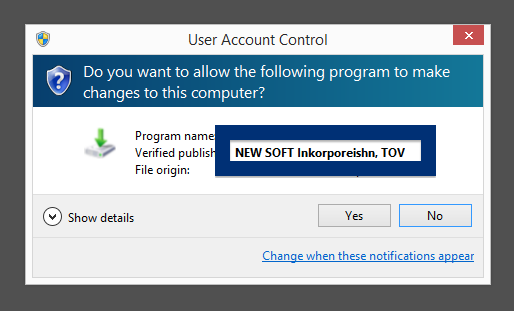
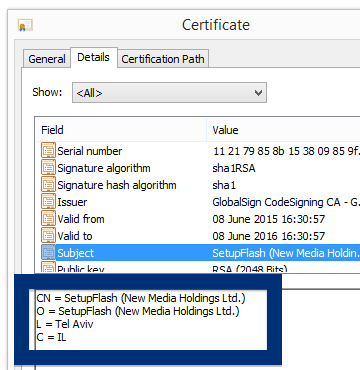
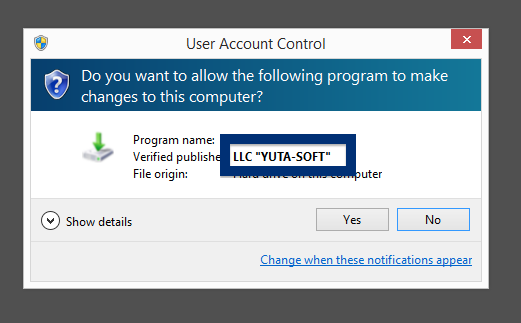
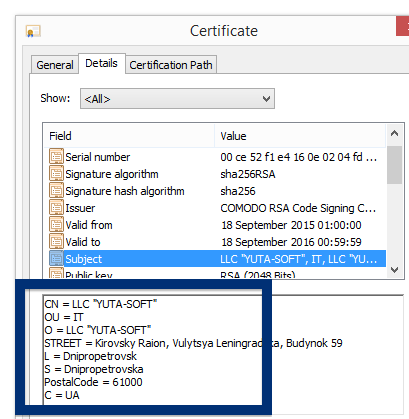
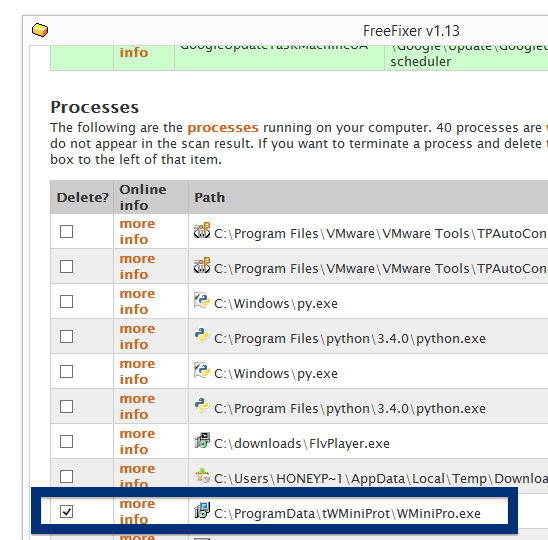
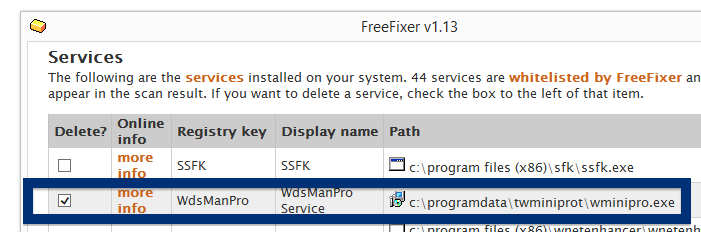
Welcome! If you’ve been following me for the last year you know that I’ve been examining many software publishers that put a digital signature on their downloads. Today I found another publisher called NEW SOFT Inkorporeishn, TOV.
