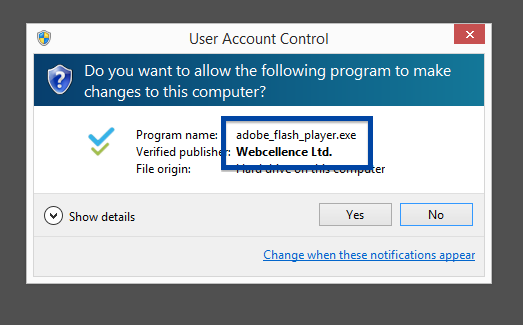
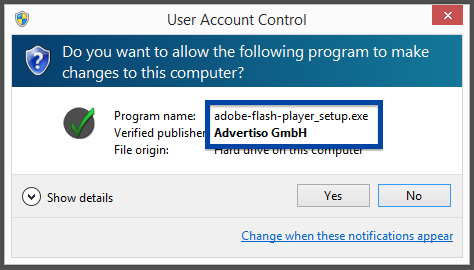
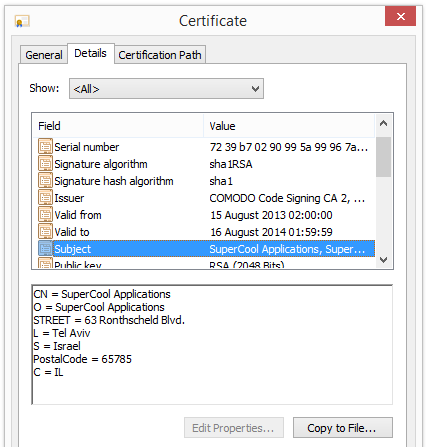
Hi there! If you’ve been following me for the last year you know that I’ve been examining many software publishers that put a digital signature on their downloads. A few days ago I found another publisher called Webcellence Ltd..
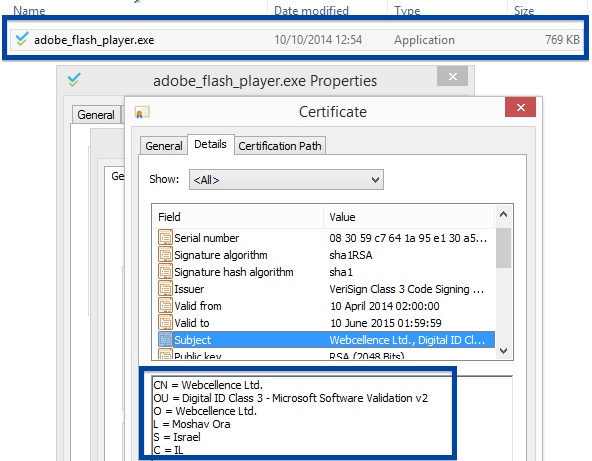
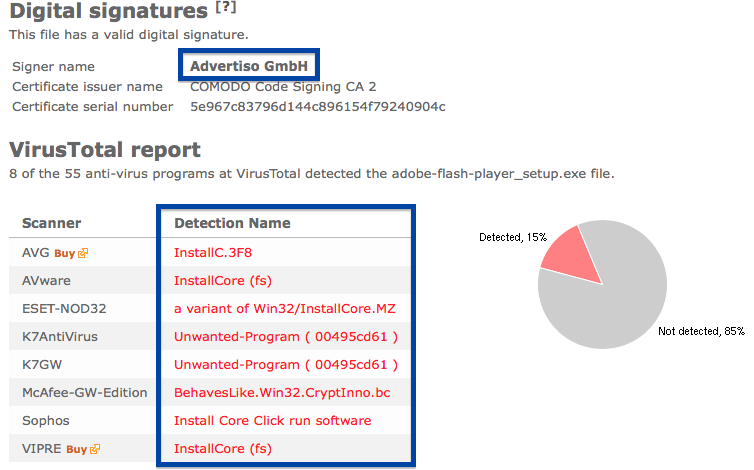
