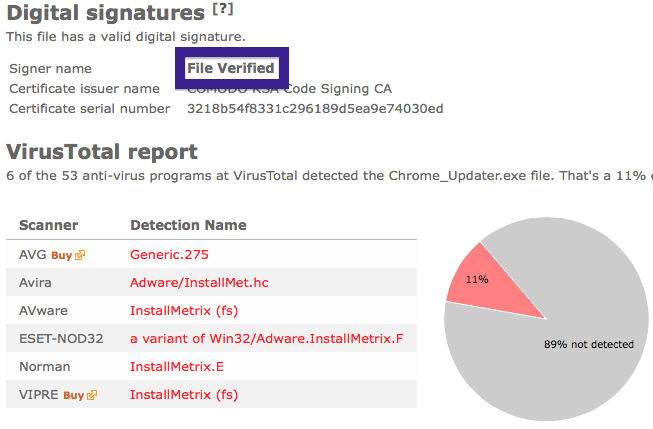
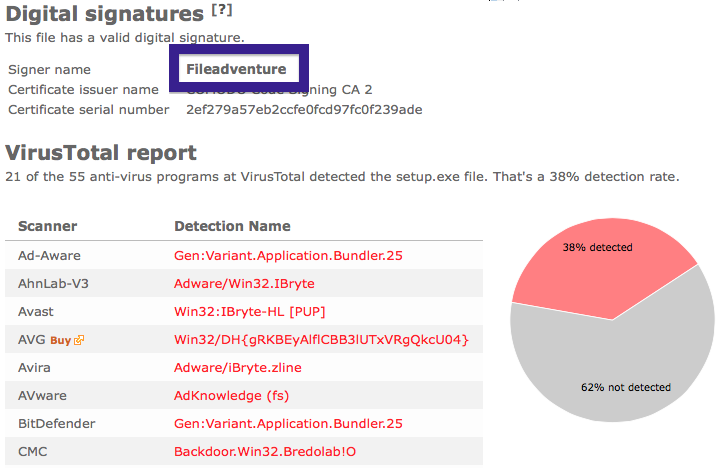
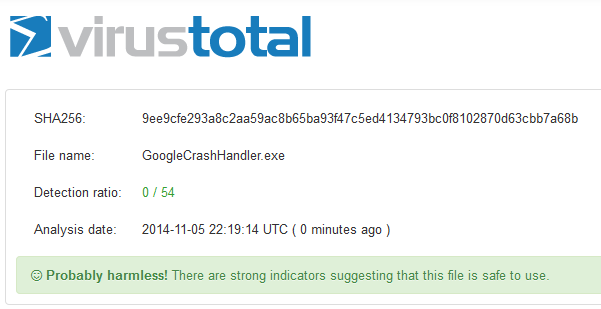
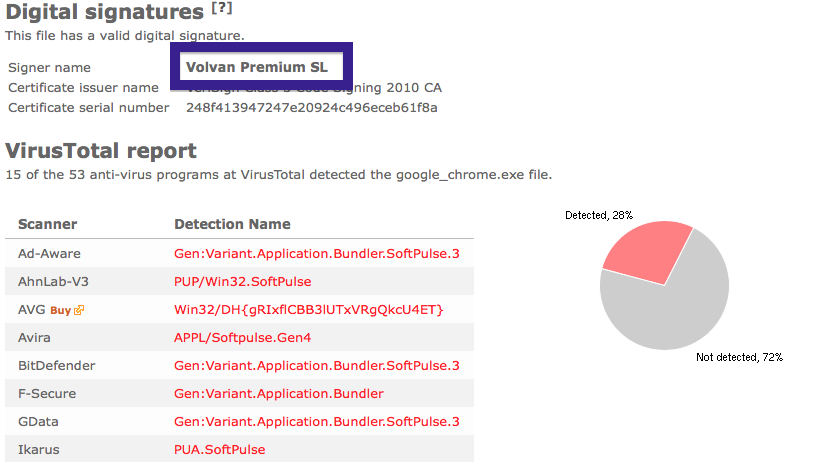
The issue with the CoolMirage Ltd. file is that it is detected by many of the anti-malware scanners. Here are some of the detection names: Gen:Application.Bundler.DefaultTab.1, PUP.Optional.OneClickDownloader.A, Adware-SweetIM, PUP/MultiToolbar.A and CoolMirage.
Did you also find a CoolMirage Ltd. file? Do you remember the download link? Please post it in the comments below and I’ll upload it to VirusTotal to see if that one is also detected.
Thanks for reading.