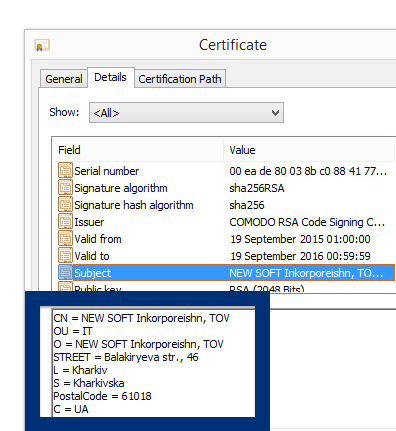
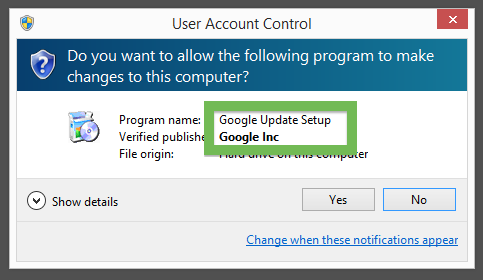
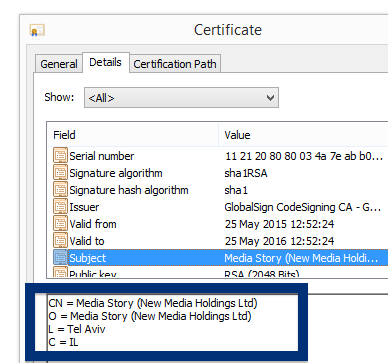
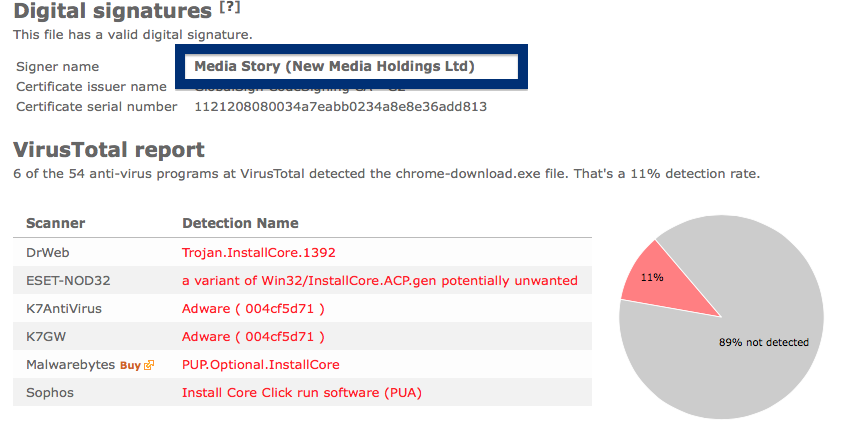
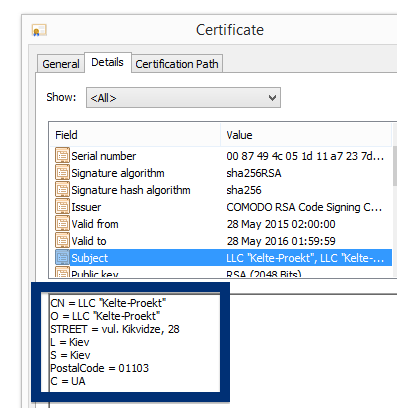
You can see who the signer is when double-clicking on an executable file. NEW SOFT Inkorporeishn, TOV appears in the publisher field in the dialog that pops up. It is also possible to check a digital signature by looking at a file’s properties. Here’s a screenshot of the NEW SOFT Inkorporeishn, TOV certificate.
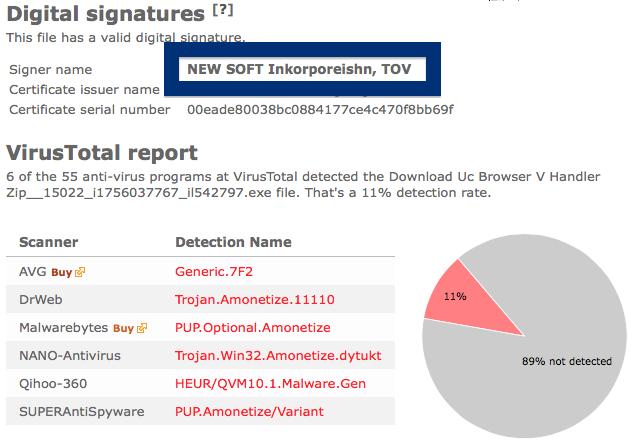
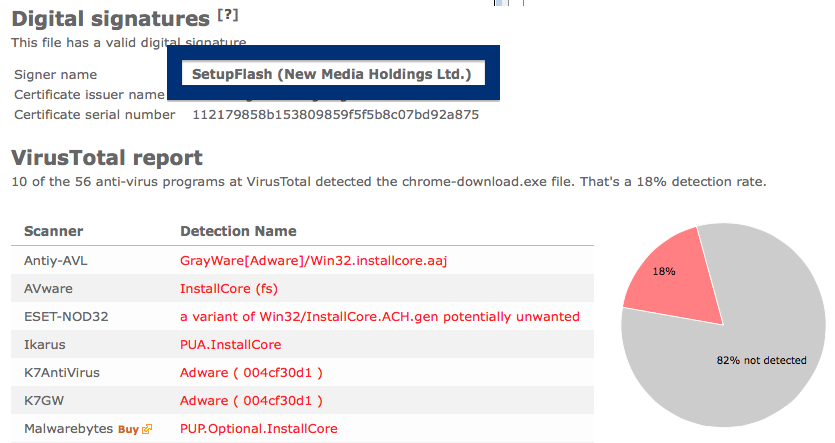
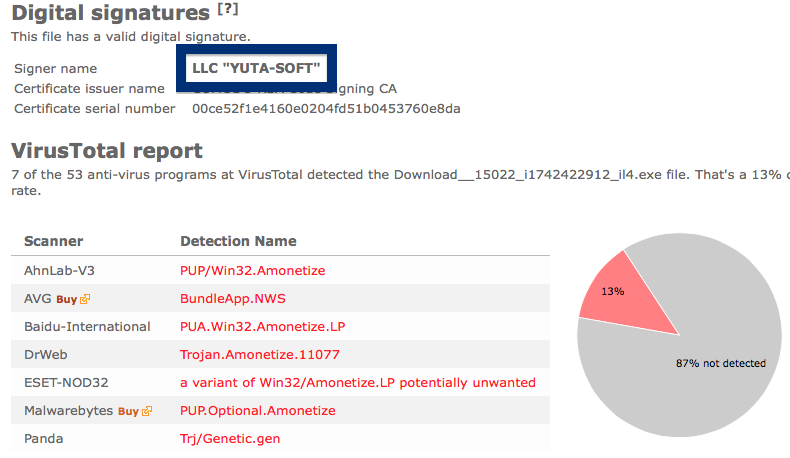
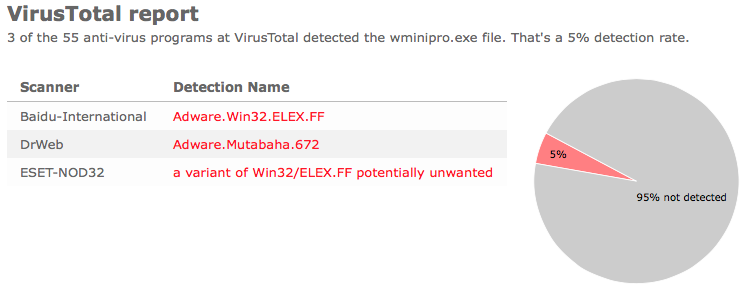