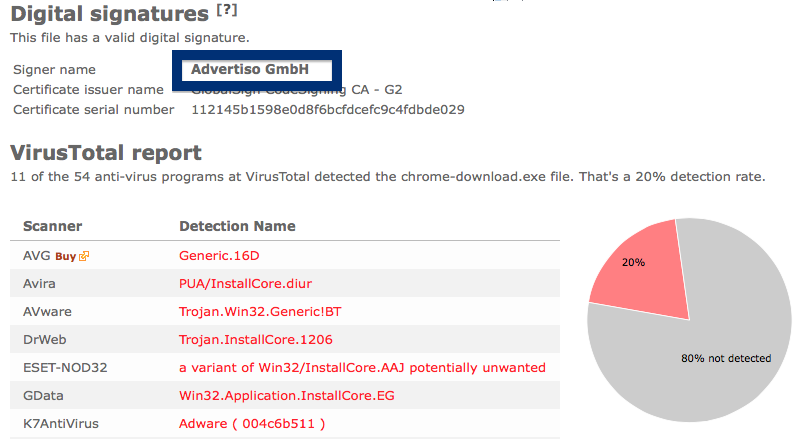
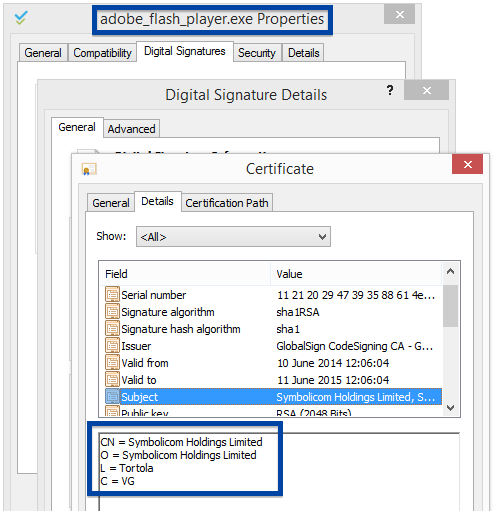
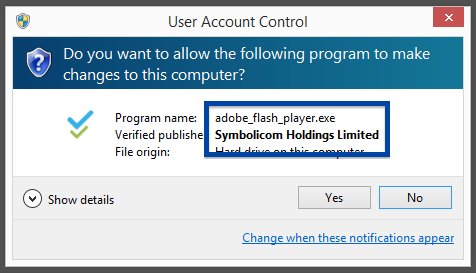
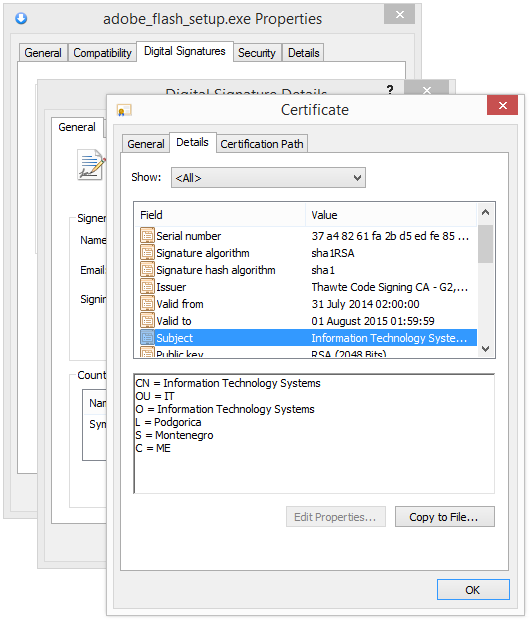
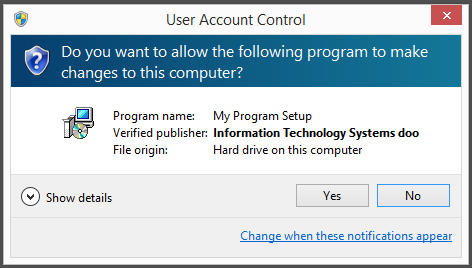
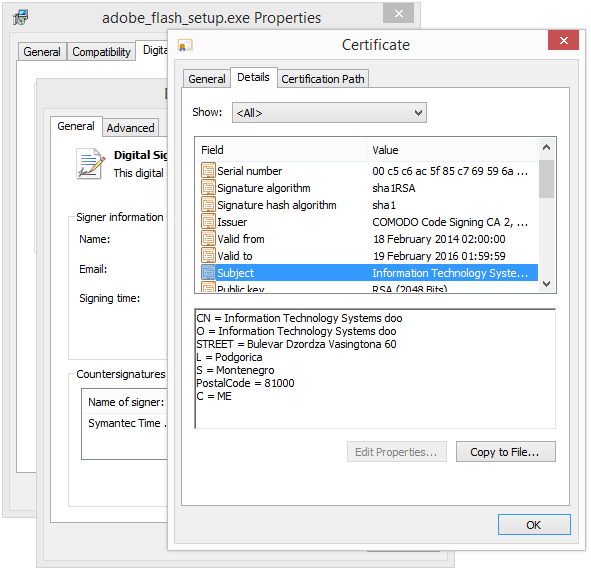
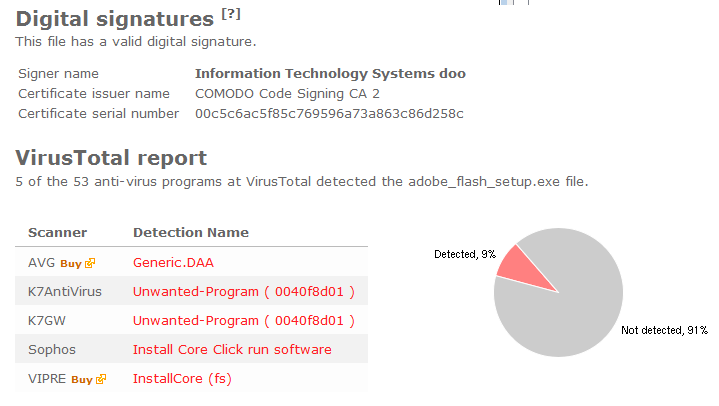
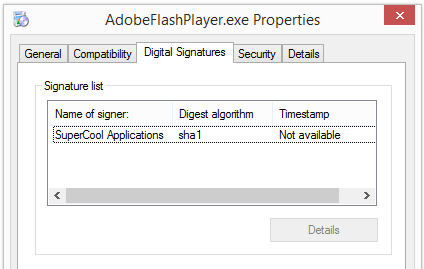
To get more details on the publisher, you can view the certificate by right-clicking on the file, and looking under the Digital Signatures