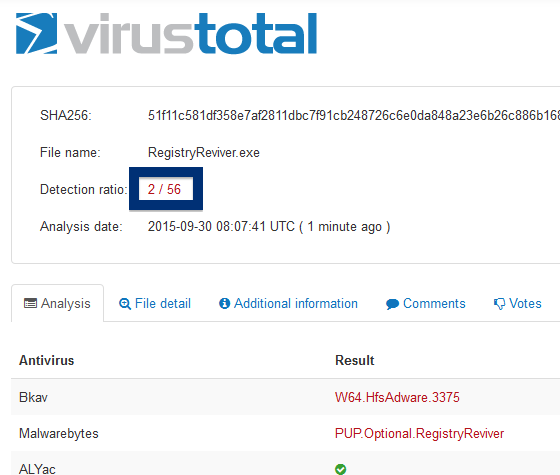
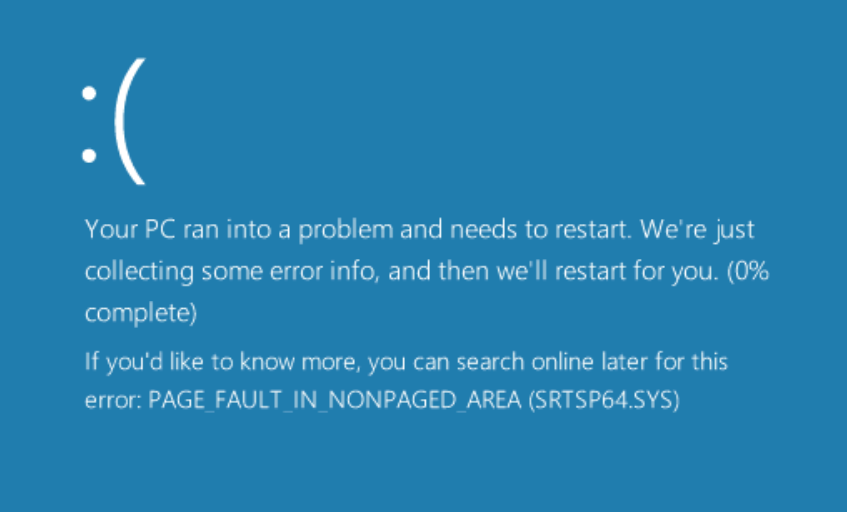
So, why am I writing about the NEW SOFT Inkorporeishn, TOV file? Check out what the anti-malware software report about the file:
SUPERAntiSpyware reports PUP.Amonetize/Variant, Malwarebytes classifies it as PUP.Optional.Amonetize, Qihoo-360 calls it HEUR/QVM10.1.Malware.Gen and DrWeb reports Download Uc Browser V Handler Zip__15022_i1756037767_il542797.exe as Trojan.Amonetize.11110 are a few of the detection names for Download Uc Browser V Handler Zip__15022_i1756037767_il542797.exe.
Did you also find a NEW SOFT Inkorporeishn, TOV download? What kind of download was it?
Thanks for reading.