tab: According to the certificate we can see that Webcellence Ltd. is located in Moshav Ora, Israel and that the certificate is issued by VeriSign Class 3 Code Signing 2010 CA.
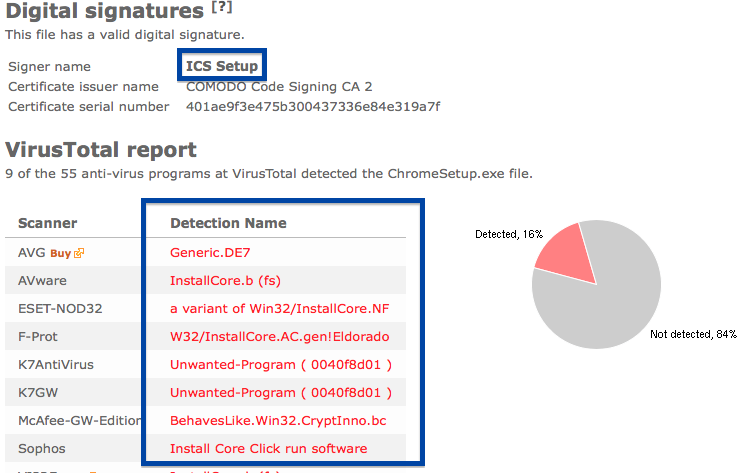
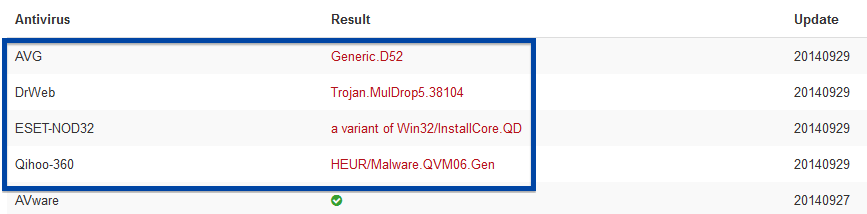
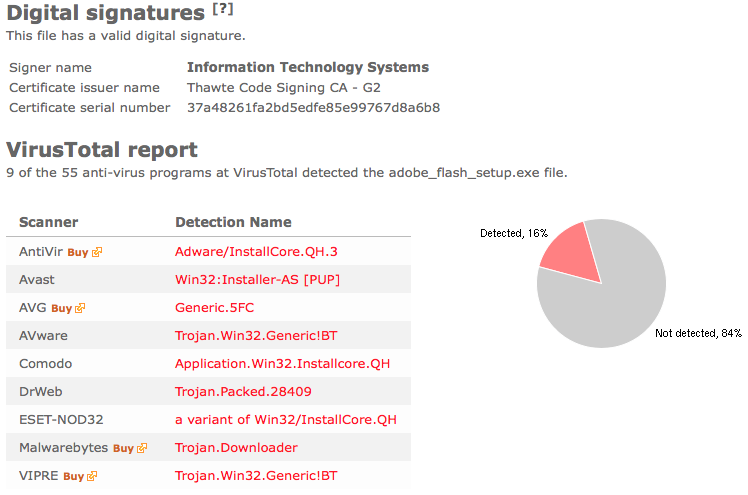
The reason I’m writing this blog post is that the Webcellence Ltd. file is detected by a few of the anti-virus progams at VirusTotal. DrWeb classifies adobe_flash_player.exe as Trojan.MulDrop5.38502 and ESET-NOD32 calls it a variant of Win32/InstallCore.QD.
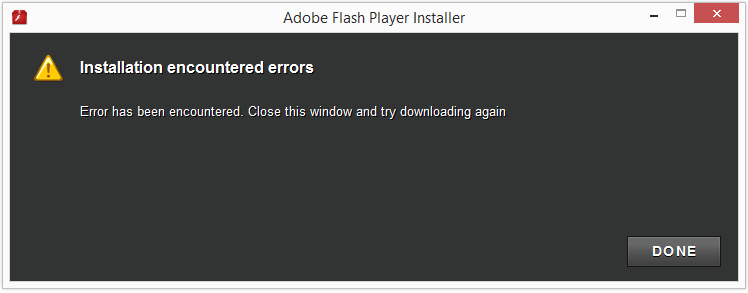
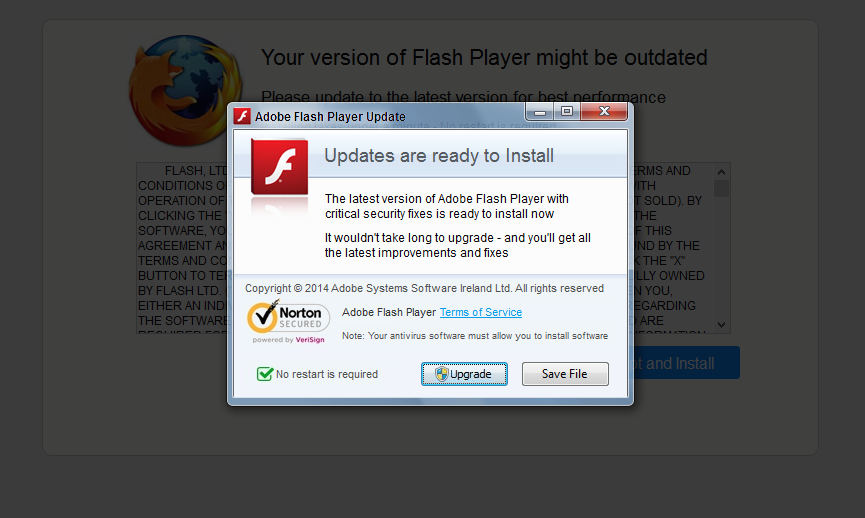
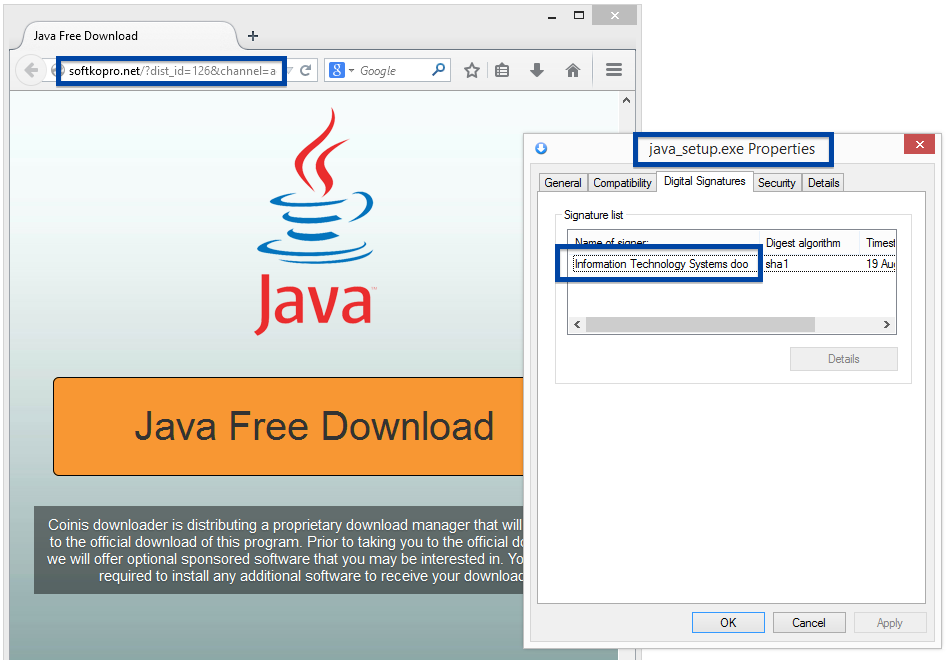
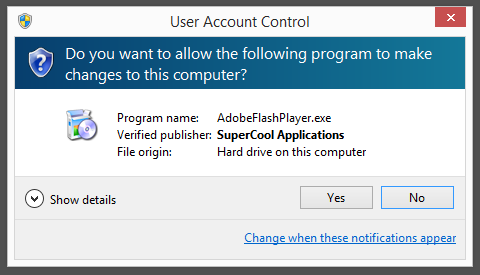
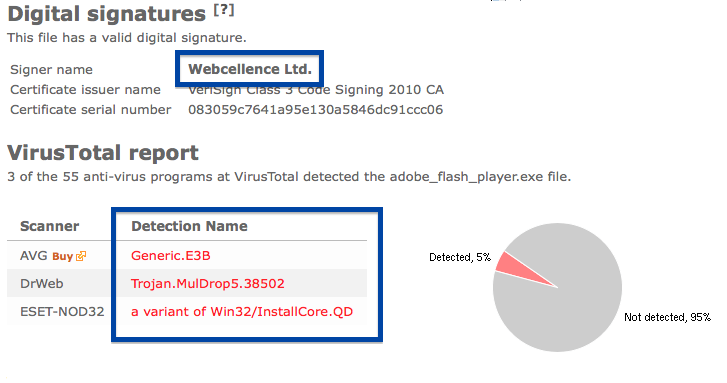 Although the file is named adobe_flash_player.exe it’s not the official download for the Adobe Flash Player. The real flash player installer should be digitally signed by the Adobe company.
Although the file is named adobe_flash_player.exe it’s not the official download for the Adobe Flash Player. The real flash player installer should be digitally signed by the Adobe company.
Did you also find an Webcellence Ltd.? Do you remember the download link? Please post it in the comments below and I’ll upload it to VirusTotal to see if that one is also detected.
Thank you for reading.